
微软在2025年10月的补丁星期二发布了史上最大规模的安全更新,修复了167个CVE漏洞,包括三个零日漏洞。同时,Windows 10正式结束支持服务。 2025-10-14 18:3:40 Author: www.tenable.com(查看原文) 阅读量:82 收藏
October 14, 2025
7 Min Read

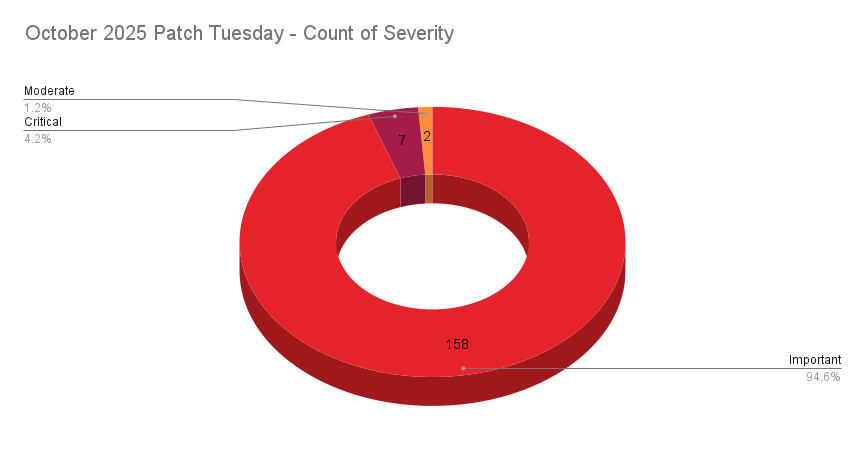
- 7Critical
- 158Important
- 2Moderate
- 0Low
Microsoft addresses 167 CVEs in its largest Patch Tuesday to date, including three zero-day vulnerabilities, two of which were exploited in the wild.
Microsoft patched 167 CVEs in its October 2025 Patch Tuesday release, its largest Patch Tuesday release to date, with seven rated critical, 158 rated important, and two rated moderate. Our counts omitted 27 vulnerabilities, including 14 Chromium CVEs, three MITRE CVEs, one GitHub CVE, one CERT/CC CVE, and eight cloud CVEs that Microsoft published advisories for on October 9.
This month’s update includes patches for:
- .NET
- .NET,.NET Framework, Visual Studio
- Active Directory Federation Services
- Agere Windows Modem Driver
- ASP.NET Core
- Azure Connected Machine Agent
- Azure Entra ID
- Azure Local
- Azure Monitor
- Azure Monitor Agent
- Azure PlayFab
- Confidential Azure Container Instances
- Connected Devices Platform Service (Cdpsvc)
- Copilot
- Data Sharing Service Client
- Inbox COM Objects
- Internet Explorer
- JDBC Driver for SQL Server
- Microsoft Brokering File System
- Microsoft Configuration Manager
- Microsoft Defender for Linux
- Microsoft Exchange Server
- Microsoft Failover Cluster Virtual Driver
- Microsoft Graphics Component
- Microsoft Office
- Microsoft Office Excel
- Microsoft Office PowerPoint
- Microsoft Office SharePoint
- Microsoft Office Visio
- Microsoft Office Word
- Microsoft PowerShell
- Microsoft Windows
- Microsoft Windows Search Component
- Microsoft Windows Speech
- Network Connection Status Indicator (NCSI)
- NtQueryInformation Token function (ntifs.h)
- Remote Desktop Client
- Software Protection Platform (SPP)
- Storport.sys Driver
- Virtual Secure Mode
- Visual Studio
- Windows Ancillary Function Driver for WinSock
- Windows Authentication Methods
- Windows BitLocker
- Windows Bluetooth Service
- Windows Cloud Files Mini Filter Driver
- Windows COM
- Windows Connected Devices Platform Service
- Windows Core Shell
- Windows Cryptographic Services
- Windows Device Association Broker service
- Windows Digital Media
- Windows DirectX
- Windows DWM
- Windows DWM Core Library
- Windows Error Reporting
- Windows ETL Channel
- Windows Failover Cluster
- Windows File Explorer
- Windows Health and Optimized Experiences Service
- Windows Hello
- Windows High Availability Services
- Windows Hyper-V
- Windows Kernel
- Windows Local Session Manager (LSM)
- Windows Management Services
- Windows MapUrlToZone
- Windows NDIS
- Windows NTFS
- Windows NTLM
- Windows PrintWorkflowUserSvc
- Windows Push Notification Core
- Windows Remote Access Connection Manager
- Windows Remote Desktop
- Windows Remote Desktop Protocol
- Windows Remote Desktop Services
- Windows Remote Procedure Call
- Windows Resilient File System (ReFS)
- Windows Resilient File System (ReFS) Deduplication Service
- Windows Routing and Remote Access Service (RRAS)
- Windows Server Update Service
- Windows SMB Client
- Windows SMB Server
- Windows SSDP Service
- Windows StateRepository API
- Windows Storage Management Provider
- Windows Taskbar Live
- Windows USB Video Driver
- Windows Virtualization-Based Security (VBS) Enclave
- Windows WLAN Auto Config Service
- Xbox
- XBox Gaming Services
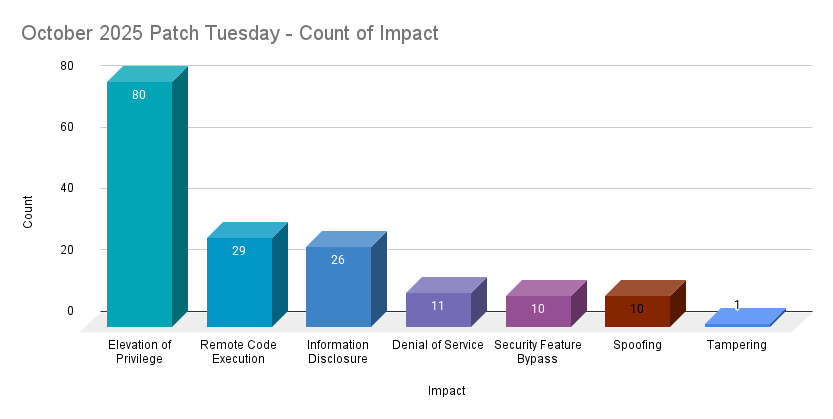
Elevation of Privilege (EoP) vulnerabilities accounted for 47.9% of the vulnerabilities patched this month, followed by Remote Code Execution (RCE) vulnerabilities at 17.4%.
CVE-2025-24052 and CVE-2025-24990 | Windows Agere Modem Driver Elevation of Privilege Vulnerabilities
CVE-2025-24052 and CVE-2025-24990 are EoP vulnerabilities in the third party Agere Modem driver. Both CVEs were assigned CVSSv3 scores of 7.8 and rated as important. Microsoft reports that CVE-2025-24990 has been exploited in the wild and CVE-2025-24052 was disclosed prior to a patch being made available. Successful exploitation would allow an attacker to gain administrator privileges on an affected system.
The ltmdm64.sys driver has historically shipped natively with supported Windows operating systems, but will no longer be supported following the October update. Microsoft notes, that ltmdm64.sys-dependent hardware will no longer work on Windows, and recommends users remove existing dependencies.
CVE-2025-59230 | Windows Remote Access Connection Manager Elevation of Privilege Vulnerability
CVE-2025-59230 is an EoP vulnerability affecting Windows Remote Access Connection Manager. According to Microsoft, this vulnerability has been exploited in the wild. It was assigned a CVSSv3 score of 7.8 and is rated as important. Exploitation of this vulnerability involves improper access control in Windows Remote Access Connection Manager and could allow a local attacker to gain SYSTEM privileges.
Including CVE-2025-59230, there have been 22 reported and patched vulnerabilities for the Windows Remote Access Connection Manager service (RasMan) since January 2022. CVE-2025-59230 is the first reported RasMan CVE to be exploited as a zero-day.
CVE-2025-59287 | Windows Server Update Service (WSUS) Remote Code Execution Vulnerability
CVE-2025-59287 is a RCE in the Windows Server Update Service (WSUS). It was assigned a CVSSv3 score of 9.8 and rated critical. It has been assessed as “Exploitation More Likely” according to Microsoft’s Exploitability Index. An attacker could exploit this vulnerability to gain RCE by sending a crafted event that leads to a deserialization of untrusted data.
This is just the third WSUS vulnerability patched as part of Microsoft Patch Tuesday since 2023, when Microsoft patched two WSUS EoP vulnerabilities (CVE-2023-32056, CVE-2023-35317) in the July 2023 Patch Tuesday, but the first RCE and to be assessed as more likely to be exploited.
CVE-2025-59227, CVE-2025-59234 | Microsoft Office Remote Code Execution Vulnerability
CVE-2025-59227 and CVE-2025-59234 are RCE vulnerabilities in Microsoft Office. Both vulnerabilities were assigned a CVSSv3 score of 7.8, rated critical and assessed as “Exploitation Less Likely.” An attacker could exploit these flaws through social engineering by sending the malicious Microsoft Office document file to an intended target. Successful exploitation would grant code execution privileges to the attacker.
Despite being flagged as “Less Likely” to be exploited, Microsoft notes that the Preview Pane is an attack vector for both CVEs, which means exploitation does not require the target to open the file.
CVE-2025-55680 | Windows Cloud Files Mini Filter Driver Elevation of Privilege Vulnerability
CVE-2025-55680 is an EoP vulnerability in the Windows Cloud Files Mini Filter Driver. It was assigned a CVSSv3 score of 7.8, rated important and assessed as “Exploitation More Likely.” A local, authenticated attacker would need to win a race condition in order to exploit this vulnerability. Successful exploitation would allow the attacker to elevate to SYSTEM privileges.
This is the 17th vulnerability in the Windows Cloud Files Mini Filter Driver since 2022. Microsoft patched two in 2022, six in 2023, six in 2024, and three in 2025. As part of its November 2023 Patch Tuesday release, Microsoft patched CVE-2023-36036, another EoP flaw, that was exploited in the wild as a zero-day.
Windows 10 End of Support
As of October 14, Windows 10 has reached its end of support. This means that no new security updates will be released for Windows 10 without being enrolled in the Extended Security Updates (ESU) program. To identify unsupported versions of Windows 10, customers can use plugin ID 192814.
Additionally, Long-Term Servicing Branch (LTSB) support for Windows 10 Enterprise 2015 LTSB and Windows 10 IoT Enterprise LTSB 2015 also ended as of October 14. Plugins to identify these versions are as follows:
Additional Microsoft Products End of Support
As of October 14, several Microsoft Products have reached end of support or extended support. Since these products will no longer receive security updates, we recommend upgrading to supported versions as soon as possible.
- Exchange Server 2016
- Exchange Server 2019
- Outlook 2016
- Skype for Business Server 2015
- Skype for Business 2016
- Skype for Business Server 2019
- Windows 11 Enterprise and Education Version 22H2
- Windows 11 IoT Enterprise Version 22H2
Tenable Solutions
A list of all the plugins released for Microsoft’s October 2025 Patch Tuesday update can be found here. As always, we recommend patching systems as soon as possible and regularly scanning your environment to identify those systems yet to be patched.
For more specific guidance on best practices for vulnerability assessments, please refer to our blog post on How to Perform Efficient Vulnerability Assessments with Tenable.
Get more information
- Microsoft's October 2025 Security Updates
- Tenable plugins for Microsoft October 2025 Patch Tuesday Security Updates
Join Tenable's Research Special Operations (RSO) Team on Tenable Connect and engage with us in the Threat Roundtable group for further discussions on the latest cyber threats.
Learn more about Tenable One, the Exposure Management Platform for the modern attack surface.

Research Special Operations
The Research Special Operations (RSO) team serves as Tenable’s Forward Logistics Element in the threat landscape, providing customers with the analyses and contextualized exposure intelligence required to manage risks to critical business assets. With over 150 years of collective expertise, this hand-picked group of world-class security researchers is united with one mission: to cut through the noise and deliver critical intelligence about the most dangerous cyber threats emerging right now. Uniting the missions of the Tenable Security Response, Zero-Day Research, and Decision Science Operations teams, RSO disseminates timely, accurate, and actionable information about the latest threats and exposures.
- Exposure Management
- Vulnerability Management
Cybersecurity news you can use
Enter your email and never miss timely alerts and security guidance from the experts at Tenable.
如有侵权请联系:admin#unsafe.sh