
文章介绍了面向工业环境的"OT Breach Ready Cyber Defense"策略,强调通过主动检测、快速响应和恢复能力来应对网络安全威胁。该方法采用微分段技术将网络划分为独立的安全区域,限制潜在攻击的扩散范围,并通过最小化攻击面和快速隔离机制来提高整体系统的弹性和安全性。 2025-10-14 15:38:20 Author: securityboulevard.com(查看原文) 阅读量:75 收藏
Breach ready cyber defense is a proactive and resilient approach designed to ensure that operational technology (OT) environments, such as manufacturing lines, refineries, pipelines, rail control systems, or telecom switching networks, can continue operating even if a cyber breach occurs. This approach goes beyond preventive cybersecurity controls and best practices that focus on making it difficult for attackers to gain access, prioritizing active containment upon early detection to prevent attacks from expanding beyond the initial point of entry.
Unlike traditional perimeter-focused security, which assumes you can keep attackers out, breach ready cyber defense assumes compromise is inevitable and focuses its activities on:
Prevention: Anticipating attacks through attack path mapping, surface reduction, interception modeling, and lateral movement control
Response: Containing attacks mid-stream by quarantining zones, isolating unaffected systems, and disrupting breaches
Resilience: Evolving organizational endurance through effective containment, recovery, and failover capabilities
In OT environments, this is more than just avoiding data theft. it’s about preventing loss of life, environmental disasters, or crippling national infrastructure and ensuring reliable efficiency. OT breach ready cyber defense is the bedrock of society in general and absolutely paramount to the growth of the nation.
Are You Breach Ready? Uncover hidden lateral attack risks in just 5 days. Get a free Breach Readiness Assessment with a visual roadmap of what to fix first.
Urgent for Critical Infrastructure
Let us look at reality. Despite increasing investments into cybersecurity, a market estimated to grow at a rapid pace from $276.63 billion in 2025, cyberattacks are not slowing down.
Increased digitalization and adoption of Industry 4.0 and 5.0 are resulting in the explosion of the global digital attack surface:
- Manufacturing: Smart factories integrate robots, sensors, MES, ERP, and supplier networks
- Pharma: Batch control systems tied to cloud analytics and regulatory portals
- Oil & Gas: Offshore rigs and refineries with hybrid IT/OT/IoT ecosystems
- Transportation: Signaling, safety, and scheduling systems connected to corporate IT
- Telecom: Core network elements linked to orchestration platforms and customer systems
This is not all. Digital industrial systems are fundamentally different from traditional IT, making it challenging to apply traditional cybersecurity solutions. The complexities include legacy OT devices with no built-in security, flat networks where one compromised device can take down an entire plant, IT–OT convergence blurring trust boundaries, ransomware and nation-state attacks targeting physical disruption (not just data), and regulatory pressure (e.g., NIS2, CISA advisories, NERC CIP, ISA/IEC 62443).
Industrial organizations must invest in OT breach ready cyber defense today. Delays can cause safety system failure, production halts, environmental damage, cascading effects on national supply chains, and even loss of life, think Colonial Pipeline, Triton/TRISIS safety controller malware, attacks on various Hospital medical systems, or NotPetya’s global manufacturing shutdowns.
Microsegmentation is Foundational
Microsegmentation is the practice of breaking the OT network into small, controlled security zones or micro-perimeters with tightly enforced communication rules on the conduits that connect them, which can be disconnected as soon as a cyberattack attempt is detected. Instead of one “big flat” OT network, you have multiple isolated zones of excellence that can only talk in pre-approved, minimal ways, in a topology illustrated in the Figure below. And this means that even if an attacker manages to beat the traditional cybersecurity controls, the attack remains confined to that specific micro perimeter.
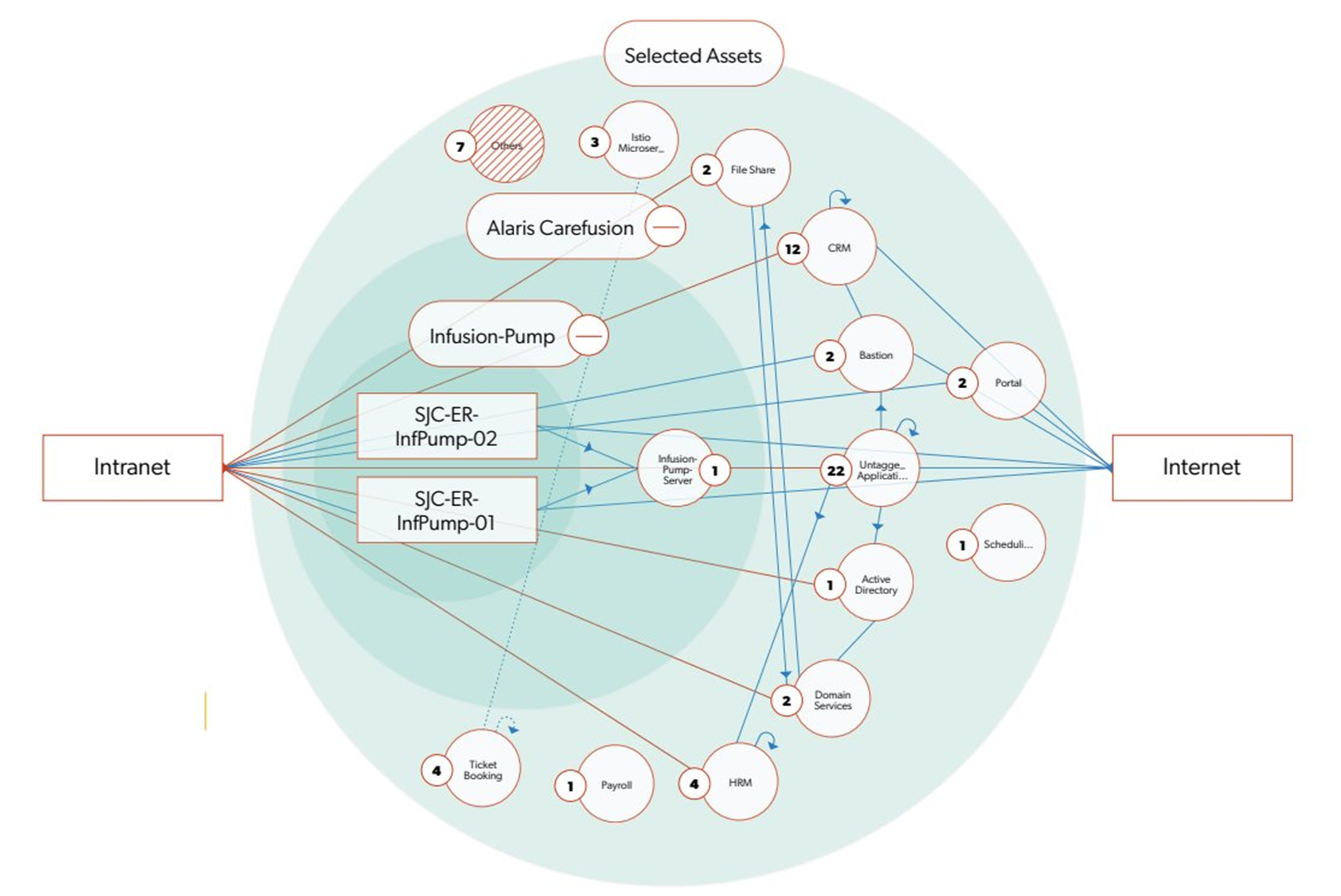
Figure: Color-coded lines indicating in-policy and out-of-policy traffic. Views can be organized by up to 20 dimensions. Users can see different views for their role.
Access Forrester Wave Report | Discover why ColorTokens was rated ‘Superior’ in OT, IoT, and Healthcare Security.
Report | Discover why ColorTokens was rated ‘Superior’ in OT, IoT, and Healthcare Security.
When deployed for breach ready cyber defense, microsegmentation can:
- Isolate safety systems from non-safety systems (TRICONEX or SIS controllers in separate, locked-down zones)
- Segment critical ICS components so that a compromise in a monitoring system doesn’t jump to control logic
- Control lateral movement, ensuring attackers can’t move from one zone to another or reach critical assets
- Protect cyber-physical systems by ring-fencing PLCs, RTUs, and SCADA servers from unnecessary access
- Enforce least privilege, only the exact devices, protocols, and ports needed for the function are allowed
- Contain breaches at the edge where IT, cloud, and industrial systems meet
There are other advantages of using microsegmentation, including a highly reduced attack surface, thus the security alerts reaching an OT cyber defense center (also called OT SOC) would become more real; a highly reduced blast radius of each digital system, thus attempts of lateral movement would become malicious much faster; and a faster mean time to respond to cyberattacks from days or hours to minutes.
Microsegmentation is Resilience Bedrock
Without microsegmentation, the consequences of a breach can be severe. One compromised laptop can pivot across the plant network. A single compromised VPN credential can open the door to human harm or ransomware or malware in quality control monitoring could jump into process control logic. Attackers can move from IT to OT via shared services (active directory, file servers, historian databases, etc.)
In the past, we’ve seen examples of attacks on OT systems including:
- Attackers attempted to poison the water supply by increasing the level of sodium hydroxide (lye) in a Florida water treatment plant in 2021.
- Attackers disrupted a pressure regulation pump and defaced a PLC-HMI system in 2023.
- A ransomware attack forced Tower Semiconductor to halt operations at some manufacturing facilities.
With microsegmentation, the attack surface shrinks dramatically, reducing threat intel overload. By blocking the lateral movement of potential breaches, the subsequent impact is limited to one zone and one micro perimeter, speeding up incident response time because compromise is localized. As a result, building cyber defense becomes scalable; once segmentation policies exist, they can be rolled out across plants, sites, and geographies. With emerging capabilities to integrate with existing EDR, retrofitting cybersecurity procedures to establish a “breach ready” cyber defense strategy for OT systems becomes a one-day activity.
Today, OT breach ready cyber defense is not optional, it is mission-critical for every industrial organization, ensuring human and societal safety and allowing them to continue operating critical parts of their supply chain. This allows them to operate in a regulatory-heavy environment and afford days or weeks of acceptable downtime in small areas.
Microsegmentation serves as the first step of OT breach readiness. By creating a structure where cyberattacks can be immediately contained, unaffected areas can reliably continue normal operations while the effects of the breach are managed quicker and with higher efficacy. Without it, every other cyber control is weakened by an attacker’s ability to roam freely.
Connect with our experts to strengthen your OT security and contain breaches before they spread.
This article was originally published on Circuit Cellar.
The post What is OT Breach Ready Cyber Defense? appeared first on ColorTokens.
*** This is a Security Bloggers Network syndicated blog from ColorTokens authored by Agnidipta Sarkar. Read the original post at: https://colortokens.com/blogs/ot-security-breach-ready-microsegmentation/
如有侵权请联系:admin#unsafe.sh
