SonicWall 的零日漏洞被报告后,在 2023 年 4 月出现针对其 API 路径的探测活动,涉及特定 IP 地址和 URL 路径。 2025-4-30 01:29:43 Author: isc.sans.edu(查看原文) 阅读量:19 收藏
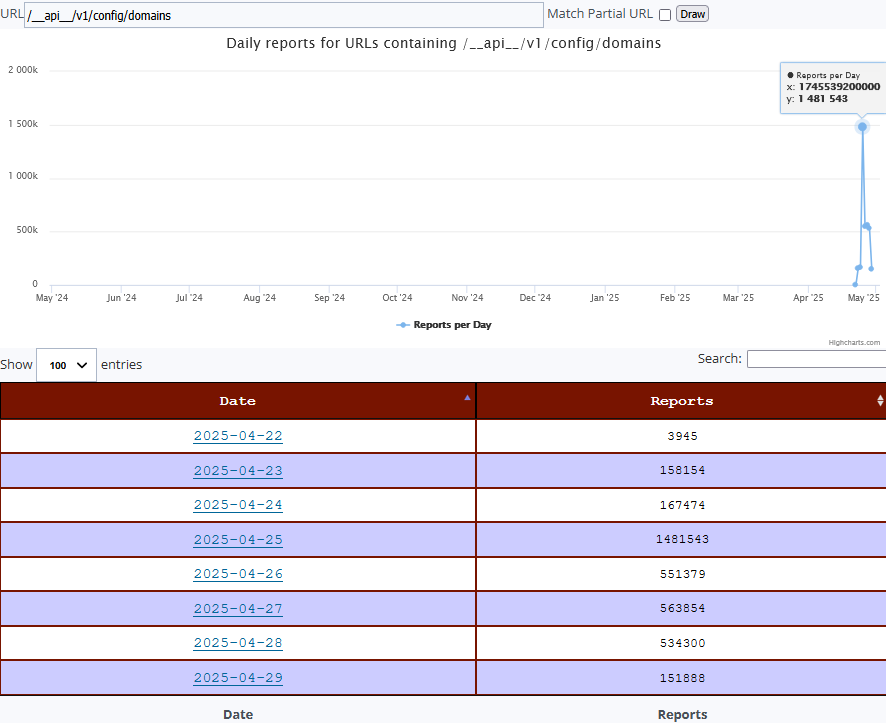
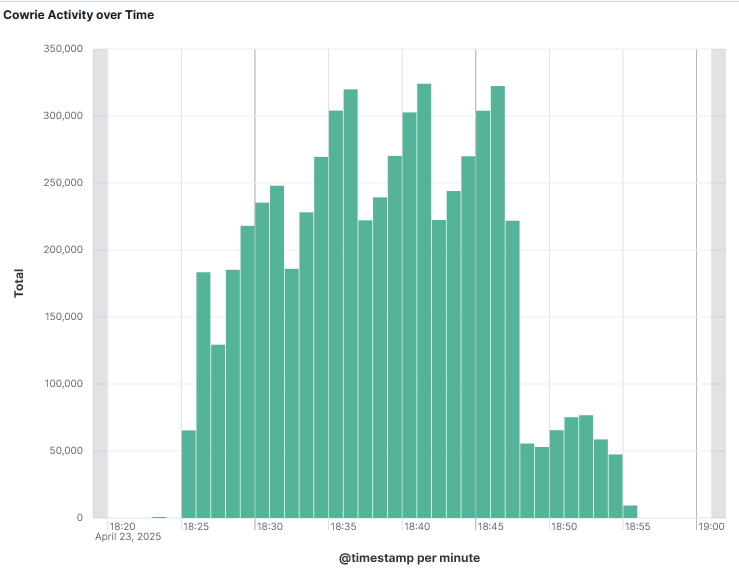
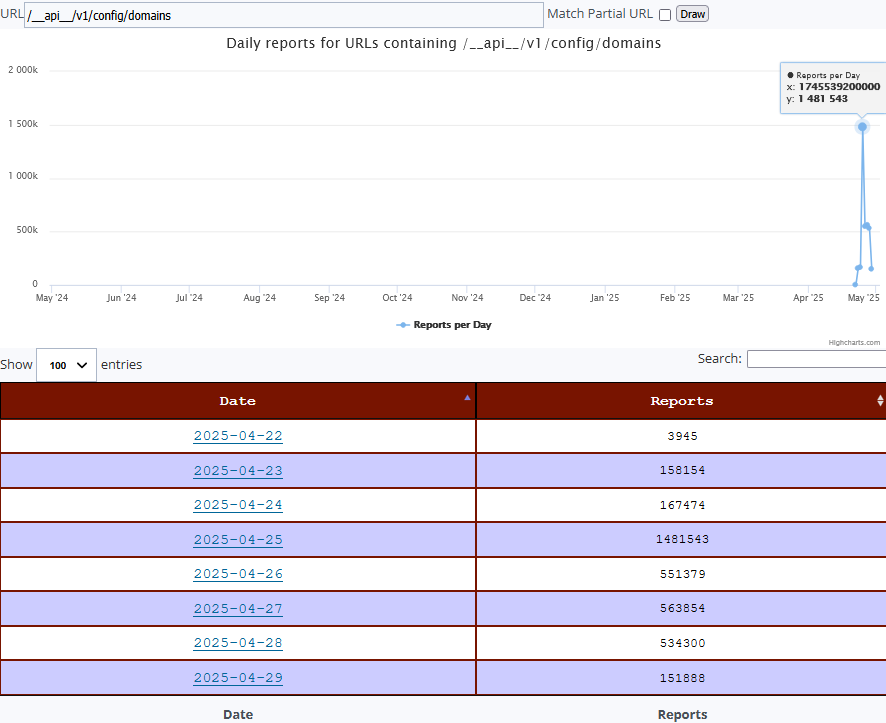
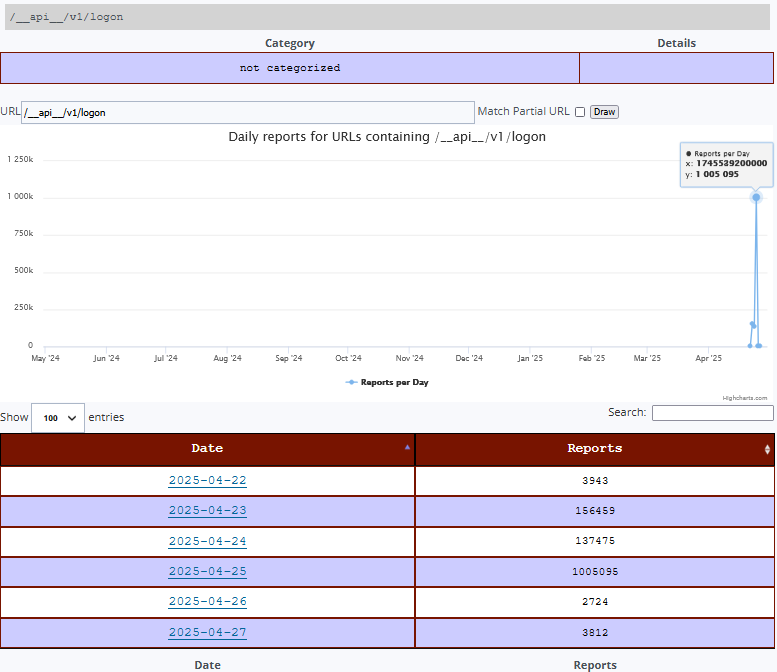
There was a post initially published in January 2022 showing an exploitable "probable zero-day vulnerabilities"[1] for Sonicwall but looking back in what has been submitted in the past year to ISC, this past week was the first time we have been getting some reports. The activity occured on the 23 April 2025 between 18:00 - 19:00 UTC but since then based on activity reported to DShield (see graphs below) has been happening almost daily:
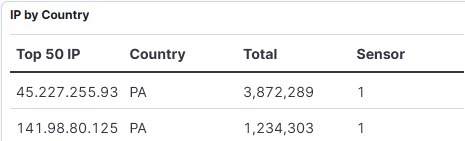
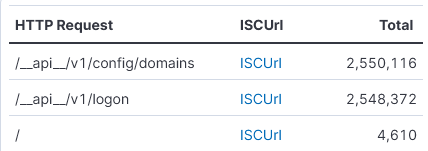
The DShield sensors (2) captured a significant probe for 3 URL from IPs 45.227.255.93 141.98.80.125. The 3 URLs are as follows:
Path Scanned
A review of the data submitted to DShield shows this activity for the first time on the 22 April 2023
/__api__/v1/config/domains [3]
/__api__/v1/logon [4]
Indicator
45.227.255.89
45.227.255.93
141.98.80.125
141.98.80.146
[1] https://es-la.tenable.com/blog/cve-2021-20016-zero-day-vulnerability-in-sonicwall-secure-mobile-access-sma-exploited
[2] https://cow-prod-www-v3.azurewebsites.net/publications/security-advisories/2021-006/pdf
[3] https://isc.sans.edu/weblogs/urlhistory.html?url=L19fYXBpX18vdjEvY29uZmlnL2RvbWFpbnM=
[4] https://isc.sans.edu/weblogs/urlhistory.html?url=L19fYXBpX18vdjEvbG9nb24=
-----------
Guy Bruneau IPSS Inc.
My GitHub Page
Twitter: GuyBruneau
gbruneau at isc dot sans dot edu
如有侵权请联系:admin#unsafe.sh