Swamped by incident alerts, Security Operations Centers (SOCs) struggle to quickly identify and prioritize high-risk attacks, leaving critical infrastructure exposed to ransomware and data theft. ANY.RUN’s integration with Palo Alto Networks Cortex XSOAR solves this by automating proactive sandbox analysis and threat intelligence correlation to beat alert fatigue, boost detection rates, and accelerate security workflows.
ANY.RUN & Palo Alto Networks Cortex XSOAR Integration
Security Operations Centers (SOCs) using Palo Alto Networks Cortex XSOAR can now seamlessly integrate ANY.RUN’s products into their workflows.
The ANY.RUN content pack includes connectors for the Interactive Sandbox, Threat Intelligence Lookup, and Threat Intelligence Feeds, empowering SOCs to streamline alert triage, broaden threat detection, and improve identification of elusive malware.
Set up the integration in your workspace →
With the ANY.RUN content pack, organizations can:
- Detect evasive threats faster with automated sandbox analysis for stronger protection.
- Prevent attacks proactively using real-time threat data to reduce breach risks.
- Clarify incidents with enriched threat context for quicker, more accurate response.
- Reduce alert overload by automating analysis and response, saving SOC time.
- Ensure compliance with secure, private workflows for safe operations.
- Strengthen security posture by integrating sandboxing, threat data, and XSOAR automation.
Interactive Sandbox in Palo Alto Networks Cortex XSOAR
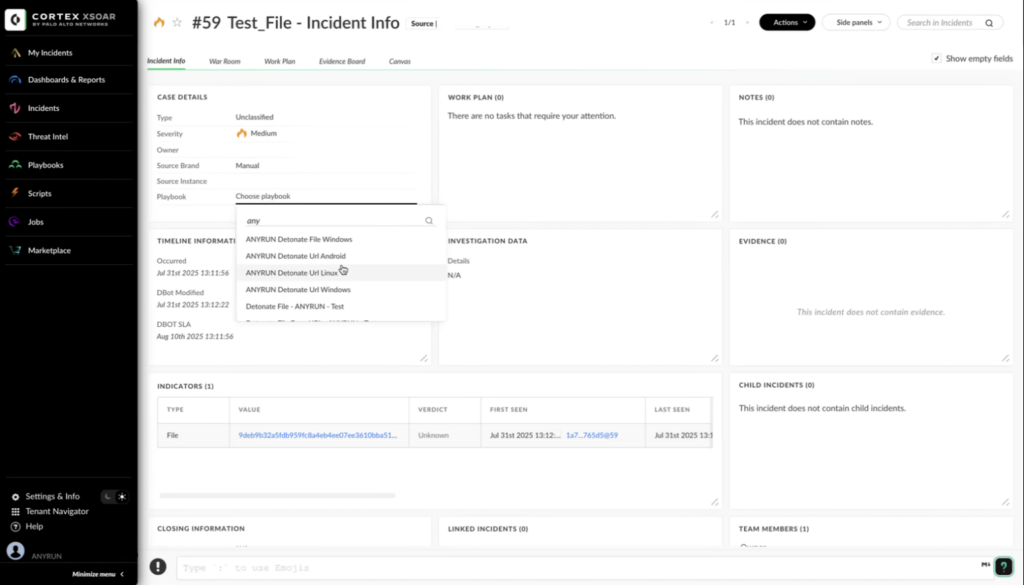
ANY.RUN’s Interactive Sandbox is a cloud-based solution offering SOC teams immediate, real-time access to Windows, Linux, and Android virtual environments for analyzing suspicious files and URLs.
With the ANY.RUN’s Interactive Sandbox in Cortex XSOAR, users can:
- Submit a file, remote file, or URL for analysis across Windows, Ubuntu, or Android operating systems.
- Retrieve detailed report details and IOCs for a specific analysis in JSON, HTML.
- Download file submission samples and analysis network traffic dumps for deeper incident response insights.
Benefits of the Interactive Sandbox in Palo Alto Networks Cortex XSOAR
- Higher detection rate: Automated Interactivity ensures even evasive attacks are fully detonated and identified.
- Faster incident resolution: Quick insights accelerate response to critical threats.
- Reduced alert fatigue: Focus only on severe incidents, while the sandbox identifies.
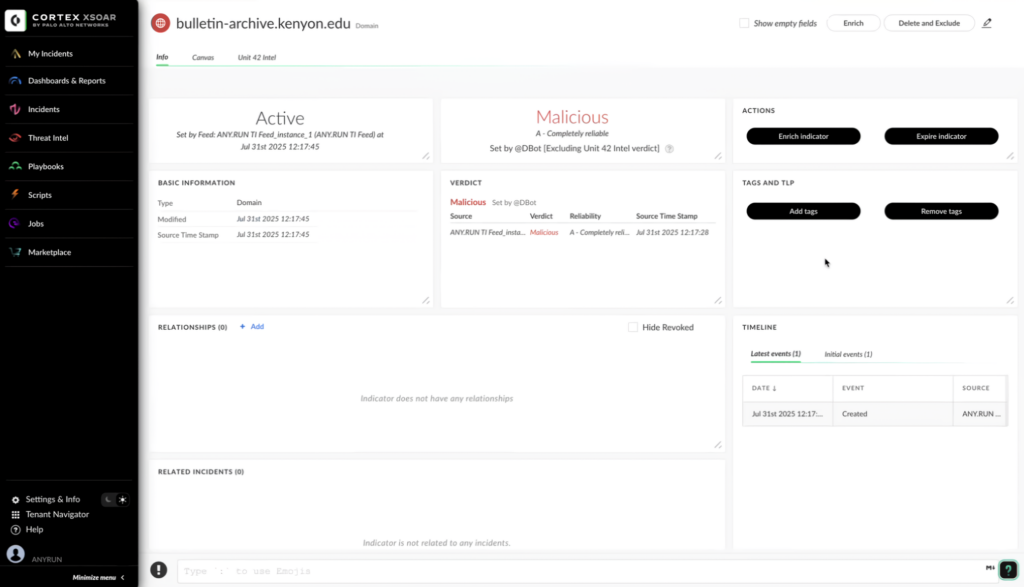
Threat Intelligence Feeds in Palo Alto Networks Cortex XSOAR
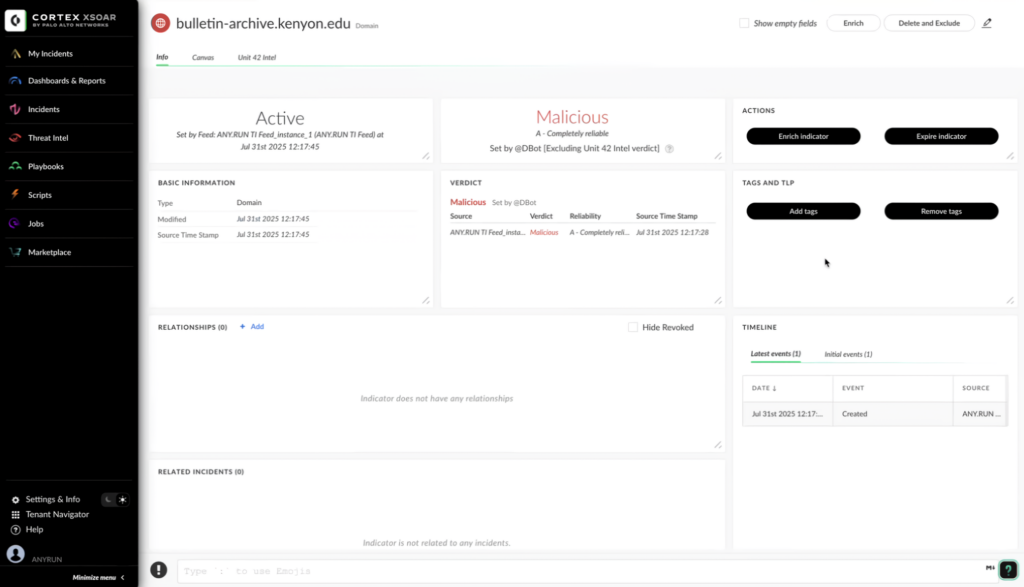
ANY.RUN’s Threat Intelligence Feeds empower SOCs and MSSPs to strengthen security with high-fidelity, actionable IOCs from real-time sandbox analysis. New indicators are continuously added to TI Feeds from sandbox investigations across 15,000+ organizations after filtering. This means you get a curated stream of malicious IPs, domains, and URLs that have been active for no more than several hours and can still be used to detect attacks that are happening right now.
With ANY.RUN’s Threat Intelligence Feeds in Cortex XSOAR, users can:
- Correlate feed data with incoming alerts to identify high-risk threats.
- Use indicators to create new detection rules for proactive threat mitigation.
- Automate threat hunting and response workflows using XSOAR playbooks.
Benefits of Threat Intelligence Feeds in Palo Alto Networks Cortex XSOAR:
- Expanded threat coverage: Real-time IOCs from 15,000+ organizations catch diverse threats.
- Enhanced threat prioritization: Correlating alerts with IOCs highlights critical risks.
- Proactive attack prevention: Fresh intelligence enables early threat detection.
Threat Intelligence Lookup in Palo Alto Networks Cortex XSOAR
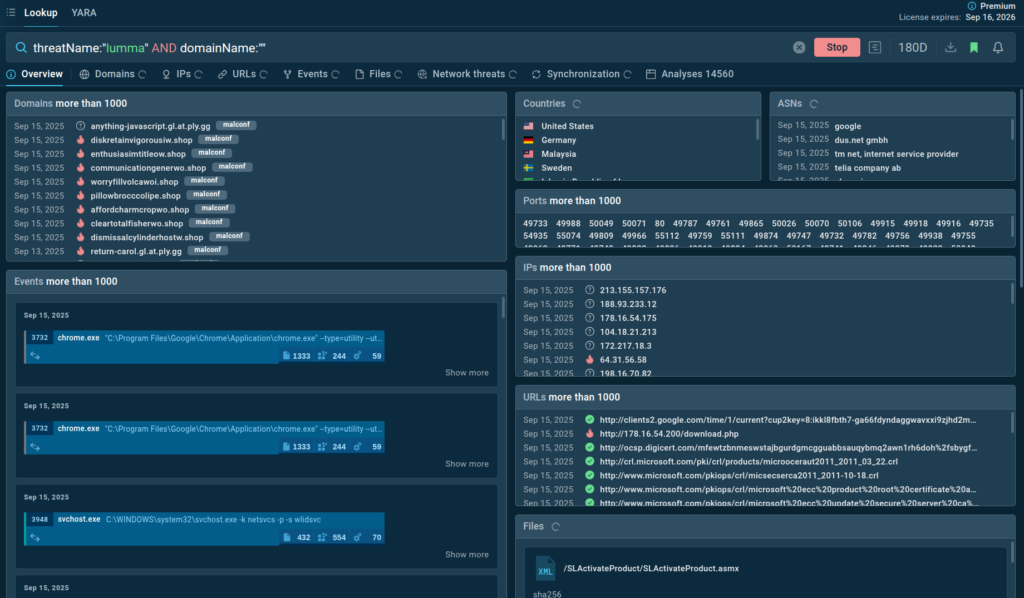
ANY.RUN’s Threat Intelligence Lookup offers a searchable database of up-to-date IOCs, IOBs, and IOAs, drawn from real-time sandbox analysis of active malware and phishing attacks across 15,000+ organizations (Learn more about TI Lookup’s capabilities). This ensures fresh, actionable threat data is available swiftly post-attack.
With the ANY.RUN’s Threat Intelligence Lookup in Cortex XSOAR, users can:
- Perform deep searches for IOCs, IOAs, and IOBs to uncover detailed threat intelligence.
- Enrich incident investigations with extensive context on threats.
- Search threat info by parameters like threat level, OS, or submission country for targeted investigations.
Benefits of Threat Intelligence Lookup in Palo Alto Networks Cortex XSOAR
- Greater incident clarity: Rich threat data provides precise attack context.
- Broader threat insight: Detailed IOC/IOA/IOB analysis expands attack understanding.
- Enhanced threat hunting: Targeted searches help identify hidden threats effectively.
About ANY.RUN
Trusted by over 500,000 cybersecurity professionals and 15,000+ organizations in finance, healthcare, manufacturing, and other critical industries, ANY.RUN helps security teams investigate threats faster and with greater accuracy.
Our Interactive Sandbox accelerates incident response by allowing you to analyze suspicious files in real time, watch behavior as it unfolds, and make confident, well-informed decisions.
Our Threat Intelligence Lookup and Threat Intelligence Feeds strengthen detection by providing the context your team needs to anticipate and stop today’s most advanced attacks.
Ready to see the difference? Start your 14-day trial of ANY.RUN today →