
文章概述了网络安全领域的最新动态:美国起诉并制裁多个网络犯罪分子及诈骗网络;GitHub遭遇大规模供应链攻击“GhostAction”,泄露数千个敏感信息;同时警告中国涉嫌利用钓鱼邮件进行政治间谍活动。 2025-9-12 16:24:10 Author: www.sentinelone.com(查看原文) 阅读量:17 收藏
The Good | U.S. Charges Ransomware Operator, Sanctions $10B Scam Networks & Secures BlackDB Guilty Plea
Kosovo national Liridon Masurica (33), has pleaded guilty to operating BlackDB[.]cc, a cybercrime marketplace active online from 2018 to 2025. Arrested in December 2024 and extradited to the U.S. this May, Masurica has admitted to selling stolen credit cards, compromised accounts, server credentials, and personally identifiable information (PII), primarily from U.S. victims. Cybercriminals would purchase and use the data for identity theft, tax fraud, and financial crimes. Charged with six counts of fraud, Masurica faces up to 55 years in prison.
While Masurica’s conviction highlights the dangers of underground markets, U.S. authorities are also focusing on larger-scale fraud networks. The Department of the Treasury has sanctioned major cyber scam networks in Myanmar (formerly Burma) and Cambodia that stole over $10 billion from Americans in 2024, a 66% increase from 2023. These operations, often run with forced labor and human trafficking, engage in romance scams and fake crypto schemes. OFAC named 19 individuals and entities tied to the Karen National Army (KNA) and Cambodian crime groups. The sanctions freeze U.S. assets, cut access to international finance, and disrupt operations despite no arrests.
Building on these actions, the U.S. Department of Justice has charged Ukrainian national Volodymyr Tymoshchuk (aka deadforz, Boba, msfv, and farnetwork) for administering the LockerGoga, MegaCortex, and Nefilim ransomware operations. From 2019 to 2021, he and accomplices breached over 250 companies worldwide, stealing millions and disrupting critical services. Tymoshchuk allegedly managed Nefilim, granting affiliates access for a share of ransom payments. Already on FBI and EU most wanted lists, he faces multiple fraud and computer crime charges. The U.S. State Department is offering $10 million for information leading to his capture.

The Bad | ‘GhostAction’ Supply Chain Attack Exfiltrates Thousands of Secrets from GitHub
Cyber researchers have uncovered a large-scale software supply chain attack on GitHub dubbed “GhostAction”, which has exposed more than 3,300 secrets, including PyPI, npm, DockerHub, GitHub tokens, Cloudflare API keys, AWS access keys, and database credentials so far.
The campaign came to light after suspicious activity was detected in the FastUUID project on September 2. Attackers had compromised maintainer accounts and injected a malicious GitHub Actions workflow designed to trigger on code pushes or manual dispatch.
Once activated, the workflow harvested secrets from the environment and exfiltrated them via a curl POST request to an attacker-controlled server. In FastUUID’s case, its PyPI token was stolen, though no malicious package uploads were made prior to the breach being contained.
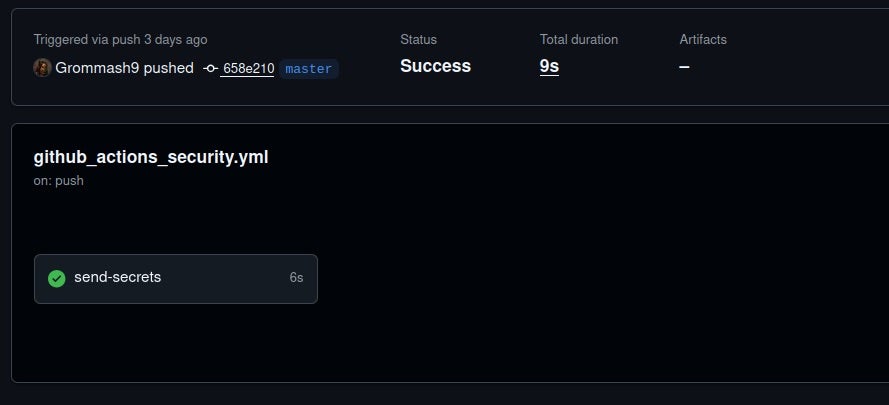
Further investigation revealed that the incident was far more widespread than just FastUUID. At least 817 repositories were found to contain similar malicious commits, all sending stolen secrets to the same endpoint. To maximize the theft, attackers enumerated secret names from legitimate workflows, then hardcoded them into their own scripts.
By September 5, researchers had notified GitHub, npm, and PyPI, while also filing issues across 573 impacted repositories. One hundred projects, at this point, had already detected and reverted the malicious commits. Soon after disclosure, the exfiltration endpoint was taken offline, but not before significant damage occurred.
The exposure affects at least nine npm and 15 PyPI packages, leaving open the possibility of malicious releases unless maintainers revoke compromised tokens. While the campaign shares similarities with the AI-powered ‘s1ngularity’ attack on over 2100 GitHub accounts from August, researchers believe GhostAction is altogether a separate operation.
The Ugly | House Panel Warns of Chinese Cyber Espionage Exploiting Political Communication
Highly targeted cyber espionage campaigns amidst tense trade negotiations between the U.S. and China have led the House Select Committee on China to issue an advisory warning. These campaigns, linked to the PRC, are focused on U.S. government agencies, business groups, law firms, and think tanks while the two economic powers continue talks on tariffs and diplomacy.
According to the committee, suspected threat actors based in China impersonated Republican Party Congressman John Robert Moolenaar (R-MI) in phishing emails sent out to trusted contacts. The emails, framed as requests for input on sanctions against China, carried attachments that deployed malware to steal sensitive data and establish persistence. So far, the actors are believed to be APT41, a prolific state-backed group known for global espionage campaigns.

Moolenaar, who is also the Chairman of the House Select Committee, stressed that these attacks aim to steal U.S. strategy and leverage it against Congress, the Administration, and the American people. Historically, the campaign aligns with tactics often used by state-sponsored threat actors, including abuse of cloud services and legitimate software to obscure activity and exploit personal or unofficial communication channels. The Chinese embassy has rejected the allegations, stating it “firmly opposes and combats all forms of cyber attacks and cyber crime” and opposes accusations without solid evidence.
Adversaries are increasingly exploiting the extension of modern political communication. Not all exchanges occur over official government accounts or devices, and attackers are capitalizing on trusted officials that engage with partners through personal or less-secure channels. By masquerading as familiar public figures and using the right lures, they can amplify authenticity and carry out their objectives while evading detection.
如有侵权请联系:admin#unsafe.sh