嗯,用户让我总结这篇文章的内容,控制在一百个字以内,而且不需要特定的开头。首先,我需要快速浏览文章,抓住主要信息。 文章讲的是一个新的网络攻击活动,目标是俄罗斯的汽车和电子商务行业。使用的是一种新的.NET恶意软件,叫做CAPI Backdoor。攻击者通过钓鱼邮件传播,邮件里有一个ZIP文件,里面包含恶意链接和一个诱饵文档。诱饵看起来像是税务局的通知,内容涉及工资调整和税率变化。 恶意软件一旦运行,会窃取浏览器数据、截图、收集系统信息,并在设备上建立持久性机制。攻击者还使用了伪装的域名来隐藏真实目的,这表明他们针对的是俄罗斯的汽车行业。 所以,总结的时候需要包括:攻击活动名称、目标行业、恶意软件名称、传播方式、诱饵内容、恶意软件功能以及攻击者的策略。 现在把这些信息浓缩到100字以内。要确保涵盖关键点:Operation MotorBeacon、俄罗斯汽车和电商、CAPI Backdoor、钓鱼邮件、诱饵文档内容、恶意软件功能和攻击者策略。 最后检查字数是否符合要求,并确保语言简洁明了。 </think> 新的网络攻击活动Operation MotorBeacon针对俄罗斯汽车和电商行业,利用未知的.NET恶意软件CAPI Backdoor通过钓鱼邮件传播。邮件包含伪装成 payroll recalculation 和 tax update 的诱饵文档及恶意LNK文件,运行后窃取浏览器数据、截图并建立持久性机制。攻击者使用伪装域名隐藏真实目的。 2025-10-20 13:29:24 Author: securityaffairs.com(查看原文) 阅读量:11 收藏
CAPI Backdoor targets Russia’s auto and e-commerce sectors

A new campaign targets Russia’s auto and e-commerce sectors using a previously unknown .NET malware called CAPI Backdoor.
Cybersecurity researchers at Seqrite Labs uncovered a new campaign, tracked as Operation MotorBeacon, that targeted the Russian automobile and e-commerce sectors with a previously unknown .NET malware dubbed CAPI Backdoor.
“SEQRITE Labs Research Team has recently uncovered a campaign which involves targeting Russian Automobile-Commerce industry which involves commercial as well as automobile oriented transactions , we saw the use of unknown .NET malware which we have dubbed as CAPI Backdoor.” reads the report published by Seqrite Labs.
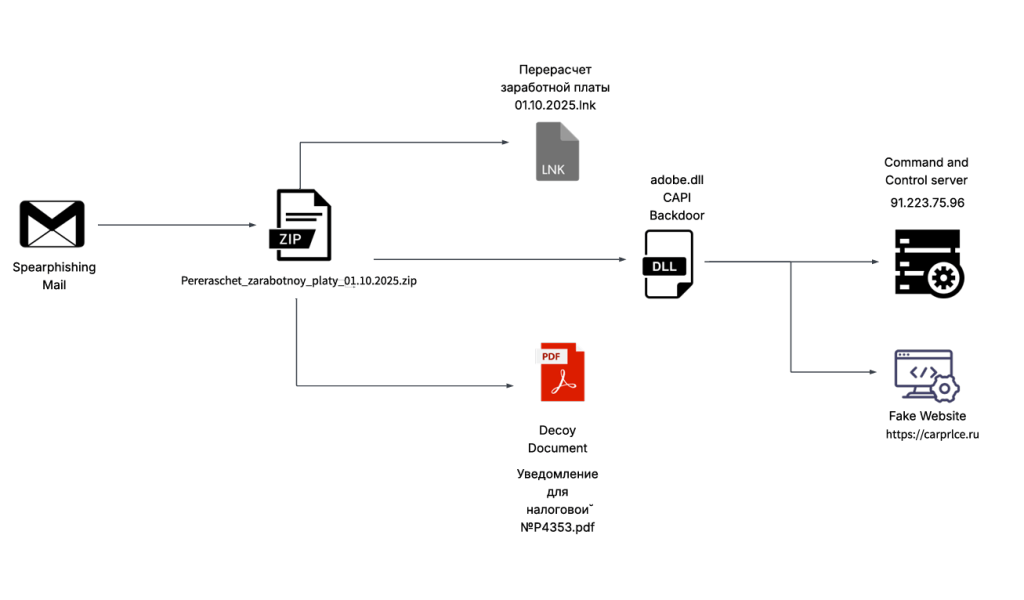
The attack chain starts with phishing emails containing a ZIP archive titled “Перерасчет заработной платы 01.10.2025 (translated Payroll Recalculation as of Oct 1, 2025)” that hides a malicious LNK that runs a .NET implant via rundll32.exe, linking to a C2 server.

The decoy “Notification for the Tax Office No. P4353.pdf” included in the archive poses as a tax update notice effective Oct 1 2025, detailing a PIT hike from 13% to 15% for incomes > 3 M rubles, showing effects on salaries and urging employees to plan budgets and consult HR.
The LNK file runs a .NET backdoor (“adobe.dll”) via rundll32.exe, checks admin rights and AV tools, then opens the decoy document before connecting to 91.223.75[.]96 to receive commands.
CAPI Backdoor supports multiple functionalities such as stealing browser data (Chrome, Edge, Firefox), taking screenshots, gathering system info, listing folders and exfiltrating results.
The malware runs multiple VM/analysis checks and establishes persistence by creating a scheduled task and placing a LNK in the Windows Startup folder to auto-launch the backdoor DLL from the Roaming directory.
Researchers found two network artifacts tied to the CAPI Backdoor, including a DGA-generated domain. The campaign, active since Oct 3, initially used a fake domain later redirected to a legitimate site. The malware was hosted on port 443 and linked in a spear-phishing lure. Early infrastructure was under ASN 197695 (AS-REG), while data exfiltration occurred via ASN 39087 (P.a.k.t LLC).
“We have been tracking this campaign since October 3rd and discovered that it uses a fake domain, carprlce[.]ru, which closely resembles carprice[.]ru the legitimate domain. This indicates that the threat actor is targeting Russian automobile sector.” concludes the report. “The malicious payload is a .NET DLL that functions as a stealer and establishes persistence for future malicious activities.”
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, Russia)
如有侵权请联系:admin#unsafe.sh