文章探讨了美英欧在红队测试方法上的差异,包括监管框架和威胁建模的不同。还分析了红队与渗透测试的区别,并介绍了红队工具链的关键类别及安全实践。 2025-6-2 17:23:37 Author: www.trustwave.com(查看原文) 阅读量:9 收藏
6 Minute Read
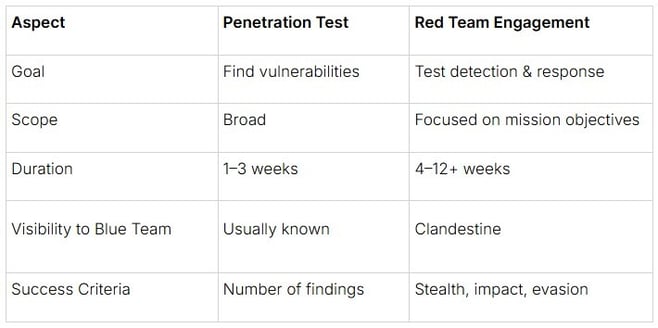
The differences between the US, the UK, and Europe are often minor but important regionally. Sometimes, we use different words to describe the same thing: French fries (US) vs. chips (UK) vs. pommes frites (France) are all fried potatoes. Sometimes, the same word can have different meanings, such as "football" and "football". Oddly, the same point holds true for Red Team testing. Due to local compliance issues and the type of attack the client wishes to conduct, a Red Team event held on the western side of the Atlantic will differ greatly from one held on the eastern side. Drawing from extensive experience in global Red Team operations, I'll present a brief analysis of how organizations approach security testing across major regions. This comparative study focuses specifically on the methodological differences between the UK, continental Europe, and the US in terms of engagement scoping, execution parameters, and operational constraints. While practices can vary significantly between organizations and sectors, this analysis reflects patterns observed across our current client portfolio, representing a substantial cross-section of enterprise-scale security programs. This overview is based on working with large businesses across these regions, but the observations are limited to Trustwave's engagements and client base; therefore, another organization might experience it differently. It's ever-changing, so Red Team testing in the future might be completely different. The UK and European landscape is characterized by robust regulatory frameworks. Red Team testing follows an organized and structured approach—a carefully planned inspection with detailed checklists. Special programs or regulatory frameworks are followed. For example, in the financial sector, we have CBEST, driven by the Bank of England and government departments, GBEST (which is based on CBEST), but managed by the UK Cabinet Office. In the UK and EU, during testing, security teams play the role of skilled attackers, albeit in a controlled manner. They try to break into systems while watching to see if the company's security team can catch them. What makes this interesting is that regulators keep track of the results - which means companies don't just get a report; they're required by regulators to fix any weaknesses that are found. These engagements excel at simulating sophisticated threats, particularly those of APT29 (Cozy Bear) and similar actors, with an equal emphasis on detection capabilities and incident response. In contrast, the US market showcases greater diversity and flexibility. While less constrained by regulatory frameworks, engagements are shaped by industry-specific needs across sectors like finance, healthcare, and energy. This results in highly customized, objective-focused exercises that adapt to each organization's unique security landscape. The most significant difference lies in the legal and ethical frameworks involved. In the UK and EU, GDPR and data protection laws establish clear boundaries. Red Teams must obtain consent, maintain data sovereignty, and work under detailed legal contracts. The US offers greater flexibility in engagement execution, particularly in the private sector. However, this flexibility can lead to ambiguous boundaries, especially when engagements lack proper scope definition or stakeholder approval. This is important because if the boundaries are not clearly defined, then things that are out of scope could be "tested"/attacked, too. Things that you do not necessarily have permission to test. 2.2. Threat Modeling Differences The regional threat modeling philosophies showcase distinct methodological differences. European Red Teams tend to execute highly specific APT emulations. These engagements precisely mirror the tactics and techniques of known threat actors like APT28 (an attempt to interfere in the US Presidential Election in 2016), providing targeted insights into an organization's resilience against state-sponsored attacks. US-based engagements, however, favor a more flexible approach. Rather than tying operations to specific geopolitical actors, teams have greater latitude to craft adversary profiles that align with the organization's unique threat landscape and business context. One of the key distinctions in cybersecurity assessments lies in understanding the difference between pen testing and Red Team engagements. Before I get to that, let me clarify. When I say Penetration Test, I don't mean a vulnerability scan. Some companies try to blend vulnerability scans and penetration tests into a single process, but I believe they are not the same. Vulnerability scans are an automated tool (such as Nessus) that scans the network for systems running vulnerable services. This tool will scan a system, find open ports, and grab the banners of the service listening on those ports. Then, compare the captured banners with its internal database of predefined vulnerabilities. The team then generates a report that contains the detected vulnerabilities and their corresponding severity levels. The biggest problem with vulnerability scans is that a number of false positives may be detected, and the severity assigned to the vulnerability does not take into account the specific context of the client environment. A vulnerability scan, however, is an important "must-have" initial step that should not be skipped for any organization serious about its security posture. Pen testing focuses on identifying vulnerabilities across systems and infrastructure. Teams systematically examine web applications, network configurations, and internal assets to uncover security gaps - providing comprehensive coverage but with limited depth in any single area. Red Team engagements, by contrast, simulate real-world attacks through mission-driven operations. Rather than conducting broad vulnerability scans, Red Teams pursue specific objectives, such as data exfiltration or establishing persistent access while remaining undetected. This targeted approach allows for deep exploration of critical attack paths. Here's a quick table to illustrate my point: 3.1. When to Use What Let's explore when to choose between penetration testing and Red Team engagements for optimal security assessment outcomes. Penetration testing serves as an essential foundation for organizations to improve their security maturity. It excels at systematically identifying vulnerabilities, ensuring compliance requirements are met, and validating the effectiveness of patch management programs. Red Team engagements, on the other hand, require a more advanced security posture. Organizations should consider this approach only after establishing robust Blue Team capabilities and comprehensive security monitoring. Without these prerequisites, the engagement may simply confirm known vulnerabilities rather than provide meaningful insights into detection and response capabilities. Consider this strategic guideline: Choose penetration testing to evaluate your technical security controls and Red Team engagements to assess your security operations and incident response (DFIR) capabilities. Let's explore the essential components of our toolchain, focusing on how each category serves a specific purpose in our operations. Just a quick lesson. Toolchain is a set of software development tools used to build and develop software. A comprehensive Red Team toolchain consists of five strategic categories, each carefully selected to maintain operational security: Understanding the nuances and operational implications of each category is crucial for maintaining operational security and achieving engagement objectives. 4.1. Popular Red Team Tools Let's examine the key tools that professional Red Teams rely on while noting important security considerations: A quick critical security advisory: Exercise extreme caution with tool sources. Unauthorized or cracked versions frequently contain malicious code, potentially compromising the operator and client environments. 4.2. Risks in the Toolchain It is very important to maintain a secure toolchain is critical for Red Team operations, and teams must exercise rigorous control over their tools and infrastructure. Only obtain commercial tools through legitimate channels because malicious actors frequently embed backdoors, remote access trojans, and credential harvesters into cracked versions of tools like Cobalt Strike, putting both operators and client environments at risk. Similarly, open-source tools require careful validation. Teams must verify repository authenticity and conduct thorough code reviews of any updates or pull requests. This is particularly important, given that adversaries are increasingly targeting Red Team infrastructure and tooling. 4.3. Operational Hygiene Tips: Maintaining Toolchain Security To ensure robust operational security, implement these essential practices: These practices distinguish professional Red Team operators from potential security risks. They form the foundation of a trustworthy and secure operational framework. 4.4. Red Team CI/CD? Red Team operations require modern development practices. By treating our toolkit as a professional software project, we ensure reliability and trust. Our CI/CD pipeline incorporates: This disciplined approach delivers what matters most: tools we can trust completely during critical operations.
UK and Europe
2.1. Legal & Ethical Boundaries
3. Pen Test vs Red Team

Table 14. Toolchain Categories
如有侵权请联系:admin#unsafe.sh