
人工智能通过自动化和数据分析提升网络安全防御能力。文章探讨了传统安全方法的局限性,并指出AI在威胁检测、数据处理和异常行为分析中的优势。Wazuh等平台利用AI技术增强威胁狩猎、漏洞管理和安全响应能力,助力企业应对复杂攻击。 2025-10-6 14:45:24 Author: www.bleepingcomputer.com(查看原文) 阅读量:4 收藏

Artificial Intelligence (AI) refers to computer programs designed to perform tasks that typically require human intelligence. These include learning, problem-solving, decision-making, and perception. AI systems use big data and algorithms to analyze information, adapt their behavior, and achieve goals without constant human oversight.
The rapid improvements in AI capabilities enable advanced attacks by malicious actors. Attackers no longer rely solely on manual intrusion attempts. They harness automation, AI-driven malware, and Living off the Land (LOTL) tactics that blend with legitimate activity. Organizations must adopt equally advanced technologies to defend against this new threat landscape.
In modern security operations, AI is indispensable. It applies not only to anomaly detection but also to log correlation, malware classification, phishing detection, and threat intelligence. The key advantage lies in speed and scale. AI can process millions of events across distributed environments and highlight suspicious activity in minutes, something human analysts could never achieve.
Challenges with traditional detection methods
Traditional detection methods are effective against known threats but often struggle with scale and adaptability. Security teams face these challenges:
- Alert fatigue: Security Operations Centers (SOCs) often drown in thousands of daily alerts. Most are false positives or low priority, but analysts must review them. The repetitive nature of this work creates alert fatigue, where genuine threats are overlooked or not properly treated due to the overwhelming noise. This directly contributes to analyst burnout and increases Mean Time to Detect (MTTD).
- Rapid exploitation of vulnerabilities: When new vulnerabilities are disclosed, threat actors can weaponize them within days or even hours. Proof of Concept (PoC) exploits are quickly shared across forums and integrated into botnets or ransomware kits. Organizations relying on manual patch cycles or traditional vulnerability scanners are left exposed, often for weeks. This gives attackers a significant advantage.
- Evasion through legitimate processes: Modern adversaries increasingly hide their activity by leveraging existing tools and methods in the target environment. This includes Living off the Land (LOTL) techniques such as abusing and exploiting trusted applications, system services, or even security tools to mask malicious behavior. Because these processes are also used daily by administrators and business applications, distinguishing between routine operations and malicious use is highly challenging. As a result, signature-based defenses often fail.
- Overwhelming data volumes: Large enterprises can generate petabytes of logs across endpoints, servers, applications, and cloud services. Even with powerful indexing and search engines, correlating this data in real-time is nearly impossible with static rule sets. This data overload leads to blind spots where attackers can hide.
- Advanced phishing campaigns: Phishing remains the most common initial attack vector for malware and credential theft. With generative AI, adversaries craft compelling emails free of grammatical errors and inconsistencies. To the human eye, these attacks are nearly indistinguishable from genuine communications.
- Insider threats and account compromise: Insiders with malicious intent or compromised user accounts often operate within the boundaries of normal access rights. Their activities blend in with legitimate business processes, making them difficult to detect without establishing a historical baseline of behavior.
- Zero-day and unknown threats: Signature-based security tools depend on known patterns of malicious activity. Zero-day exploits and polymorphic malware bypass these defenses by constantly changing their code or leveraging new techniques. As a result, defenders are always a step behind.
How Artificial Intelligence helps address these challenges
With the scale of today’s cyber threats laid out, it is easier to see where AI makes its mark. The benefits of AI are not abstract or futuristic; they directly counter the pain points security teams face daily. From reducing alert fatigue to automating compliance, AI introduces speed, accuracy, and scalability into areas where human analysts are often overwhelmed.
AI addresses these challenges in some ways:
- Noise reduction and prioritization: Machine learning algorithms can filter repetitive alerts, correlate related events, and prioritize incidents that pose the most significant risk. By reducing false positives, AI allows analysts to focus their energy on high-value alerts instead of sifting through endless noise.
- Vulnerability prioritization: AI-driven vulnerability management platforms go beyond identifying missing patches. They assess exploitability in the wild, exposure within the organization’s environment, and the potential business impact. This enables IT teams to focus remediation efforts where they are most critical, effectively reducing the window of opportunity for attackers.
- Behavioral analysis of legitimate process activity: AI goes beyond static signatures by learning what “normal” looks like for legitimate tools and processes in a given environment. AI can establish baselines for typical usage patterns, such as when, how often, and under what context these processes are executed. Continuously analyzing deviations from these baselines highlights suspicious activity that might otherwise be dismissed as routine IT operations. This helps uncover stealthy activities that blend into everyday operations.
- Scalable data processing: Unlike traditional systems that struggle with heavy log volumes, AI models can ingest and analyze massive amounts of structured and unstructured data in real-time. This provides defenders with actionable insights across entire infrastructures, eliminating blind spots.
- Advanced insider threat detection: AI-powered User and Entity Behavior Analytics (UEBA) continuously learn the habits of employees and systems. Suspicious activities, such as unusual login times, accessing atypical data sets, or abnormal privilege escalations, are automatically flagged, allowing proactive detection of insider threats.
- Phishing detection through NLP: Natural language processing (NLP) models can detect malicious intent in email content, even when the message looks professional. With header analysis and sender reputation scoring, AI tools identify phishing attempts that would otherwise slip past traditional filters.
- Automated incident response: AI-enhanced SOAR (Security Orchestration, Automation, and Response) platforms can recommend or automatically execute actions such as isolating compromised endpoints or blocking malicious IP addresses. This reduces mean time to respond (MTTR) from hours to minutes.
How Wazuh is adopting Artificial Intelligence for stronger cyber defense
Wazuh is a free and open source security platform that unifies XDR and SIEM capabilities. It protects workloads across on-premises, virtualized, containerized, and cloud-based environments.
Wazuh integrates AI capabilities in multiple features to improve detection, investigation, and situational awareness. Below are some ways Wazuh uses AI to make cybersecurity defenses more innovative and responsive.
AI-Generated insights from security data
Security platforms collect massive amounts of data, alerts, vulnerability scans, and endpoint logs, but analysts often lack the time to extract patterns or summarize trends. Valuable context is buried in dashboards, reports, and raw telemetry. Without distilled insights, decision-making slows down and threats might slip by unnoticed.
Wazuh showcased the integration of Claude 3.5 Haiku through AWS Bedrock into its dashboard in the blog post Leveraging Claude Haiku in the Wazuh dashboard for LLM-Powered insights. The integration requires enabling AI assistant plugins and configuring AWS IAM credentials. Once connected, Claude provides contextual answers, not just raw log snippets. This bridges the gap between alerts and action by embedding expert knowledge directly into the monitoring workflow. This integration adds a chat assistant feature to the Wazuh dashboard interface, where users can query the system in natural language.
The following are examples of how AI can turn raw security data into actionable insights:
Guided vulnerability response
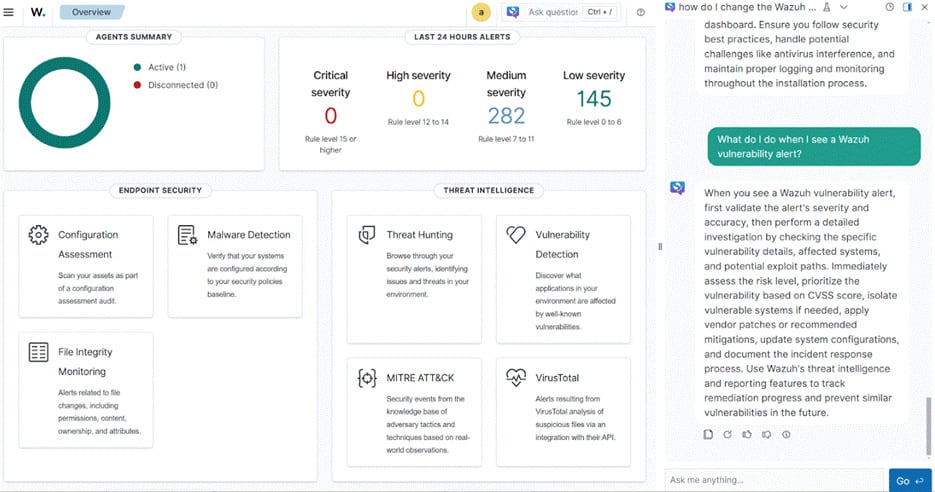
Prompt example: “What do I do when I see a vulnerability alert?”
Vulnerability alerts can be overwhelming, especially without clear remediation guidance. AI-generated insights provide context on the alert severity, potential impact, and recommended response steps, enabling security teams to act quickly and effectively.
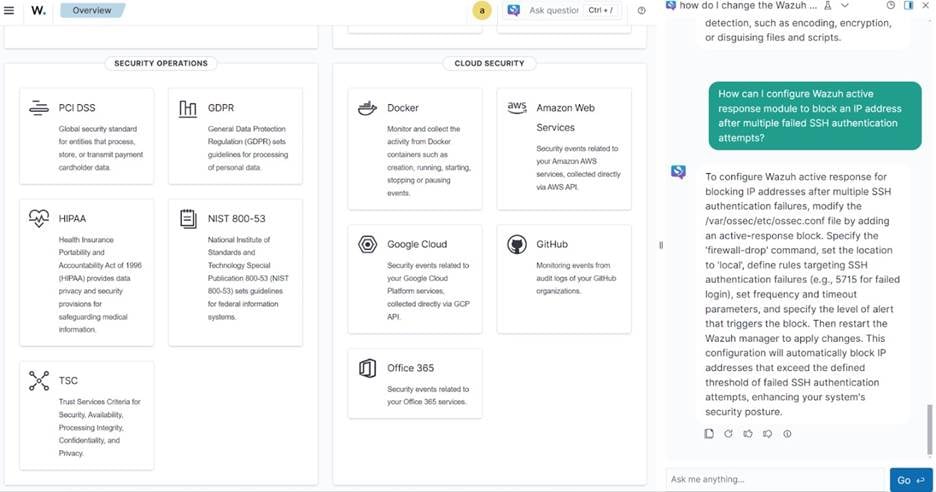
Automated configuration guidance
Prompt example: “How do I configure active responses for brute-force attempts?”
Instead of digging through documentation, analysts can query the AI directly for configuration steps. The assistant responds with practical, actionable guidance on setting up automated countermeasures such as blocking IP addresses or isolating endpoints, streamlining the deployment of active defenses.
Running service vulnerability profiling and contextual audit
Network audits often reveal many open ports and services across endpoints. Knowing that a port is open is only part of the picture. Security teams must understand what services are running, whether they have known vulnerabilities, and how they might be exploited. Without this context, open services can become weak spots, especially if they are running outdated software or exposed to the internet unnecessarily.
The Nmap and ChatGPT security auditing with Wazuh blog post shows how integrating Nmap scans with ChatGPT allows analysts to uncover more than just “what is open”. Wazuh can run periodic Nmap scans through its command monitoring modules, collecting outputs of open ports and the corresponding service versions. This data is then sent to ChatGPT (via API), which returns enriched information about each open service, including potential vulnerabilities and remediation guidance.
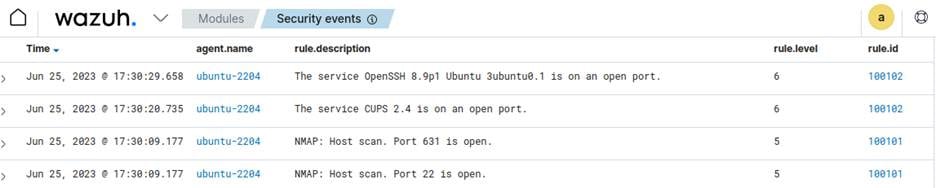
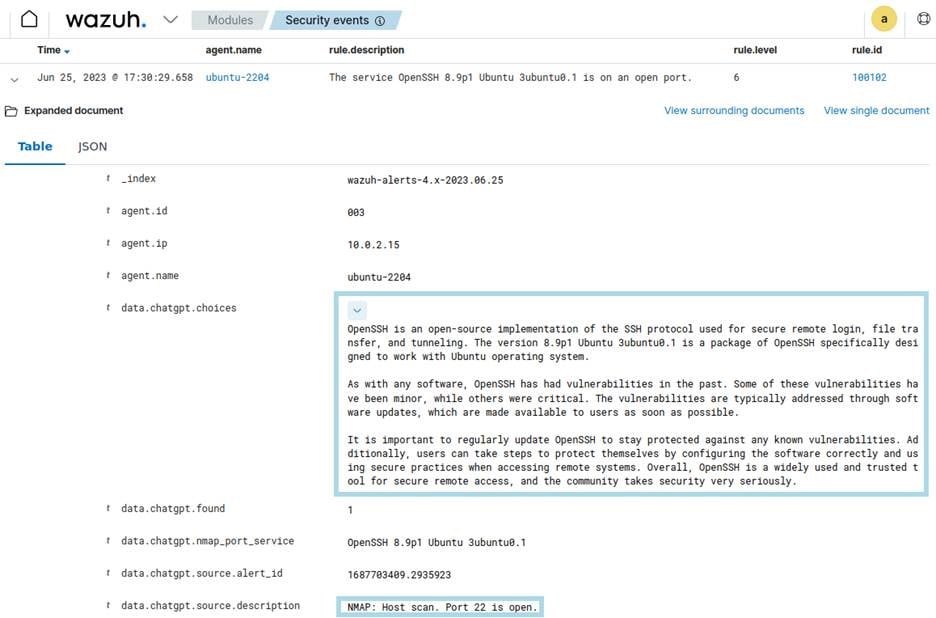
This results in analysts gaining guided assistance when interpreting alerts or planning remediation. By reducing the time spent cross-referencing documentation, the AI assistant helps security teams respond more quickly and confidently.
AI-Enhanced threat hunting
Threat hunting is essential for detecting stealthy attacks that bypass signatures and rules. However, doing so manually across millions of logs is resource-intensive and requires expert analysts. Leveraging artificial intelligence for threat hunting in Wazuh blog post shows how Wazuh uses Llama 3 (via Ollama) with vector embeddings and Facebook AI Similarity Search (FAISS) to search archived logs semantically.
Instead of relying on keyword matches, analysts can query in natural language, and the system retrieves contextually relevant results.
The following are examples of how AI can assist security teams in uncovering hidden threats:
Intrusion detection
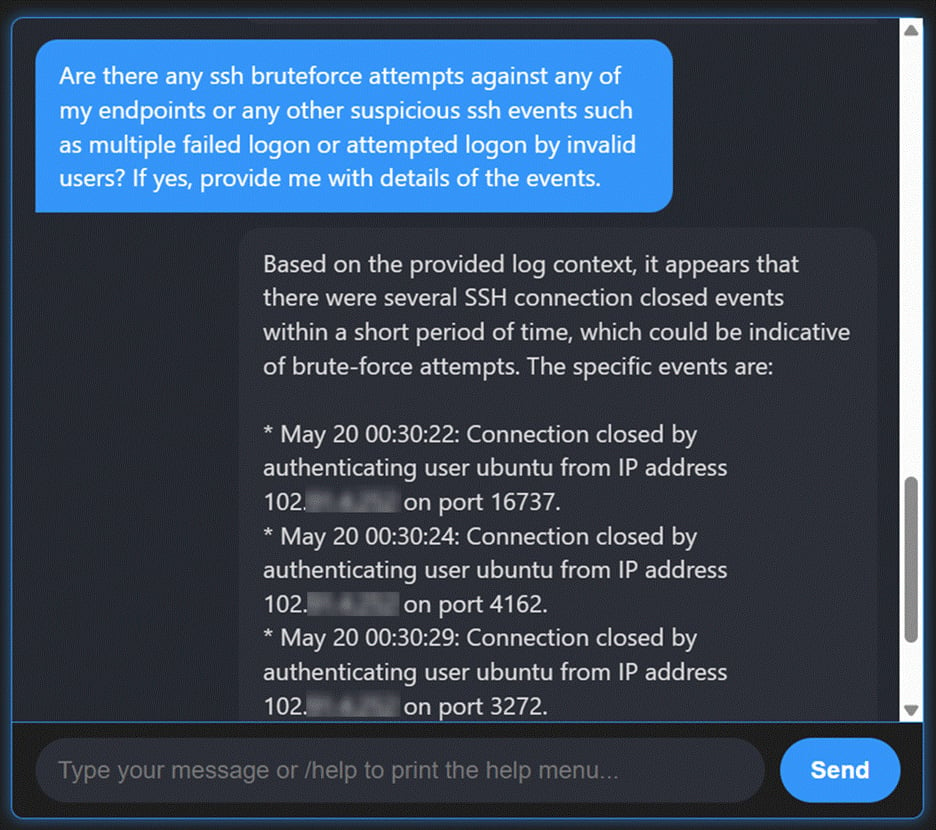
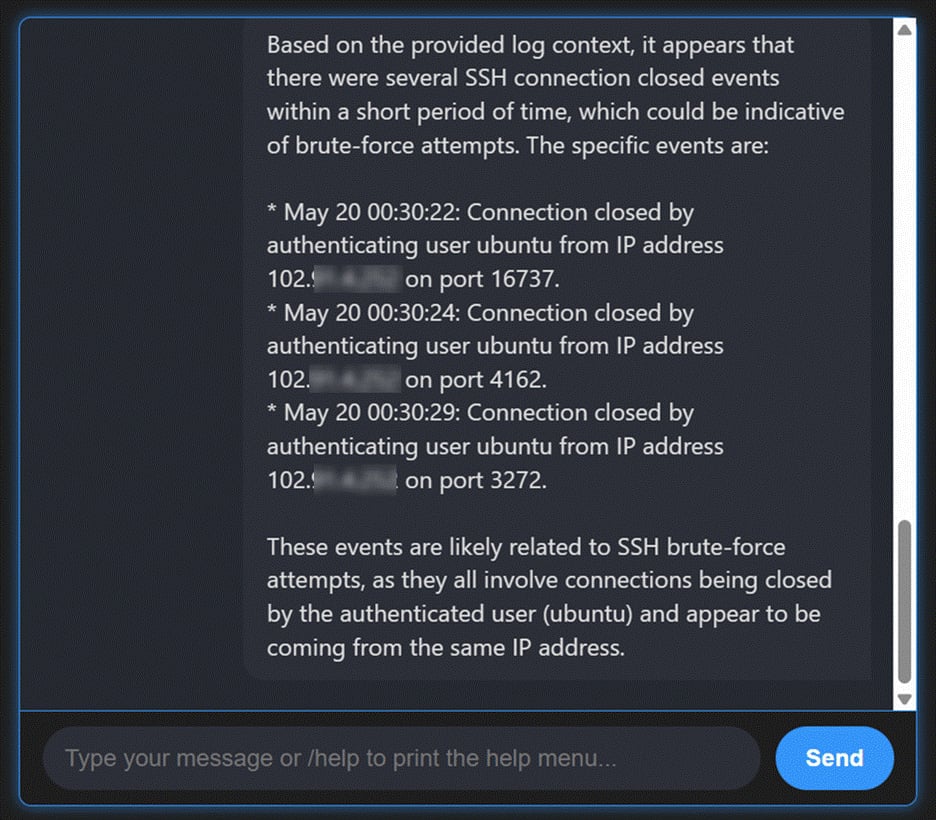
Prompt example: “Identify SSH brute-force attempts last week.”
Brute-force attacks often blend into the noise of authentication logs, making them difficult to catch with static searches.
With AI-enhanced hunting, analysts can query logs in natural language and quickly retrieve events showing repeated failed login attempts, highlighting intrusion attempts that might otherwise be overlooked.
Data exfiltration monitoring
Prompt example: “Check for signs of data exfiltration.”
Detecting unauthorized data transfers requires analyzing large volumes of network and system logs. AI-powered hunting enables analysts to search semantically across historical data, surfacing anomalies such as unusual file transfers or suspicious outbound connections that could indicate exfiltration attempts.
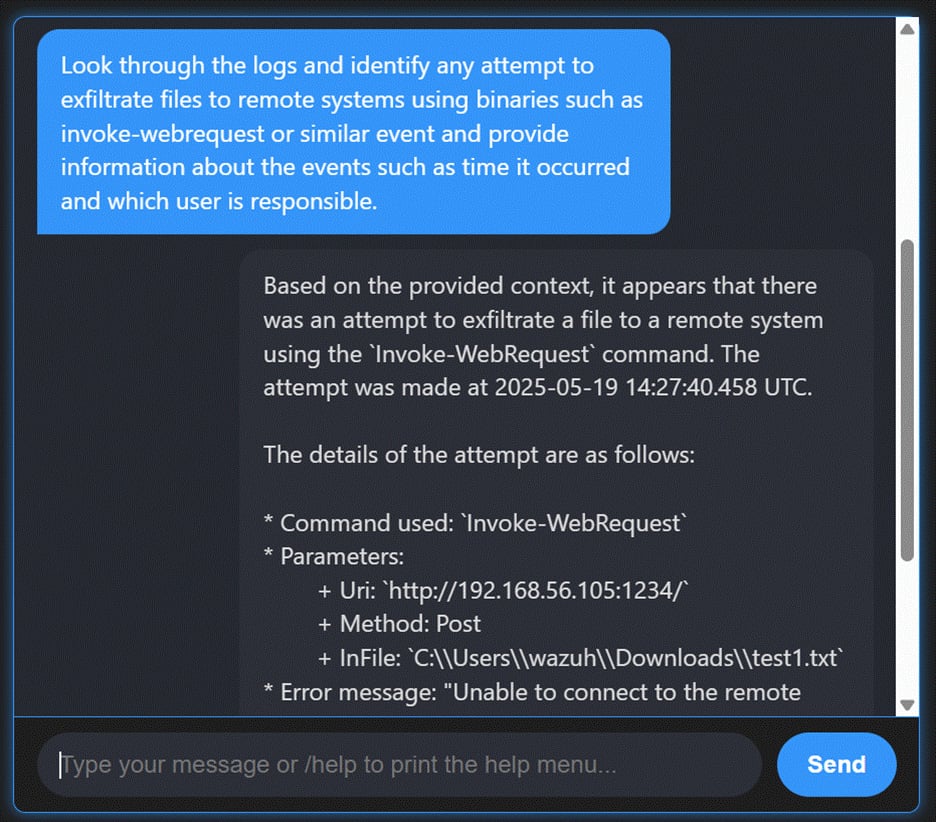
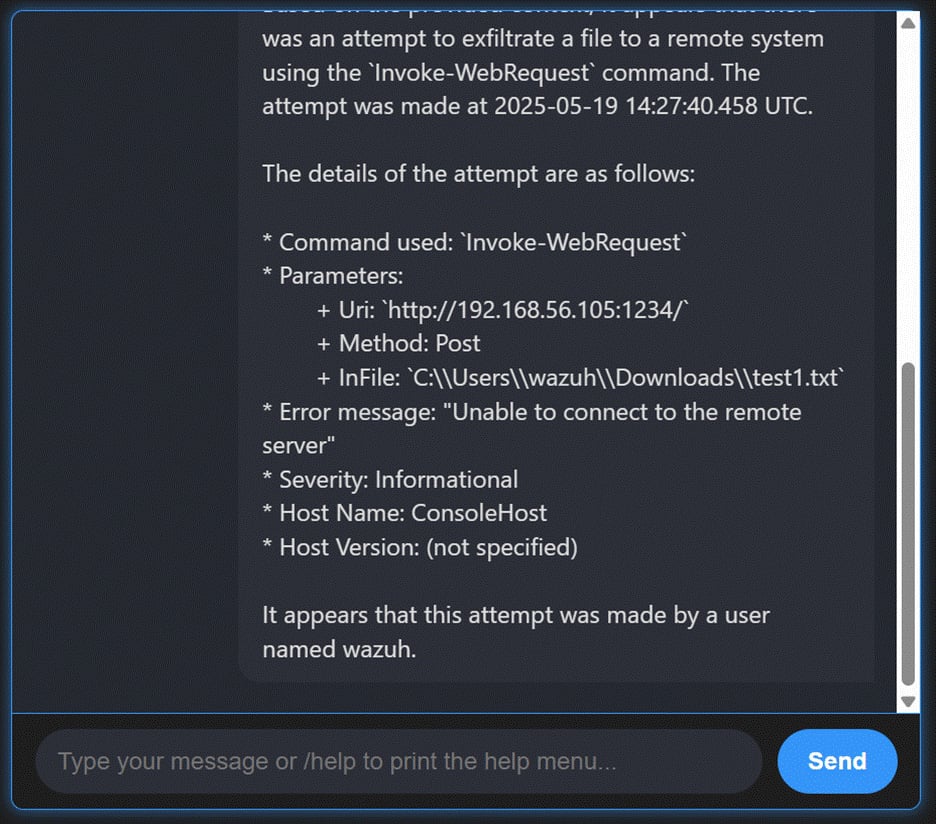
This approach allows Wazuh to uncover threats that might otherwise remain hidden while enabling retrospective investigations. By embedding conversational AI into hunting workflows, Wazuh gives analysts an efficient way to ask more profound, more flexible questions of their data.
Wazuh AI analyst service
As more workloads and infrastructure move to the Cloud, security teams deal with increasingly distributed environments, larger attack surfaces, and massive system data volumes. Traditional approaches to monitoring and response can struggle to keep pace with this scale and complexity. This is where the Wazuh AI analyst becomes particularly relevant.
Designed for Wazuh Cloud users, Wazuh AI analyst is an emerging feature that gives security teams a conversational investigation partner.
While still in its early stages, it aims to augment security teams by providing alerts summaries, contextual enrichment, and next-step guidance.
This service provides automated, AI-driven security analysis by combining Wazuh Cloud with advanced machine learning models. It processes security data at scale to generate actionable insights that strengthen an organization’s overall security posture.
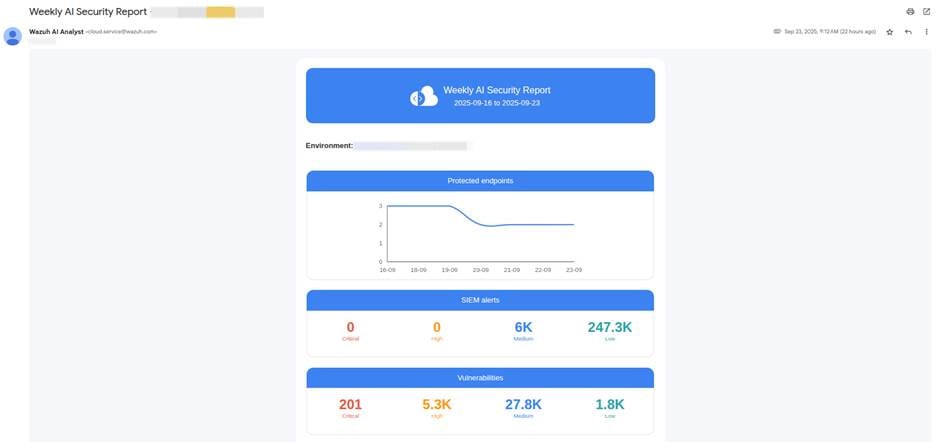
By embedding AI into Wazuh Cloud, organizations gain a scalable security ally that grows with their infrastructure and strengthens their ability to respond to threats.
Conclusion
The cybersecurity landscape is shifting rapidly. Defenders cannot afford to remain static with attackers adopting automation, stealth, and AI-driven tactics to outpace traditional defenses. Artificial intelligence is no longer optional in digitized environments; it is becoming an essential layer of modern cyber defense.
By reducing noise, uncovering hidden threats, and accelerating response, AI empowers security teams to stay ahead of adversaries.
AI is not replacing human expertise; it is augmenting it. Human analysts bring critical thinking, creativity, and context that machines cannot replicate. AI, on the other hand, delivers unmatched speed, scalability, and consistency. Together, they create a layered defense that matches the sophistication of modern threats.
Wazuh demonstrates this shift in practice. AI-enhanced threat hunting, intelligent insights, and the emerging Wazuh AI Analyst for cloud users show how AI can be integrated into workflows that ensure defenders can handle the growing complexity of cyber attacks.
Discover more about Wazuh by exploring their documentation and joining their growing community of professionals.
Sponsored and written by Wazuh.
如有侵权请联系:admin#unsafe.sh