2025年9月26-27日, 韩国大田NIRS数据中心因LG电池爆炸起火, 导致数百个政府系统瘫痪数周. 警方逮捕四人涉疏忽. 事件引发对朝鲜网络攻击关联的猜测. 2025-10-7 16:17:39 Author: krypt3ia.wordpress.com(查看原文) 阅读量:19 收藏
Date: 2025-10-07
Analyst: Krypt3ia
Executive Summary
Between 26–27 September 2025, a lithium-ion battery explosion at the National Information Resources Service (NIRS) data center in Daejeon crippled hundreds of South Korean government systems, forcing weeks of recovery and prompting police to charge four individuals for alleged negligence. The fire began while aging LG Energy Solution battery modules were being relocated and serviced, highlighting serious vulnerabilities in the maintenance of critical backup power infrastructure. The cascading failure underscored how intertwined technical, procedural, and vendor-level risks can bring down essential national services despite existing redundancy protocols.
Recent developments have intensified speculation that the NIRS fire may represent a continuation of North Korea’s escalating cyber campaign against South Korea. In the months preceding the incident, DPRK-linked advanced persistent threat (APT) groups such as Kimsuky, Andariel, and Lazarus dramatically increased both the frequency and technical sophistication of their intrusions into South Korean telecommunications, defense contractors, and research networks. These operations have been characterized by a growing willingness to blur the line between espionage and disruption, targeting not only data but also operational continuity. Against that backdrop, the possibility that the Daejeon data-center fire could be part of a hybrid offensive—combining physical sabotage with digital infiltration—has drawn scrutiny from intelligence analysts and policymakers alike. Although investigators have not publicly confirmed any link, the timing, strategic value, and symbolic impact of disabling core government systems align with Pyongyang’s broader doctrine of asymmetric pressure, prompting renewed debate over whether this event marks a turning point from covert collection toward overt destabilization of South Korea’s digital infrastructure.
In the aftermath, South Korea elevated its national cyber threat level to “caution,” amid fears that hostile actors might exploit the outage’s chaos for intrusion or data theft. This caution was not unfounded, LG Group and telecom networks had suffered prior compromises linked by public reporting to state-sponsored threat actors, including suspected DPRK (North Korean) APTs. While no direct evidence yet ties Pyongyang to the fire, the shared corporate ecosystem and recent cyber-espionage activity establish plausible, though unproven, grounds to treat the incident as a potential cyber-physical compromise, warranting deep forensic analysis of battery management systems (BMS), firmware, and industrial control interfaces for signs of manipulation or implanted malware.
Purpose & Methodology
This report synthesizes open reporting, industry incident patterns, and known DPRK APT TTPs to reconstruct plausible attack chains that could turn a battery maintenance event into thermal runaway via cyber means, and to hypothesize specific malware and firmware techniques that might induce overcharge or disable safety interlocks. It then translates those hypotheses into prioritized detection, forensic, and mitigation actions for government and vendor stakeholders, focusing on artifact preservation, firmware analysis, vendor device forensics, OT/IT telemetry correlation, and rapid containment measures.
The assessment draws on mainstream and industry sources, Reuters, The Guardian, DataCenterDynamics, The Korea Times, alongside technical threat reporting (Mandiant / M-Trends 2025), ICS malware analyses, and coverage of LG Group and telecom compromises; load-bearing statements are cited to those sources. The product is intended as an operational playbook: to guide immediate hunts for BMS/ESS compromise indicators, to inform medium-term OT hardening, and to support decisions about cross-sector intelligence sharing and supply-chain remediation.
Background / Context
On 26 September 2025, a lithium-ion battery fire broke out at the National Information Resources Service (NIRS) data center in Daejeon, spreading rapidly through adjacent battery racks and servers and forcing the shutdown of hundreds of critical South Korean government systems. The complex fire, driven by the volatile chemistry of lithium cells and compounded by restricted access in the server environment, took hours to extinguish and left essential digital infrastructure crippled for weeks. Police have since charged four individuals involved in maintenance work at the facility, as investigators examine whether procedural errors or equipment faults triggered the ignition.
The batteries were manufactured by LG Energy Solution, part of the broader LG Group, and several reports have pointed to outdated module vintages and a lack of modern fire-suppression systems within the rack-based UPS/ESS configuration. The event unfolded in a wider atmosphere of escalating cyber risk — major telecom operators such as LG Uplus and KT had faced compromises earlier in 2025, attributed to capable, state-linked adversaries. In response to the outage, South Korea’s government elevated its national cyber-threat level to “caution”, acknowledging that such a disruption could be exploited by hostile actors for data theft or further intrusion, underscoring the intersection of physical safety failures and cyber-espionage exposure in national infrastructure.
Timeline
In the months leading up to the September 2025 incident, South Korea’s threat landscape was already deteriorating. A series of telecom breaches and vendor exposures had revealed the extent to which regional infrastructure was being surveilled by advanced threat actors, many with suspected state affiliations, according to public reporting. These compromises weakened trust in the resilience of core service providers and exposed overlapping dependencies between government networks, critical utilities, and private-sector vendors such as those under the LG Group umbrella.
On the evening of 26 September 2025, at approximately 20:15 local time, a battery module explosion occurred during scheduled maintenance at the NIRS data center in Daejeon, igniting a fire that rapidly spread through adjacent racks and servers. By 27–30 September, extensive forensic and police investigations were underway, and four individualsassociated with on-site maintenance were booked on negligence charges. Meanwhile, the outage crippled hundreds of essential government systems and forced the elevation of South Korea’s national cyber alert level, reflecting fears that the downtime might provide a window for hostile cyber exploitation or follow-on attacks.
Threat Hypotheses
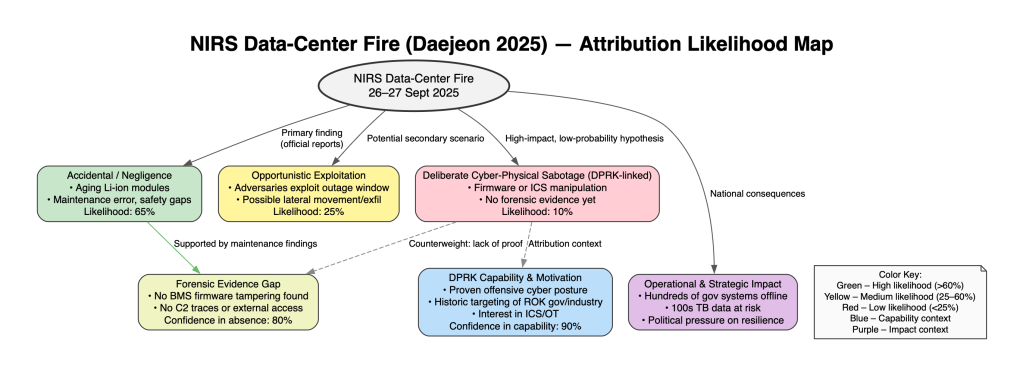
Current official reporting points to an accidental or negligence-based cause as the most likely explanation for the Daejeon data-center fire. Investigators have focused on aging battery modules, improper maintenance procedures, and insufficient safety controls as primary contributing factors. The decision to charge on-site personnel for negligence reinforces this baseline assessment, suggesting a failure of operational discipline rather than a coordinated external attack. Confidence in this hypothesis remains moderate to high, as physical evidence and witness statements appear consistent with an unintentional ignition event resulting from human and technical error.
However, alternative hypotheses remain under review. One scenario posits that a pre-existing IT compromise, potentially linked to earlier intrusions into LGU plus or affiliated vendor networks—may have enabled opportunistic exploitation during the ensuing chaos, with adversaries using the downtime to pivot, exfiltrate, or reconnoiter government systems. A more speculative but technically plausible hypothesis considers deliberate cyber-physical sabotage, possibly involving DPRK-linked APT actors modifying battery management or UPS control firmware to trigger a controlled thermal runaway. While North Korea’s proven interest in industrial control systems lends credibility to this possibility, no public forensic evidence yet substantiates such an intrusion, keeping confidence in this scenario at low to moderate.
Technical plausibility: how malware could cause a lithium-ion fire
Thermal runaway in lithium-ion cells is a cascading thermal and chemical failure that can be initiated by a handful of root causes: sustained overcharging, internal cell shorting, excessively high discharge currents, severe cell imbalance, or mechanical damage that breaches separators. Once a single cell enters thermal runaway it can rapidly heat neighboring cells, producing venting, fire, or explosion, which is why battery modules are designed with layered protections and conservative operating thresholds.
Modern Battery Management Systems (BMS) and Energy Storage System (ESS) architectures implement those protections, cell balancing, thermal monitoring, over-/under-voltage cutouts, current limiting, and emergency relay disconnects, specifically to prevent conditions that lead to runaway. To defeat those safeguards remotely would require either modification of the BMS/ESS supervisory logic (for example via firmware tampering), spoofing or corrupting telemetry so controllers never see critical sensor values, bypassing interlock signals to prevent automatic disconnects, or direct physical tampering with protective hardware; any of these paths substantially raises the technical bar compared with a simple IT intrusion.
Plausible cyber-paths:
- Remote firmware patching of BMS microcontrollers (e.g., via vendor update tools, USB updates, or remote maintenance interfaces) to change charge thresholds, disable balancing, or suppress over-temp alarms. (Mechanism: malicious firmware image with timebomb.)
- Telemetry spoofing / sensor manipulation injecting false temperature/voltage telemetry to supervisory systems so that automatic shutdowns are not triggered. (Mechanism: man-in-the-middle on Modbus/CAN/Proprietary channels or malware on the BMS.)
- Command injection to charge controllers / inverters sending commands to UPS/charger to continue charging or to increase current beyond safe limits. (Mechanism: compromised SCADA/PLC or vendor management console.)
- Disabling relay/fuse control signals override protective relay actuators to keep circuits closed during a fault.
- Coordinated physical + digital action adversary triggers actions in the middle of maintenance (e.g., during power down/up) so that operator procedures mask anomalous digital commands.
Malware families such as TRITON (which targeted safety instrumented systems), INDUSTROYER (capable of manipulating industrial protocols), and a range of state-actor toolkits that employ wiper logic or direct firmware patching provide concrete precedents for how attackers can bypass safety layers and drive ICS equipment into hazardous states. These tools demonstrate several technical techniques relevant to battery systems: direct manipulation of control protocols, suppression or falsification of safety alarms, and replacement or tampering of firmware to alter device behavior, all routes that can convert a protected control loop into a failure mode.
North Korean actors, while better known for espionage and financially motivated operations, have in open reporting shown use of loaders, backdoors, and experimentation against OT/ICS components, which makes the broad class of cyber-physical sabotage technically plausible in principle. That plausibility, however, is not proof: applying those ICS techniques to induce a lithium-ion thermal runaway would require targeted knowledge of vendor firmware, maintenance workflows, or physical access vectors. In this incident, therefore, such malware-driven scenarios remain credible hypotheses to be investigated, but they require firmware artifacts, command logs, or definitive telemetry anomalies to move from plausible to proven.
DPRK Attribution Assessment
DPRK involvement warrants consideration because North Korean cyber units are among the most capable and aggressive in the world, with a well-documented history of targeting South Korean government, defense, and industrial systems. Multiple sanctions and intelligence advisories through 2025 have described an ongoing offensive posture, combining espionage, disruptive campaigns, and financial theft—demonstrating that Pyongyang maintains both the motivation and technical skill to strike at critical infrastructure. Their past intrusions into telecommunications and logistics networks illustrate a sustained interest in operational technologies that could intersect with energy or datacenter environments.
That said, attribution in this specific case remains weak. Current public findings emphasize maintenance activity, aging lithium-ion batteries, and human negligence, with police actions centered on on-site workers rather than external operatives. To date, there is no publicly disclosed forensic evidence of battery-management firmware tampering, command-and-cIndicators of Compromise (IOCs)
The operational impact of the NIRS data-center fire was severe, crippling critical South Korean government functions such as identity issuance, certificate validation, and access to public records. The outage affected hundreds of systems and reportedly jeopardized hundreds of terabytes of government data, with recovery timelines stretching into weeks. The disruption exposed deep dependencies on centralized digital infrastructure and revealed the fragility of national continuity mechanisms in the face of compounded physical and technical failures. Even if the root cause was accidental, the scale of the outage demonstrates how a single point failure in a high-density data environment can cascade into a multi-agency service collapse.
Strategically, the incident has intensified public concern and political debate around digital resilience and centralization. The government faces mounting scrutiny over whether redundancy, geographic diversification, and disaster recovery measures were adequate. At the same time, security analysts have warned that the chaos may have offered a window for adversarial exploitation, allowing threat actors to move laterally through connected systems or exfiltrate sensitive data during restoration efforts. If such opportunistic activity occurred, it would extend the event’s impact from operational disruption to long-term national security risk, underscoring the urgent need for coordinated cross-sector forensic huntsand a comprehensive review of how cyber and physical contingencies are integrated within South Korea’s critical infrastructure planning.
Open Questions (intelligence gaps to close)
Several intelligence gaps remain that will determine whether the NIRS fire was purely accidental or had a cyber-physical dimension. Chief among them is the need to verify whether any vendor maintenance laptops, jump hosts, or diagnostic devices contained malware or command-and-control (C2) artifacts consistent with known DPRK toolkits. Forensic imaging of these systems is essential to confirm or rule out compromise of the maintenance environment, as such systems could have provided a covert path into the Battery Management System (BMS) or Energy Storage System (ESS). Equally important is a binary-level comparison of recovered firmware against vendor baselines to detect unauthorized modifications—such as altered voltage thresholds, bypassed thermal interlocks, or hidden persistence modules—that might indicate deliberate manipulation of safety controls.
Parallel to technical forensics, broader intelligence collection must focus on network correlation and signals intelligence. Analysts should determine whether lateral movement occurred in government or contractor networks during or immediately after the fire, activity that could reveal opportunistic exploitation by an embedded actor. Finally, the intelligence community should assess whether any intercepted communications or coordination indicators tie North Korean assets to the event’s timing or planning. Closing these gaps will transform the current hypothesis-driven narrative into an evidence-based attribution model, distinguishing between coincidence, exploitation, or deliberate sabotage within South Korea’s critical infrastructure ecosystem.
Assessment & Likelihood of APT Activity Causality
Based on all available open source reporting and technical indicators, the most probable explanation for the Daejeon NIRS datacenter fire remains an accidental thermal event triggered during the relocation or maintenance of aging lithium-ion battery modules. Equipment degradation, insufficient safety interlocks, and procedural lapses appear to have converged to produce a catastrophic failure with cascading national consequences. Yet the incident did not occur in a vacuum: the preceding series of telecom and LG-group network compromises, along with DPRK’s well documented interest in industrial control and operational technology systems, introduces a layer of strategic ambiguity that cannot be dismissed without comprehensive forensic validation.
Accordingly, the hypothesis of cyber-physical interference or sabotage should be treated not as an assumption, but as a high impact line of inquiry to be rigorously pursued. Investigators should prioritize firmware extraction and differential analysis, vendor credential and access tracing, and cross-correlation of physical events with network telemetry to confirm or rule out adversary involvement. Only through disciplined, data driven analysis can South Korea separate coincidence from intent, and, in doing so, strengthen both the resilience and credibility of its national cyber-incident response posture moving forward.
如有侵权请联系:admin#unsafe.sh

