September brought big updates to ANY.RUN. From four new connectors that plug our sandbox and threat intelligence straight into the world’s top SIEM and SOAR platforms, to a redesigned Threat Intelligence Lookup home screen built for speed and simplicity, your SOC now works smarter and faster than ever.
Add in 99 fresh signatures, 11 new YARA rules, and 2,322 Suricata rules, and you’ve got sharper coverage against the latest ransomware, stealers, and phishing campaigns.
Product Updates
Expanding the Ecosystem: New Connectors for Top SIEMs & SOARs
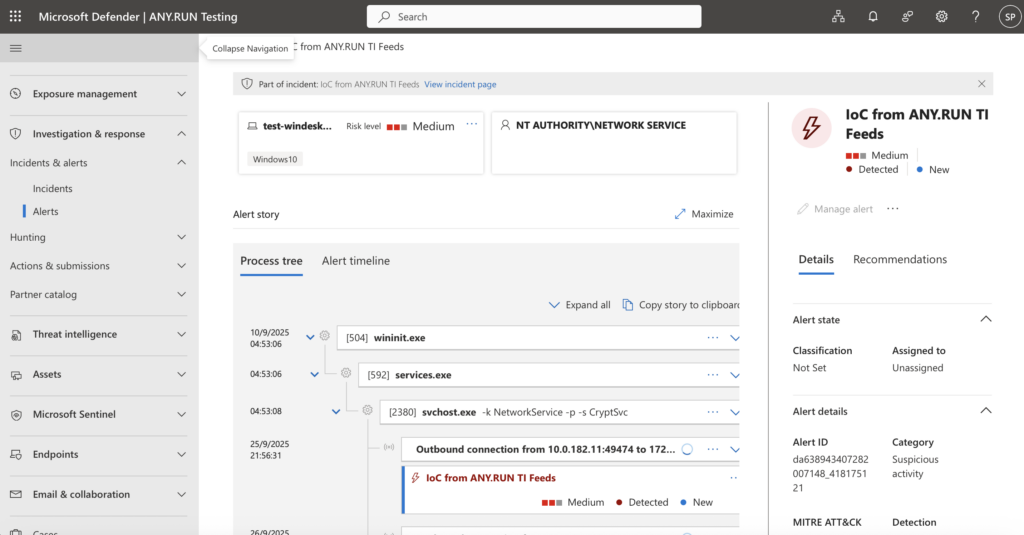
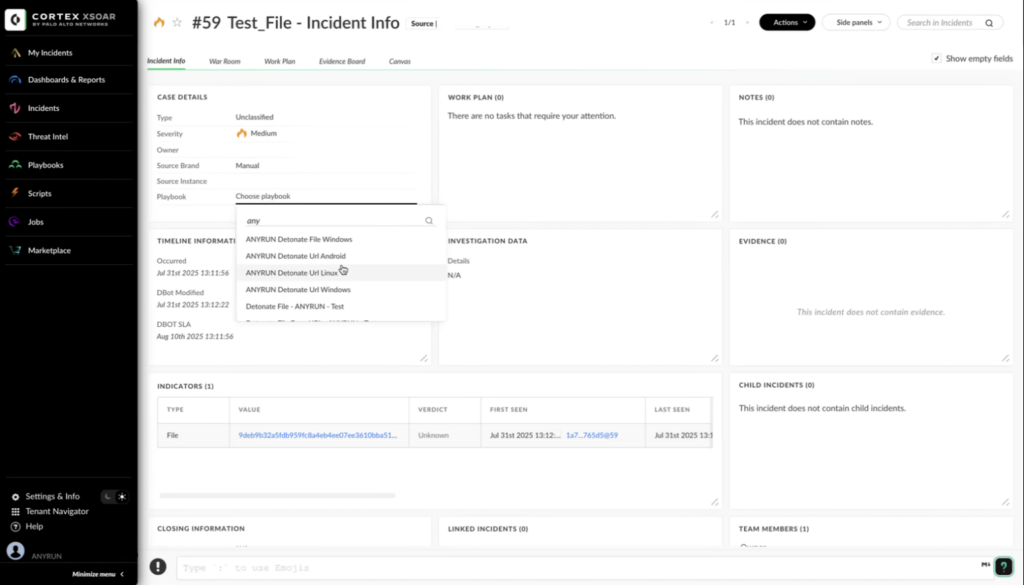
We continue to grow the ANY.RUN ecosystem so security teams can work inside familiar platforms while gaining richer, faster visibility into threats. The new integrations with IBM QRadar SIEM, Palo Alto Networks Cortex XSOAR, Microsoft Sentinel, and Microsoft Defender bring sandboxing and real-time IOCs directly into your daily workflows.
Instead of switching platforms or manually enriching alerts, analysts can now automate malware analysis, correlate logs with high-fidelity IOCs, and prioritize incidents faster; all without disrupting existing workflows.
- IBM QRadar SIEM: Enrich log and event correlation with real-time IOCs from ANY.RUN’s Threat Intelligence Feeds. Analysts can pivot from QRadar alerts straight into sandbox context for faster triage.
- Palo Alto Networks Cortex XSOAR: Build automated playbooks that include sandbox analysis enrichment, IOCs from TI Feeds, and Threat Intelligence lookup without leaving XSOAR.
- Microsoft Sentinel: Detonate suspicious files and links directly from Sentinel alerts and get enriched verdicts and IOCs fed back automatically.
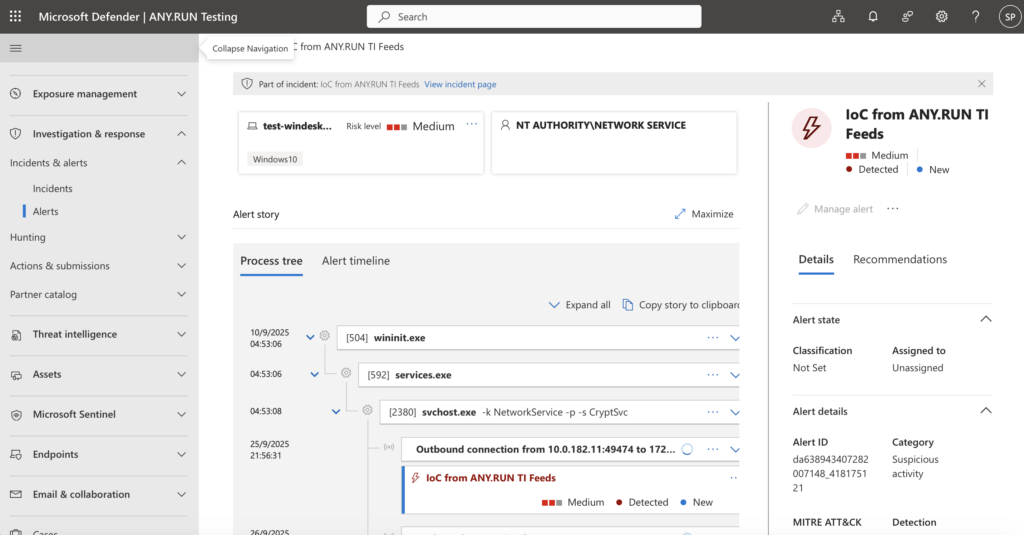
- Microsoft Defender: Enhance endpoint alerts with Interactive Sandbox insights and live Threat Intelligence Feeds, reducing manual enrichment and improving accuracy.
What Security Teams Achieve with ANY.RUN Connectors
- Early Detection: Spot threats earlier in the kill chain with live IOCs from sandbox detonations, reducing breach risk by up to 42% compared to static feeds.
- Reduced MTTR: Automating enrichment and triage cuts investigation time by up to 21 minutes per incident, accelerating containment and remediation.
- Lower Alert Fatigue: With nearly 100% malicious IOCs, analysts waste less time chasing false positives, freeing focus for true high-risk alerts.
- Higher Productivity: SOC efficiency improves by up to 3x as routine checks and manual correlation are eliminated.
Connectors use API and STIX/TAXII standards, ensuring smooth deployment with no need for workflow redesign or extra infrastructure. By leveraging existing SIEM and SOAR platforms, teams avoid duplicate tools and infrastructure, reducing total cost of ownership (TCO).
Updated Threat Intelligence Home Screen
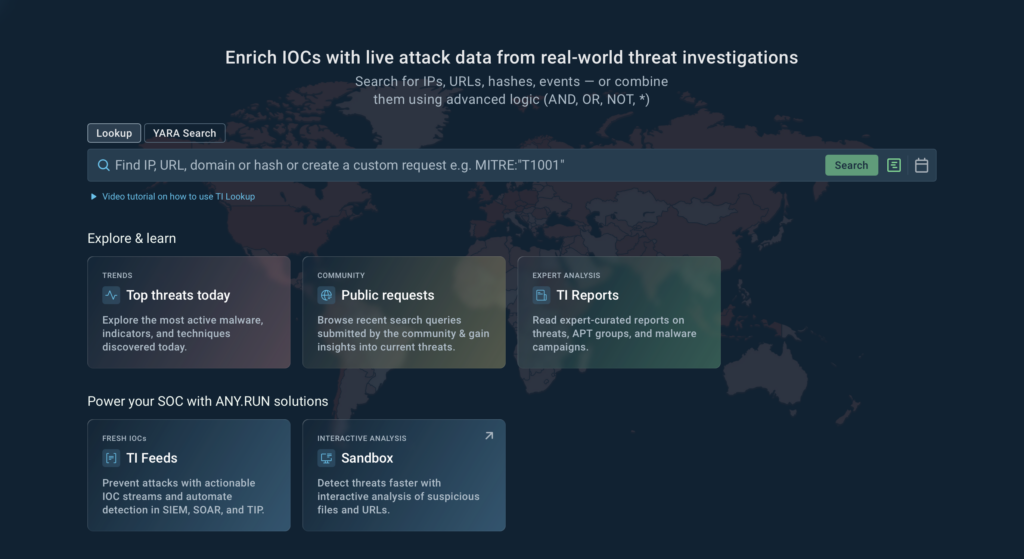
We’ve redesigned the Threat Intelligence (TI) Lookup home screen to make it more user-friendly and accessible for analysts of all levels.
The new layout now includes:
- Explore & Learn section: Quick access to daily top threats, public requests from the community, and expert-curated TI reports.
- Beginner-friendly video tutorial: A short guide to help new users start searching, enriching, and analyzing IOCs right away.
- Streamlined navigation: Cleaner interface for running lookups, YARA searches, or custom requests with advanced logic.
With these improvements, both new and experienced analysts can get to actionable threat intelligence faster, learn from the community, and explore the latest attack trends all in one place.
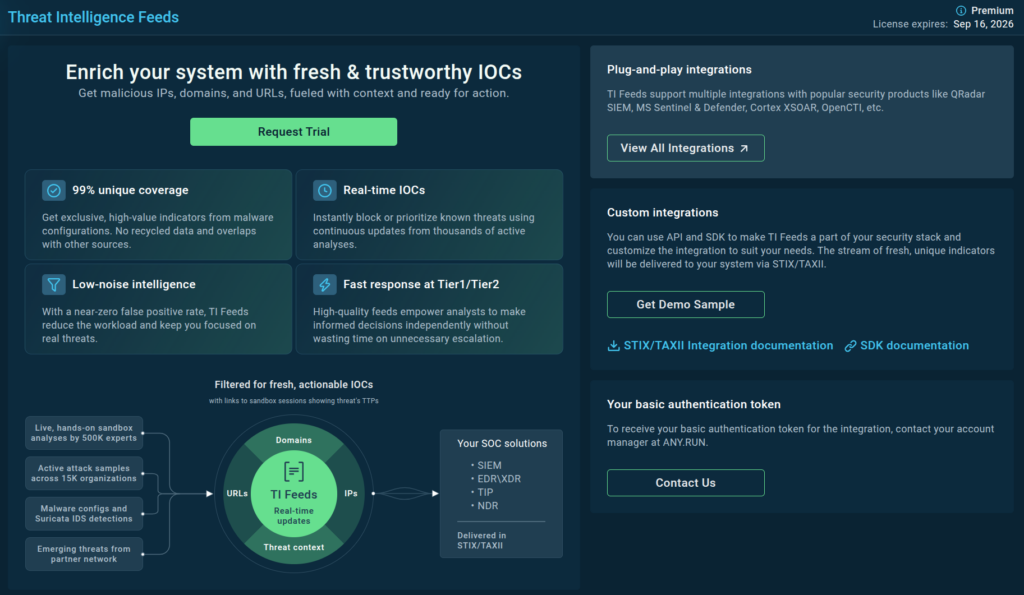
Along with the TI home screen, we’ve also updated the Threat Intelligence Feeds page. Now you can easily request a trial, download a sample, or set up an integration with your security systems in just a couple of clicks.
Threat Coverage Update
In September, our team continued to strengthen detection capabilities so SOCs can stay ahead of new and evolving threats:
- 99 new signatures were added to improve coverage across malware families and techniques.
- 11 new YARA rules went live in production, enhancing accuracy and hunting capabilities.
- 2,322 new Suricata rules were deployed, expanding detection for network-based attacks.
These updates mean analysts gain faster, more confident verdicts in the sandbox and can enrich SIEM, SOAR, and IDS workflows with fresh, actionable IOCs.
New Behavior Signatures
This month’s signatures help analysts detect obfuscation, destructive activity, and persistence earlier in the attack chain. The new coverage spans ransomware, loaders, stealers, and RATs, alongside mutex detections of legitimate tools abused by attackers.
Highlighted families and techniques include:
YARA Rule Updates
In September, we introduced 11 new YARA rules into production to help SOC teams detect emerging malware families, improve hunting accuracy, and broaden coverage across RATs, stealers, loaders, and C2 infrastructure. These rules give analysts faster verdicts and deeper visibility during investigations.
Key additions include:
New Suricata Rules
In September, we added 2,322 new Suricata rules to strengthen network-based detections against phishing, exfiltration, and evasive malware activity. These rules help SOCs identify threats earlier at the network layer and reduce investigation blind spots.
Key highlights include:
- Google Auth Phishing Activity (sid:85003912): Detects phishing attempts based on mismatched domains and authorization URLs.
- Generic Phishkit Exfiltration Attempt (sid:85003960): Flags HTTP requests from newly observed phishing frameworks, potentially PhaaS-based.
- Tycoon 2FA Domain Generation Algorithms (sids: 85004041–85004047): Identifies DGA patterns across multiple TLD zones used by Tycoon 2FA infrastructure.
About ANY.RUN
ANY.RUN supports more than 15,000 organizations worldwide across industries like banking, manufacturing, telecom, healthcare, retail, and technology, helping them build faster, smarter, and more resilient cybersecurity operations.
Our cloud-based Interactive Sandbox enables teams to safely analyze threats targeting Windows, Linux, and Android systems in under 40 seconds, with no complex infrastructure required.
Combined with Threat Intelligence Lookup and Threat Intelligence Feeds, ANY.RUN empowers SOC teams to accelerate investigations, cut risks, and improve efficiency at every stage of the threat detection workflow.
Ready to see the difference?