VMRay Labs团队在2025年8月专注于提升威胁检测能力,新增多项威胁标识符以识别钓鱼攻击、恶意进程行为及系统修改;更新配置提取器以支持更多恶意软件分析;增强自动交互功能以应对新型钓鱼手法;并新增20多条YARA规则以加强恶意软件检测能力。 2025-9-11 10:8:56 Author: www.vmray.com(查看原文) 阅读量:20 收藏
The Labs team at VMRay actively gathers publicly available data to identify any noteworthy malware developments that demand immediate attention. We complement this effort with our internal tracking and monitor events the security community reports to stay up-to-date with the latest changes in the cyber threat landscape.
In August 2025, the VMRay Labs team has been focused on the following areas:
1) New VMRay Threat Identifiers addressing:
- URLs and domains with phishing-heavy gTLDs
- Detecting executables that terminate after checking the keyboard layout
- Detecting downloads and execution of binaries with different architectures
- Detecting starting a new service in Linux environment
- Detecting loading of kernel extensions
- Detecting process enumeration via API
- Detecting reconnaissance via system utilities
- Detecting overwriting /etc/hosts
- Detecting redirecting CMD output to files in suspicious paths
2) New or updated Configuration Extractors for:
- Vidar v14.6
- CryptBot
- Improved Lumma v6 extractor
- Improved StealcV2 extractor
- Improved Rhadamanthys extractor
3) AutoUI enhancements addressing recent phishing tricks, including:
- Support interaction with Notion-based phishing
- Support interaction with new phishing campaigns requesting choosing a country
4) +20 new YARA rules
Now, let’s delve into each topic for a more comprehensive understanding.
New VTIs
In a few last blog posts, we introduced you to the concept of the VMRay Threat Identifiers (VTIs). In short, VTIs identify threatening or unusual behavior of the analyzed sample and rate the maliciousness on a scale of 1 to 5, with 5 being the most malicious. The VTI score, which greatly contributes to the ultimate Verdict of the sample, is presented to you in the VMRay Platform after a completed analysis. Here’s a recap of the new VTIs that we added, or improved in the past month.
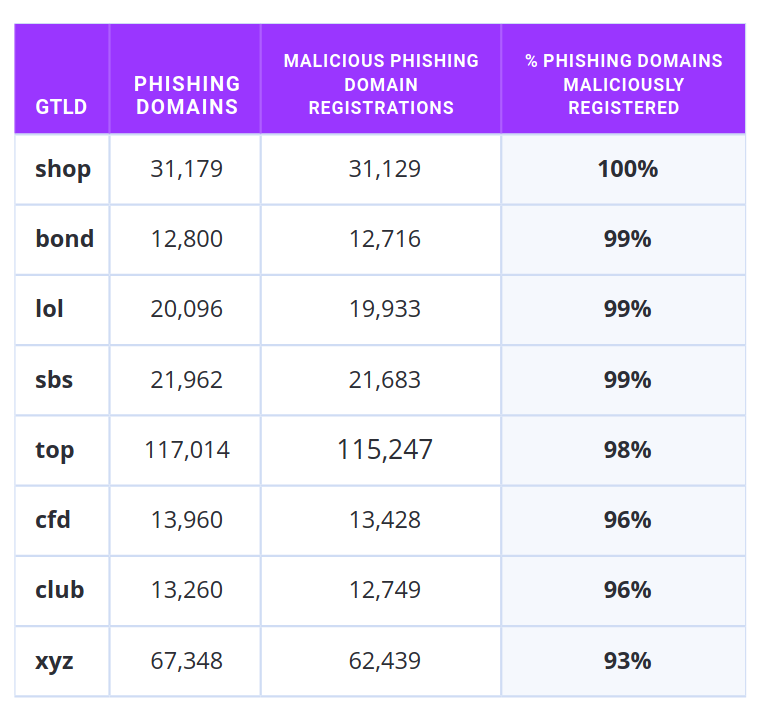
Flagging URLs and domains with phishing-heavy gTLDs
Category: Heuristics
One of the latest additions to our VTIs focuses on a powerful signal – the use of certain new generic top-level domains (gTLDs) in phishing campaigns. Over the past several months, our Labs team analyzed large volumes of submissions to uncover patterns in domain usage. We noticed that some newer or unusual gTLDs, such as “.shop”, among others, appear disproportionately often in phishing attacks. These domains are inexpensive, easy to register, and provide threat actors with a seemingly endless pool of names to abuse.
Similar to the Smart Link Detonation rule we improved last quarter, we now also flag URLs with a VTI whenever a submission contacts a URL with a flagged gTLD, in addition to recursively submitting it.
Detecting executables that terminate after checking the keyboard layout
Category: DefenseEvasion
MITRE ATT&CK® Technique: T1614
One tactic we’ve recently addressed and now covered with a new VTI is malware that checks the system’s keyboard layout and then exits prematurely. Legitimate software rarely terminates simply because of a user’s keyboard layout. But in the malware world, this check is often a form of environment-aware evasion and serves as a mean to:
- Inspect the keyboard layout to reason out the system’s locale
- Exclude execution in countries that threat actors operate for
- If a “forbidden” locale is detected, the malware may terminate before its malicious payload runs, preventing exposure to analysis and avoiding unintended infections
Our new VTI detects a specific suspicious sequence of gfn calls that queries the keyboard layout and then terminates before the timeout period.
Detecting downloads and execution of binaries with different architectures
Category: Execution
Attackers are constantly looking for ways to maximize the reach of their malware. One technique we’ve seen in families like IoT-focused Mirai botnet is the use of multiple binaries compiled for different CPU architectures, all attempted in sequence.
Legitimate software typically has a clear architectural target: x86 or x64. Normal applications don’t need to fetch and execute a wide range of binaries for different architectures. In contrast, malware does this for several reasons:
1) Compatibility across environments: Threat actors want their payloads to run on as many systems as possible. By including multiple architecture variants, they improve the odds that at least one binary will successfully execute.
2) Redundancy against failures: If one version crashes, encounters restrictions, or lands in an unsupported environment, another variant may still work.
3) Evasion of analysis: Some sandboxes only emulate or monitor specific architectures (e.g.: often 32-bit). By testing and executing multiple versions, malware can bypass incomplete analysis coverage and reduce its chance of being fully exposed.
Our new VTI will trigger whenever a process will try to execute multiple binaries of different CPU architectures.
Detecting starting a new service in Linux environment
Category: Execution
MITRE ATT&CK® Technique: T1569/003/
Linux malware often seeks persistence and stealth, and one way to achieve both is by abusing system services. Our latest VTI detects when a process attempts to start a new service using systemctl, the command-line tool for interacting with systemd, the init system and service manager. It’s central to controlling system services, checking their status, and managing system states.
Legitimate administrators use systemctl to manage services like web servers, databases, or background daemons. However, malware can exploit it for malicious purposes such as: persistence, elevated privileges or continuous execution.
A typical attack pattern might look like this:
- Drop a malicious binary to
/usr/local/bin/malware. - Create a
systemdunit file/etc/systemd/system/malware.servicepointing to the binary. - Run
systemctl enable malware.serviceto start at boot andsystemctl start malware.serviceto run immediately.
By doing this, the malware ensures persistent execution, stealth, and automated malicious activity.
Detecting loading of kernel extensions
Category: Persistence
MITRE ATT&CK® Technique: T1547/006
Malware often seeks to establish persistent, high-privilege access to a system, and one way to do this on Linux or macOS is through Loadable Kernel Modules (LKMs) or kernel extensions (KEXTs). Our latest VTI detects when a process attempts to load such extensions.
Kernel extensions are pieces of code that can be loaded into the operating system kernel on demand, extending its functionality without a reboot. While legitimate uses include device drivers and system enhancements, malicious use is highly dangerous because of:
- Highest privilege level: Kernel extensions run in ring 0, giving malware almost unrestricted control over the system.
- Persistence: Malicious modules can automatically load at boot, ensuring the malware executes before most defenses are active.
- Stealth: Kernel-mode rootkits can hide themselves, files, processes, and network activity, as well as tamper with logs.
- Advanced Capabilities: LKMs can manipulate system calls, intercept hardware or network requests, and provide authenticated backdoors for attackers.
A malware sample may load a kernel module to:
- Hide its presence on the system.
- Intercept system or network activity.
- Maintain root-level access across reboots.
Our new VTI triggers when a process attempts to install or load a kernel extension, signaling a potentially malicious attempt to establish high-privilege access on the system.
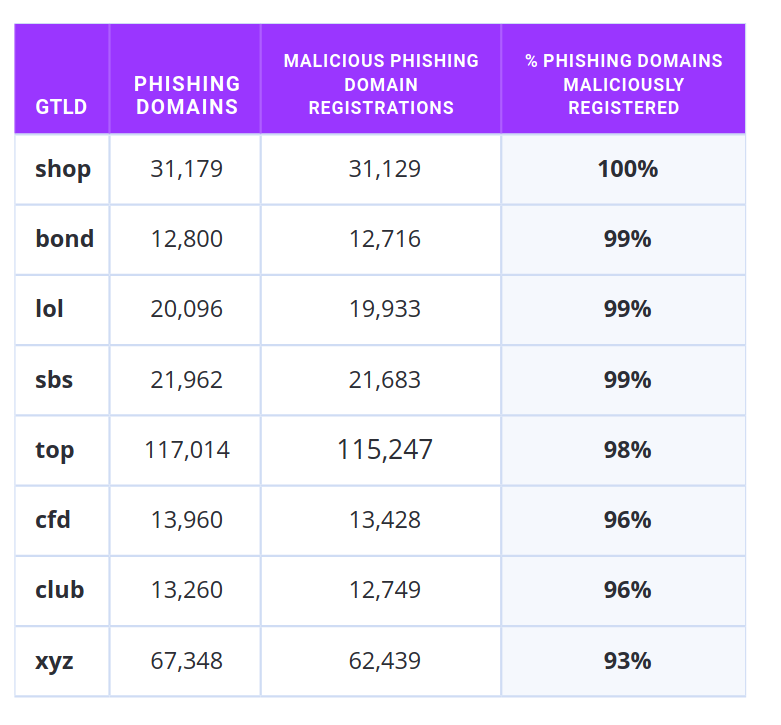
Detecting process enumeration via API
Category: Discovery
MITRE ATT&CK® Technique: T1057
During recent analysis, we observed a sample leveraging a low-level system call for process discovery. At runtime, the sample invoked NtQuerySystemInformation, retrieving a complete list of running processes. The malware then compared this list against a hardcoded set of AV and security-related process names. Unlike other enumeration methods, NtQuerySystemInformation is a native Windows API that . It provides malware with a richer, more detailed view of the system, including:
- Full process image names
- Process IDs and parent process IDs
- Thread counts and CPU usage times
This makes the technique valuable for environment profiling and defense evasion, as it allows malware to spot security tools that might otherwise attempt to conceal themselves from higher-level APIs.
Detecting reconnaissance via system utilities
Category: Discovery
MITRE ATT&CK® Technique: T1082
In recent analysis, we observed a malware sample leveraging native Windows utilities for host reconnaissance and connectivity checks. Specifically, the malware executed two behaviors:
1) The malware invoked systeminfo.exe through cmd.exe to collect detailed host information, including:
- OS version and build number
- Installed hotfixes and patch level
- System architecture (x86/x64)
- Domain/workgroup membership
This information enables attackers to fingerprint the system for profiling, assess target value (), or select payloads or exploits based on OS version and patch state.
2) The sample also used ping.exe to test external connectivity. In this case, requests were sent to well-known public DNS services such as Google (8.8.8.8, 8.8.4.4, google.com).
This activity likely served multiple purposes:
- Internet connectivity check, ensuring the host can reach external networks
- DNS resolution validation, confirming the system can resolve domains (critical for contacting C2 servers)
- Fallback behavior – if connectivity fails, the malware may delay, switch to offline actions, or attempt later
Our new VTI will now trigger when either of these behaviors is detected.
Detecting overwriting /etc/hosts
Category: System Modification
The file /etc/hosts is a plain text configuration file found on Unix-like operating systems (Linux, macOS, etc.). Normally, when you something like google.com, your computer asks the DNS system to find the right server. But before it asks DNS, it first checks its own local “address book”, so the file called /etc/hosts. If /etc/hosts says “google.com = 1.2.3.4“, then your computer will go to 1.2.3.4, even if the real Google is somewhere else. This means /etc/hosts can override the real internet addresses.
Recently we observed a sample that opens /etc/hosts with write permissions and overwrites its content. This behavior is highly suspicious as malware could:
- Redirect traffic for legitimate domains (e.g., banking sites, update servers, antivirus sites) to attacker-controlled IPs
- Block access to security update servers or antivirus vendors
- Funnel all traffic for certain domains into a malicious location
It’s really a red flag as, normal applications almost never need to overwrite /etc/hosts. Even system administrators usually just append entries, not wipe the file. To address this threat, our new VTI will trigger on attempts to modify the etc/hosts.
Detecting redirecting CMD output to files in suspicious paths
Category: Defense Evasion
MITRE ATT&CK® Technique: T1218
One trick malware often uses to stay under the radar is quietly running system commands in the background. On Windows, this usually happens through cmd.exe, the command-line program built into the system.
Here’s the suspicious part: instead of just running a command, the malware redirects the output (the results of that command) to unusual or suspicious file paths. But why this should raise concerns? In normal software it is quite common that applications run the cmd.exe, but redirecting its output to a temp folder or strange locations is more suspicious. Attackers, on the other hand, may use this trick to hide traces of what they’re doing. By redirecting output, they may potentially:
- Collect system information (like user accounts or network settings).
- Store logs of what worked or failed during the attack.
- Hide their tools and results somewhere defenders aren’t looking.
In the past month, we added Configuration Extractors for the malware families mentioned below:
Vidar is an info stealer, based on Arkei stealer, and well-known for abusing platforms such as Steam, Telegram or Twitter as part of their command and control (C2) infrastructure.
The latest release, Vidar v14.6, introduced changes to its internal configuration layout. This update meant our existing extractor no longer worked out of the box. After analyzing the new structure, we adapted our tooling so that configuration data can now be successfully parsed from this version as well.
CryptBot is an info stealer that targets users’ sensitive data, often focusing on cryptocurrency-related information. It’s known for stealing login credentials, private keys, and other sensitive data from cryptocurrency wallets, as well as from browsers, financial applications, and other services.
To keep up with the evolving tactics of cybercriminals, we implemented a new config extractor for the CryptBot malware family.
Main extractable fields include:
- C2 domains – helps identify the command-and-control servers used by CryptBot.
- Payload URL – extracts the location from which the malware downloads additional malicious payloads.
In addition to the main fields, we can now extract a variety of other critical configuration details that CryptBot uses to target and steal data. These include (and there’s much more!):
- Browser data
- Wallet data
- File locations
- System and user data
- Anti-detection and persistence
Lumma is an info stealer malware that has been active since 2022. Sold as Malware-as-a-Service (MaaS), it primarily targets cryptocurrency wallets and two-factor authentication (2FA) browser extensions. With one of its latest versions, Lumma v6, we updated our configuration extractor to provide better visibility into mission IDs. These mission IDs are unique identifiers used by attackers to tag infections or campaigns, helping them organize stolen data and control malware behavior.
is the new version of the infamous StealC infostealer, written in C++, released in March, 2025. The new v2 version features a custom RC4-encryption for obfuscating its internal strings and its network traffic. StealCv2 can steal credentials from cryptowallets, game clients, VPN software, and many messenger applications.
Rhadamanthys is an info stealer with lots of evasion techniques embedded. It’s mainly spreading via malicious websites mimicking geniune software, like AnyDesk, Zoom, Teams and others. These malicious websites are promoted through Google Ads to increase user drive-by traffic and successful installation of the malware.
To ensure our Platform is up-to-date with config extractors for top 10 malware families seen in 2025 Q2, we improved the config extraction for Rhadamanthys.
AutoUI Enhancements
Support interaction with Notion-based phishing
In a recent phishing campaign, attackers attempted to harvest Microsoft credentials by distributing emails that contained links to notion.site pages. The phishing emails pointed to seemingly legitimate Notion pages, which then redirected users to malicious sites. This impersonation tactic is similar to what we’ve previously seen with phishing campaigns abusing Google Drive and other trusted platforms.
Until now, our Auto UI feature already supported automatic interaction with many common phishing delivery methods. With this latest enhancement, Auto UI can now detect and interact with Notion pages during automated analysis.
Support interaction with new phishing campaigns requesting choosing a country
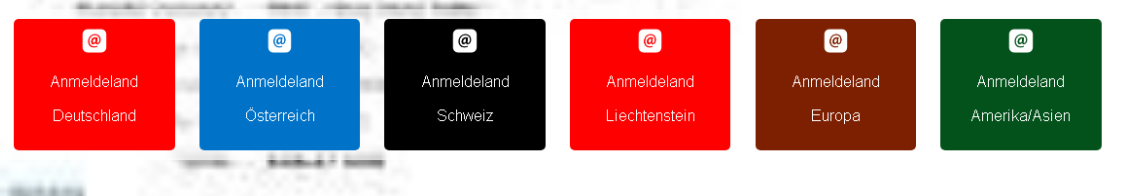
Building on our recent support for Notion-based phishing detection, we enhanced Auto UI to better handle multi-stage phishing campaigns.
In the observed case, after a user clicked a malicious notion.site link, they were redirected to a page masquerading as a OneNote “country selection” splash screen. The page displayed multiple clickable tiles, each representing a different region (e.g., Germany, Austria, Switzerland, USA/Asia). Importantly, the actual login form and malicious payload were only revealed after a country option was selected.
Phishing authors might introduce these intermediate steps for several reasons:
- Target filtering: ensuring only victims in selected regions see the final phishing page.
- Localization: tailoring phishing pages to a victim’s language or region to improve credibility.
- Selective delivery: skipping regions the attackers don’t want to target (often their home countries).
To expose these attacks, VMRay’s Auto UI has been upgraded with logic to handle such “region selection” prompts. By doing so, Auto UI ensures the hidden login form and payload delivery are revealed for full inspection.
YARA Rules Update
Our hunt for new YARA rules never stops. Over the past months, we added more than 140 fresh YARA rules to strengthen detection across a wide range of threats. This month, we’re continuing that momentum with 20+ new rules, focused on delivering a solid drop of high-quality detections. Here’s a quick preview of what we’re shipping this month.
EDRKillShifter
Scavenger
BlackMatter (Windows)
Pearl Stealer (MacOS)
CastleLoader
Gunra ransomware (Linux)
SquidLoader
Ducktail
CherryLoader
RemoteManipulatorSystem ()
MarsStealer
SharkStealer
Byt3rRansomware
SSDDestroyer
KillMBR
RavenStealer
QatarRAT
AuKill EDR Killer
TodoSwift (MacOS)
WEEVILPROXY
New rule on FakeAudioVideo-style phishing
New rule on Press&Hold CAPTCHA-style phishing
New rules for Phishkit.B36 and Phishkit.Acode
Final Thoughts
August 2025 was a busy month for our Labs team, marked by major enhancements to our VMRay Threat Identifiers, configuration extractors and a broadened, fine-tuned YARA rule set spanning multiple threat categories. As attackers refine their tactics, our ongoing commitment remains clear — to stay ahead of the curve, proactively enhancing detection, and equipping defenders with the tools needed to counter modern cyber threats. Stay tuned for our next edition of signature and detection updates, planned to be published in the weeks ahead.
如有侵权请联系:admin#unsafe.sh