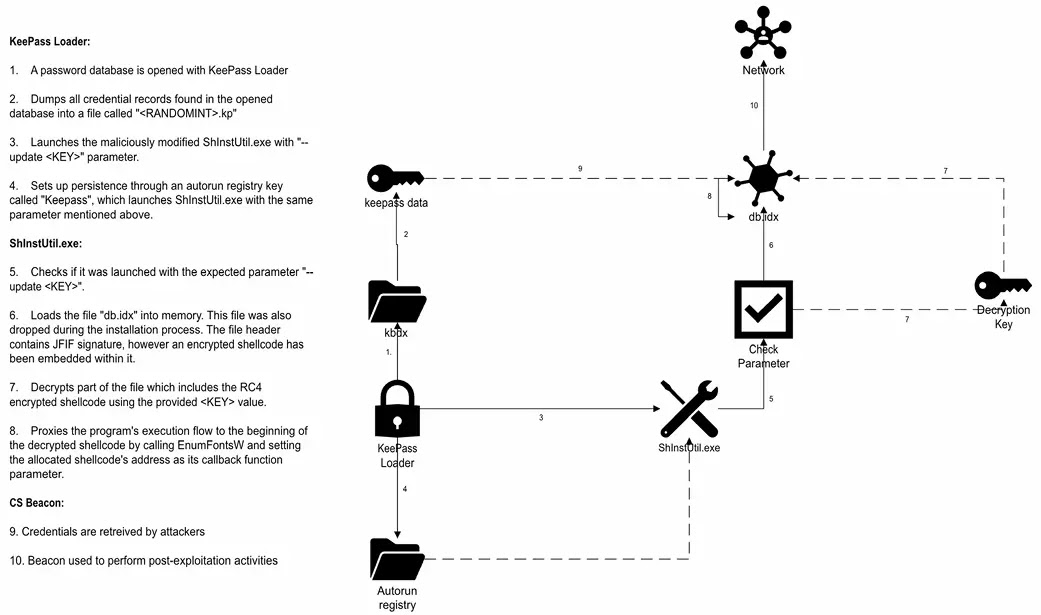
sophisticated cyberattack targets KeePass password manager via tampered download links and malicious software, stealing sensitive credentials and compromising user trust in security tools. 2025-5-13 14:0:41 Author: cybersecuritynews.com(查看原文) 阅读量:16 收藏
In a concerning development for cybersecurity professionals and everyday users alike, sophisticated threat actors have begun targeting KeePass, one of the most popular open-source password managers, to distribute malware and exfiltrate sensitive credentials.
The campaign, which appears to have begun in early April 2025, involves compromised download links and trojanized versions of the legitimate KeePass application that appear identical to the authentic software on the surface, while harboring dangerous capabilities beneath.
Security experts have identified multiple attack vectors, with the primary distribution channel being tampered download links spread through phishing emails and malicious advertisements that redirect users to convincing but fraudulent KeePass download pages.
Once downloaded, the trojanized application maintains full password management functionality while simultaneously executing malicious code in the background, making detection particularly challenging for unsuspecting users who observe no performance degradation or unusual behavior from the application.
Withsecure researchers identified the campaign after investigating reports of unexplained credential theft from users who insisted their password hygiene was robust.
“This is a particularly sophisticated supply chain attack,” noted Mika Aalto, Principal Threat Researcher at Withsecure.
“The attackers have gone to extraordinary lengths to ensure the malicious version behaves identically to legitimate KeePass software, with the malware component only activating after several days of normal operation to avoid immediate detection.”
Initial analysis suggests thousands of users worldwide may have already been compromised, with the financial services, healthcare, and government sectors appearing to be primary targets.
The malware’s credential harvesting capabilities extend beyond the KeePass database itself, with evidence showing it can extract browser-saved passwords, authentication cookies, and cryptocurrency wallet credentials from infected systems.
The threat represents a concerning evolution in supply chain attacks targeting security tools themselves.
By compromising password managers-software explicitly designed to enhance security-attackers exploit the inherent trust users place in these applications and gain access to the complete digital identity of victims, including their most sensitive accounts and information.
Infection Mechanism and Code Analysis
The infection process begins with a seemingly normal installation routine, but during execution, the malicious version creates an additional dynamic-link library (DLL) with a filename designed to mimic legitimate KeePass components.
.webp)
This DLL implements a technique known as “DLL search order hijacking” to ensure it loads whenever the legitimate application starts.
The following code extract from the malware shows how it hooks into the KeePass password processing functions:-
// Malicious hook implementation
public static byte[] ProcessEncryptedData(byte[] encryptedData, byte[] key)
{
// Execute original KeePass decryption function
byte[] decryptedData = OriginalProcessEncryptedData(encryptedData, key);
// Stealthily exfiltrate the decrypted data
if (IsConnectedToInternet() && !IsRunningInSandbox())
{
ExfiltrateData(decryptedData, "pwd_dump");
}
return decryptedData;
}This code effectively creates a man-in-the-middle within the application itself, intercepting decrypted passwords before they’re displayed to the user.
The malware then employs a sophisticated exfiltration routine that fragments and encrypts stolen data before transmitting it through DNS queries-a technique chosen specifically because DNS traffic is often less scrutinized by security solutions than HTTP or SMTP protocols.
When users unlock their KeePass database, the malware captures both the master password and all stored credentials.
It then establishes persistence through a fileless technique that stores malicious code in the Windows Registry and uses scheduled tasks with obscure names to maintain access even if the original infection is detected and removed.
How SOC Teams Save Time and Effort with ANY.RUN - Live webinar for SOC teams and managers
如有侵权请联系:admin#unsafe.sh

.png
)