
SAP发布针对CVE-2025-31324的紧急补丁,修复SAP NetWeaver中的零日漏洞。该漏洞为未认证文件上传高危风险(CVSS 10.0),已被用于攻击部署恶意软件。建议用户立即安装补丁以应对威胁。 2025-4-25 16:0:24 Author: www.tenable.com(查看原文) 阅读量:33 收藏
April 25, 2025
3 Min Read

SAP has released out-of-band patch to address CVE-2025-31324, a critical zero-day vulnerability in SAP NetWeaver that has been exploited by threat actors. Organizations are strongly encouraged to apply patches as soon as possible.
Background
On April 22, ReliaQuest published details of their investigation of exploit activity in SAP NetWeaver servers. Initially it was unclear if their discovery was a new vulnerability or the abuse of CVE-2017-9844, a vulnerability that could lead to a denial-of-service (DoS) condition or arbitrary code execution. ReliaQuest reported their findings to SAP and on April 24, SAP disclosed CVE-2025-31324, a critical missing authorization check vulnerability with the highest severity CVSS score of 10.0.
| CVE | Description | CVSSv3 | VPR |
|---|---|---|---|
| CVE-2025-31324 | SAP NetWeaver Unauthenticated File Upload Vulnerability | 10.0 | 8.1 |
*Please note: Tenable’s Vulnerability Priority Rating (VPR) scores are calculated nightly. This blog post was published on April 25 and reflects VPR at that time.
Analysis
CVE-2025-31324 is an unauthenticated file upload vulnerability affecting the Metadata Uploader component of SAP NetWeaver Visual Composer. Successful exploitation of this vulnerability could allow an unauthenticated attacker to upload malicious files which can be used by an attacker to achieve code execution. The flaw is the result of missing authorization checks to the “/developmentserver/metadatauploader” endpoint. According to ReliaQuest, this vulnerability has been exploited in the wild as a zero-day by threat actors who have abused the flaw to upload malicious web shells to affected hosts. These webshells were used to deploy malware and establish communications with command and control (C2) servers.
Proof of concept
At the time this blog was published, no proof-of-concept (PoC) code had been published for CVE-2025-31324. If a public PoC exploit becomes available, we anticipate a variety of attackers will attempt to leverage this flaw in their attacks as SAP products are widely used by a variety of organizations, including government agencies.
Solution
SAP has released patches for affected versions of SAP NetWeaver. At this time, the SAP security note #3594142 is not publicly accessible, so we are unable to provide a list of affected and patched versions. It is important to note that these patches were released after SAP’s April 2025 Security Patch Day published on April 8. So even if those patches were applied, you will still need to apply the out-of-band patches released for CVE-2025-31324.
Identifying affected systems
A list of Tenable plugins for this vulnerability can be found on the individual CVE page for CVE-2025-31324 as they’re released. This link will display all available plugins for this vulnerability, including upcoming plugins in our Plugins Pipeline.
Additionally, customers can utilize Tenable Attack Surface Management to identify public facing assets running SAP NetWeaver by using the following filters:
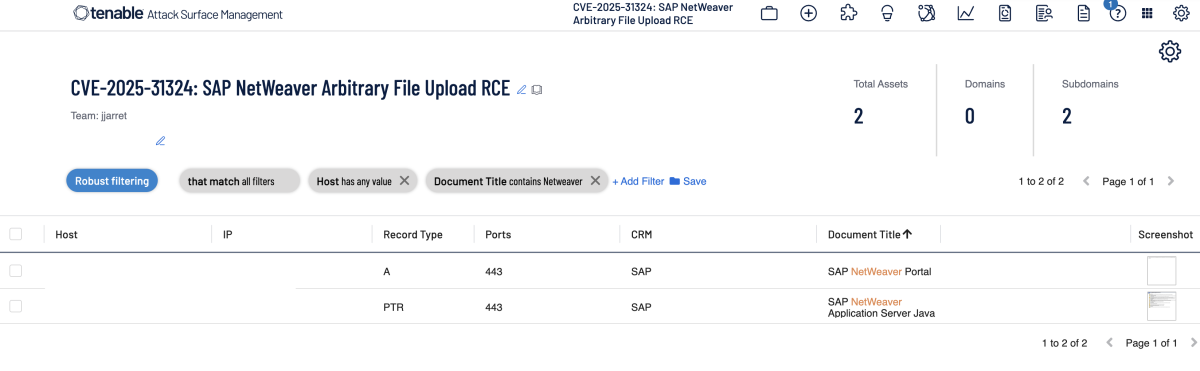
Get more information
- ReliaQuest Blog: ReliaQuest Uncovers New Critical Vulnerability in SAP NetWeaver
- SAP Security Patch Day - April 2025
Join Tenable's Security Response Team on the Tenable Community.
Learn more about Tenable One, the Exposure Management Platform for the modern attack surface.

Scott Caveza
Senior Staff Research Engineer, Security Response
Scott joined Tenable in 2012 as a Research Engineer on the Nessus Plugins team. Over the years, he has written hundreds of plugins for Nessus, and reviewed code for even more from his time being a team lead and manager of the Plugins team. Previously leading the Security Response team and the Zero Day Research team, Scott is currently a member of the Security Response team, helping the research organization respond to the latest threats. He has over a decade of experience in the industry with previous work in the Security Operations Center (SOC) for a major domain registrar and web hosting provider. Scott is a current CISSP and actively maintains his GIAC GWAPT Web Application Penetration Tester certification.
Interests outside of work: Scott enjoys spending time with his family, camping, fishing and being outdoors. He also enjoys finding ways to break web applications and home renovation projects.
- Exposure Management
- Vulnerability Management
Cybersecurity news you can use
Enter your email and never miss timely alerts and security guidance from the experts at Tenable.
如有侵权请联系:admin#unsafe.sh