Sep 16 2025
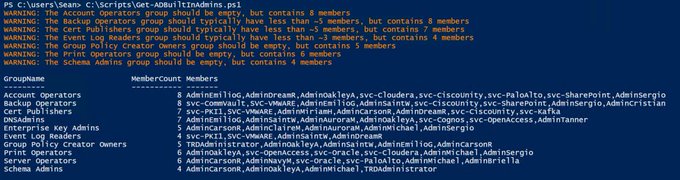
There are several default/built-in privileged groups that should be reviewed:
- Account Operators – should be empty per Microsoft due to highly privileged access in AD.
- Backup operators – should only contain backup service accounts to backup and restore Active Directory.
- Cert Publishers – should only contain PKI related accounts (CAs & related service accounts) since it can publish certificates for AD users.
- DNSAdmins – typically only used when admins other than ADAs perform DNS administration. Use sparingly. * Enterprise Key Admins – have admin rights on key objects in AD.
- Event Log Readers – should only include accounts that require access to Domain Controller event logs.
- Group Policy Creator Owners – can modify Group Policies in the domain. Membership should be empty and rights delegated instead.
- Print Operators – used only when a Domain Controller is used as a print server (which shouldn’t happen). Group has the ability to logon to Domain Controllers and install drivers which makes this group highly privileged. Group should be empty.
- Server Operators – effectively local admin on Domain Controllers. Use sparingly.
- Schema Admins – should be empty except when updating the AD schema.
https://learn.microsoft.com/en-us/windows-server/identity/ad-ds/manage/understand-security-groups

PowerShell Script leveraging the Active Directory PowerShell module:
https://github.com/PyroTek3/Misc/blob/main/Get-ADBuiltInAdmins.ps1
(Visited 16 times, 16 visits today)