2025年第三季度欧洲遭遇288起勒索软件攻击, Qilin以65起居首, SafePay迅速崛起至第二位。德国遭受69起攻击最多, 英国、意大利等紧随其后。机场等关键基础设施受损导致多国混乱。威胁持续且不断演变。 2025-10-15 11:31:13 Author: cyble.com(查看原文) 阅读量:19 收藏
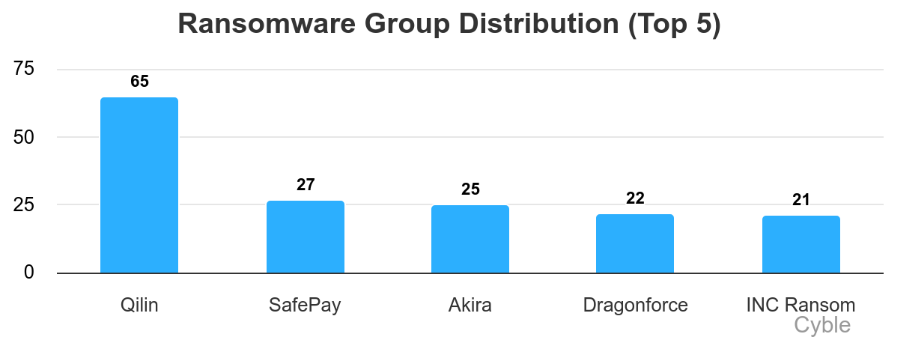
Europe recorded 288 ransomware attacks in Q3 2025, with Qilin maintaining dominance at 65 victims and SafePay rapidly ascending to second place.
Europe’s ransomware problem isn’t getting better!
Q3 2025 saw 288 attacks hammer organizations across the region, with Qilin claiming 65 victims and cementing its position as the most aggressive threat actor targeting the continent. But it’s SafePay’s meteoric rise to second place—and a devastating airport attack that rippled across multiple countries—that has security teams particularly worried about what’s coming next.
The numbers tell a sobering story in Cyble’s latest report, “Europe’s Threat Landscape: What 2025 Exposed — and Why 2026 Could Be Worse.” Despite everything organizations have thrown at the ransomware problem—better defenses, more awareness, increased spending—attackers are adapting faster. And when a supply chain attack can ground flights across an entire region, it’s clear we’re dealing with threats that go far beyond encrypted files and ransom notes.
Q3’s attacks represent just a slight dip from Q2’s 294, but don’t mistake that for progress. The threat landscape has essentially plateaued at dangerously high levels, with ransomware groups showing no signs of backing down.
The quarter’s most alarming incident came when attackers compromised a third-party service provider, triggering widespread chaos at airports throughout Europe and the UK. Flights delayed, check-in systems down, baggage handling paralyzed—all because one shared service provider got hit.
Germany took the hardest beating with 69 attacks, followed by the UK (48), Italy (40), France (33), and Spain (28). If you’re running security for an organization in Western Europe, you’re in the crosshairs of some of the world’s most sophisticated cybercriminals, and they’re not slowing down.

Qilin Owns Europe While SafePay Emerges as the New Threat
Qilin didn’t just lead in Q3—they dominated. Their 65 victims represent nearly a quarter of all ransomware attacks in the region, more than double SafePay’s 27.

What makes Qilin so effective? Their ransomware-as-a-service model is essentially the Uber of cybercrime: slick platform, good tools, and affiliate payouts generous enough to poach talent from competing operations.
The group’s targeting is strategic, not random. France saw 14 Qilin attacks, Germany 10, Spain and Italy 9 each, and the UK 8.

They’re going after the biggest economies where companies have deep pockets and low tolerance for downtime. Manufacturing companies took 11 hits from Qilin, Construction firms 10, and Professional Services 9. These aren’t accidents—they’re calculated choices targeting sectors where a few days of disruption costs millions.

But here’s what’s keeping threat analysts up at night: SafePay’s sudden emergence as a major player. This group only showed up in September 2024, yet they’ve already claimed 27 victims across Europe in Q3 alone. Unlike typical ransomware-as-a-service operations that rely on a loose network of affiliates, SafePay runs as a tight-knit crew, which lets them move fast and hit hard. Some days they’ve launched more than 10 attacks in a single 24-hour period.
Their technical game is strong too. SafePay uses double extortion—encrypting your systems with AES and RSA while simultaneously stealing your data—so even if you have backups, they can still leak everything to the dark web. With over 330 claimed victims globally, they’re proving that you don’t need years in the game to make a massive impact.
Rounding out the top five, Akira grabbed third place with 25 victims, Dragonforce took 22, and INC Ransom hit 21. What this spread tells us is that Europe isn’t dealing with a single dominant threat—multiple well-funded groups are running parallel campaigns, which makes defense exponentially harder.
Who’s Getting Hit and Where
Professional Services firms bore the brunt of Q3’s attacks, with 44 organizations compromised. Manufacturing wasn’t far behind at 41, followed by Construction at 38. The pattern makes sense when you think about it—Professional Services firms hold client data from dozens of other companies, Manufacturing operations can’t afford extended downtime, and Construction projects run on tight margins where delays equal catastrophic losses.

Consumer Goods companies took 19 hits, IT firms 16, and the Automotive, Transportation & Logistics, and Energy sectors each saw 11-13 attacks. Even Education and Hospitality, often considered lower-value targets, experienced 10 attacks each.
The concentration of attacks on Professional Services is particularly nasty. Breach one law firm or consulting company, and you potentially compromise data from every client they serve. It’s the ransomware equivalent of breaking into an apartment building versus a single house—way more value for the same amount of effort.
Qilin’s ability to hit every major country and industry in the region shows just how versatile and well-organized they are. This isn’t some fly-by-night operation running automated scans—it’s a professional criminal enterprise with the resources and expertise to maintain dominance across multiple continents simultaneously.
Germany’s position as the top target reflects its economic weight in Europe. You’ve got massive manufacturing operations, critical infrastructure, and a business culture that historically prioritized operational efficiency over security hardening. That’s changing now, but legacy vulnerabilities don’t disappear overnight.
The UK’s 48 attacks hit everything from London financial firms to tech startups to manufacturing centers in the Midlands. Italy’s 40 incidents ranged from fashion houses to small businesses, while Spain’s 28 attacks targeted hospitality, manufacturing, and services. France’s 33 incidents affected aerospace contractors, retailers, and everything in between. The message is clear: nobody’s safe, regardless of size, sector, or location.
New Players Enter the Game
September 2025 saw The Gentlemen ransomware group make their debut, and they made sure everyone noticed. Within their first month, they posted 35 victims to their leak site.
What’s drawing attention isn’t just their aggressive pace—it’s their affiliate compensation model. They’re offering a 90/10 split favoring affiliates, which is basically unheard of in the ransomware world. That kind of money is going to pull experienced operators away from established groups, and Q4 could see The Gentlemen’s victim count skyrocket.
LockBit, meanwhile, is trying to make a comeback. After law enforcement actions in 2024 basically destroyed their operations, they announced LockBit 5.0 on September 3, 2025. The announcement came via the dark web forum RAMP, but so far they’re struggling to regain relevance. The ransomware landscape moved on while they were down, and breaking back into the top tier won’t be easy with competition this fierce.
Other groups worth watching include DragonForce, Meow, KillSec, and Cicada3301. These operations are experimenting with decentralized structures that make them harder to track and disrupt. Some are also mixing financial motives with ideological elements, which makes their behavior less predictable and the incident response more complicated.
On the technical side, ransomware developers are getting smarter about evading detection. New variants are specifically designed to slip past the endpoint protection solutions most European enterprises use. Intermittent encryption—where attackers only encrypt portions of files to speed up the process—is becoming more common, shrinking the window defenders have to detect and stop attacks in progress.
When Critical Infrastructure Gets Hit
The transportation sector’s nightmare scenario played out in Q3 when a third-party provider got ransomware, taking down airport systems across multiple countries. This is exactly what security professionals have been warning about for years—hit one shared service provider, and the damage cascades to everyone relying on them.
Flight delays, check-in failures, baggage system crashes—these aren’t hypothetical risks, they’re what actually happened. And the recovery took days, not hours, with real operational and financial consequences rippling through the entire aviation ecosystem.
This attack pattern is becoming the preferred approach for sophisticated ransomware groups. Why spend time and resources compromising 50 individual companies when you can hit one managed service provider or software vendor and impact hundreds of downstream clients simultaneously? The math is simple for attackers. Same effort, exponentially higher impact, and potentially much bigger ransom demands.
The aviation incident proves that ransomware has moved beyond being an IT problem—it’s now a physical infrastructure problem. When critical systems go down, people get stranded, cargo gets delayed, and entire supply chains grind to a halt. Organizations need to be thinking about incident response plans that account for these extended, multi-day outages affecting core operations.
What This Means Going Forward
Europe’s ransomware situation isn’t improving, and pretending otherwise is dangerous. The 288 attacks in Q3 show that despite increased awareness, better tools, and more investment in cybersecurity, attackers are keeping pace. Organizations that think their current defenses are “good enough” are setting themselves up for a very expensive lesson.
Qilin’s continued dominance, SafePay’s explosive growth, and The Gentlemen’s aggressive entry into the market all point to the same conclusion: the ransomware ecosystem is healthy, well-funded, and constantly evolving. Groups that get disrupted are quickly replaced by new operations that learned from their predecessors’ mistakes. The idea that law enforcement actions or improved defenses will solve this problem is increasingly divorced from reality.
What Actually Works?
Network segmentation that limits how far attackers can move once they’re in. Offline, immutable backups that can’t be encrypted or deleted by attackers. Hardened endpoints and infrastructure that close the easy vulnerabilities. Risk-based vulnerability management that fixes the stuff that actually matters. Continuous monitoring across endpoints, networks, and cloud environments that catches attacks in progress. And incident response plans that get tested regularly, not just filed away in a drawer.
Cyble’s attack surface management platform helps organizations identify and fix exposures across their network and cloud assets before attackers find them. Our dark web monitoring provides early warning when credentials leak or threat actors start planning attacks against your sector.
Get a free external threat profile to see what your organization looks like from an attacker’s perspective—and what you need to fix first.
For the complete picture of threats facing Europe and the UK in 2025, including detailed intelligence on threat actors, attack techniques, and regional trends, check out the full report “Europe’s Threat Landscape: What 2025 Exposed — and Why 2026 Could Be Worse.”
如有侵权请联系:admin#unsafe.sh