Active Directory计算机管理建议每年审查一次,处理旧操作系统和停用设备。通过LastLogonDate和PasswordLastSet属性判断设备活跃状态,并使用PowerShell脚本进行自动化检查。 2025-9-16 00:3:0 Author: adsecurity.org(查看原文) 阅读量:21 收藏
Sep 15 2025
Active Directory computers should be reviewed about once a year. Old operating systems can hold back security progress like keeping SMBv1 and NTLMv1 active. Inactive computers should be discovered and disabled when no longer in use (and eventually removed).
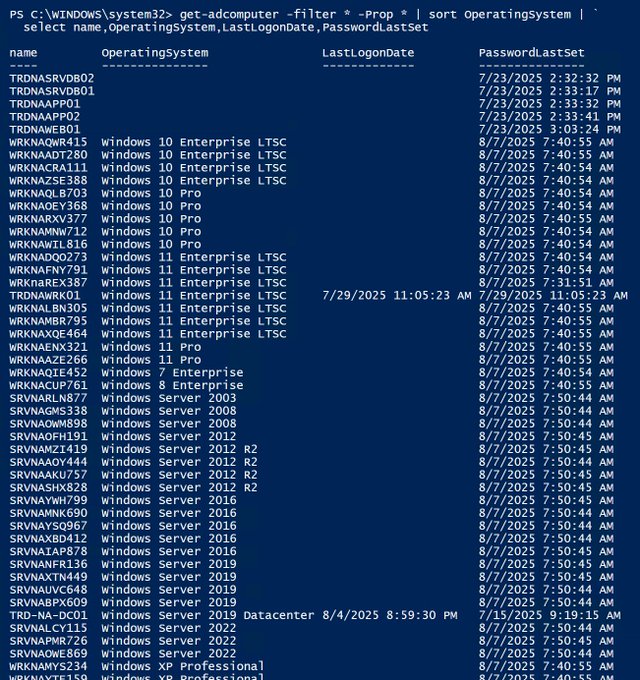
The OperatingSystem & PasswordLastSet attributes are self-explanatory, though we can use the LastLogonDate which represents the last reboot of the computer. The computer password should change every ~30 days by default. We can correlate the PasswordLastSet & LastLogonDate attribute values to determine if a computer is active or not. A blank LastLogonDate value means the computer object is just that and not associated with an actual system.
Computer Password Information

PowerShell code (using the Active Directory PowerShell module):
$Domain = $env:userdnsdomain
$DomainDC = (Get-ADDomainController -Discover -DomainName $Domain).Name
Get-ADComputer -filter * -Prop name,OperatingSystem,LastLogonDate,PasswordLastSet -Server $DomainDC | sort OperatingSystem | select name,OperatingSystem,LastLogonDate,PasswordLastSet(Visited 14 times, 14 visits today)
如有侵权请联系:admin#unsafe.sh
