GitGuardian在2025年第一季度推出了多项新功能和改进,包括非人类身份治理、支持多种秘密管理器集成、增强的秘密分析工具、容器registry中的秘密检测以及对Jira、Confluence Cloud等平台的历史秘密扫描功能。这些更新旨在提升企业对敏感信息的控制能力,并通过自动化和智能化手段加强整体安全防护。 2025-5-5 15:22:55 Author: securityboulevard.com(查看原文) 阅读量:12 收藏
Q1 2025 was all about turning chaos into control.
At GitGuardian, we expanded our secrets detection arsenal, launched full-scale governance for machine identities, and made it easier than ever to integrate, analyze, and act on secrets across your environment.
Here’s what’s new and why it matters.
New Non-Human Identity governance has arrived
NHI Governance
Machine identities now outnumber humans by 100:1. Every API key, automation credential, and service account is a potential entry point for attackers.
Our new NHI Governance product helps you:
- Build a centralized, up-to-date secrets inventory.
- Map secrets to their consumers and resources that use them.
- Enforce access policies based on the OWASP NHI Top 10.
- Spot overprivileged or orphaned identities fast.
This isn’t just visibility. It's your command center for cleaning up the NHI sprawl, reducing risk, and enforcing least privilege across your stack.
Get a personalized walkthrough
Secrets managers integrations via ggscout
GitGuardian Scout (ggscout) now supports integrations with all major secrets managers:
- AWS Secrets Manager
- HashiCorp Vault
- Azure Key Vault
- Google Secret Manager
- Delinea
- Akeyless
This powerful integration lets you:
- Instantly see which leaked secrets are already properly vaulted, giving you a single source of truth across all vaults, no matter how many you use.
- Identify unvaulted, duplicate, or stale secrets across your infrastructure, helping to control secrets sprawl and prevent the proliferation of orphaned or unused credentials.
- Simplify vault migrations and clean-up operations, making managing secrets across different systems easier.
- Kickstart remediation by writing missing secrets to the vault (optional, auditable, and controlled), enabling proactive threat detection and improved incident response.
No plaintext secrets ever leave your environment. ggscout hashes values with HMSL before any data is sent, ensuring confidentiality.
More context = smarter prioritization
Secrets Analyzers
Finding a secret is only half the battle. Understanding its impact is where the real work starts. Our new Secrets Analyzer automatically gathers critical metadata for detected secrets, including:
- Scopes and permissions associated with the credential, revealing the level of access it grants and the potential for privilege escalation. This is crucial because many secrets are overly permissive, allowing attackers to cause widespread damage by performing unauthorized actions.
- Perimeter data to assess the potential blast radius, helping to understand the systems and resources that could be affected if the secret is compromised. Even with limited permissions, a compromised secret in a central system can provide a foothold to reach numerous other critical assets.
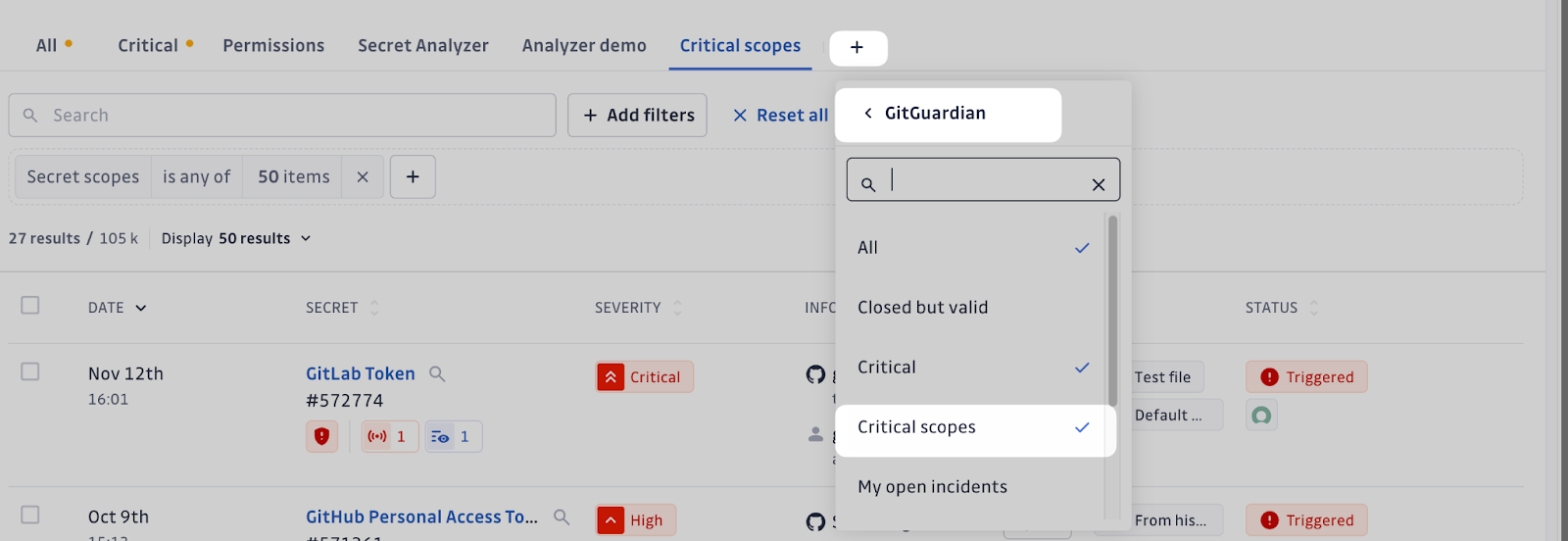
The Critical Scopes view makes it easy to surface secrets with the most sensitive permissions (e.g., GitHub PATs with repo write access, Slack tokens with admin privileges). This allows security teams to focus on the highest-priority risks, addressing the most dangerous exposures first.
Analysis is continuous. Incidents are automatically re-checked based on status, age, and validity. This ensures that security teams stay ahead of evolving threats and don't miss critical changes in a secret's permissions.
This intelligence helps security teams:
- Evaluate the impact more accurately, moving beyond simply detecting secrets to understanding the real-world consequences of their exposure.
- Prioritize remediation based on actual risk, focusing efforts on secrets that pose the greatest danger to the organization.
- Streamline response workflows, enabling faster and more effective containment and mitigation of security incidents.
You can’t keep treating all secrets equally. Some carry wide permissions while others are barely a threat. Now you can focus your energy where it matters most.
Explore the Secret Analyzers documentation
Generic Secret Enricher V1
Generic secrets like usernames and passwords are notoriously tricky. That’s why we rolled out the Generic Secret Enricher, a machine learning model that helps:
- Classify secrets based on document context, addressing the challenge that the validity of a generic secret depends entirely on its surrounding context within the code.
- Associate secrets with providers like PostgreSQL or AWS, giving security teams crucial information to assess the risk and prioritize remediation.
- Add powerful filters for Provider, Category, and Family, enabling security teams to focus on genuine threats rather than being overwhelmed by false alarms, a key benefit given that the broad nature of generic secrets makes them prone to false positives.
Spend less time investigating these secrets and more time fixing the ones that matter.
New integrations to scan wherever secrets live
Secrets detection in container registries
We uncovered over 100,000 valid secrets leaked on public Docker infrastructure, including DockerHub.
This massive exposure highlights a concerning pattern where developers underestimate the risk of embedding secrets in their images.
Our analysis of 15 million public Docker images in late 2024 revealed that:
- 97% of valid secrets are hidden in image layers
- 60% of leaks occurred in build configuration files
- 65% of leaks originated from ENV instructions
- Most leaked tokens were tied to production environments
- Alarmingly, over 7,000 valid AWS keys remained active
This exposure isn't limited to individual developers. The majority of exposures were found in corporate contexts, affecting critical sectors including pharmaceutical, energy, defense, and major tech companies.
Secrets in container images pose a critical threat, especially due to their proximity to CI/CD and runtime environments, often containing credentials for high-privilege operations.
This isn't just poor hygiene. It's a systemic risk.
You can now detect hardcoded secrets inside registries like:
- Docker Hub
- JFrog Artifactory
- Amazon ECR
- Azure Container Registry
- Google Artifact Registry
Containers have credentials sneaking in through:
- Hardcoded API keys in application code
- Dockerfile ENV/RUN commands leaking credentials
- Build-time secrets that persist in image layers
By scanning your container images before deployment, we help you catch these credentials before they reach production. Shift-left security just took another leap forward!
Check out our Blog Post for more details!
Historical secrets scanning for Jira & Confluence Cloud
Secrets don't die of old age, and they're just as dangerous when forgotten. That's why we're thrilled to announce historical scanning for Jira and Confluence Cloud!
Previously, our integration would only catch secrets in real-time as they appeared. Now, we're digging through the archives to find those lurking threats from the past. This means you can:
- Unearth and remediate forgotten secrets that still pose active risks.
- Build a truly comprehensive security posture with no historical blind spots.
- Finally, clean up those secrets in your collaboration tools.
After all, a secret leaked six months ago isn't any less compromised than one leaked yesterday.
Check out our public documentation to enable the feature:
Read how to enable secrets detection for Jira Cloud
Read how to enable secrets detection for Confluence Cloud
Secrets detection in ServiceNow
Track secrets and honeytoken detections within ServiceNow. Automate workflows and simplify escalation. Available under the Business plan with a 30-day trial.
Introducing GitGuardian Secrets Detection Integration For ServiceNow
Secrets detection in Bitbucket Cloud
You asked, we delivered. GitGuardian now supports real-time detection and full visibility for Bitbucket Cloud repositories.
Integrate Bitbucket Cloud With GitGuardian's Secrets Detection Platform Now Supports
Custom tags
Take control of incident management with custom tags that let you categorize, filter, and search incidents your way. Whether you're organizing by team, project, severity, or custom workflow stage, tags provide the flexibility you need to make GitGuardian work for your organization.
Developers can even interact with tags programmatically via our API, opening up endless automation possibilities.
Check out our detailed guide on how to use custom tags
Enhanced email incident alerts
Notification fatigue is real. That's why we've added granular controls for email alerts, letting you:
- Customize notification settings through the API
- By default, notify users when a new incident is detected
- Managers can set account-level defaults for a consistent experience
- Ensure the right people get the right alerts at the right time
Learn how to customize email alert settings
Secret Value Search
Ever wonder if a particular secret has been leaked across your repositories? Now you can search directly by secret value across your entire monitored perimeter.
Streamlined communication and incident tracking
Microsoft Teams Alerts
Get real-time alerts delivered straight to your Teams workspace—complete with action links for instant triage.
Jira Data Center Integration
Auto-create issues, sync custom fields, and auto-resolve incidents linked to Jira tickets.
Wrapping Up
Secrets are messy. NHIs are multiplying. And security teams are stretched thin.
This quarter, we focused on helping you see more, know more, and act faster — with better detection, smarter context, and powerful automation.
Want to see these features in action? Reach out to your GitGuardian contact or book a demo.
Expect even more ways to:
- Expand visibility to more sources
- Automate remediation workflows
- Enforce secrets governance at scale
Because when it comes to securing credentials, good enough just isn’t safe enough.
Until next time, keep your secrets safe.
*** This is a Security Bloggers Network syndicated blog from GitGuardian Blog - Take Control of Your Secrets Security authored by Soujanya Ain. Read the original post at: https://blog.gitguardian.com/q1-2025-recap-gitguardian-doubles-down-on-secrets-security-and-machine-identity-control/
如有侵权请联系:admin#unsafe.sh

