
文章指出,在AI时代下,API已成为AI行动的核心平台,但其安全性面临严峻挑战。报告数据显示,因API风险导致企业放缓或停止应用发布的比例高达50%,且三分之一的企业在过去一年遭遇过API相关安全事件。攻击者利用认证和自动化手段针对外部API展开攻击,主要集中在OWASP Top 10中的安全配置错误和对象级别授权漏洞。文章建议企业需加强实时API监控、完善治理框架,并提升开发者安全意识以应对AI驱动的安全威胁。 2025-10-8 12:0:3 Author: securityboulevard.com(查看原文) 阅读量:11 收藏
AI adoption has fundamentally redefined the role of APIs. They are no longer just conduits for data; they have become the “AI action plane” for autonomous systems. Every AI workflow, agent, and tool call now rides on an API, exposing a critical truth: you cannot secure AI without first securing your APIs. The H2 2025 State of API Security report reveals that this dependency is dangerously outpacing current security practices. The findings are not a future warning; they are a clear and present threat to business. Evidence shows that visibility gaps and weak governance are already hindering AI velocity, with half of all organizations having slowed or halted a new application release due to API risk, and one in three suffering an API-related security incident in the past year.

The New Attacker Playbook: Authenticated and Automated
As AI agents and protocols, such as MCP, accelerate automation, they also increase risk exposure. Our Salt Labs research confirms that attackers have adapted their playbook to this new reality, rendering traditional perimeter security irrelevant.
- The primary threat is now authenticated and internal. An astonishing 96% of attack attempts originate from authenticated entities, such as compromised users, insiders, or rogue AI agents.
- Attackers are targeting external-facing APIs and exploiting the most common weaknesses. The dominant vectors map directly to the OWASP Top 10, with Security Misconfiguration (API8) accounting for 78% of attacks and Broken Object Level Authorization (BOLA/API1) following at 10%.
In an automated environment, these issues are amplified from serious bugs into opportunities for systemic agent abuse. Authentication alone will not save you.
The AI Imperative: Building on an Unstable Foundation
The push toward AI is fueling this trend. Organizations are rapidly expanding their API portfolios to support key AI initiatives, such as machine learning and autonomous agents. Adoption is already widespread, with nearly two-thirds of organizations now using Generative AI (GenAI) for at least some of their API development.
The danger is that this rapid, AI-driven development is being built on a foundation with the same critical security gaps that have been seen all year.
- A massive 80% of organizations still lack continuous, real-time API monitoring.
- Confidence in API inventories remains dangerously low, with only a small fraction of organizations (19%) stating they are “very confident” in the accuracy of their inventories.
The Confidence Crisis: Underprepared for AI-Driven Threats
While organizations are embracing GenAI for development, they are simultaneously unprepared for the risks it introduces. A clear majority now perceives GenAI as a growing security concern. Their top fears center on a lack of control over the security of AI models and the difficulty of securing AI-generated code.
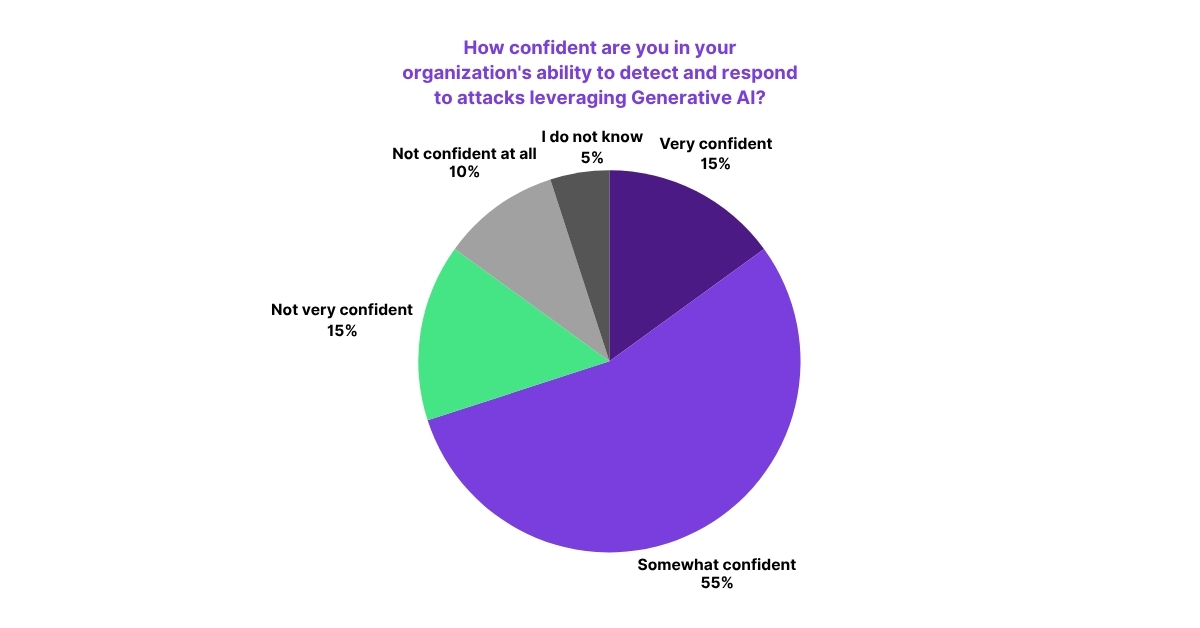
This anxiety is justified. There is a significant readiness gap when it comes to defense, with only 15% of security professionals feeling “very confident” in their ability to detect and respond to attacks leveraging GenAI.
A New Playbook for the AI Era
The AI Agent Economy requires a new security playbook—one that is proactive, comprehensive, and built for the speed of automated innovation.
- Mandate a Real-Time API Inventory: You cannot govern what you cannot see. With GenAI poised to dramatically increase the scale of API creation and use, a dynamic, automated inventory is a foundational control to mitigate the risk of shadow and undocumented APIs.
- Shift Focus from Authentication to Authorization: Since the vast majority of attacks come from authenticated sources, the focus must shift to what users can do after they log in. This requires robust runtime protection, behavioral anomaly detection, and a strong posture governance model to prevent the misconfigurations that attackers are actively exploiting.
- Govern GenAI, Don’t Just React to It: With most organizations already using or planning to use GenAI, security must move from reactive code reviews to proactive governance. This includes establishing formal frameworks for secure AI adoption, mandating developer training, and using specialized AI security tools.
- Measure Security’s ROI as an Innovation Enabler: The value of API security in the AI era lies in its ability to enable the business to move fast and safely. Leading organizations measure ROI through metrics like an improved compliance posture, cost savings from breach prevention, and increased developer productivity.
Implementing this new playbook requires a clear strategy and a method to measure your progress. As outlined in Beyond the Hype: The CISO’s Playbook for Securing the Agentic Enterprise, security leaders should start by asking critical questions, such as: If our teams deploy 10 new AI agents tomorrow, how long would it take to discover the new APIs they are using?. To help answer these questions and benchmark your current capabilities, you can use the AI Agent & MCP Security Readiness Checklist to conduct a rapid assessment of your organization’s posture across discovery, governance, and threat protection.
Get the New Playbook
The AI revolution is here, and it is an API revolution. Securing your APIs is no longer just a technical task; it is the foundational action plan for your entire AI strategy and a critical requirement for complying with emerging regulations, such as the EU AI Act, and standards like ISO/IEC 42001.
Download the complete H2 2025 State of API Security Report to get the full data and insights you need to secure your innovation.
*** This is a Security Bloggers Network syndicated blog from Salt Security blog authored by Eric Schwake. Read the original post at: https://salt.security/blog/from-bottleneck-to-enabler-a-new-approach-to-api-security-in-the-age-of-ai
如有侵权请联系:admin#unsafe.sh
