凭证收集攻击通过钓鱼、恶意软件等手段窃取用户认证信息,可能导致数据泄露、财务损失和声誉损害。企业和个人需加强安全意识培训、使用多因素认证、避免重复密码,并警惕可疑邮件和链接。 2025-10-10 06:26:51 Author: securityboulevard.com(查看原文) 阅读量:11 收藏
Key Takeaways
- Credential harvesting targets usernames, passwords, and security tokens through phishing, malware, and fake login pages.
- A single compromised account can lead to data breaches, financial loss, and long-term reputational damage.
- Organizations must implement email authentication protocols, MFA, security training, and proactive monitoring.
- Individuals should use unique passwords, enable multi-factor authentication, and scrutinize all digital communications.
A single stolen password can bring down an entire organization. The 2024 Change Healthcare breach proved this all too well: attackers gained access through one low-level customer support account in a credential-harvesting phishing scheme, setting off a chain reaction that disrupted the entire U.S. healthcare system and exposed the personal information of 192.7 million individuals.
What makes credential harvesting so dangerous is how deceptively simple it can begin, yet the fallout can cripple critical infrastructure, drain billions in losses, and erode trust on a massive scale.
What Is Credential Harvesting?
Credential harvesting is a cyberattack method in which malicious actors steal authentication details such as usernames, passwords, multi-factor authentication (MFA) tokens, and session cookies. With these stolen credentials, attackers can impersonate legitimate users, infiltrate accounts and networks, or sell the data on underground markets for further exploitation.
Unlike brute-force attacks that rely on guessing passwords, credential harvesting relies on deception. Victims are tricked into handing over their login information, often through fake login pages or malicious software that quietly captures input. Because the credentials are real, attackers can bypass many security controls and operate unnoticed inside an organization’s environment. Once a valid account is compromised, cybercriminals gain a powerful foothold to steal sensitive data, commit fraud, deploy ransomware, or launch further attacks against partners and customers.
Some of the most frequent targets include:
- Corporate email accounts and cloud platforms
- Financial portals and payment systems
- Social media and personal email accounts
- VPNs and remote access logins
- Administrative or privileged user accounts
How Credential Harvesting Attacks Work
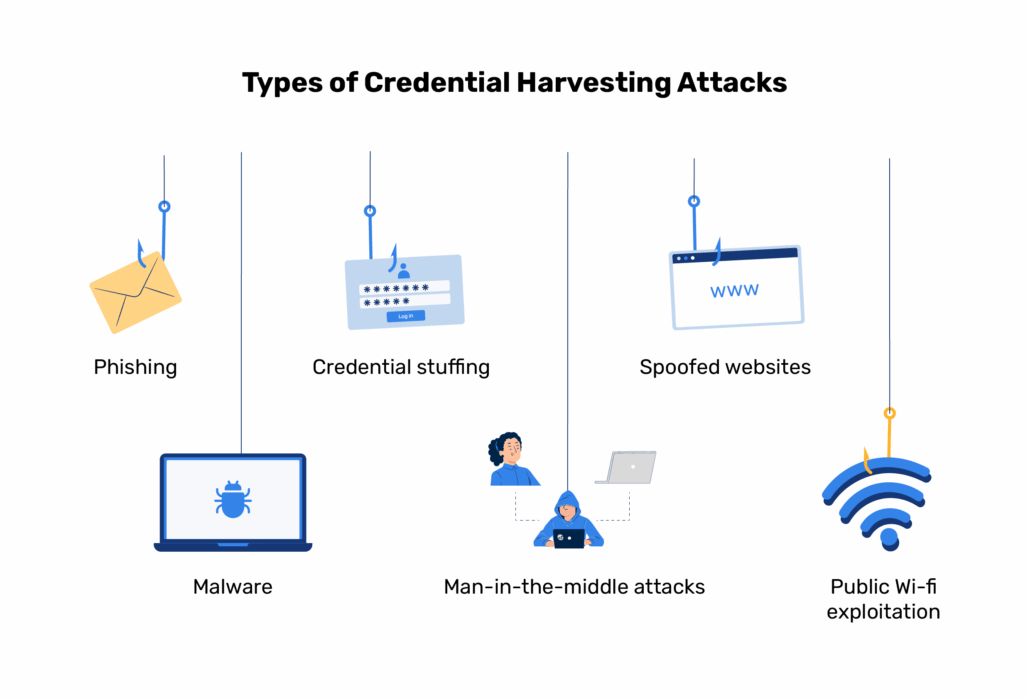
Cybercriminals use multiple sophisticated techniques to steal credentials. Understanding these methods is the first step in building effective defenses. Some of the most common methods used for this kind of attack include:
Phishing
Attackers send fraudulent emails or messages that appear as if they come from trusted sources, such as banks, IT departments, or popular services. These messages create urgency and direct victims to fake login pages that capture entered credentials. Phishing emails often use social engineering tactics to bypass user skepticism.
Malware
Malicious software like keyloggers, information stealers, and trojans is secretly installed on devices through infected email attachments, compromised websites, or software vulnerabilities. Once active, this malware captures every keystroke, including passwords, and transmits them to attackers. Different types of malware serve different purposes in credential theft operations.
Spoofed websites
Attackers create nearly identical copies of legitimate login pages with URLs that differ by only a character or two. Unsuspecting users enter their credentials, which are immediately captured and stored by the attacker while often being forwarded to the real site to avoid suspicion.
Credential stuffing
Cybercriminals use automated bots to test large databases of previously stolen username-password combinations across hundreds of websites. Because many users reuse the same password across multiple platforms, attackers can often gain access to multiple accounts using credentials stolen from just one breach.
Man-in-the-Middle (MITM) attacks
In MITM attacks, attackers position themselves between a user and a website, intercepting all data transmitted between them—including login credentials. This technique is especially effective on unsecured public Wi-Fi networks, where attackers can easily monitor unencrypted traffic.
Public Wi-Fi exploitation
Using unsecured public Wi-Fi networks makes users highly vulnerable to interception attacks. Cybercriminals on the same network can use packet-sniffing tools to capture login credentials, session tokens, and other sensitive data transmitted without proper encryption.
Risks of Credential Harvesting
The impact of stolen credentials rarely stops at the first compromised account. What begins with a single username and password can quickly spiral into large-scale breaches, financial losses, and reputational harm that organizations may struggle to recover from for years.
When attackers gain access to corporate accounts, the consequences can be wide-ranging and extremely costly. Typically, the consequences include:
- Data breaches: Stolen credentials provide attackers with legitimate access to systems, allowing them to extract customer data, intellectual property, financial records, and confidential communications
- Financial loss: Direct theft, fraudulent transactions, ransom payments, incident response costs, legal fees, and regulatory fines can total millions
- Operational disruption: Compromised systems may need to be taken offline for investigation and remediation, halting business operations and productivity
- Reputational damage: Loss of customer trust, negative media coverage, and competitive disadvantage can have long-term impacts on brand value and customer retention
- Compliance violations: Failure to protect credentials can result in violations of GDPR, HIPAA, PCI DSS, and other regulatory frameworks, leading to significant penalties
On a personal level, stolen credentials can open the door to:
- Identity theft: Attackers can use stolen credentials to open fraudulent accounts, apply for loans, or commit crimes in your name
- Unauthorized financial transactions: Access to banking and payment accounts enables direct theft of funds
- Account lockouts: Attackers often change passwords immediately after gaining access, locking legitimate users out of their own accounts
- Privacy violations: Personal communications, photos, and sensitive documents can be accessed, leaked, or used for blackmail
- Cascading compromises: Stolen credentials from one account are used to access others, especially when passwords are reused
Signs of a Credential Harvesting Attack
Detecting credential harvesting early is often the difference between a minor scare and a full-scale breach. Because attackers use deception to blend in with normal communications, knowing the warning signs is critical for stopping them before they gain access to sensitive systems or personal accounts.
Email and message red flags
Suspicious emails and text messages remain the most common vehicle for credential theft. Be alert for:
- Urgent language demanding immediate action (“Your account will be suspended in 24 hours!”)
- Generic greetings (“Dear Customer” instead of your name)
- Grammatical errors and awkward phrasing
- Sender addresses that don’t match the claimed organization
- Requests for credentials, payment information, or personal data via email
- Unexpected password reset requests or multi-factor authentication codes you didn’t initiate
URL and website indicators
Fake login pages are often carefully designed to mimic legitimate sites, but they leave subtle clues behind. Warning signs include:
- Misspelled domain names or unusual extensions (.co instead of .com)
- Missing HTTPS encryption (no padlock icon in the browser address bar)
- Visual inconsistencies compared to the legitimate website
- Pop-up login windows appearing unexpectedly
- Browser warnings about insecure or suspicious sites
Account activity warnings
Once credentials have been stolen, unusual account behavior is often the first indicator. Watch for:
- Login alerts from unfamiliar locations or devices
- Password reset emails you didn’t request
- Notifications of account changes you didn’t make
- Unexpected failed login attempts
- Strange activity in your sent folder or communication history
- Missing emails or unusual account behavior
If you notice any of these signs, act immediately: change your passwords, enable multi-factor authentication if it’s not already active, and report the incident to your IT security team or the affected service provider. Quick action can prevent data breaches from escalating.
How to Prevent Credential Harvesting
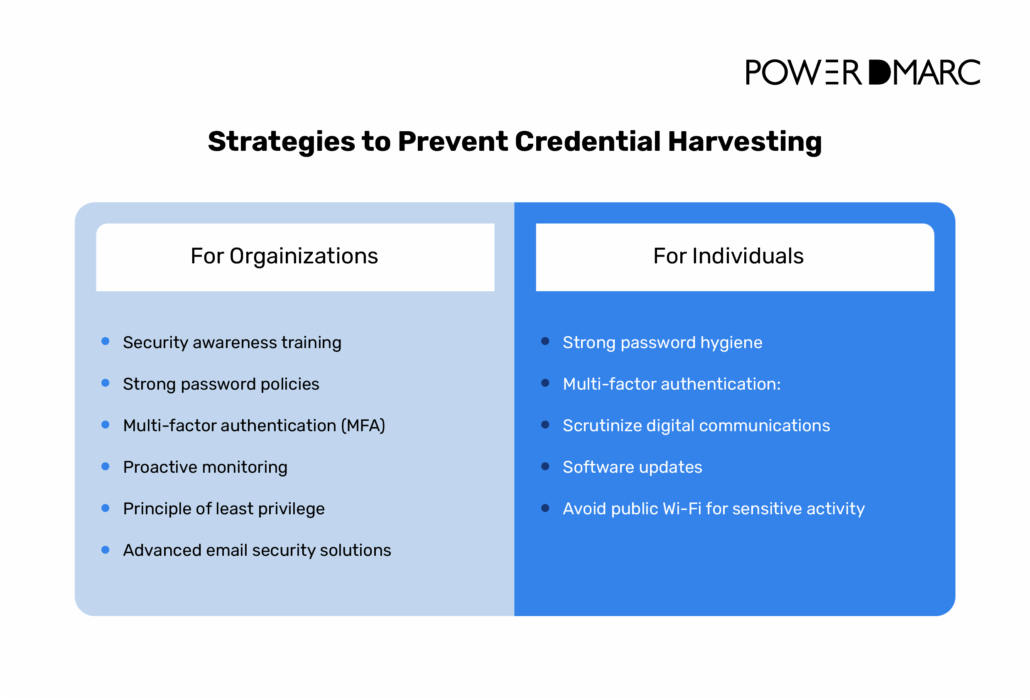
Prevention of credential harvesting calls for a layered approach to cybersecurity that combines technology, processes, and human awareness. Different strategies apply to organizations and individuals, but all are essential.
For organizations
Effective organizational defense starts with recognizing that credential protection is a shared responsibility across security teams, IT infrastructure, and every employee. The following strategies create overlapping layers of defense that make credential harvesting exponentially more difficult.
Security awareness training
Regular training helps employees recognize and report social engineering and phishing attacks before they succeed. Organizations should conduct phishing simulations to test employee readiness and reinforce training with real-world examples.
Strong password policies
Enforce corporate password policies that mandate complexity (minimum length, character variety), prohibit password reuse, and require regular password changes. Implement password managers at the organizational level to help employees generate and store unique, complex passwords for every system.
Multi-factor authentication (MFA)
Require MFA across all systems—especially for email, VPN, administrative accounts, and financial applications. Even if credentials are stolen, MFA provides a critical second layer of defense that prevents unauthorized access.
Proactive monitoring
Deploy security information and event management (SIEM) and intrusion detection systems (IDS) to monitor network logs and user behavior. Look for anomalies like logins from unusual locations, access attempts outside normal business hours, or rapid sequential login failures across multiple accounts.
Principle of least privilege
Grant employees only the minimum access levels necessary to perform their job functions. This security concept limits the potential damage of any single compromised account by restricting what an attacker can access or modify.
Advanced email security solutions
Deploy dedicated email security platforms designed to automatically detect and block malicious emails, attachments, and links before they reach employees. Email authentication protocols like DMARC prevent attackers from spoofing your domain and impersonating your organization in phishing campaigns. PowerDMARC’s DMARC Record Checker helps you verify your email authentication configuration and identify vulnerabilities.
For individuals
Individual users are often the first, and sometimes only, line of defense against credential harvesting. These proactive habits significantly reduce your personal risk exposure.
Strong password hygiene
Use a unique and complex password for every online account. This prevents one breach from compromising multiple accounts. Password managers generate and securely store complex passwords, removing the burden of memorization while dramatically improving security.
Multi-factor authentication (MFA)
Enable MFA wherever available—especially for email, banking, social media, and any account containing sensitive information. MFA requires a second verification factor (typically a code from an authenticator app) after entering your password, making unauthorized access extremely difficult even if your password is stolen.
Scrutinizing digital communications
Before clicking any link or entering credentials, verify sender authenticity. Hover over links to preview the actual URL, check sender email addresses carefully for subtle misspellings, and be skeptical of messages that create false urgency. When in doubt, navigate to the website directly by typing the URL rather than clicking email links.
Software updates
Regularly update your devices, operating systems, browsers, and applications. Software updates frequently contain critical security patches that fix known vulnerabilities attackers tend to exploit in order to install malware and steal credentials. Enable automatic updates whenever possible.
Avoid public Wi-Fi for sensitive activities
Never access banking, email, or other sensitive accounts over unsecured public Wi-Fi. If you must use public networks, use a reputable VPN (Virtual Private Network) to encrypt your traffic and protect credentials from interception.
Stay Ahead of Credential Harvesters
Credential harvesting attacks continue to evolve, but the fundamentals of defense remain consistent: combine technical controls with human awareness, implement multi-layered security, and maintain constant vigilance.
Organizations must prioritize email authentication protocols like DMARC, enforce MFA across all systems, and invest in ongoing security training. Individuals need to adopt strong password hygiene, enable multi-factor authentication, and critically evaluate every digital communication before taking action.
PowerDMARC’s email security platform can make all the difference for organizations seeking to prevent phishing and spoofing attacks that enable credential harvesting. Don’t wait until you’re the next headline. Take action today to protect your credentials, your data, and your organization.
Check your domain’s DMARC configuration now with our free DMARC Record Checker!
Frequently Asked Questions
How do hackers use credential stuffing to break into systems?
Hackers use automated bots to test millions of stolen username-password combinations across multiple websites, exploiting password reuse to gain unauthorized access to accounts where users haven’t created unique credentials.
How can services protect against credential stuffing?
Services can implement rate limiting on login attempts, require CAPTCHA verification, monitor for unusual login patterns, enforce strong password policies, and require multi-factor authentication to block automated credential stuffing attacks.
Is there a way to report fake credentials?
Yes! You can report phishing sites to the Anti-Phishing Working Group ([email protected]), use browser built-in phishing report features, notify the impersonated organization directly, and report fraudulent emails to your email provider’s abuse department.
*** This is a Security Bloggers Network syndicated blog from PowerDMARC authored by Milena Baghdasaryan. Read the original post at: https://powerdmarc.com/credential-harvesting/
如有侵权请联系:admin#unsafe.sh
