ArcGIS Hidden Functionality Allows Insecure OAuth 2.0 Based Authentication - CVE-2025-0020 VSL-2025-21
ArcGIS存在OAuth 2.0认证漏洞(CVE-2025-0020),CVSS评分7.9。其隐藏功能允许攻击者请求未记录的自定义令牌过期时间,导致权限滥用和配置/环境操纵风险。 2025-5-17 02:37:11 Author: seclists.org(查看原文) 阅读量:41 收藏
ArcGIS存在OAuth 2.0认证漏洞(CVE-2025-0020),CVSS评分7.9。其隐藏功能允许攻击者请求未记录的自定义令牌过期时间,导致权限滥用和配置/环境操纵风险。 2025-5-17 02:37:11 Author: seclists.org(查看原文) 阅读量:41 收藏

Full Disclosure mailing list archives
From: CVE - VULSec Labs via Fulldisclosure <fulldisclosure () seclists org>
Date: Wed, 14 May 2025 08:32:41 +0000
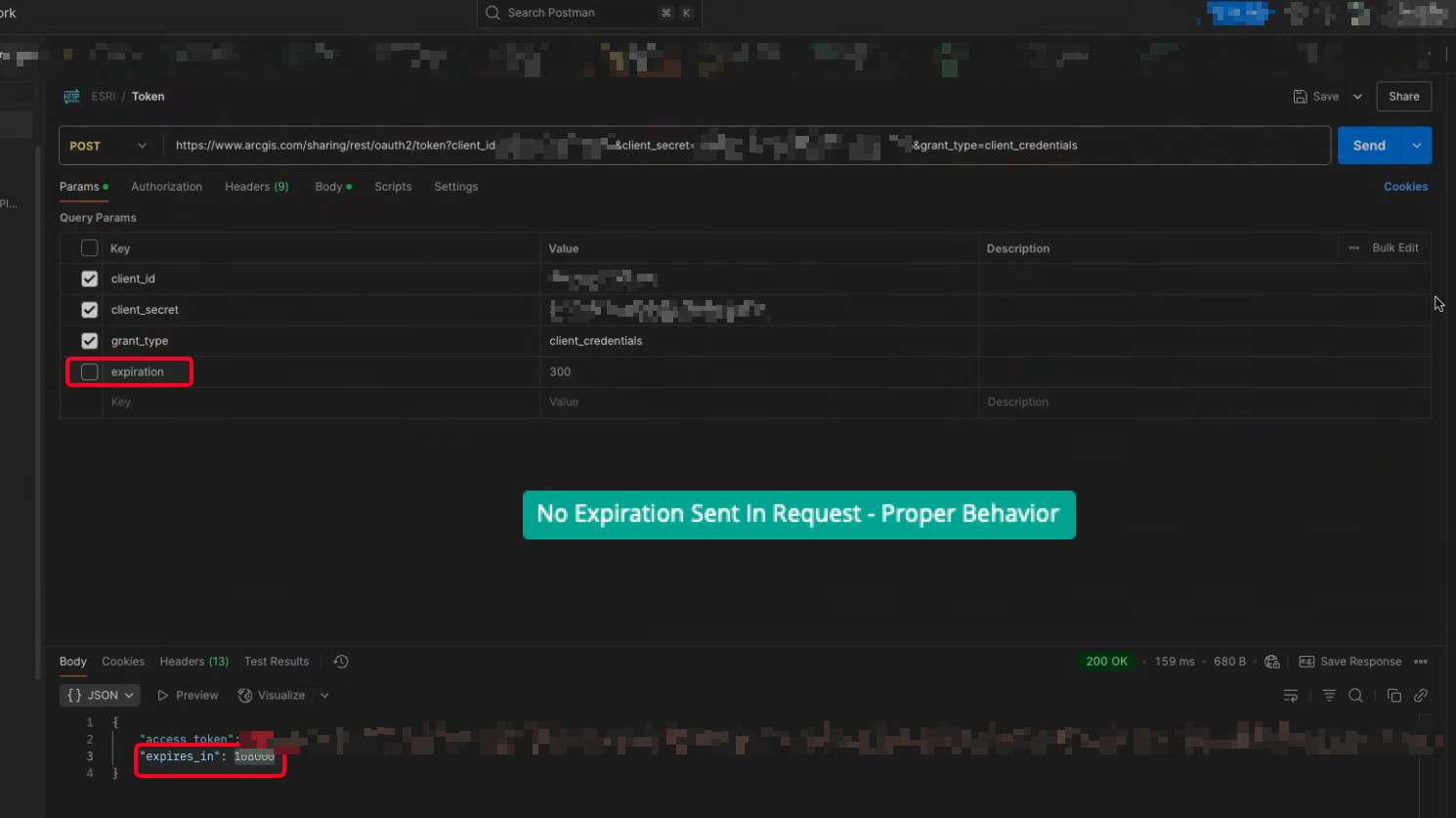
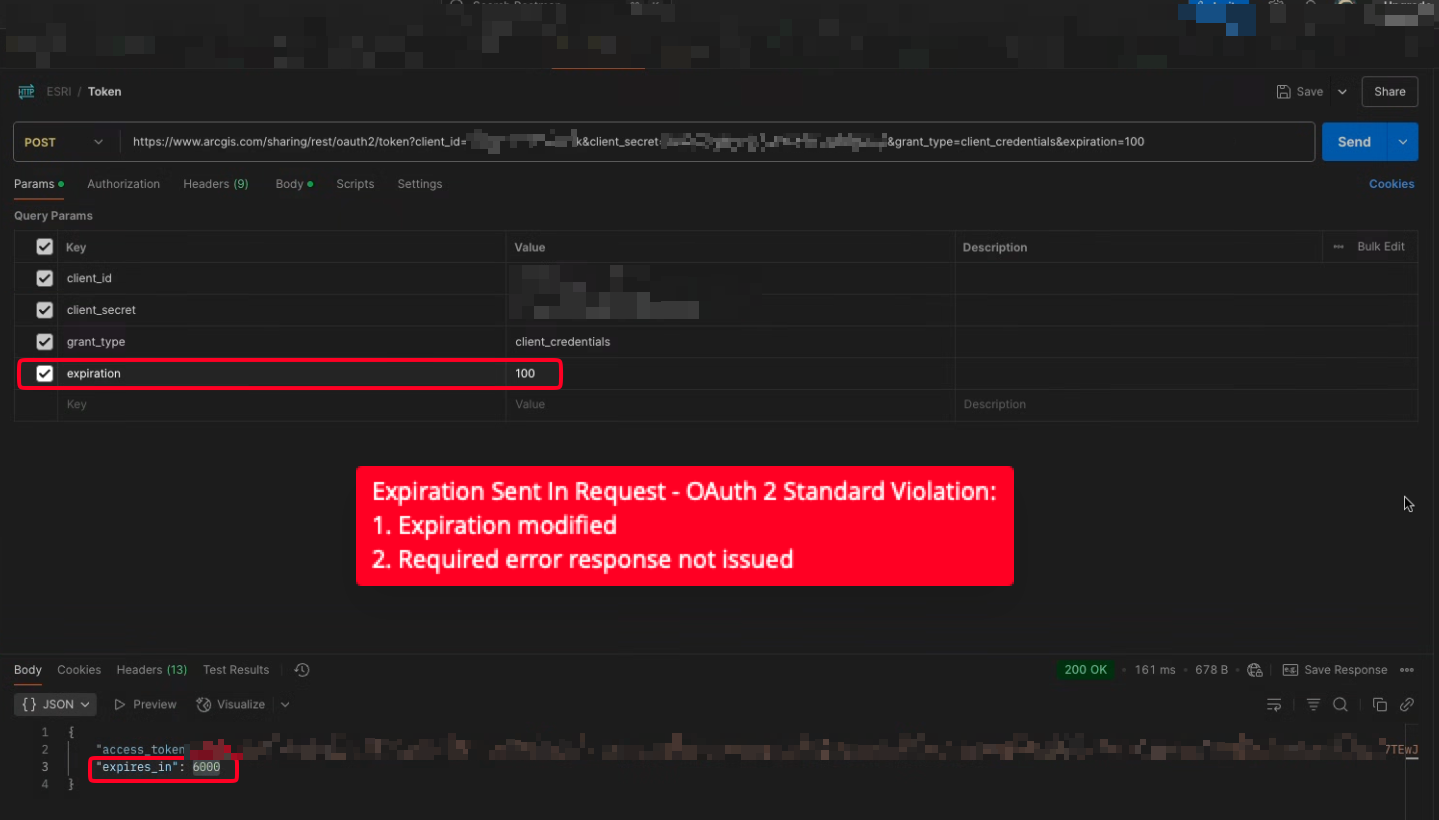
=== SUMMARY === Vendor: ArcGIS Product: ArcGIS Subject: ArcGIS Hidden Functionality Allows Insecure OAuth 2.0 Based Authentication - CVE-2025-0020 VSL-2025-21 CVSS: 7.9 (high) CVSS:4.0/AV:N/AC:L/AT:N/PR:N/UI:N/VC:N/VI:N/VA:N/SC:H/SI:H/SA:H/U:Amber Credit: Erez Kalman Author: VULSec Labs Date: 2025-05-14 === DETAILS === CWE/CAPEC: Violation of Secure Design Principles, Hidden Functionality, Incorrect Provision of Specified Functionality vulnerability in ArcGIS (Authentication) allows Privilege Abuse, Manipulating Hidden Fields, Configuration/Environment Manipulation. The ArcGIS client_credentials OAuth 2.0 API implementation does not adhere to the RFC/standards; This hidden (known and by-design, but undocumented) functionality enables a requestor (referred to as client in RFC 6749) to request an, undocumented, custom token expiration from ArcGIS (referred to as authorization server in RFC 6749). === LINKS === https://www.vulsec.org/advisories PoC (/attached) https://www.cve.org/cverecord?id=CVE-2025-0020 https://www.rfc-editor.org/rfc/rfc6749 https://developers.arcgis.com/documentation/security-and-authentication/
Attachment:
publickey - [email protected] - 0x04D8BEEC.asc
Description:
Attachment:
signature.asc
Description: OpenPGP digital signature
_______________________________________________ Sent through the Full Disclosure mailing list https://nmap.org/mailman/listinfo/fulldisclosure Web Archives & RSS: https://seclists.org/fulldisclosure/
Current thread:
- ArcGIS Hidden Functionality Allows Insecure OAuth 2.0 Based Authentication - CVE-2025-0020 VSL-2025-21 CVE - VULSec Labs via Fulldisclosure (May 16)
文章来源: https://seclists.org/fulldisclosure/2025/May/2
如有侵权请联系:admin#unsafe.sh
如有侵权请联系:admin#unsafe.sh