
大规模网络扫描针对Cisco ASA设备展开,GreyNoise记录两次显著扫描高峰,涉及25,000个IP地址。第二次由巴西僵尸网络主导(80%),使用类似Chrome的用户代理。主要目标为美国、英国和德国。此类侦察活动通常预示新漏洞披露。管理员建议更新安全补丁、启用多因素认证并避免直接暴露关键端点以应对潜在威胁。 2025-9-8 21:45:17 Author: www.bleepingcomputer.com(查看原文) 阅读量:6 收藏

Large network scans have been targeting Cisco ASA devices, prompting warnings from cybersecurity researchers that it could indicate an upcoming flaw in the products.
GreyNoise has recorded two significant scanning spikes in late August, with up to 25,000 unique IP addresses probing ASA login portals and also Cisco IOS Telnet/SSH.
The second wave, logged on August 26, 2025, was largely (80%) driven by a Brazilian botnet, using roughly 17,000 IPs.
In both cases, the threat actors used overlapping Chrome-like user agents, suggesting a common origin.
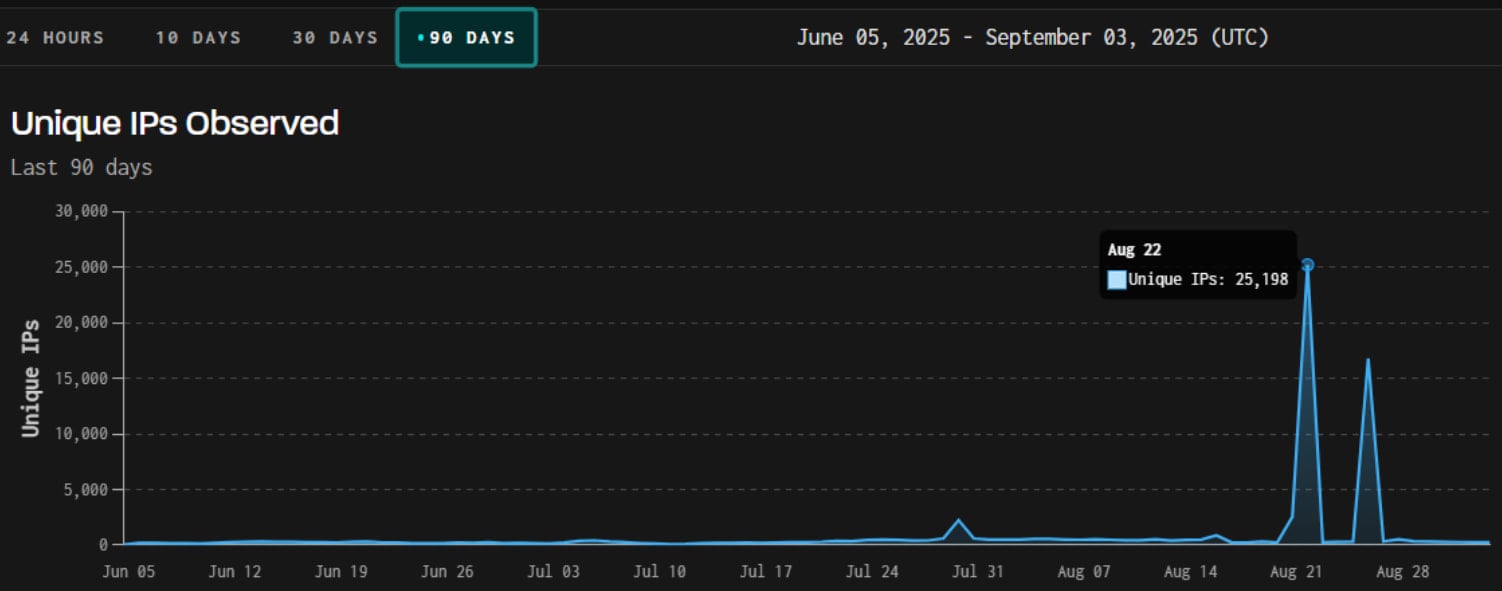
The scanning activity predominantly targeted the United States, while the UK and Germany were also targeted.
GreyNoise has previously explained that such reconnaissance activity precedes the disclosure of new vulnerabilities on the scanned products in 80% of cases.
Statistically, this correlation was weaker for Cisco, compared to other vendors, but information about such spikes can still be to helpful to defenders in enhancing their monitoring and proactive measures.
These scans are commonly failed exploitation attempts of already-patched bugs, but they can also be enumeration and mapping efforts in preparation for exploiting new flaws.
A separate report published earlier by system administrator 'NadSec – Rat5ak' reports overlapping activity that started on July 31 with low opportunistic scans that escalated in mid-August and culminated on August 28.
Rat5ak saw 200,000 hits on Cisco ASA endpoints within 20 hours, with a uniform 10k/IP traffic that appeared highly automated.
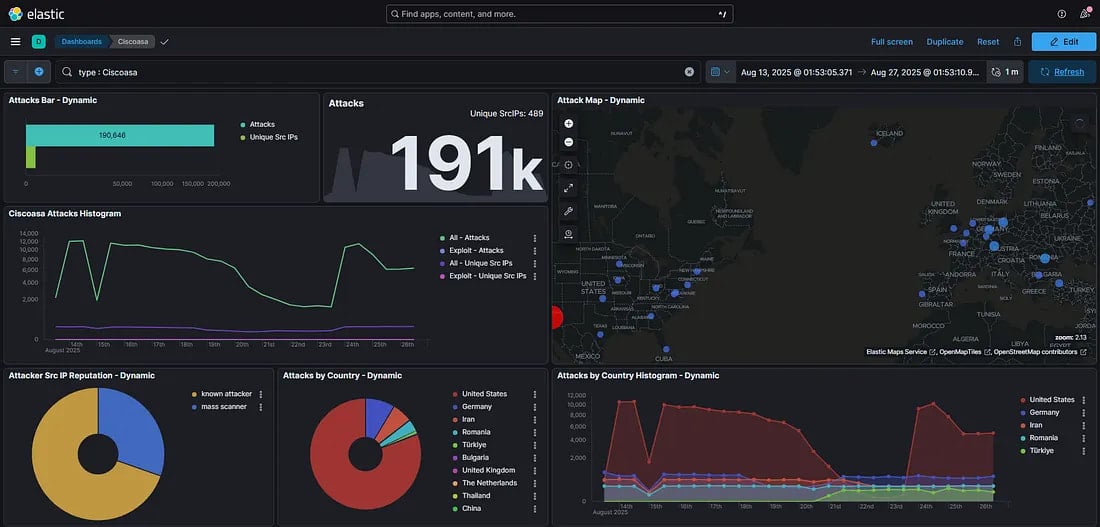
The administrator reports that the activity came from three ASNs, namely Nybula, Cheapy-Host, and Global Connectivity Solutions LLP.
System administrators are advised to apply the latest security updates on Cisco ASA to patch known vulnerabilities, enforce multi-factor authentication (MFA) for all remote ASA logins, and avoid exposing /+CSCOE+/logon.html, WebVPN, Telnet, or SSH directly.
If external access is required, a VPN concentrator, reverse proxy, or access gateway should be used to enforce additional access controls.
Finally, use the scanning activity indicators shared in GreyNoise and Rat5ak's reports to preemptively block these attempts, or use geo-blocking and rate limiting for regions far from your organization.
BleepingComputer has contacted Cisco for a comment on the observed activity, and we will update this post when we hear back from them.
如有侵权请联系:admin#unsafe.sh
