
文章讲述了保险公司面临的数据安全威胁及通过渗透测试发现开发环境中的重大漏洞,并采取措施加强身份安全和风险管理的故事。 2025-9-10 13:0:0 Author: horizon3.ai(查看原文) 阅读量:11 收藏

Stephen Gates | September 10, 2025 | Blogs
A Pentest Wednesday® Story
Insurance companies don’t just protect homes, cars, and livelihoods. They safeguard enormous amounts of personal and financial data — making them prime targets for adversaries. The National Insurance Crime Bureau projects a 49% surge in identity theft-related insurance fraud in 2025, while synthetic identity fraud already costs the life insurance sector an estimated $30 billion annually, accounting for up to 85% of all cases.
For one large U.S.-based insurer, the wake-up call came not from regulators or an incident — but from their own development environment. When identities are the new perimeter and fraud is measured in billions, security leaders need proof that all environments can withstand a live attack.
That’s the idea behind Pentest Wednesday — a way of describing how organizations move from assumptions and paperwork to continuous validation and measurable risk reduction. For this insurer, it began with a single test of their development environment — and it reframed how they viewed identity security, developer environments, and third-party risk.
The Customer
This insurer is one of the largest in its region, with hundreds of offices and a vast field presence. Thousands of employees, agents, and claims professionals serve hundreds of thousands of policyholders and their families, providing multi-line coverage across auto, home, farm, commercial, and life insurance.
The company has been a NodeZero® customer since 2022, running monthly pentests to keep pace with change. But Dev remained off-limits, with developers assuring leadership that it was isolated and low-risk. For years, that argument held — until a single Dev pentest changed everything. What it revealed inside this insurer wasn’t just a local issue — it reflected the systemic risks facing large insurers everywhere.
The Problem
Large insurers operate at a scale where identity and data protection become existential challenges. With hundreds of offices, thousands of employees and agents, and services that span multiple lines of business, the attack surface is enormous.
Each line of business carries its own sensitive data:
Auto Insurance: driver’s licenses, vehicle registrations, accident reports, telematics data
Home Insurance: property records, mortgage details, appraisals, photos
Life Insurance: social security numbers, medical histories, beneficiaries
Farm Insurance: agricultural business data, land ownership, equipment valuations
Commercial Insurance: financial statements, business continuity plans, payroll info
Together, these datasets represent a comprehensive profile of policyholders’ lives and livelihoods — a goldmine for attackers.
Compliance frameworks may demand evidence of control effectiveness, but too often the proof comes in the form of paperwork. Audits can be passed, dashboards can show green, and questionnaires can be filed — yet none of it validates whether defenses will hold against a live attacker.
In this sector, the weakest link is almost always identity. Credentials can be stolen, weak, reused, or overprivileged. Third-party access expands exposure even further, as insurers often depend on vendors and contractors for claims, IT, and application development. It’s a systemic problem: adversaries don’t need to “hack in” when they can simply log in.
For insurers of this scale, the result is a dangerous gap between what leaders believe about their defenses and what is actually true in practice.
AHA Moment
Their development environment had never been tested with NodeZero before. For years, it was treated as low risk and kept outside security’s oversight. But when the first pentest finally ran, the results reflected systemic risks — and made them impossible to ignore:
- 266 cracked passwords, including 146 accounts sharing the same password
- Service accounts with “password does not expire” — some weak, contextual, and already found on breach lists
- Overprivileged and misconfigured accounts enabling unchecked privilege escalation
- An unpatched ActiveMQ service, exploited to install a remote access tool (RAT)
- Unexpected connectivity between Dev and Prod, including open VPN ports — clear evidence that remote developers and contractors had pathways into production
- Backup Exec accounts compromised, tying cracked credentials directly to recovery tools meant to ensure business continuity
Executive credentials were also cracked and proven valid, but the actual pivot into Prod came from a service account compromised via the RAT — an account with Domain Admin privileges in the production domain. With millions of policyholder records and sensitive PII at stake, the exposure was undeniable.
The findings stopped the NodeZero op-review in its tracks. The security team paused the call with Horizon3.ai’s Customer Success team to bring in Compliance. Together, they replayed the attack path step by step: from weak passwords to domain admin, from Dev to Prod, from assumptions to proof.
NodeZero validated all of these risks safely, proving that continuous testing doesn’t have to come at the expense of uptime or stability. Since 2022, the same approach has been applied in production without disruption.
It also sparked a cultural change: purple teaming. Instead of treating Dev as off-limits, cybersecurity and developers began working together — validating vulnerabilities, testing fixes, and building stronger controls before anything reached production. By shifting validation left, Dev became a proving ground for resilience.
“The dev environment is the developers’, and the cybersecurity team is not allowed to touch it.”
Security Leader
“We thought our IAM controls were solid. Seeing how easily NodeZero moved laterally was a reality check.”
Security Analyst
Dev wasn’t a sandbox. It was a staging ground for attackers.
How NodeZero Exposed the Path from Dev to Prod
Step 1: Cracked Credentials
- Over 3 days, 16 hours, NodeZero cracked 266 valid accounts
- 146 users shared identical passwords
- 2 backup accounts using shared creds exposed business continuity systems
Note: Attackers routinely run password-cracking campaigns in the background for weeks. Within days, NodeZero had harvested enough credentials to open the door.
Step 2: LSADump
- Non-expiring service accounts uncovered in 15 minutes, 30 seconds
- Some passwords unchanged since 2021
Step 3: ActiveMQ Exploit
- Unpatched service exploited in 10 hours, 16 minutes
- NodeZero dropped a remote access tool (RAT) by 10 hours, 33 minutes
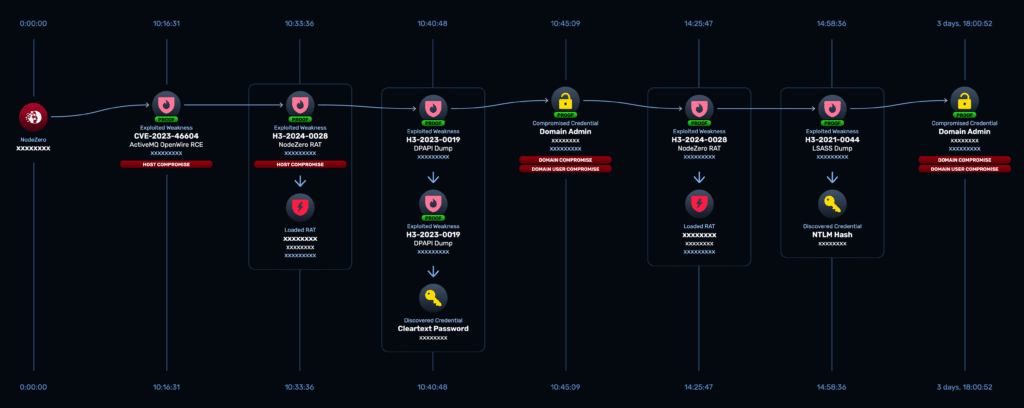
NodeZero Attack Path of ActiveMQ Exploitation -> Domain Compromise
Step 4: Privilege Escalation
- RAT used to compromise a service account with Domain Admin privileges
- Open VPN ports in Dev created additional remote access exposure
Step 5: Prod Exposure
- Domain Admin rights enabled lateral movement into production
- Executive credentials were also cracked and valid, underscoring how high the stakes were
Not visible in scanners: Weaknesses like SMB Signing Not Required enabled NTLM relay and MITM attacks that traditional vuln scanners would have missed.
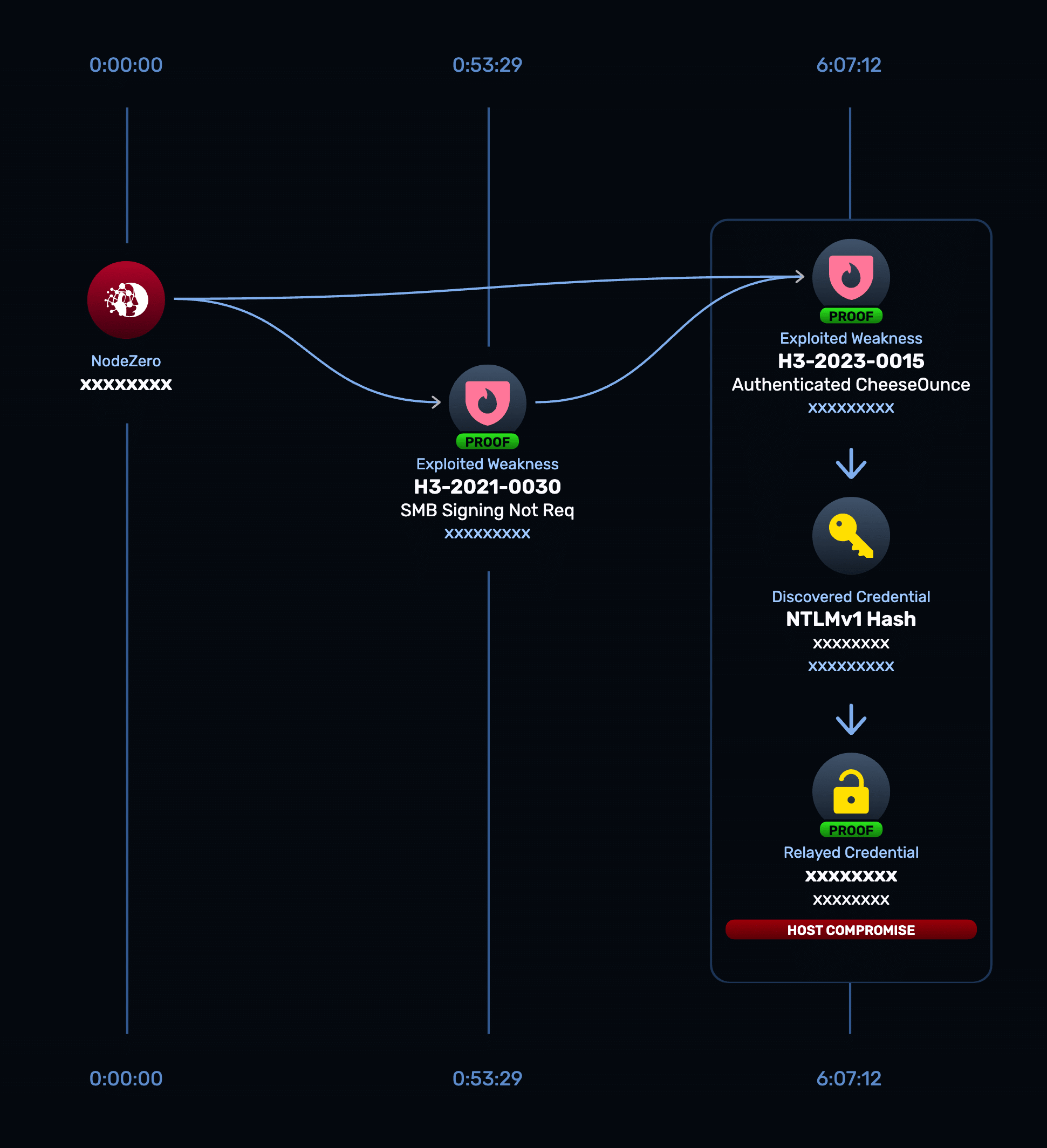
NodeZero Attack Path of SMB Signing Not Required -> Host Compromise
The insurer’s security strategy transformed from reactive monitoring to proactive validation. Key steps included:
- Password policies overhauled — weak and reused credentials eliminated
- Privileged accounts locked down — reducing lateral movement blast radius
- More than 100 NodeZero Tripwires™ deployed — canary tokens to detect unauthorized access attempts early
- Single Sign-On (SSO) rolled out — strengthening authentication and reducing the attack surface
- Vulnerability Management Hub adopted — consolidating findings into a single pane of glass
- EDR effectiveness testing expanded — proving coverage across Dev and Prod
- Insider threat simulations and AI-powered MCP integrations explored — automating reporting and improving executive visibility
- Backup and recovery gaps addressed — ensuring resilience beyond detection
- Precision operations replaced broad pentests — validating specific risks, fixes, and controls
Executives were shown evidence, not assumptions. NodeZero demonstrated how a service account compromised via a RAT escalated to Domain Admin in Prod — while also proving that executive credentials had been cracked and were valid, underscoring the risk at the highest levels of the organization.
Even during system change freezes — like major policy or platform rollouts — NodeZero kept validation running, ensuring resilience was never compromised.
“That shows executives good and bad. Look, this is how strong our defenses are. Currently, this is where we need to tighten it up. And that gives us latitude to get the other things in.”
Lead Cyber Security Infrastructure Compliance Analyst
Why Pentest Wednesday Matters
Insurance organizations face adversaries skilled at exploiting identity weaknesses, compromised credentials, and third-party gaps. Dev and staging aren’t exceptions; they’re opportunities.
This insurer’s journey shows why Pentest Wednesday matters: it turns identity defense from reactive assumptions into proactive, continuously validated protection. The result wasn’t just technical improvement — it was organizational confidence and a stronger security culture.
Why Identity Security Validation Changes the Game
For insurers, compliance and audits will always be part of the landscape. But as this story shows, they don’t prove whether identity controls, segmentation, or detection actually work.
Proof in Numbers
- 266 cracked passwords uncovered
- 146 accounts sharing the same password
- Pivot from Dev to Prod confirmed via service account compromised through RAT with Domain Admin privileges
- Executive credentials also cracked and proven valid
- 101 NodeZero Tripwires deployed for live detection
- VPN ports exposed in Dev — remote access into Prod path
- Backup Exec accounts compromised
- EDR effectiveness validated in Dev, closing blind spots
This is where Identity Security Validation comes in. NodeZero doesn’t just find weak passwords or misconfigured accounts — it executes real credential-based attacks to prove how adversaries could harvest identities, escalate privileges, and move laterally across hybrid environments.
- It reveals what logs and monitoring miss, such as credential reuse, dormant privileges, and access path drift.
- It validates under real-world pressure, safely emulating identity-based attacks in Active Directory and cloud identity systems.
- It operationalizes ITDR by making identity risk measurable — enabling scheduled tests, retests of fixes, and tracked exposure reduction over time.
For this insurer, the outcome was clear: by validating identity defenses through NodeZero, security leaders could finally prove which controls worked, which didn’t, and how quickly attackers could turn Dev into a doorway to Prod.
Ready to Prove It?
Insurance thrives on trust. Policyholders depend on their carriers not only to cover losses but also to safeguard their personal data. Identity is the new perimeter — and third-party vendors are the new frontier of exposure.
Whether you manage policyholder systems, claims applications, or third-party vendors, your Dev and Prod environments may be more connected than you think. Pentest Wednesday gives you the evidence to close those paths before attackers exploit them.
Each week, I’ll be sharing new stories from the field — real-world examples of how organizations are using Pentest Wednesday to turn assumptions into evidence, and uncertainty into confidence.
How can NodeZero help you?
Let our experts walk you through a demonstration of NodeZero®, so you can see how to put it to work for your organization.
如有侵权请联系:admin#unsafe.sh