VMRay UniqueSignal与OpenCTI整合,为安全团队提供高保真恶意软件情报,解决指标过载、缺乏上下文、追踪困难等问题。通过实时数据和可视化工具,提升威胁检测、响应效率及决策能力。 2025-10-13 14:17:59 Author: www.vmray.com(查看原文) 阅读量:136 收藏
TL;DR: If you’re tracking fast-moving malware (think infostealers, loaders, cryptominers) and drowning in indicators, VMRay UniqueSignal + OpenCTI gives you high-fidelity, malware-centric context you can act on—without building a heavy/spaghetti enrichment pipeline. This post lays out 5 real problems security teams face and how this integration solves them, with concrete use cases.
Why this matters
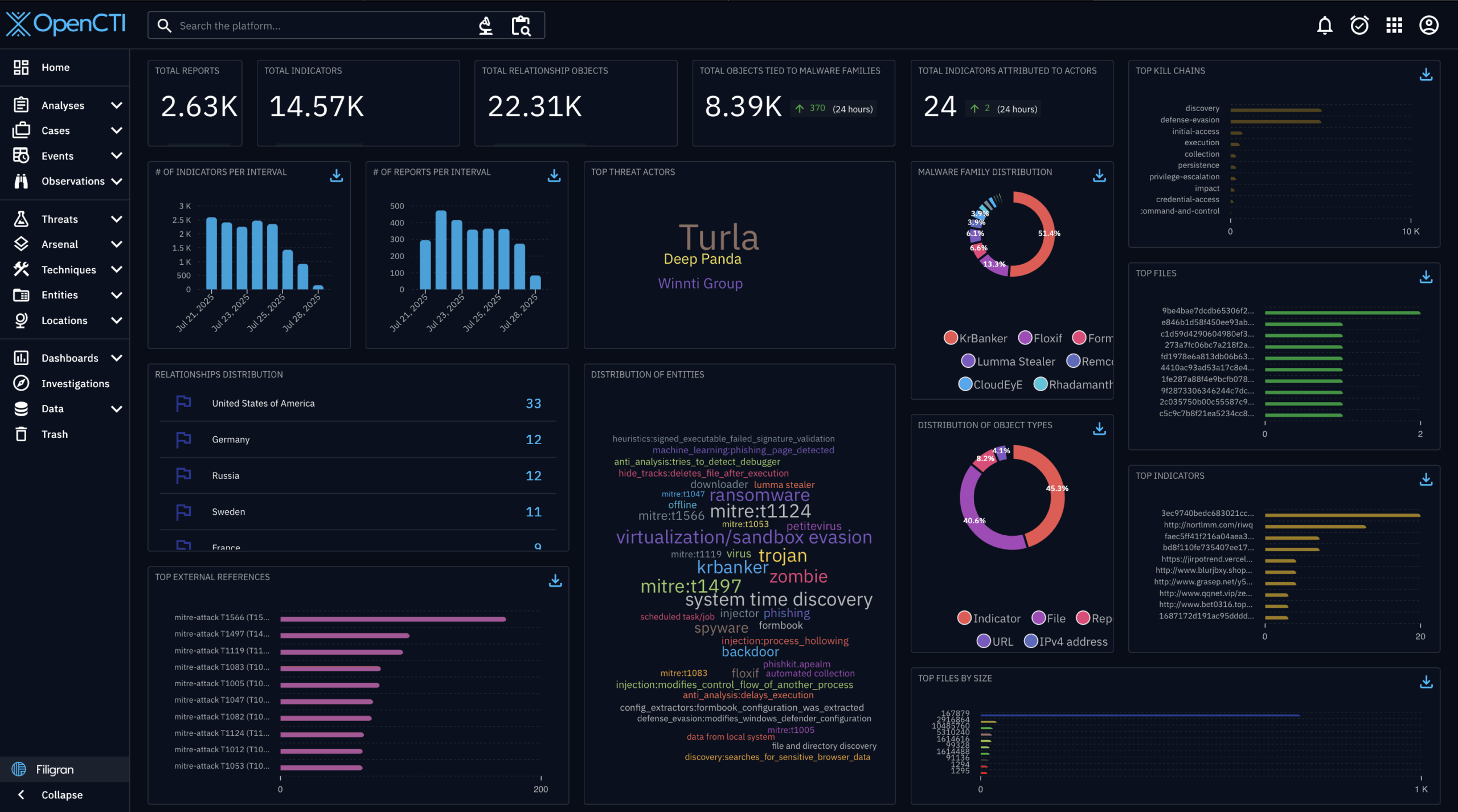
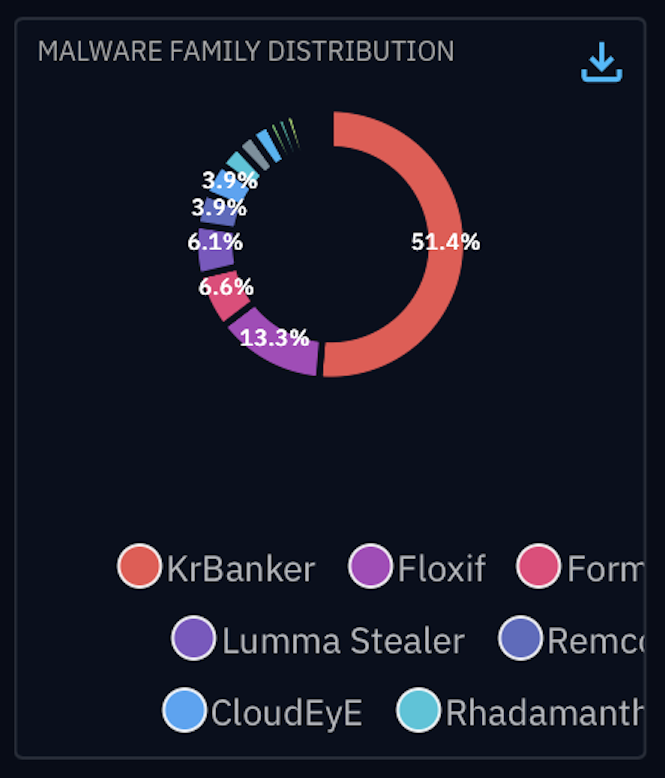
Malware tracking is critical but resource-intensive. Families morph, infrastructure flips, and flat IOCs age out fast. UniqueSignal was built for this reality: it’s a malware-centric feed sourced from real detonations in the evasion-resistant VMRay Sandbox, delivered as STIX/TAXII 2.1, and designed for accuracy, uniqueness, and timeliness. When you ingest it via OpenCTI, you get dashboards your analysts can actually use—trends, detonation timelines, victimology and targeted-industry tags, and attack-infrastructure labels—so the SOC can move from “more indicators” to decisions.
The integration at a glance
- Feed: VMRay UniqueSignal (malware-focused, STIX/TAXII 2.1).
- Platform: OpenCTI (dashboard-centric visualization; no live pivots required).
- What you see: Current malware families, related infra (C2/IP/FQDN), ATT&CK technique coverage, high-reliability clues on victimology, targeted-industry, and infrastructure labels.
- How it fits: Coexists with your TIP and MISP—OpenCTI is the operational workbench&view, UniqueSignal is the high-fidelity malware data lake feeding your downstream controls.
5 problems this solves
1) Indicator overload & stale intel
The problem: SOC/SIEM hunting queues swell with aged-out IOCs and false positives.
How it helps: UniqueSignal arrives current and confidence-scored; OpenCTI visualizes first-seen and aging so you retire dead infra quickly.
Use it for:
- Push curated, auto-aging watchlists to SIEM/EDR and web proxies for proactive detection and blocking.
- Cut FPs on fast-cycling C2 used by loaders and trojans.
2) No context to prioritize
The problem: TI feeds often tell you what, not who/why/where.
How it helps: UniqueSignal is pulled with various behavioral context, relevant labels and relationship objects; OpenCTI makes the relevance visible and useful.
Use it for:
- Monitoring behavioral markers (VMRay Threat Identifiers – VTIs) to see most observed evasion techniques
- Aim hunts at infostealer (e.g. Lumma, Vidar) campaigns that actually match your threat model.
3) Malware family tracking is heavy
The problem: Keeping pace with evolving families eats senior CTI and malware analyst time.
How it helps: UniqueSignal is derived from real samples and kept fresh; OpenCTI dashboards surface trending families, new infra, ATT&CK coverage—ready to brief.
Use it for:
- A weekly Malware Watch: top families, new infra to block.
- Rapid incident response with rich context attached to the atomic indicators (malware-specific intel pack)
4) Enrichment pipelines slow time-to-action
The problem: Stitching “who/where/how” across tools delays decisions.
How it helps: UniqueSignal brings the context to take you to the top of Pyramid of Pain; OpenCTI becomes the place to automate, consume and publish SOC-ready lists—no bespoke spaghetti.
Use it for:
- Alert enrichment with clear confidence.
- Faster, more consistent triage and escalation across shifts.

5) Proving impact to stakeholders
The problem: Hard to show what changed in the threat landscape and why it matters.
How it helps: OpenCTI visualizations + UniqueSignal timeliness let you report trend lines (e.g. top families, top threat actors), ATT&CK coverage, and blocked/retired infra by industry/geo.
Use it for:
- Quarterly CTI readouts: “Top 5 malware targeting our industry” + blocked infra + reduced time to respond.
- Budget justification: measurable drop in infostealer-led escalations.
See it in action & Join our Webinar
We’re hosting a practical session that focuses on operational value—no boring mechanics—just what your analysts will see and use on day one.
Webinar: Operational Threat Intel Wins with VMRay UniqueSignal × Filigran OpenCTI
When: Tuesday, 21 October 2025 · 10:00 am Eastern Time
Note for OpenCTI users: OpenCTI customers are eligible for a 60-day free trial of UniqueSignal to replicate the dashboards in your own environment.
👉 Register here: https://zoom.us/webinar/register/1217595007403/WN_3TS-xlXpRsuPxxwfTTcJkA
Bottom line: With UniqueSignal × OpenCTI, you move from “more IOCs” to actionable malware context—so your SOC blocks earlier, hunts smarter, and wastes less time.
如有侵权请联系:admin#unsafe.sh