2025年9月,网络犯罪集团Scattered LAPSUS$ Hunters利用Salesforce漏洞窃取近十亿条记录,并通过钓鱼攻击和OAuth令牌滥用获取访问权限。该组织威胁在10月10日前公开数据,影响涉及航空、零售、金融等多个行业。 2025-10-3 18:40:3 Author: krypt3ia.wordpress.com(查看原文) 阅读量:43 收藏
An OSINT-led assessment of the October 2025 deadline release by Scattered Shiny Hunters
By Krypt3ia
Executive Summary
In September 2025, a coalition of cybercriminals operating under the banner Scattered LAPSUS$ Hunters (SLSH) emerged with a new dark web leak portal that marked a notable escalation in scale and ambition. This group , a convergence of actors historically tied to LAPSUS$, ShinyHunters, and Scattered Spider , claims to have compromised over one hundred Salesforce customer instances, collectively representing close to one billion individual records. Unlike prior ransomware collectives that sought disruption through encryption and downtime, SLSH has deliberately pivoted toward a pure data theft and extortion model, recognizing that the value of centralized SaaS platforms lies in the depth and sensitivity of the customer data they aggregate.
The attackers’ tradecraft reflects both technical exploitation and human manipulation. Social engineering, in the form of sophisticated vishing campaigns, was paired with the abuse of Salesforce OAuth tokens, enabling bypass of multi-factor authentication and persistent backdoor access into targeted environments. This hybrid technique has proven especially effective in SaaS contexts where trust in app integrations is often implicit and poorly monitored. Once access was secured, the group conducted systematic exfiltration of CRM datasets containing customer personally identifiable information, financial histories, and corporate communications.

http://shinypogk4jjniry5qi7247tznop6mxdrdte2k6pdu5cyo43vdzmrwid%5B.%5Donion/
The result is a wide-ranging compromise that cuts across aviation, retail, finance, healthcare, technology, and luxury goods, with household-name enterprises now listed as victims. What distinguishes this campaign from traditional breach disclosures is the synchronized extortion deadline: every compromised organization has been given until 10 October 2025 to negotiate or face public release of their data. This alignment creates a high-pressure, collective crisis that amplifies reputational fallout for Salesforce itself, positioning the SaaS provider as a de facto target of blame.

Call out to arrested LAPSUS$ / Scattered Spiders recently taken down
As of early October 2025, public acknowledgments remain sparse, though Cisco and TransUnion have filed disclosures confirming CRM-related incidents consistent with the attackers’ claims. The absence of similar filings from other named companies raises the likelihood that many are either still conducting internal assessments or are engaged in quiet negotiations with the extortionists. This limited transparency only heightens the uncertainty surrounding the campaign, leaving customers, regulators, and investors to speculate on the full scale of impact.
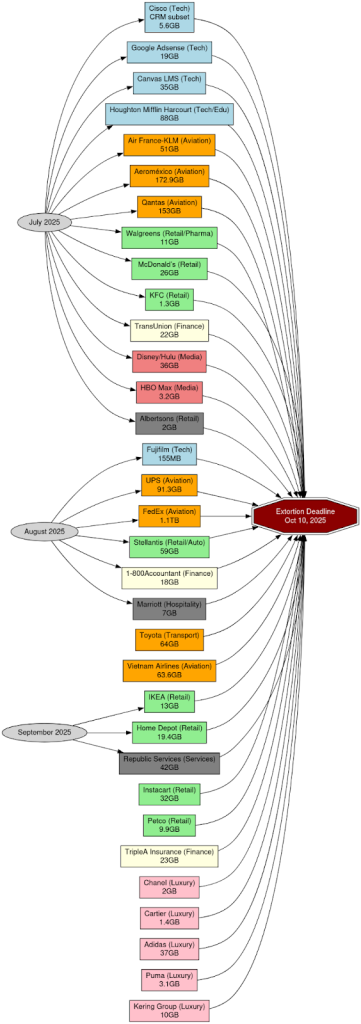
Victims Under Deadline Pressure
Based on open-source screenshots, leak site monitoring, and regulatory disclosures, the scope of the October 10, 2025 extortion deadline encompasses a cross-section of industries rarely seen in a single coordinated operation. Victims are distributed across multiple verticals, underscoring Salesforce’s role as a central data hub and the attackers’ ability to exploit that dependency.
Technology & IT:
The list of compromised tech entities , including Cisco, Google Adsense, Instructure’s Canvas LMS, Houghton Mifflin Harcourt (HMH), and Fujifilm , highlights the breadth of intellectual property, advertising ecosystems, and education platforms now exposed. Cisco’s CRM breach was publicly confirmed, while Google Adsense presents a particularly sensitive case due to its linkage with publisher revenues and advertising identity data. Education-focused services like Canvas LMS and HMH extend the risk to academic records, classroom communications, and potentially minors’ data.
Aviation & Transport:
UPS, FedEx, Air France-KLM, Aeroméxico, Qantas, Toyota, and Vietnam Airlines collectively represent one of the most critical clusters in the campaign. With FedEx alone seeing over a terabyte of records exfiltrated, these breaches could expose passenger manifests, freight logistics, customs clearance details, and loyalty program credentials. Such datasets are not only valuable for fraud but also sensitive from a national security and border control perspective. For Toyota, a manufacturer deeply integrated into supply chains, exposure of CRM-linked contracts and customer histories compounds risk.
Retail & Consumer:
Household brands such as IKEA, Home Depot, Walgreens, Stellantis, McDonald’s, KFC, Instacart, and Petco demonstrate the breadth of consumer-facing impact. These breaches potentially expose loyalty card databases, pharmacy prescription data (Walgreens), automotive service records (Stellantis), and massive volumes of food delivery and retail purchase histories. Unlike aviation or finance, where regulators enforce mandatory disclosure, many of these firms may attempt to quietly negotiate or downplay impact, leaving consumers vulnerable to follow-on phishing or fraud campaigns.
Finance & Insurance:
With TransUnion, 1-800Accountant, and TripleA Insurance listed, the attackers have compromised some of the most sensitive datasets available. TransUnion’s confirmed breach alone places millions at risk of identity theft and credit fraud. Tax and accounting firms like 1-800Accountant compound the exposure with detailed financial filings, while insurers carry a mix of health and personal data. These incidents elevate the campaign to a systemic risk for fraud markets and dark web identity resale.
Luxury & Apparel:
The compromise of Chanel, Cartier, Adidas, Puma, and the Kering Group (Gucci, Balenciaga, Alexander McQueen) exposes both standard retail records and sensitive information tied to high-net-worth clients. For luxury houses, CRM platforms often store bespoke client services, including purchase histories, travel preferences, and even private event invitations. The resale or public release of such information could enable highly targeted social engineering against affluent individuals.
Media & Entertainment:
Disney/Hulu and HBO Max may appear less sensitive at first glance, but CRM data here includes subscriber PII, payment methods, and media consumption habits. Exposure of these records creates opportunities for account takeover attacks, credential stuffing against other services, and even reputational risk for individuals if viewing preferences are tied to leaked accounts.
Hospitality & Services:
Finally, entities such as Marriott, Republic Services, and Albertsons illustrate how the breach extends into both global hospitality and critical service providers. Marriott, which has faced repeated high-profile breaches, risks compounding regulatory penalties under GDPR and CCPA. Republic Services, as a waste management giant, could see operational supply chain data compromised. Albertsons, a major grocery retailer, adds another dimension of consumer loyalty and payment card risk to the incident.
Across all of these verticals, the data volumes span from modest samples to catastrophic leaks, with FedEx’s 1.1 terabytes of records being the largest identified to date. Taken together, this elevates the operation beyond a string of isolated breaches and into a systemic threat event. What is being exposed is not only global customer PII but also highly sensitive categories such as travel manifests, financial records, insurance claims, healthcare prescriptions, and luxury client profiles. The campaign effectively demonstrates how a single SaaS dependency , Salesforce , can serve as a fault line through which attackers access and extort multiple critical industries at once.
Public Confirmations

Cisco:
Cisco has been the most transparent of the victims identified so far, publishing a blog post and filing an 8-K disclosure acknowledging a CRM-related breach. The company confirmed that attackers used a vishing campaign to impersonate IT support staff and convince employees to approve a malicious Salesforce OAuth application. Once authorized, the attackers bypassed multi-factor authentication controls and harvested OAuth tokens to maintain persistent access. Cisco stated that the compromised data was limited to a subset of user profile information from a third-party CRM instance, but it has not yet clarified the full scope of records stolen. This admission aligns directly with the tactics advertised by Scattered LAPSUS$ Hunters, providing the first verified bridge between the group’s claims and a Fortune 500 disclosure.
TransUnion:
On July 28, 2025, TransUnion disclosed through an SEC 8-K filing that it had suffered a significant unauthorized access incident, later confirmed to involve more than 4.4 million consumer records. The credit bureau reported that attackers had accessed personally identifiable information including names, Social Security numbers, and credit file details. While TransUnion did not explicitly name Salesforce in its filings, the timeline, data types, and extortion alignment strongly match the Scattered LAPSUS$ Hunters campaign. Given the company’s regulatory obligations in both the U.S. and abroad, this disclosure represents one of the most material confirmations of the incident’s legitimacy and scope.
Other Victims:
As of October 3, 2025, none of the other high-profile organizations listed on the leak portal , including UPS, FedEx, Home Depot, Air France-KLM, Qantas, IKEA, and Disney/Hulu , have filed 8-Ks or equivalent disclosures acknowledging a breach tied to Salesforce. The lack of public statements could reflect multiple dynamics:
- Delayed Reporting: Many firms may still be conducting internal forensic investigations and legal reviews before confirming Salesforce linkage.
- Regulatory Thresholds: Certain jurisdictions do not mandate disclosure until consumer harm is evident, creating gaps between breach discovery and public acknowledgment.
- Negotiation Window: The shared October 10 extortion deadline suggests some companies may be quietly engaging with Scattered LAPSUS$ Hunters in an effort to suppress data leaks prior to disclosure.
- Reputational Risk Management: Organizations in sectors like aviation and luxury retail may be weighing the reputational impact of disclosure and attempting to limit exposure until forced by regulators or data release.
Strategic Implications
The Scattered LAPSUS$ Hunters (SLSH) campaign represents a pivotal shift in the cyber-extortion ecosystem. Traditionally, ransomware groups have operated on a victim-by-victim basis, seeking direct ransom payments in exchange for data decryption or suppression of leaks. What differentiates this campaign is its supply-chain extortion model: by targeting Salesforce as the common dependency, the attackers are attempting to reframe the economics of response. Instead of dozens of separate negotiations, they are openly suggesting that Salesforce itself could “pay once” to shield its entire customer base. This tactic reframes a SaaS provider not merely as an indirect vector of compromise, but as the ultimate pressure point in global enterprise operations. It highlights a new frontier in SaaS abuse, where cloud giants are portrayed as single points of systemic failure that can be held accountable for customer losses.
For Victims:
The implications are severe. Companies across aviation, finance, healthcare, retail, and technology now face overlapping risks that extend far beyond data loss. Regulatory agencies in multiple jurisdictions, from GDPR in Europe, to HIPAA in the U.S., to aviation safety boards, may launch investigations once the leaked data becomes public. Reputational damage will ripple across sectors, eroding customer trust in brands that range from airlines to luxury fashion houses. Legal risks include class-action lawsuits, shareholder actions, and penalties for failing to safeguard customer data. In industries such as aviation and healthcare, where personal data intersects with safety and critical service delivery, the consequences could escalate from financial harm to national security concerns.
For Salesforce:
This incident is more than a customer security lapse; it is a platform trust crisis. The attackers’ messaging reframes Salesforce not as a passive third party, but as the responsible entity whose weaknesses enabled the cascade of breaches. Even if the vulnerabilities exploited were rooted in customer misconfigurations or social engineering, the narrative now positions Salesforce as culpable for the systemic exploitation of its ecosystem. This creates reputational strain not just with customers but with regulators, investors, and partners. If Salesforce is perceived as failing to secure its OAuth and app ecosystem, it could accelerate calls for greater regulatory oversight of SaaS providers and force the company into a defensive posture to protect both its market valuation and long-term viability.
For the Threat Landscape:
The formation of SLSH itself signals a troubling evolution. By uniting actors historically linked to LAPSUS$ (known for brazen social engineering), ShinyHunters (data broker specialists), and Scattered Spider (SIM swapping and extortion), this campaign represents the consolidation of complementary skill sets into a cartel-like structure. Youthful, reckless operators are now merged with more organized monetization strategies, creating a hybrid adversary capable of both opportunistic social engineering and sustained extortion operations. This consolidation echoes broader trends in cybercrime, where fluid, networked groups rebrand and reconfigure rather than disappear. The implication is that future campaigns will increasingly target shared dependencies, SaaS platforms, managed service providers, or cloud integrations, and attempt to extort them at scale, reframing not just how ransom is demanded but who is held responsible.
APPENDIX A: Tactics, Techniques, and Procedures
Initial access , Vishing + Social Engineering
What they do
- Call targets pretending to be IT, security, or a vendor, and socially engineer the user into approving a connected app authorization in Salesforce (or similar SaaS).
- May combine social proofs (internal ticket numbers, spoofed caller ID, known user names) and urgency (“you must approve this update now”) to force quick action.
- May also phish via email with a “Connect this app” flow that looks legitimate.
Why it works
- Users trust in-app-authorization flows and MFA push prompts; they are trained to “approve” prompts from corporate admins.
- Many organizations have a weak process for vetting/whitelisting connected apps, and admin consent can be granted with a single click.
Hunt & detection ideas
- Monitor phone-system / helpdesk telemetry for calls that mention app approvals or ask users to “approve Salesforce app.” Correlate with subsequent suspicious auth events.
- Look for spike in user-initiated OAuth app consent events.
- Detect sudden creation or unusual approvals of “Connected Apps” in Salesforce Admin logs.
Persistence , OAuth token abuse and durable API access
What they do
- When a user authorizes a malicious connected app, the app receives OAuth access and refresh tokens. These tokens can be used to access APIs without the user’s password or triggering additional MFA, and refresh tokens grant long-lived access.
- Attackers store and reuse refresh tokens to regain access even after short-lived tokens expire.
Why it’s powerful
- Bypasses password policies and many MFA setups because OAuth tokens are treated as valid sessions.
- Acts at API level , attackers can perform bulk queries, export resources, and create backdoors (e.g., create service accounts, insert integration credentials).
Hunt & detection ideas
- Monitor for “refresh_token” grant events and for token usage from IPs/geolocations that do not match the authorizing user’s baseline.
- Watch API call patterns for high-volume SOQL queries, large numbers of “queryAll” or bulk query operations, and use of data export APIs.
- Identify connected apps with broad scopes (Admin, API, Full) and last-used times that don’t match authorized workflows.
Exfiltration , Bulk CRM data extraction
What they do
- Use API access to enumerate objects (Contacts, Leads, Accounts, Cases), then perform large exports or iterative queries to extract PII, financial records, travel manifests, and internal notes.
- May use integrated third-party apps (Drift, middleware, ETL) to pivot into other services (e.g., Snowflake, AWS) and exfiltrate through those pipes.
Indicators
- High volume of REST or Bulk API requests within a short window.
- Large QUERY operations returning huge row counts, or many queryMore pagination cycles.
- Use of rare API endpoints (e.g., Apex REST, Metadata, Tooling) by non-admin users.
- Unusual data staging (temporary S3 buckets, external FTP, or third-party analytics endpoints receiving large uploads).
Hunt & detection ideas
- Query Salesforce Event Monitoring logs: API, Login, ApexExecution, and Bulk API events.
- Correlate large exports with external network egress logs, proxy logs, or cloud storage writes (S3, Azure Blob).
- Alert on any export >X GB (threshold tuned to environment) or >Y records in a short period.
Impact & Strategy , Data theft + extortion (not encryption)
What they do
- Rather than encrypt systems, publish samples and threaten public dumps unless ransom is paid.
- Use synchronized deadlines to maximize pressure on victims and platform provider (Salesforce).
- May attempt to name-and-shame, threaten GDPR lawsuits, or use media channels/Telegram to amplify damage.
Operational consequences
- Regulatory exposure (GDPR, CCPA, sectoral regulators) and legal liability.
- Secondary attacks (phishing, account takeover) leveraging exposed PII.
- Reputation damage for both customers and the SaaS provider, potentially precipitating customer churn.
MITRE ATT&CK mapping (contextualized)
- T1078 , Valid Accounts
Use of legitimate OAuth tokens / authorized sessions to access accounts and APIs. - T1566.004 , Phishing: Vishing
Voice-based social engineering to obtain authorization or consent. - T1550.001 , Use of Stolen Tokens
Reuse of OAuth access/refresh tokens to access APIs and maintain persistence. - T1530 , Data from Cloud Storage Object
Exporting data from cloud services or from cloud-connected storage (incl. SaaS export features).
Detection rules / example SIEM EXAMPLE queries
Splunk (pseudo)
- Detect refresh token usage and suspicious connected app authorizations:
index=salesforce eventType=OAuthToken
| stats count by connected_app, user, src_ip, grant_type, _time
| where grant_type=”refresh_token” OR count>100
- Detect large Bulk API exports:
index=salesforce eventType=BulkAPI
| stats sum(recordsReturned) as rows by user, src_ip
| where rows > 100000
Elastic / Kibana (pseudo) EXAMPLE
- High-frequency SOQL queries:
GET /salesforce/_search
{
“query”: {
“bool”: {
“must”: [
{“match”: {“event”:”API_CALL”}},
{“match”: {“operation”:”query”}}
],
“filter”: {
“range”: {“@timestamp”: {“gte”: “now-1d”}}
}
}
},
“aggs”: {
“by_user”: {“terms”: {“field”: “user.keyword”, “size”: 20}}
}
}
Salesforce Admin / Event Monitoring EXAMPLE
- Audit EventLogFile for API and Login events, and parse fields:
- ApiType (Bulk REST, SOAP), Operation, Rows, ClientIp, UserId, ConnectedAppId.
- ApiType (Bulk REST, SOAP), Operation, Rows, ClientIp, UserId, ConnectedAppId.
- Alert when a ConnectedApp with OAuthScope including full, api, or refresh_token is authorized by a non-admin user.
Short-term containment & IR playbook (prioritized)
- Identify & preserve evidence
- Snapshot Salesforce org configuration, ConnectedApp list, Event LogFiles, and LoginHistory. Do not immediately purge logs.
- Snapshot Salesforce org configuration, ConnectedApp list, Event LogFiles, and LoginHistory. Do not immediately purge logs.
- Contain
- Revoke suspicious refresh tokens and access tokens immediately.
- Disable & quarantine untrusted Connected Apps.
- Restrict all sessions for affected users (reset sessions, require re-login).
- Revoke suspicious refresh tokens and access tokens immediately.
- Eradicate
- Force password resets for impacted users, rotate service account credentials, and rotate API keys used by integrations.
- Revoke any OAuth tokens for third-party apps not on the approved whitelist.
- Force password resets for impacted users, rotate service account credentials, and rotate API keys used by integrations.
- Remediate
- Remove unnecessary OAuth scopes from trusted apps; implement stricter connected-app approval workflows.
- Enforce session IP restrictions and org-wide login IP ranges where feasible.
- Remove unnecessary OAuth scopes from trusted apps; implement stricter connected-app approval workflows.
- Recover & validate
- Validate that exports stopped, monitor for re-use of revoked tokens, and run proactive privilege escalation checks.
- Validate that exports stopped, monitor for re-use of revoked tokens, and run proactive privilege escalation checks.
- Notify & coordinate
- Brief legal, communications, and executive teams; coordinate disclosures and regulator notifications as required.
- Reach out to Salesforce CS/Trust for platform assistance (connected app revocation, token invalidation support).
- Brief legal, communications, and executive teams; coordinate disclosures and regulator notifications as required.
- Law enforcement
- Engage appropriate law enforcement and share artifact sets (e.g., token strings, timestamps, connected app IDs, C2 endpoints used).
- Engage appropriate law enforcement and share artifact sets (e.g., token strings, timestamps, connected app IDs, C2 endpoints used).
Recommended immediate technical mitigations (high priority)
- Revoke unused refresh tokens and set short token lifetimes where possible.
- Require admin review for all Connected App authorizations; limit who can approve apps.
- Whitelist/allowlist trusted apps only; block all others by default.
- Implement OAuth policies that restrict IP ranges, device types, and require reauthentication for sensitive scopes.
- Enable Salesforce Event Monitoring / Shield to collect API, Login, and Data Export events for forensic visibility.
- Enforce least privilege on integration/service accounts, and remove unused profiles/permissions.
- Require hardware MFA (FIDO2) for high-privilege users to reduce push-approval social engineering risk.
- Network egress controls: detect and block large uploads to unknown cloud storage or external endpoints.
Recommended organizational mitigations (people & process)
- Vishing training: run simulated vishing exercises and train staff on never approving unknown app authorizations.
- Third-party risk: inventory all Connected Apps and third-party integrations, require vendor security attestations.
- Incident playbooks: have a Salesforce-specific IR playbook that includes token revocation and connected app quarantine steps.
- Legal & comms prep: pre-write incident disclosure templates and regulator contact plans.
- Emergency response SLA with Salesforce: ensure a fast communication channel to request token revocation support or Org-level protection.
Forensics & evidence to collect (must-have)
- EventLogFile exports for the entire suspected window (API, Login, Bulk API, ApexCallout).
- ConnectedApp create/authorize logs and the OAuthToken grant records.
- Downloaded sample files, external storage endpoints, and any attacker-controlled domains/IPs seen in egress logs.
- Telephone metadata / helpdesk logs that correspond to suspicious approvals.
- SIEM logs showing API patterns and anomalous IP geolocation.
Example prioritized detections to implement quickly
- Alert: Connected app approval by non-admin for scope containing refresh_token or full.
- Alert: refresh_token grant followed by API calls from different geolocation > 500 miles within 1 hour.
- Alert: Bulk API export > 100GB or > X million rows in < 24 hours.
- Alert: Elevated number of Token Exchange or OAuth events for the same ConnectedApp.
- Alert: Sudden increase in queryAll/queryMore operations by a single user/service account.
如有侵权请联系:admin#unsafe.sh
