文章探讨了Azure中Global Administrator通过特定配置获取对所有订阅和管理组的控制权限的风险,并分析了攻击者如何利用此权限进行横向移动和资源滥用。微软已增加监控和日志功能以缓解此类风险。 2025-8-10 19:17:37 Author: adsecurity.org(查看原文) 阅读量:11 收藏
Aug 10 2025
In early 2020, I published an article on how a Global Administrator could gain control of Azure resources, that no one would know about it, and how this access would persist even after removing them from Global Administrator.
From that article:
“While Azure leverages Azure Active Directory for some things, Azure AD roles don’t directly affect Azure (or Azure RBAC) typically. This article details a known configuration (at least to those who have dug into Azure AD configuration options) where it’s possible for a Global Administrator (aka Company Administrator) in Azure Active Directory to gain control of Azure through a tenant option. This is “by design” as a “break-glass” (emergency) option that can be used to (re)gain Azure admin rights if such access is lost. In this post I explore the danger associated with this option how it is currently configured (as of May 2020). The key takeaway here is that if you don’t carefully protect and control Global Administrator role membership and associated accounts, you could lose positive control of systems hosted in all Azure subscriptions as well as Office 365 service data.”
Elevated Access
There is a switch that can be flipped from “No” to “Yes” that allows a Global Administrator to gain “manage access to all Azure subscriptions and management groups in this directory”. Flipping this switch to Yes adds the current user to the Azure role User Access Administrator at the root level. Once this access is provided, the current user can then add themself to other roles like Subscription Admin.
The graphic below shows this flow.

This leads to some interesting attack scenarios. The one I covered in the article involved jumping to Azure and compromising an Azure hosted Domain Controller. The graphic below shows the conceptual attack scenario laid out in the article.

Attack Scenario Key Takeaways
- An attacker that can gain admin rights to one environment can often pivot to another.
- Hosting Domain Controllers on virtual infrastructure such as cloud requires trust in that platform as well as additional protections around compromised accounts & monitoring.
- Jumping from Entra ID to Azure to on-prem Active Directory is possible given how many enterprises are configured and if the Global Admins group isn’t well protected or standard user accounts have the ability to elevate.
- The attacker could also use resources in your subscriptions for their purposes such as spinning up new virtual instances for attacker systems or bitcoin mining.
- Control of subscription access enables the attacker to launch ransomware against virtual instances.
Updates to Elevated Access
Since I submitted the information to Microsoft and wrote the article describing the issue, there have been changes to how this works.
https://learn.microsoft.com/en-us/azure/role-based-access-control/elevate-access-global-admin
There is now a bar below the Access management for Azure resources area that states how many users have elevated access. This provides clear messaging around how elevate access is used in the environment

Clicking on this link takes us to a new page that shows users with elevated access. On this page we have the ability to select and remove the accounts that have this right.

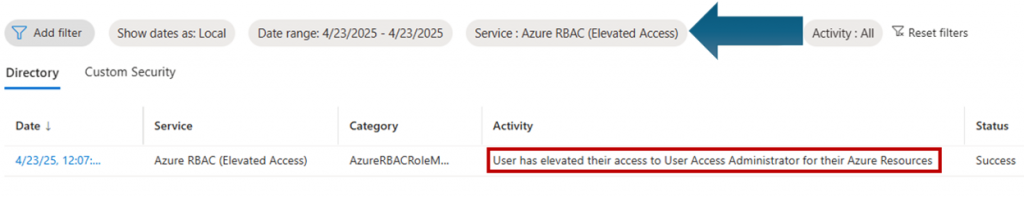
There are also now logs associated with this right called Elevated Access Audit Logs (preview). The first event I show here is when a user flips the bit and receives elevated access.


When we remove a user from having elevated access, we can now see that in a log as well.


Attack Scenario Key Mitigation
- Severely restrict membership in Global Admins.
- Use PIM (eligible) for Global Admins & require MFA.
- Once Elevated Access is applied to an account, removing role membership has no impact. Elevated Access must be removed separately.
- Monitor the Entra ID Audit Log for Azure RBAC (Elevated Access) activity.
- Closely monitor membership of the “User Access Administrator” Azure role (root level).
- Remove any account with Elevated Access that doesn’t require it.
- Place Domain Controllers and other sensitive systems in another Azure tenant.
Conclusion
Elevated Access is one of those nearly hidden options that provides the ability for a Global Admin to gain highly privileged rights in Azure. This level of access should be audited regularly and the logs ingested in the SIEM.
(Visited 7 times, 7 visits today)
如有侵权请联系:admin#unsafe.sh