
read file error: read notes: is a directory 2025-10-3 13:0:0 Author: www.tenable.com(查看原文) 阅读量:27 收藏
As we kick off Cybersecurity Awareness Month, AI security challenges take the spotlight. Meanwhile, new marching orders say OT security teams need a comprehensive view of their systems. And get the latest on post-quantum computing standards and on a fresh batch of CIS Benchmarks!
Key takeaways
- Your staff is likely feeding sensitive data to AI tools you don’t know they’re using. Time to rev up your AI security awareness training.
- OT security teams must have a full understanding of their OT environment’s architecture in order to fully protect it.
- A new standard specification seeks to add consistency to the technical jargon used in post-quantum cryptography.
Here are five things you need to know for the week ending October 3.
1 - It’s Cybersecurity Awareness Month, and the state of AI security ain’t good
Cybersecurity Awareness Month is here and boy, do we need a special focus on cyber right now, especially on the area of AI security.
How precarious is the AI security situation? Check out these stats:
- Everyone's using it: AI usage is booming, with 65% of people using AI tools, up from 44% a year ago.
- Most aren’t trained for it: A whopping 58% of employees have received zero training on AI security or privacy risks.
- Business secrets are spilling: 43% of employees admit to feeding company info into AI tools. We're talking internal documents (50%), financial data (42%) and even client data (44%).
Those numbers come from the report “Oh, Behave! The Annual Cybersecurity Attitudes and Behaviors Report 2025-2026” from the National Cybersecurity Alliance and CybSafe. Published this week, the report is based on a survey of 7,000-plus respondents from Australia, Brazil, Germany, India, Mexico, the U.K. and the U.S.
“The rapid rise in AI usage is the double-edged sword to end all double-edged swords: while it boosts productivity, it also opens up new and urgent security risks, particularly as employees share sensitive data without proper oversight,” reads the report.
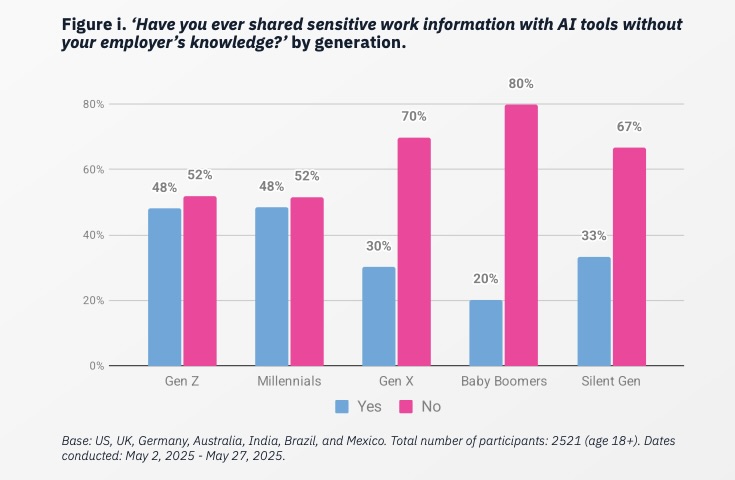
And it’s not like people are clueless about AI risks. They’re worried about AI super-charging scams and cyber crime (63%), fake info (67%), security system bypassing (67%) and identity impersonation (65%). Yet, respondents’ faith in companies adopting AI responsibly and securely is only 45%.

As the gap between people’s AI adoption and AI security awareness widens, so does the attack surface security teams must protect. In fact, shadow AI, which is the unauthorized use of AI tools in the workplace, is “here to stay” and “becoming the new norm,” the report states, attributing its rise to insufficient AI security awareness training.
“Without urgent action to close this gap, millions are at risk of falling victim to AI-enabled scams, impersonation, and data breaches,” Lisa Plaggemier, Executive Director of the National Cybersecurity Alliance, said in a statement.
There are tons of other insights, findings and recommendations in the 142-page report about a variety of cyber threats, so we encourage you to give it a read.
In the end, the report recommends zeroing-in on five core practices “that make or break security”:
- Practicing password hygiene, such as creating complex passwords and never reusing them
- Using multi-factor authentication (MFA)
- Keeping software updated
- Backing up data
- Being alert to phishing signs
To learn more about securing your AI systems, check out these Tenable resources:
- “New Tenable Report: How Complexity and Weak AI Security Put Cloud Environments at Risk” (blog)
- “The State of Cloud and AI Security 2025” (research report)
- “Introducing Tenable AI Exposure: Stop Guessing, Start Securing Your AI Attack Surface” (blog)
- “AI Is Your New Attack Surface” (on-demand webinar)
- Know Your Exposure: Is Your Cloud Data Secure in the Age of AI? (on-demand webinar)
2 - Here's your Cybersecurity Awareness Month care package
The cyber industry has your back with a bunch of free resources this month. Here’s a quick roundup of some of them:
- National Cybersecurity Alliance: Along with their eye-opening report, the NCA is running a “Stay Safe Online” campaign, which includes the “Protecting Your Business’s Cash from Cyber Criminals” webinar on Oct. 28 at 1 pm ET.
- CISA: As part of its “Building a Cyber Strong America” campaign, the U.S. Cybersecurity and Infrastructure Security Agency is offering a cybersecurity awareness toolkit for organizations, as well as cyber guidance for small and medium-sized businesses (SMBs) and for state and local governments.
- SANS Institute: Worried about AI? SANS' “AI Awareness Toolkit” aims to help organizations educate their employees about AI cyber risks. It includes factsheets, a sample AI acceptable use policy, an infographic, tip sheets and more.
- World Economic Forum: Get the 30,000-foot view with WEF's article “Cybersecurity Awareness Month: 10 things to know in 2025,” which covers everything from the talent shortage to the threat of agentic AI.
And of course, stay tuned to Tenable! As a partner of the NCA's Cybersecurity Awareness Month effort, we'll be raising awareness of simple, proven ways to boost online safety and sharing tips to put these cyber practices into action.
CISA Acting Director Madhu Gottumukkala on Cybersecurity Awareness Month 2025
3 - Memo to OT teams: You can't secure what you can't see
If you’re tasked with securing your organization’s operational technology (OT) systems, this one’s for you.
This week, U.S. and U.K. cyber agencies published the guide “Creating and maintaining a definitive view of your OT architecture” with a simple message: you need a complete, up-to-date map of your OT systems and network.
“A definitive OT record enables organizations to conduct more comprehensive risk assessments, prioritize critical and exposed systems, and implement appropriate security controls,” CISA said in a statement.
The guidance also tackles third-party risk management, OT data security and architectural controls design.
Having the visibility that this “definitive OT record” provides is increasingly critical because OT networks are no longer isolated islands. They’re connected to IT networks and the internet, making them an attractive target.

(Image created by Tenable using Google Gemini)
This record should be your single source of truth for every OT component, connection and configuration. To properly assemble this OT architecture map, the guide, co-authored by the U.K.'s National Cyber Security Centre (NCSC), prescribes five core principles:
- Define your process: Figure out how you'll collect, validate and maintain information for this OT map.
- Lock it down: Establish an OT information-security management program to protect the confidentiality, integrity and availability of OT information.
- Know what matters: Identify and categorize your assets so you can protect the most critical ones first by making informed, risk-based decisions.
- Trace the wires: Identify and document every OT connection to build effective security controls.
- Monitor your suppliers: Understand and document the risks coming from third-party vendors that have access to your systems.
Following these steps will give you the visibility needed to defend your OT environment effectively, according to CISA and the NCSC.
For more information about OT security, check out these Tenable resources:
- “Mind the Gap: A Roadmap to IT/OT Alignment” (white paper)
- “Unlock Advanced IoT Visibility in your OT Environment Security” (on-demand webinar)
- “Blackbox to blueprint: The security leader’s guidebook to managing OT and IT risk” (white paper)
- “Identity Security Is the Missing Link To Combatting Advanced OT Threats” (blog)
- “Securing critical infrastructure” (solution overview)
- “From Compliance Burden to Security Advantage: A Practical Approach for OT/IT Security” (on-demand webinar)
4 - U.K. NCSC champions common post-quantum terminology
There’s a communication problem among those working on post-quantum cryptography (PQC), and the U.K.’s cyber agency wants to help solve it.
This week, the U.K. National Cyber Security Centre promoted a specification to standardize the terminology used by organizations developing and adopting cryptography that can withstand attacks powered by quantum computers.
“Consistent terminology across PQC ensures that technical proposals and discussions have clarity and consistency, and prevents misunderstandings that can lead to security issues,” reads an NCSC blog.

The new standard, which the NCSC developed along with Dr. Britta Hale from the Naval Postgraduate School, is named RFC 9794 and was published by the Internet Engineering Task Force (IETF) in June.
The new terminology is especially important for discussing "hybrid" scenarios in which traditional cryptography and PQC are used in tandem.
The goal of RFC 9794 is to ensure that everyone, from technical experts to policymakers, can communicate effectively and make informed decisions about securing systems against the quantum threat.
The new standard is already being adopted in technical drafts, academic papers and guidance from other standards bodies, demonstrating its immediate and significant impact on the cybersecurity field, according to the NCSC.
Quantum computers that can break today’s cryptographic algorithms are expected to be available at some point during the next decade.
For more information about the quantum computing threat, check out these Tenable blogs:
- “U.K.’s Cyber agency Offers Post-Quantum Migration Guidance”
- “Quantum Threat: The Time To Get Ready Is Now”
- “First Quantum-Resistant Algorithms Ready for Use”
- “ETSI Issues Quantum-Resistant Crypto Standard”
- “NIST Picks Another Quantum-Resistant Algorithm”
- “Experts Issue Best Practices for Migrating to Post-Quantum Cryptography”
5 - CIS updates Benchmarks for Google, Microsoft and Oracle products
Does your organization use the CIS Benchmarks to strengthen software configurations? The Center for Internet Security (CIS) just rolled out its monthly update of secure-configuration guidelines. It's time to check the list and harden your systems.
This month's updates include guidelines for Windows Server, Oracle Database, Google ChromeOS and many more.
Here’s the full list:
- CIS AKS Optimized Azure Linux 2 Benchmark v1.1.0
- CIS IBM i V7R4M0 Benchmark v2.1.0
- CIS IBM i V7R5M0 Benchmark v2.1.0
- CIS GitHub Benchmark v1.1.0
- CIS Google ChromeOS Benchmark v1.1.0
- CIS Microsoft Windows Server 2016 STIG Benchmark v4.0.0
- CIS Microsoft Windows Server 2022 STIG Benchmark v3.0.0
- CIS MongoDB 7 v1.2.0 Benchmark
- CIS Oracle Database 23ai Benchmark v1.1.0 Benchmark
- CIS Oracle Linux 8 Benchmark v4.0.0
- CIS Red Hat Enterprise Linux 8 Benchmark v4.0.0
- CIS Rocky Linux 8 Benchmark v3.0.0
- CIS Palo Alto 10 Benchmark v1.3.0
In addition, CIS released four brand new Benchmarks:
- CIS AKS Optimized Azure Linux 3 Benchmark v1.0.0
- CIS Linux Mint 22 Benchmark v1.0.0
- CIS MongoDB 8 Benchmark v1.0.0
- CIS Red Hat Enterprise Linux 10 Benchmark v1.0.0
To help organizations implement these guidelines more efficiently, new Build Kits — tools that automate the configuration process — have also been released for CIS Microsoft Windows Server 2016 STIG Benchmark v4.0.0 and CIS Microsoft Windows Server 2022 STIG Benchmark v3.0.0.

The CIS Benchmarks’ configuration recommendations are designed for hardening software against cyber attacks. There are 100-plus Benchmarks for over 25 vendor product families. Software categories covered by the CIS Benchmarks include: cloud platforms; databases; desktop and server software; mobile devices; operating systems; and more.
To get more details, read the CIS blog “CIS Benchmarks Monthly Update September 2025.” For more information about the CIS Benchmarks list, check out its home page and FAQ, as well as:
- “Getting to Know the CIS Benchmarks” (CIS)
- “Security Via Consensus: Developing the CIS Benchmarks” (Dark Reading)
- “How to Unlock the Security Benefits of the CIS Benchmarks” (Tenable)
- “CIS Benchmarks Communities: Where configurations meet consensus” (Help Net Security)
- “CIS Benchmarks: DevOps Guide to Hardening the Cloud” (DevOps)

Juan Perez
Senior Content Marketing Manager
Juan has been writing about IT since the mid-1990s, first as a reporter and editor, and now as a content marketer. He spent the bulk of his journalism career at International Data Group’s IDG News Service, a tech news wire service where he held various positions over the years, including Senior Editor and News Editor. His content marketing journey began at Qualys, with stops at Moogsoft and JFrog. As a content marketer, he's helped plan, write and edit the whole gamut of content assets, including blog posts, case studies, e-books, product briefs and white papers, while supporting a wide variety of teams, including product marketing, demand generation, corporate communications, and events.
如有侵权请联系:admin#unsafe.sh
