
Global Group是一个勒索软件即服务组织,在2025年6月出现。该组织提供高收益分成、移动友好面板和AI谈判功能,并与Mamona和BlackLock有关联。其恶意软件用Go编写,支持跨平台,并采用ChaCha20-Poly1305加密算法。AttackIQ发布攻击图模拟其行为以测试安全措施。 2025-10-16 18:24:27 Author: securityboulevard.com(查看原文) 阅读量:3 收藏
Introduction
Global Group is a Ransomware-as-a-Service (RaaS) operation that publicly surfaced in June 2025 and was promoted on underground forums by a Russian-speaking actor using the moniker “$$$”. The group markets itself as a commercial, affiliate-friendly RaaS platform, offering high revenue shares and no entry fees, mobile-friendly affiliate admin panels, customizable payload builders, and even AI-assisted negotiation/chatbot features for extortion dialogues to speed up monetization and make it easier for affiliates to operate at scale.
Multiple analyses have highlighted strong overlaps between Global Group and earlier ransomware families such as Mamona and BlackLock, pointing to a likely rebrand or continuation of the same developer group. The similarities extend beyond surface-level traits, encompassing shared infrastructure, identical mutex, and reused code segments within the encryption and network communication routines. Even the ransom note style and negotiation patterns resemble those of Mamona and BlackLock, suggesting that Global Group represents an evolutionary step rather than a new operation.
Global Group’s payloads are written in Go to provide cross-platform support (Windows, Linux, MacOS) with features like LDAP propagation, token impersonation, and configurable execution modes, allowing affiliates to customize encryption behavior for speed, spread, stealth, or delayed execution times. For encryption, Global Group employs the ChaCha20-Poly1305 algorithm and prioritizes speed and efficiency, with files smaller than 5 MB fully encrypted, while larger files have only 20% of their content encrypted to accelerate the overall encryption process. The ransomware also disables recovery mechanisms, terminates antivirus and endpoint detection and response (EDR) processes, clears Windows Event Logs, and deletes shadow copies to ensure maximum disruption and leverage during extortion.
AttackIQ has released a new attack graph that emulates the Tactics, Techniques, and Procedures (TTPs) associated with the deployment of Global Group ransomware to help customers validate their security controls and their ability to defend against this threat.
Validating your security program performance against these behaviors is vital in reducing risk. By using these new attack graphs in the AttackIQ Security Optimization Platform, security teams will be able to:
- Evaluate security control performance against baseline behaviors associated with the Global Group ransomware.
- Assess their security posture against an opportunistic adversary, which does not discriminate when it comes to selecting its targets.
- Continuously validate detection and prevention pipelines against a playbook similar to those of many of the groups currently focused on ransomware activities.
[Malware Emulation] Global Group Ransomware – 2025-09 – Associated Tactics, Techniques, and Procedures (TTPs)
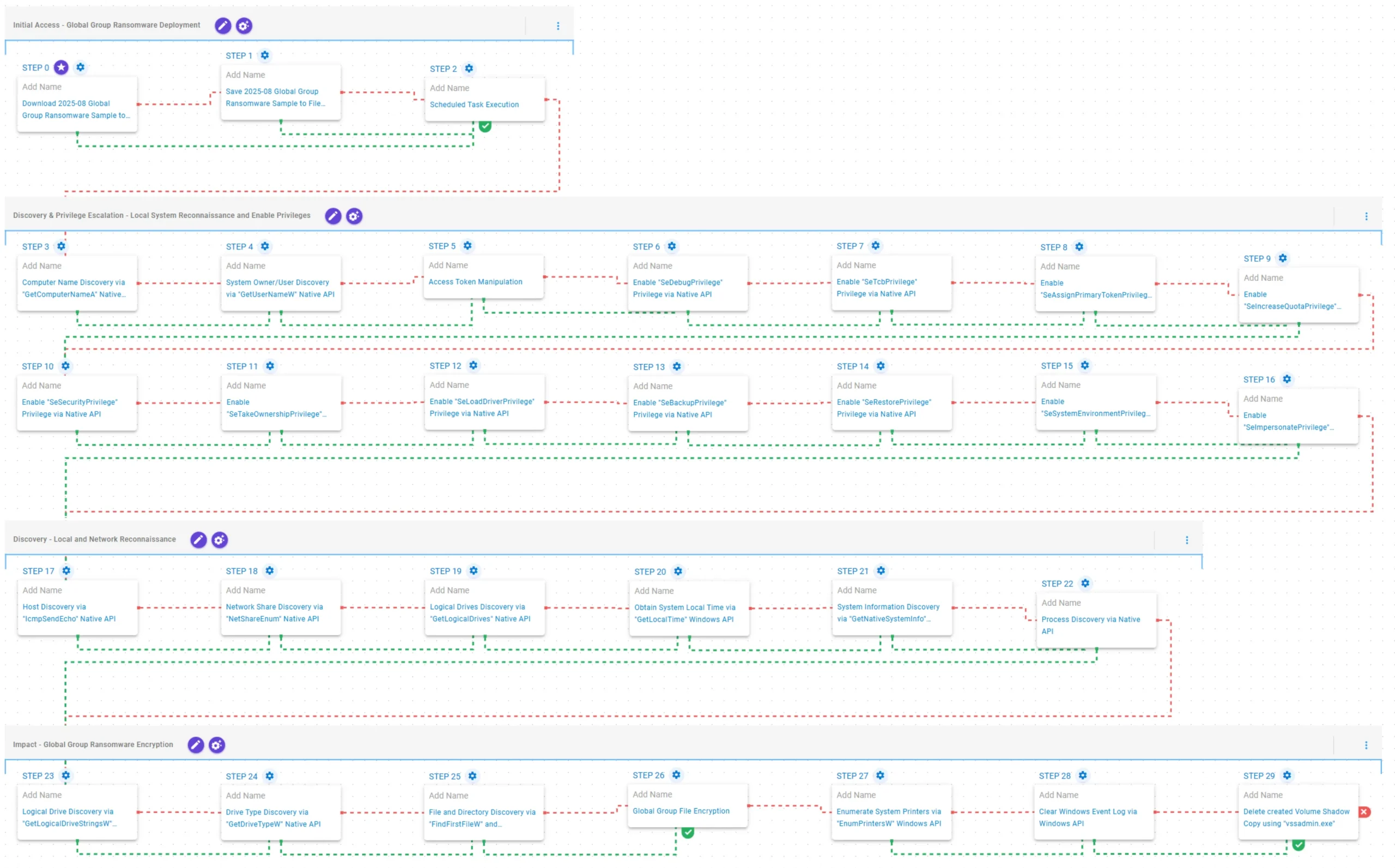
This emulation replicates the sequence of behaviors associated with the deployment of Global Group Ransomware on a compromised system with the intent of providing customers with the opportunity to detect and/or prevent a compromise in progress.
Initial Access – Global Group Ransomware Deployment
This stage begins with the deployment of Global Group ransomware on the target system. Execution is achieved through the creation of a scheduled task, which is immediately executed to begin infection.
2025-08 Global Group Ransomware Sample (T1105): The Global Group Ransomware sample (SHA256: 23b43226d53e2c8cd9519d785ba75b833fbd11939cd1d70999f84c1365b2da5d) is downloaded to memory and saved to disk in two separate scenarios to test network and endpoint controls and their ability to prevent the delivery of known malicious samples.
Scheduled Task Execution (T1053.005): This scenario emulates persistence by scheduling and executing a task using the Windows utility schtasks.
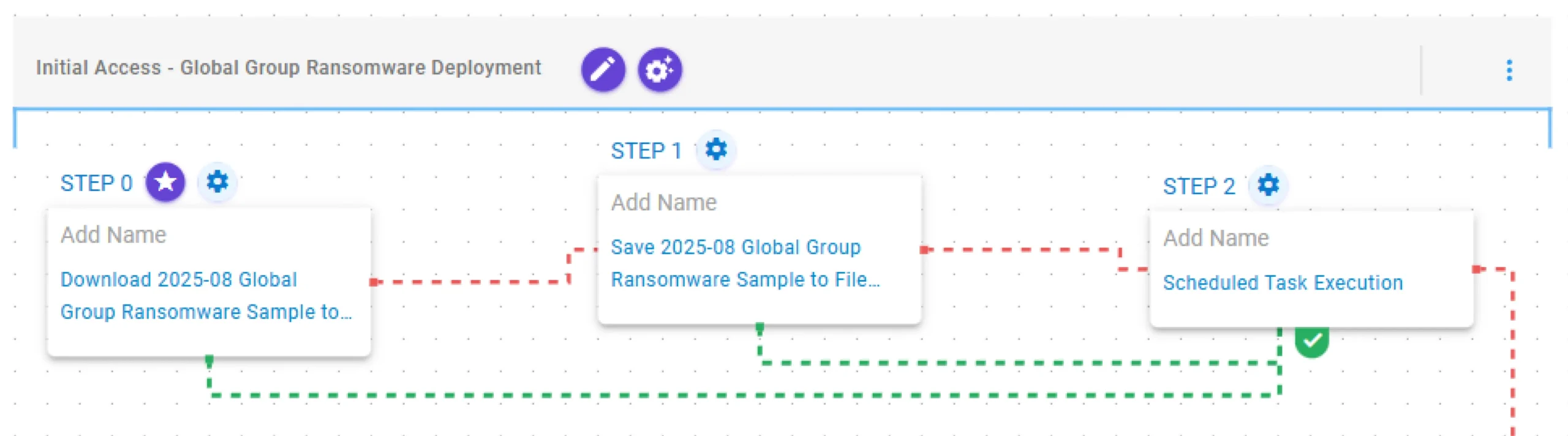
Discovery & Privilege Escalation – Local System Reconnaissance and Enable Privileges
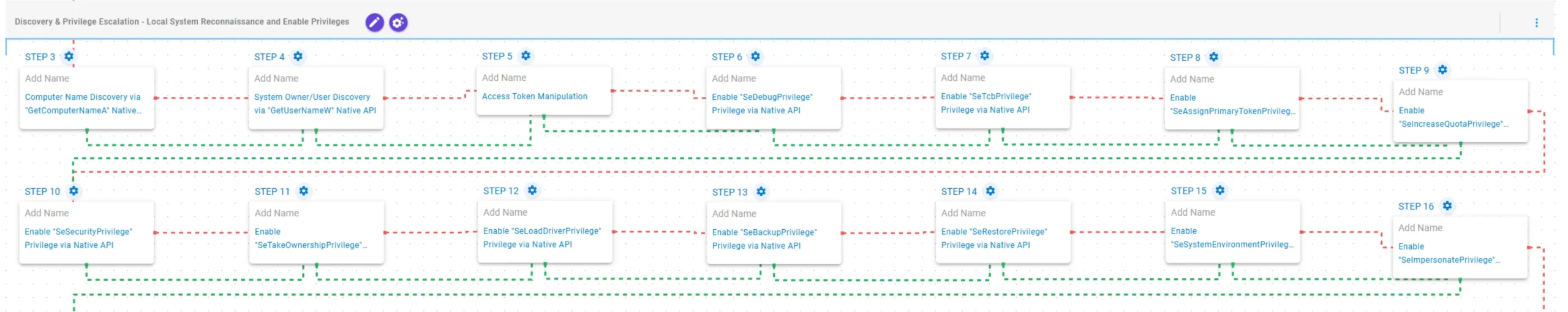
This stage begins with the retrieval of local identity information using GetComputerNameA to obtain the host name and GetUserNameW to determine the logged-on user. After this, access token manipulation is performed to list tokens and impersonate the current user. Finally, AdjustTokenPrivilege is invoked to enable several required privileges and achieve privilege escalation.
Computer Name Discovery via “GetComputerNameA” Native API (T1082): This scenario calls the GetComputerNameA Windows API to gather the NetBIOS name.
System Owner/User Discovery via “GetUserNameW” Native API (T1033): This scenario executes the GetUserNameW Windows native API call to retrieve the account name associated with the local computer.
Access Token Manipulation (T1134): This scenario lists and duplicates access tokens of the running processes available on the target system in order to escalate privileges. This technique allows the execution of arbitrary commands by impersonating a logged-in user.
Enable “SeDebugPrivilege” Privilege via Native API (T1134): This scenario enables the SeDebugPrivilege privilege for the current process using the AdjustTokenPrivilege Windows API.
Enable “SeTcbPrivilege” Privilege via Native API (T1134): This scenario enables the SeTcbPrivilege privilege for the current process using the AdjustTokenPrivilege Windows API.
Enable “SeAssignPrimaryTokenPrivilege” Privilege via Native API (T1134): This scenario enables the SeAssignPrimaryTokenPrivilege privilege for the current process using the AdjustTokenPrivilege Windows API.
Enable “SeIncreaseQuotaPrivilege” Privilege via Native API (T1134): This scenario enables the SeIncreaseQuotaPrivilege privilege for the current process using the AdjustTokenPrivilege Windows API.
Enable “SeSecurityPrivilege” Privilege via Native API (T1134): This scenario enables the SeSecurityPrivilege privilege for the current process using the AdjustTokenPrivilege Windows API.
Enable ” SeTakeOwnershipPrivilege” Privilege via Native API (T1134): This scenario enables the SeTakeOwnershipPrivilege privilege for the current process using the AdjustTokenPrivilege Windows API.
Enable “SeLoadDriverPrivilege” Privilege via Native API (T1134): This scenario enables the SeLoadDriverPrivilege privilege for the current process using the AdjustTokenPrivilege Windows API.
Enable “SeBackupPrivilege” Privilege via Native API (T1134): This scenario enables the SeBackupPrivilege privilege for the current process using the AdjustTokenPrivilege Windows API.
Enable “SeRestorePrivilege” Privilege via Native API (T1134): This scenario enables the SeRestorePrivilege privilege for the current process using the AdjustTokenPrivilege Windows API.
Enable “SeSystemEnvironmentPrivilege” Privilege via Native API (T1134): This scenario enables the SeSystemEnvironmentPrivilege privilege for the current process using the AdjustTokenPrivilege Windows API.
Enable “SeImpersonatePrivilege” Privilege via Native API (T1134): This scenario enables the SeImpersonatePrivilege privilege for the current process using the AdjustTokenPrivilege Windows API.
Discovery – Local and Network Reconnaissance

This stage is initiated by ICMP probes using IcmpSendEcho to discover remotely accessible systems on the network. Then, network shares are enumerated via NetShareEnum. Next, GetLogicalDrives is invoked to identify mounted volumes and drive letters, system information is confirmed with GetNativeSystemInfo, and local time discovery is performed using GetLocalTime. Finally, running processes are enumerated by taking a snapshot with CreateToolhelp32Snapshot and iterating through entries with Process32FirstW and Process32NextW.
Host Discovery via “IcmpSendEcho” Native API (T1046): This scenario executes the IcmpSendEcho Windows API call to perform a discovery scan on local networks.
Network Share Discovery via “NetShareEnum” Native API (T1135): This scenario executes the NetShareEnum Windows native API call to enumerate network shares from the local computer.
Logical Drives Discovery via “GetLogicalDrives” Native API (T1082): This scenario executes the GetLogicalDrives Windows API call to retrieve the currently available disk drives.
Obtain System Local Time via “GetLocalTime” Windows API (T1124): This scenario executes the GetLocalTime Windows API to retrieve the local system time.
System Information Discovery via “GetNativeSystemInfo” Native API (T1082): This scenario executes the GetNativeSystemInfo Native API call to retrieve information associated with the system.
Process Discovery via Native API (T1057): This scenario executes the CreateToolhelp32SnapshotWindows native API call to receive a list of running processes and iterates through each process object with Process32FirstW and Process32NextW.
Impact – Global Group Ransomware Encryption

This stage is initiated by drive enumeration, using GetLogicalDriveStringsW to list available drives, followed by a call to GetDriveTypeW to determine the drive types. Next, files are discovered and traversed using FindFirstFileW and FindNextFileW to identify encryption targets, which are then encrypted using the ChaCha20-Poly1305 algorithm. Following successful encryption, printers are enumerated with EnumPrintersW, event logs are cleared to hinder forensic analysis, and shadow copies are removed using vssadmin to prevent system recovery.
Logical Drive Discovery via “GetLogicalDriveStringsW” Native API (T1120): This scenario executes the GetLogicalDriveStringsW Windows native API call to retrieve information about the system’s physical drives.
Drive Type Discovery via “GetDriveTypeW” Native API (T1120): This scenario retrieves information about the system’s physical disks using the GetDriveTypeW Windows API call.
File and Directory Discovery via “FindFirstFileW” and “FindNextFileW” Native API (T1083): This scenario executes the FindFirstFileW and FindNextFileW Windows native API calls to enumerate the file system.
Global Group File Encryption (T1486): This scenario performs the file encryption routines used by common ransomware families. Files matching an extension list are identified and encrypted in place using similar encryption algorithms as used by Global Group ransomware.
Enumerate System Printers via “EnumPrintersW” Windows API (T1120): This scenario executes the EnumPrintersW Windows API to enumerate available printers, print servers, domains, or print providers.
Clear Windows Event Log via Windows API (T1070.001): This scenario executes the ClearEventLogW Windows API to clear Windows Event Logs.
Delete created Volume Shadow Copy using “vssadmin.exe” (T1490): This scenario executes the vssadmin.exe utility to delete a recent Volume Shadow Copy created by the assessment template.
Wrap-up
In summary, this emulation will evaluate security and incident response processes and support the improvement of your security control posture against the behaviors exhibited by Global Group ransomware. With data generated from continuous testing and use of this assessment template, you can focus your teams on achieving key security outcomes, adjust your security controls, and work to elevate your total security program effectiveness against a known and dangerous threat.
AttackIQ, the leading provider of Adversarial Exposure Validation (AEV) solutions, is trusted by top organizations worldwide to validate security controls in real time. By emulating real-world adversary behavior, AttackIQ closes the gap between knowing about a vulnerability and understanding its true risk. AttackIQ’s AEV platform aligns with the Continuous Threat Exposure Management (CTEM) framework, enabling a structured, risk-based approach to ongoing security assessment and improvement. The company is committed to supporting its MSSP partners with a Flexible Preactive Partner Program that provides turn-key solutions, empowering them to elevate client security. AttackIQ is passionate about giving back to the cybersecurity community through its free award-winning AttackIQ Academy and founding research partnership with MITRE Center for Threat-Informed Defense.
Ayelen Torello is an Adversary Research Engineer at AttackIQ where she creates adversary emulations to enable customers to test and validate their security controls. Ayelen has extensive experience in the CTI field and is a results-driven professional with a passion for malware analysis and conducting thorough investigations.
如有侵权请联系:admin#unsafe.sh
