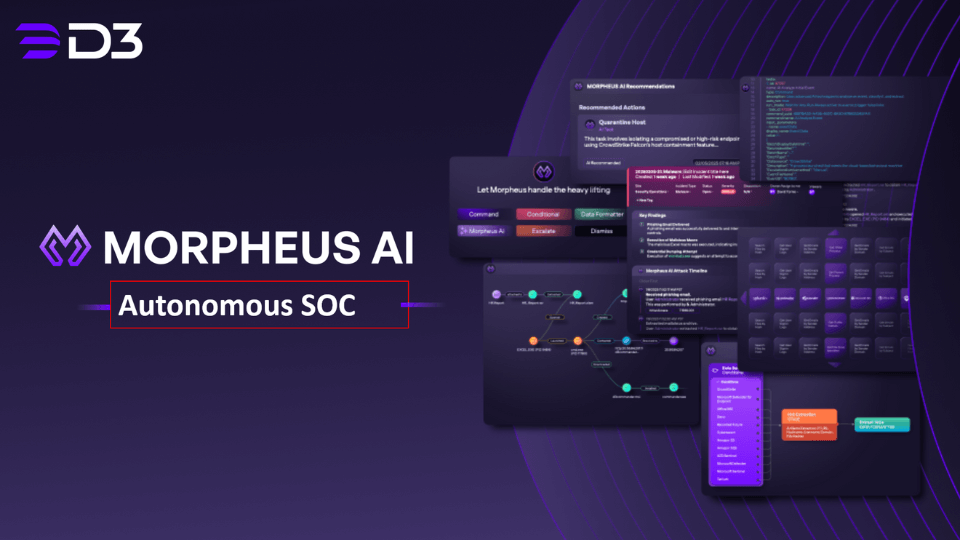
网络攻击者利用AI加速钓鱼和渗透攻击,导致警报量激增。大多数SOC团队仍依赖传统工具应对警报积压和疲劳问题。Morpheus作为D3 Security的自主AI SOC解决方案,通过统一数据模型、自动调查和跨栈关联功能,帮助分析人员快速处理所有警报,降低平均解决时间并提升团队效率与士气。 2025-10-7 20:4:5 Author: securityboulevard.com(查看原文) 阅读量:24 收藏
Attackers now use AI to phish, probe defenses, and move faster. Volume is up. Speed is up. Impact is up. Yet most SOCs still fight the same battle with the same tools, as backlogs grow and teams get tired, unable to investigate 40% of alerts.
Morpheus closes that gap. It’s D3 Security’s autonomous AI SOC solution that triages, investigates, and responds to every alert at machine speed. Morpheus picks up the alert, gathers context, correlates signals, and proposes action within policy. Analysts review, approve, or take over when judgment is needed. Think of it as adding 20 to 100 analyst equivalents to your team.
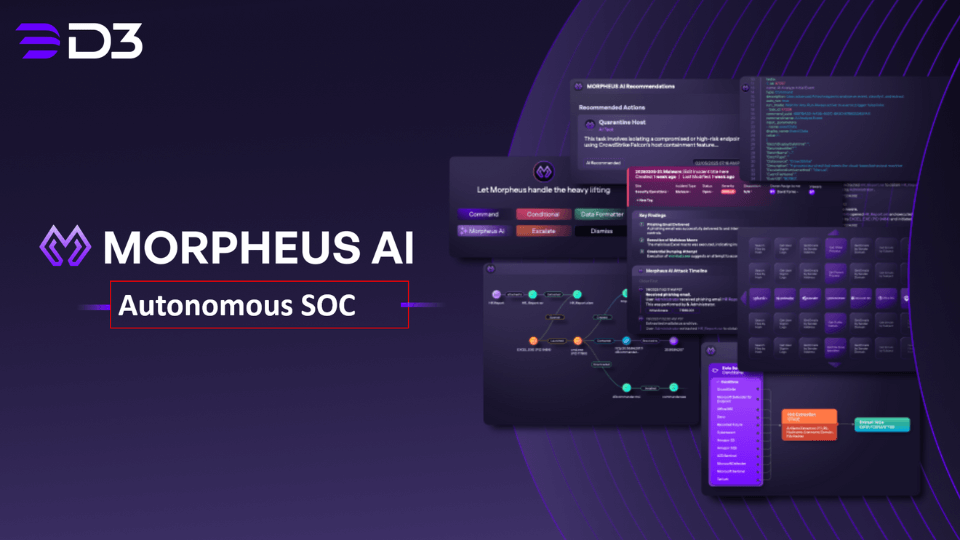
Where Traditional Tools Plateau
Alert format chaos. Alerts arrive from dozens of tools in different formats. Your SIEM uses one schema. EDR uses another. Your firewall uses a third. Analysts waste time translating between formats and stitching together context manually. Morpheus ingests alerts from any source and normalizes them into a unified data model. It enriches each alert with asset context, identity data, and threat intelligence. Investigations run at the same speed regardless of which tool generated the alert.
Detection tuning. Quality detections matter, and they need constant refinement. Analysts mute noisy rules to cope with alert volume, then miss weak but meaningful signals. Morpheus processes every alert with the same depth of investigation. It incorporates current threat intelligence and adapts its correlation logic as attack patterns evolve.
Cross-stack correlation. Most misses hide in the gray zone. One alert looks harmless. Three weak signals across identity, endpoint, and cloud tell a different story. Morpheus hunts vertically (deep within a single tool’s telemetry) and horizontally (across your entire stack). It builds high-fidelity incidents by merging related alerts and filtering out false positives. Sub-threshold alerts trigger full investigation before they turn into missed detections.
Analyst Augmentation, Not Replacement
Useful automation cuts toil and gives time back. It does the work that steals a day: pulling asset context, checking identity risk, pivoting through EDR telemetry, querying SIEMs, and building a clean narrative for review. Morpheus gives SOC teams:
- A single incident view. The system groups related alerts into cases and presents a timeline with evidence, queries, and response actions.
- Auto-updating summaries. Findings refresh as new data arrives. Handoffs stay crisp across shifts.
- Policy-based response. Routine actions execute automatically within defined guardrails. Sensitive operations require analyst approval.
- Complete audit trails. Every investigation step, data query, and response action gets logged with timestamps and outcomes.
The payoff is lower MTTR and higher morale. Morpheus AI gives SOC teams the means to become more efficient and effective in their roles with AI, rather than fearing it.
Align With Frameworks And Standards
Leaders need to show progress against accepted models. Morpheus helps.
MITRE ATT&CK. Morpheus maps observed behaviors to ATT&CK tactics and techniques during investigation. That pushes coverage higher across the framework and focuses teams on the campaign elements that cost attackers the most, based on the Pyramid of Pain model. Cross-stack correlation makes it practical to work at that level every day.
Compliance and audit readiness. Morpheus generates response playbooks that codify your standard operating procedures. It logs every investigation step, decision point, and approval. You get defensible records without extra work. Your team can answer “what did we know and when did we act” with timestamps and evidence.
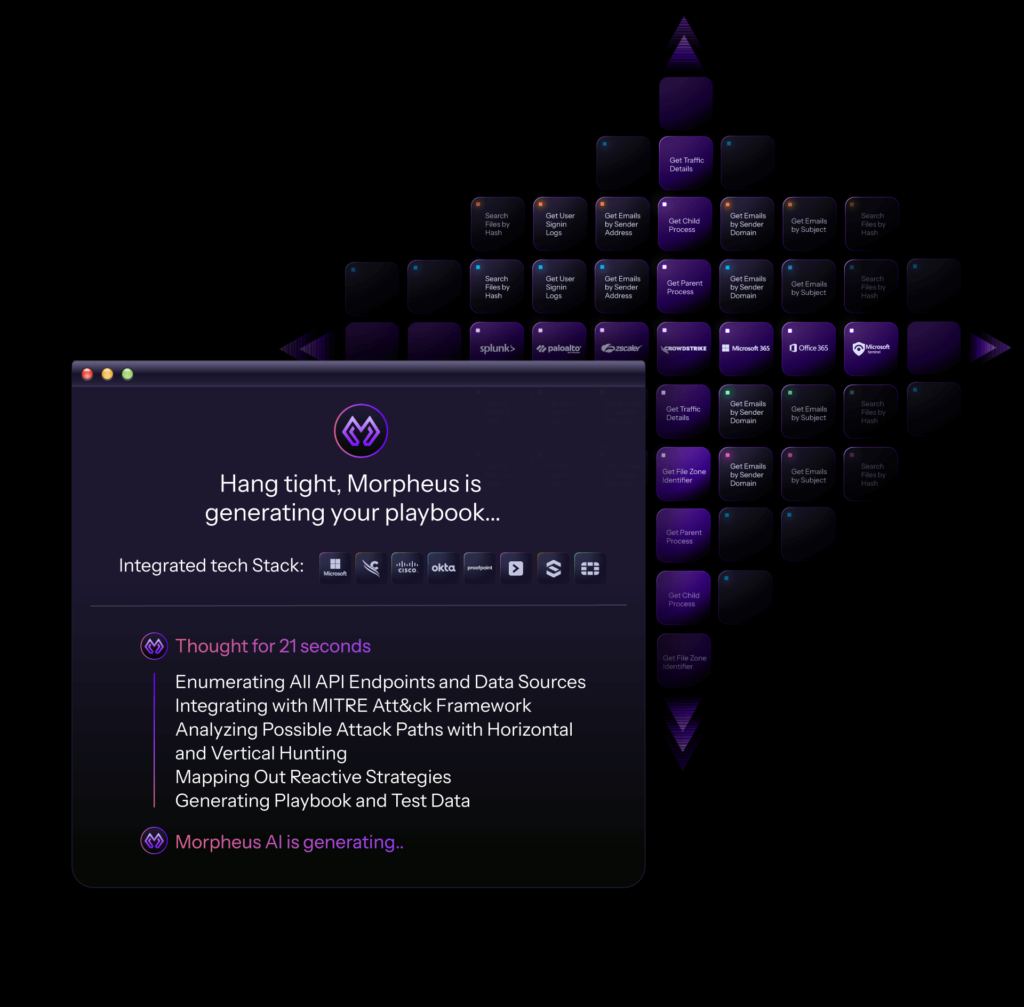
How Morpheus Handles Each Alert
Morpheus processes every alert through the same five-step investigation pattern. Each step builds on the previous one to deliver fast, accurate triage.
Normalize and Enrich
When an alert arrives through an API or webhook, Morpheus converts it into a standard format. Raw fields like “source.ip,” “src_ip,” or “sourceAddress” all become the same normalized field. This makes correlation possible across different vendor formats.
Morpheus deduplicates matching alerts to prevent analysts from seeing the same event multiple times. It attaches asset data (hostname, OS version, patch level) and identity context (user role, recent activity, group membership). It extracts all indicators: IP addresses, file hashes, domains, registry keys, and prepares them for investigation.
This step creates a structured foundation that can be queried and correlated at machine speed.
Correlate Into Incidents
Morpheus performs both vertical and horizontal hunting to build the complete attack picture.
Vertical hunting searches deep within a single data source. If an endpoint alert shows a suspicious process, Morpheus queries that endpoint’s full activity history, parent processes, child processes, network connections, file modifications, to understand what happened before and after the initial detection.
Horizontal hunting searches across the entire security stack. Morpheus checks identity systems for unusual authentication patterns, scans email logs for phishing attempts tied to the same indicators, queries firewall rules for related network traffic, and pulls cloud platform logs to see if the threat spread beyond the endpoint.
Morpheus merges related alerts into a single incident. It constructs a chronological timeline showing each step of the attack path. If five alerts from three different tools all reference the same user account within a 30-minute window, Morpheus groups them and shows how they connect.
Triage and Score
Morpheus generates an incident summary that includes:
- Timeline: Events arranged in order, from first detection to current state
- Key indicators: IP addresses, file hashes, domains, accounts involved
- Risk score: A numeric priority based on four factors
- Proposed actions: Specific response steps tailored to this incident
The risk score uses an algorithm called Incident Response Priority Score (IRPS). It weighs:
- Impact: Potential damage based on the affected asset’s criticality and the attack’s severity
- Confidence: How certain the detection is (pulled from the originating tool’s assessment)
- Contextual weight: Depth added by correlating threat intelligence, CVE data, MITRE ATT&CK mappings, and related incidents
- Mitigation status: Current containment actions (if the EDR already quarantined the file, the score adjusts down)
The score updates dynamically as new data arrives. If horizontal hunting reveals lateral movement to a domain controller, the impact score increases immediately.
Morpheus also considers historical patterns; if it has seen this combination of indicators before and marked it benign (approved user behavior, routine maintenance activity), it factors that into the current assessment.

Execute Response
Morpheus presents recommended actions based on the incident context. For a phishing-based malware incident, options might include:
- Isolate the endpoint
- Block the IP address at the firewall
- Reset the user’s password
- Quarantine the malicious file
- Disable the compromised account
If your organization configured automatic responses for certain conditions, Morpheus executes them without waiting for approval. If the incident requires human judgment; say, disabling an executive’s account or blocking traffic from a major customer’s network, Morpheus presents the response options and waits for analyst confirmation.
Every action gets logged in detail. If a response causes problems, it can trace every decision from alert to resolution and roll back the change.
Refine Correlation
Morpheus uses investigation outcomes to improve future performance. When an analyst marks an incident as a false positive and explains why (approved behavior, misconfigured detection, known test activity), it incorporates that feedback.
The next time similar alerts appear, Morpheus adjusts its correlation logic and priority scoring. It learns your environment’s normal patterns and reduces noise without requiring manual rule updates.
What To Expect From Morpheus On Day One
- Full alert coverage with sub-2-minute triage. The system investigates every alert and triages 95% in under two minutes.
- Works with your existing stack. 800-plus integrations across SIEM, EDR, identity, cloud, email, and ticketing platforms. No pipeline rebuilds or data migrations.
- Predictable pricing. Software subscription plus user count. No AI usage quotas, alert caps, execution limits, or per-workflow fees.
- Built for enterprise scale. Handles Fortune 100 alert volumes and traffic spikes without throttling or degradation.
- Transparent AI reasoning. Open YAML playbooks, logged decision steps, and human approval checkpoints keep control with your team.
- Audit-ready investigations. Evidence collection, query logs, and response timelines support regulatory reporting and incident reviews.
Ready to see Morpheus in your environment? Book a demo and give your team their time back.
The post Why SOCs Are Turning to Autonomous Security Operations: It’s Time Automation Worked For You appeared first on D3 Security.
*** This is a Security Bloggers Network syndicated blog from D3 Security authored by Alex MacLachlan. Read the original post at: https://d3security.com/blog/why-socs-need-autonomous-operations/
如有侵权请联系:admin#unsafe.sh
