网络安全市场拥挤,近4000家公司竞争。CISO面临压力大,决策依赖信任网络(同行、团队、集成商、分析师)和预算。他们注重解决问题和时间安排,并寻求可靠而非最贵的方案。 2025-10-15 08:50:26 Author: securityboulevard.com(查看原文) 阅读量:9 收藏
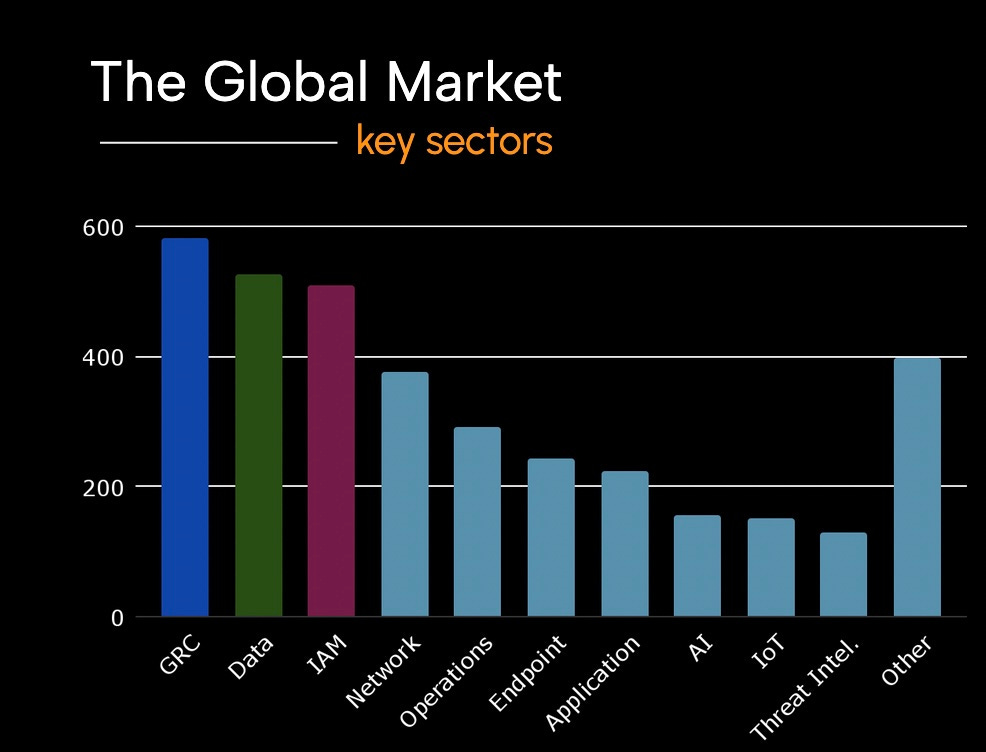
The cybersecurity market has never been more crowded. Every week, a new company claims to solve the latest threat, while others quietly vanish or are absorbed. IT-Harvest Dashboard, the most comprehensive database of cybersecurity vendors, is currently tracking nearly 4,000 companies.
The vast majority of these companies are targeting the same role within their ideal customers: the Chief Information Security Officer, or CISO. For them, this abundance doesn’t mean choice but noise. .
Meanwhile, CISOs themselves operate under intense pressure: limited bandwidth, career risk, burnout, and the enormous cost of switching solutions if they make the wrong call.
This is the first of a series of articles that will explore how CISOs are navigating this challenge, how they evaluate and approach vendors, who they trust, and what mistakes can kill relationships.
We are launching Scaling Cyber! The podcast where cybersecurity founders and leaders from all over the world share their journeys of growth, challenges, and global expansion. Subscribe now!
There’s not one way that CISOs buy. Talking with them, listening to their podcasts, or reading their LinkedIn or X posts shows that there are different approaches they take.
What is clear, though, is that they don’t “shop” like consumers nor do they evaluate vendors in the same way other enterprise buyers do. At least not entirely.
CISOs have a horizontal responsibility across their organization, needing to support the business, while also protecting it, even though they know they will never be able to prevent 100 % of threats. Pavi Ramamurthy, Global CISO and CIO at BlackHawk Network, put it in a simple yet very interesting way when describing their job: “I can’t promise safe, but I can promise ready.”
When choosing solutions, there are two very important dimensions they consider: what pain or problem they need to solve and when they can solve it. The third, obviously, is the budget.
Unless they are in the middle of a crisis or recently faced one, CISOs have a plan of what topics they will be addressing and in which priority. Resources are always limited, even for those with the deepest pockets, so planning is key for them.
As one security leader put it, “Most CISOs are looking six to twelve months out. If you’re pushing me to buy tomorrow, you’re out of sync with my world.“.
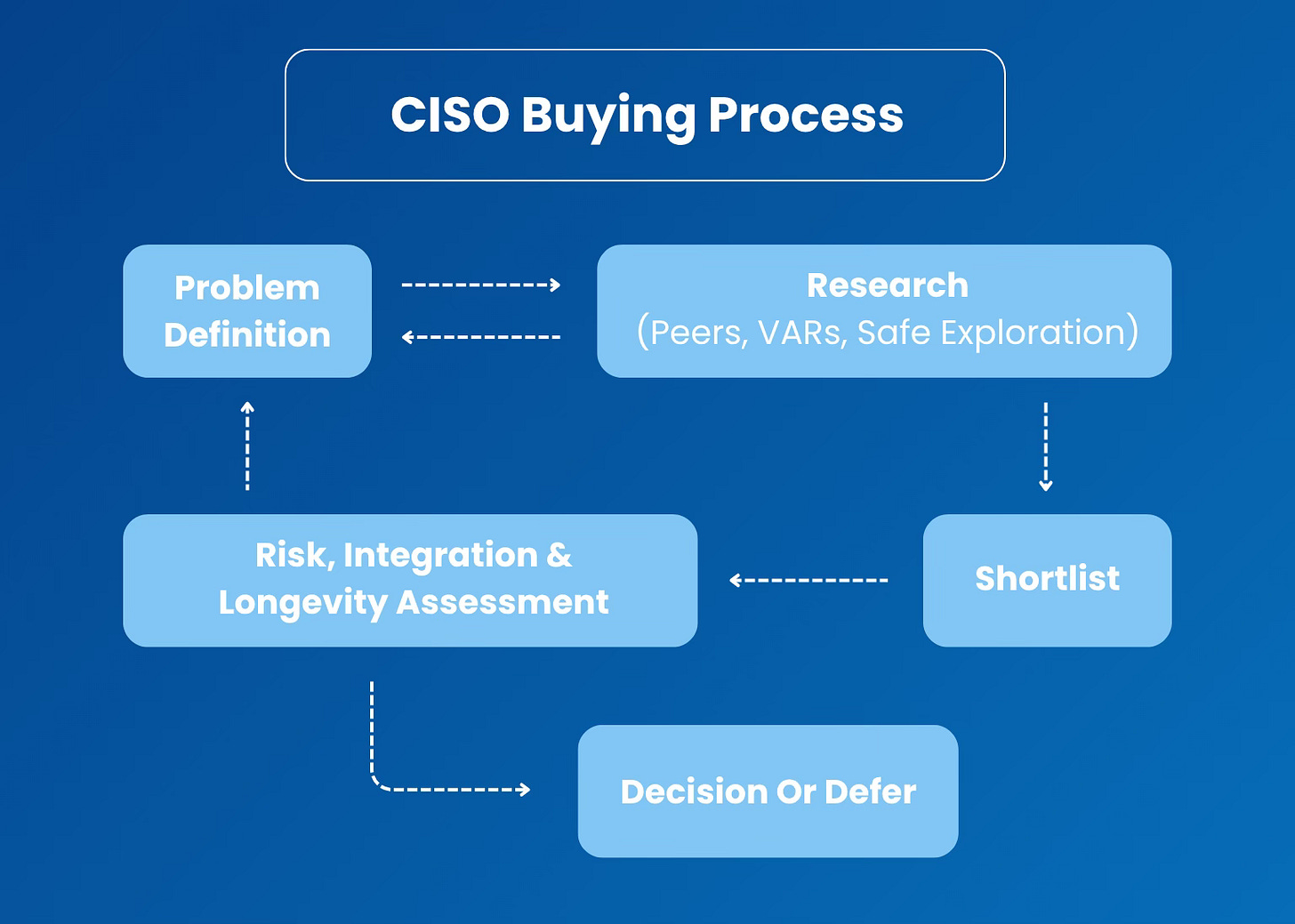
CISOs begin with a problem definition or statement, not necessarily a vendor list. Due to business priorities, compliance, trends or to improve their overall security posture, they have a set of topics (problems, pains, upgrades, improvements, etc) to address.
Going through that list, they consult with their trusted network (peers, suppliers) and conduct a “safe” exploration of the potential solutions, through articles, research, videos and reviews. Some of them, they talk with their current vendors to see if they have another solution for this new problem.
Only after that initial review, they have a shortlist of potential solutions to their problem, sometimes including the option to build it internally instead of using a third party vendor. CISOs are not the ones putting together that initial selection, at least not exclusively; they lean heavily on their teams for that.
Up to this point, with the exception of conversations they might have had with an existing vendor of theirs to see if they have a solution for this new problem, they most likely have not even talked with any other cybersecurity provider.
Once they conduct an internal assessment on risks, integration needs and the overall complexity of the potential solutions, they get to the moment to decide… and sometimes that decision might be to do nothing and accept the current problem as a known risk or maintain what they already have to address it, even if partially.
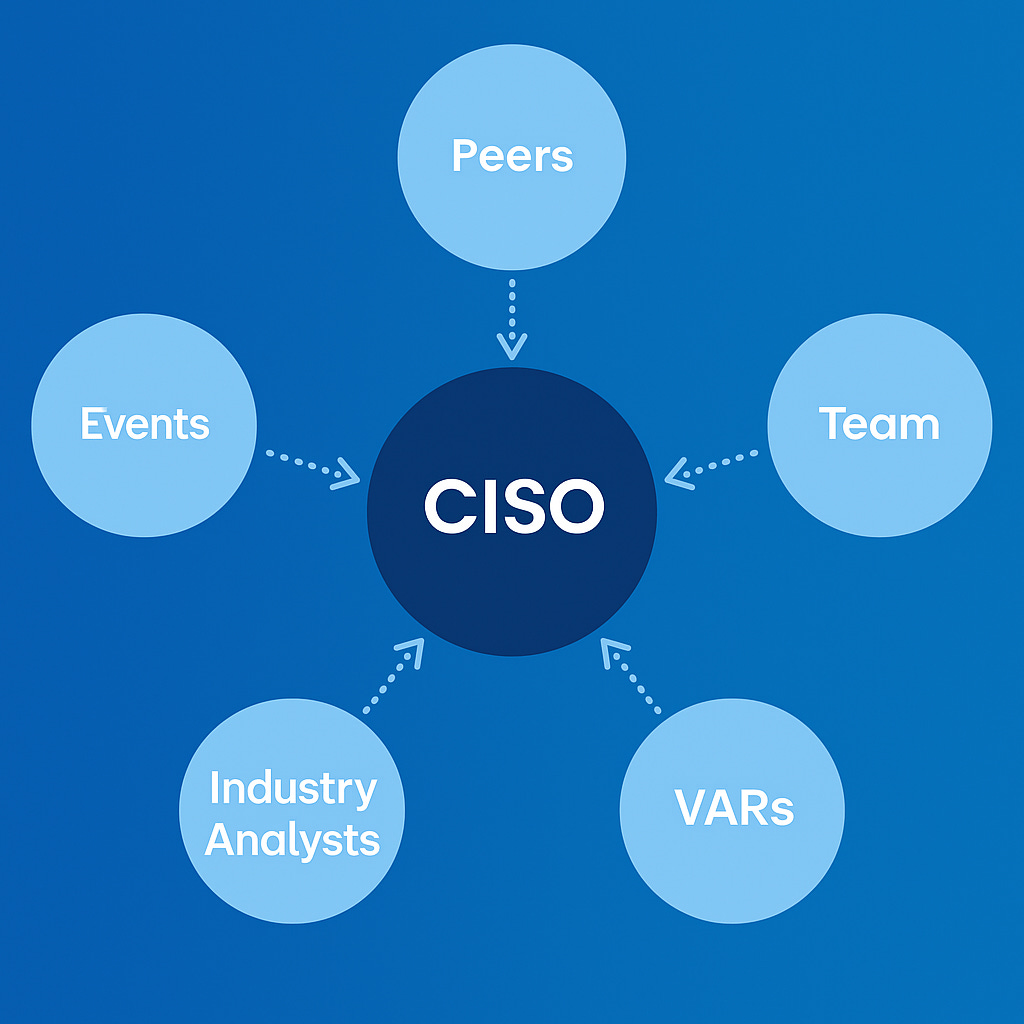
The path to the CISO is through their trusted network, which is formed by peers, their team, the VARs/Integrators they work regularly with, and the events and conferences they attend. In some cases, that network also includes industry analysts.
What they usually don’t do is follow up on cold calls, emails or direct messages, and not necessarily because they don’t want to, but because they are regularly bombarded with them.
Ross Hosman shared an informal survey he ran among other CISOs recently, and 50 % of them receive at up to 5 unsolicited contacts per day, with 12 % of them getting more than 20.
Another thing they don’t want to do is click on “Book a Demo” buttons, unless the vendor has already been vetted by someone they trust. This is not because they are not curious, it is because they don’t want to end up trapped in another sales and marketing funnel from another vendor.
Mike Johnson, from Rivian, often says that what CISOs want is to feel “safe” when evaluating new vendors. They want to do things at their own pace, in their own way, without being forced into what the vendor sales process dictates.
That’s why many CISOs would start asking their peers before anything else. The majority of CISOs are part of some close community (often a Signal group or Slack channel) where they ask questions about how others are solving problems and what vendors are using for that.
Their usual VARs and Integrators are also a source, sometimes even more important than their peers. As Edward Contreras pointed out in a recent Defense In Depth episode, his trusted VARs “have been with me for a while. They’ve been in the trenches. They’ve seen some failures. They’ve seen some successes.”
What many vendors and service providers often forget is that the CISO isn’t the only person to talk to, and moreover, sometimes it is not even the right one. More than one CISO recommends speaking to their team first, as their opinion will matter to them.
They will most probably be the real users of the solution, and they are the ones that will need to see, first-hand, if it is the appropriate one to solve the problem at hand. That’s why CISOs are looking for their feedback. “Don’t talk to the CISOs, talk to the leaders within the security org, talk to the principal engineers. Those are the folks who are making the recommendations.”, said Mike Johnson about this topic.
What happens with events and conferences? CISOs definitely continue to attend, as well as their teams, but that doesn’t mean they are going to listen to everything that is being shown to them there.
The reality is that many CISOs see the value to attend not in how much the vendor is spending in the booth, but in what is happening outside or around the event, where they can gather with their community, spend time together and learn from peers and from those they trust, as Geoff Belknap, CISO of LinkedIn, pointed out, echoing the opinion of many others in the industry.
Lastly, there are industry analysts, like Gartner, Forrester and others. While many CISOs would not recognize it publicly, the reality is that these analysts have an influence in their decision making, especially for those that are their paying customers.
No CISO (maybe some) will choose a solution just because an analyst put it at the top of the report, but many would include that “market leader” in their shortlist.
For instance, two cybersecurity companies that I consulted noticed how being mentioned directly in Gartner reports – or even that their sector was mentioned as a priority – increased the number of CISOs that started to be interested in taking their invitations to events or meetings.
Lastly, their existing vendors, directly or indirectly, also are an influence. CISOs might look into their existing stack to see if a company they already work with has a solution for this new issue they are trying to address.
“I don’t want to go through the complexity of acquiring a new product. More screens, great complexity, greater total cost of ownership is an issue that I want to manage. So, if I go to my vendor and say, what can you do? They often have purchased a product.”, said Jason Taule, CISO of Luminis Health in a recent Defense in Depth podcast.
Even left to the last part of this article, the budget has a strong impact on how CISOs choose solutions.
First and foremost, CISOs have already allocated a budget for their projects in advance, and internal rules can be very strict about their ability to spend it on people and/or tools. If they don’t have a reserve for “innovation” or “research”, the money is already in a particular budget line.
However, the budget they have allocated – and the potential price of the solution – can give these security leaders some room to navigate the selection process with more or less formality.
For instance, many organizations request formal tenders only when the price will be above a certain value – anything below can be decided alone by the budget owner.
If the price of the solution demands RFPs and involvement of a buying committee, the process can become long and cumbersome, and CISOs might choose to go with a “safer” bet (a.k.a. an established or existing vendor) to avoid the hazard of justifying the purchase of some unknown product to the CFO or others.
Moreover, in many cases, the CISO is not the sole decision maker when it comes to its budget, as some parts of it can be held by other functions in the organization, like IT, HR, Compliance, etc. This complexity can deeply affect the way they choose solutions.
In a world where every vendor promises to be the “best,” CISOs rely on something far rarer: trust.
Their buying journey isn’t a funnel; it’s an ecosystem. Peers, teams, VARs, analysts, and events all act as filters that shape which solutions even get a chance to be considered. The decision itself is slow, deliberate, and can end with “not now.”
The vendors that make it through aren’t always necessarily the loudest. They’re the ones that meet the CISO where they are: aligned with their priorities, respectful of their time, and capable of proving value without pressure.
In short, CISOs don’t buy features; they buy confidence. And as with a strong security posture, that’s something that takes time to build.
In the next part of this series, we will look at how CISOs view vendors, from startups to established ones, and what it takes for a newcomer to earn their trust.
*** This is a Security Bloggers Network syndicated blog from Cybersecurity & Business authored by Ignacio Sbampato. Read the original post at: https://cybersecandbiz.substack.com/p/inside-the-ciso-mind-series-1
如有侵权请联系:admin#unsafe.sh