文章描述了一起利用Cloudflare隧道基础设施分发远程访问木马(RAT)的网络攻击活动。攻击链复杂,涉及钓鱼邮件、LNK文件、HTA文件及PowerShell脚本等多个阶段,并通过隐藏文件和动态DNS等技术规避检测。Sekoia TDR团队通过多种Sigma规则和CTI情报成功识别并追踪该活动。 2025-4-22 07:2:19 Author: blog.sekoia.io(查看原文) 阅读量:29 收藏
During our daily tracking and analysis routine at Sekoia TDR team (Threat Detection & Research), we have been monitoring an attacker infrastructure internally called “Cloudflare tunnel infrastructure to deliver multiple RATs”. This infrastructure is used by several actors to host malicious files and deliver remote access trojans (RAT). Several security vendors (Forcepoint, Fortinet, Orange, Proofpoint) have reported that the mentioned infrastructure has been operational since at least February 2024, illustrating its resilience. The related infection chains relying upon that infrastructure is particularly complex, with multiple steps involved (as explained in the schema below) and some variations observed from one campaign to another.
The objectives of these campaigns require analysis by examining the entire malware chain. This analysis will not be detailed here, but the data theft objective remains probable, and consistent with most active cybercriminals intrusion sets.
This report describes one of the latest observed infection chains (delivering AsyncRAT) relying on the Cloudflare tunnel infrastructure and the attacker’s tactics, techniques and procedures (TTPs), with a principal focus on detection opportunities. We will illustrate how the Sekoia Defend platform detects the different steps with several detection rules that will be shared in the technical details part.
Figure 1. Infection chains distributing AsyncRAT
The usual initial access vector used in that campaign (and still the most prevalent when targeting employees) is a phishing email, often disguised as an invoice or order, attempting to deceive the recipient into opening a malicious attachment under a false sense of urgency. Some of these emails may employ a deceptive tactic by including a fabricated conversation thread with a forged reply.
Figure 2. Phishing email sample
The attachment contained in the phishing email is an old “application/windows-library+xml” file type. and in the year 2025, it is not the primary method to access files over the network (we will explain why below). While this type of file is sometimes blocked at an email gateway, it is not always the case as it may be considered as a safe file format compared to binary ones.
It is possible to block this kind of malicious email using a simple Sigma rule “Suspicious Email Attachment Received”. It allows us to detect this suspicious attachment. This kind of rule is trivial as we only want to detect a list of given suspicious extensions in any events related to an email and a file. Most of our telemetry hits are either true positives or false positives easy to filter out in a given customer context (mostly IT actions). As we did not initially have the “.ms-library” extension, the rule was updated following that investigation.
Figure 3. Suspicious ms-library file sample
If we look into that file content, the remote WebDav resource is clearly displayed and the file format is easy to detect and block eventually.
Figure 4. Suspicious ms-library file sample
Opening that file will open a warning pop-up for the user, and upon validation, it will create a network connection to the WebDav remote resource mentioned in the “url” entry, displaying the remote file.
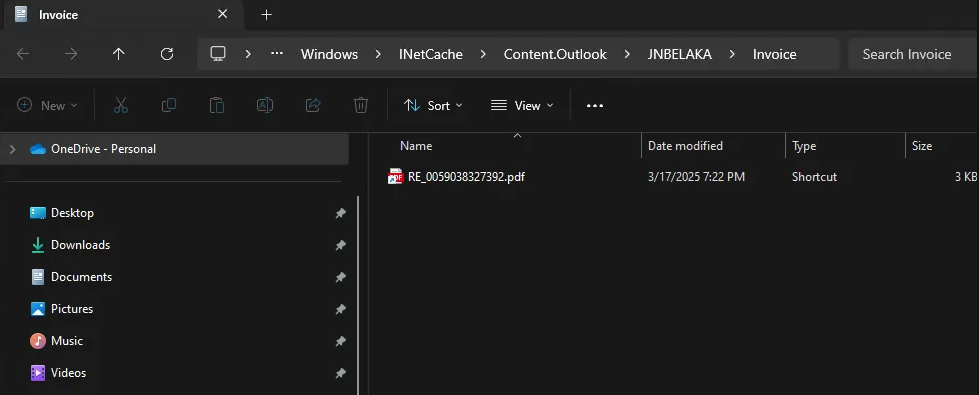
Figure 5. Explorer Window displaying the malicious remote file
In the first step of the execution, the deceptive tactic employed involves a LNK file disguised as a shortcut to a PDF file, which makes it relevant to the phishing email’s theme. LNK files are commonly used in Windows systems to create shortcuts to other files or directories. The direct download of a LNK file from a browser triggers the mechanism where modern web browsers append a “.download” extension to such files to prevent automatic execution.
Therefore, the attacker’s use of LNK access over the network likely aimed to bypass detection. Moreover, attempting to open the LNK file triggers a pop-up warning from Windows Security features, further hindering the attack.
Figure 6. Pop-up Window warning following user interaction
When the user interaction succeeded in passing these previous steps, the LNK execution will not open a PDF file but instead runs an HTA file (usually on the same website, but in some cases it can be a distinct one).
Figure 7. LNK file properties pointing to the HTA file
The HTA file uses Windows VBScript language to execute a BAT file from the same remote server.
Figure 8. Suspicious HTA content
The HTA execution triggers the simple Sigma rule “Mshta Suspicious Child Process”, matching on the “cmd.exe” process run from “mshta.exe”. This is a really efficient way to detect that first step, which does not generate many false positives in our customer’s environments (only around 60 alerts in the last few days globally).
Figure 9. Mshta Suspicious Child Process related events
The Sigma correlation rule “HTA Infection Chains” aims at detecting any infection chain using an HTA file followed by some suspicious commands. In that case we are raising an alert, based on the temporal proximity between the HTA file creation and the “mshta.exe” that runs the previous file with the Explorer application as a parent process.
Figure 10. HTA Infection Chains related events
The BAT file execution is quite complex (with many steps and relying on obfuscation to prevent any quick analysis/detection). In short, the script still leverages PowerShell to download and install its dependencies (two files archives containing the Python language and the Python scripts). For more detailed information, we advise you to read the Fortinet report, which is very complete and interesting.
Figure 11. PowerShell execution for Python installation
Figure 12. Installation folders
The BAT script’s main objective is to proceed with the next step that requires Python language. This condition induces a particularly noisy activity as a side effect, which succeeded in triggering our rule “ISO LNK Infection Chain”. In this rule, we are looking for an archive file created on disk (here not an ISO but an XZ archive) and followed by some Windows commands within five minutes. The Python installation directory embedding some archives files followed by PowerShell commands could trigger this kind of behaviour.
Figure 13. ISO LNK Infection Chain related events
The last two Sigma correlation rules are more difficult to enable in some environments where a lot of command-line administration tools are used. Indeed IT administrators usually need to perform commands that are similar to some attackers’ TTPs. To overcome these difficulties, it is possible to build an alert filter using temporal conditions. It requires some effort but it makes it usable in this kind of environment.
In the second step of the execution, the obfuscated Python continues by injecting the next stage to several “notepad.exe” processes.
Figure 14. Injection to notepad.exe
Persistence is created using the Windows Startup folder with two VBS files and one BAT file, similar to the previous BAT file in terms of obfuscation. The VBS files are likely used to detect sandbox detonation with a loop over pressing a given key.
The obvious way to detect this behaviour/technique is to monitor these filesystems entries continuously. However, this can lead to false positives in the detection process. To avoid this downside, it is possible to use a hunting query which would quickly help the analyst to find the unusual entries.
Figure 15. Startup folder with the added VBS and BAT files
Using the new Sekoia Operating Language, we could detect those entries with the following query.
events
| where timestamp >= ago(30d)
| where file.path contains "Startup\"
| where file.path contains "Users"
| distinct file.pathCode 1. SOL query sample for startup folder entries
| C:\Users\*\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\PWS.vbs |
| C:\Users\*\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\pws1.vbs |
| C:\Users\*\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\startupppp.bat |
Code 2. SOL query results in our lab
The next stage uses PowerShell to reflectively load a payload downloaded from a JPEG image hosted on a public website with a base64 payload.
Figure 16. PowerShell code run for the latest stage
This loading technique through the process “AddInProcess32” triggers our rule “Suspicious PowerShell Keywords” precisely on the “[System.Reflection.Assembly]::Load()” call.
Finally the remote access trojan (RAT) channel to its command and control server (C2) is fully established.
Figure 17. Connection to the AsyncRAT C2
After the BAT file has completed the Python part installation, some cleanup and defensive evasion is done. The script action can be flagged by the common Sigma rule “Hiding Files With Attrib.exe”, detecting the usage of the Windows command “attrib.exe” with the parameters allowing to change the Python folders properties to mark it as a hidden one for Windows file system (in that case “Extracted” and “Print”).
Figure 18. Attrib commands to hide installation folders
That technique is frequently used as well by legitimate software, but could help as a weak signal in that case. The fact it would occur several minutes after the initial infection could be difficult to correlate with the attack, but the used folder paths are an indicator as they look very suspicious.
Almost all previously mentioned files are hosted in the attacker infrastructure, which is the suspicious URI using the “Cloudflare tunnel infrastructure” relying on the TryCloudflare service with the WebDAV protocol. Off note, from our latest tests, we observed that the fake PDF invoice file, which was displayed to the user, is not always hosted in this infrastructure.
Figure 19. TryCloudflare hosted files
As this attacker infrastructure is under our continuous watch, we were able to detect the actual detonation network connection to this domain by our CTI feed.
Figure 20. WebDAV connections from the infected host
The intermediate image file for the reflective DLL was hosted on a compromised website which was not known to us as an attacker infrastructure but which has a very suspicious file name: “ENCRYPTION01.jpg”. The exact same technique has been used in other infection chains. We will not detail it in this report, but we will continue to monitor it.
Figure 21. Suspicious image and the hidden base64 code
The last network accesses to the AsyncRAT C2, are hosted to public IP addresses resolving to domain names using the “dyndns.org” service. This is detected both by our CTI feed (AsyncRAT C2 are tracked), and by our Sigma rule based on CTI enrichment “Dynamic DNS Contacted”.
Figure 22. Dynamic DNS Contacted related events
While this rule is a very effective way to find suspicious C2 connections, it can be challenging to implement in environments where this type of activity is common.
This report delves into the intricate details of a multi-stage attack that has been exploiting a resilient network infrastructure, referred to as “Cloudflare tunnel infrastructure to deliver multiple RATs” since February 2024.
The mentioned infection chain is trying to bypass security defenses in various and complicated ways. One could be surprised that such techniques are being used by attackers in 2025, when efficient security products combined with in depth security measures should prevent such attacks. This example illustrates how cyber threat intelligence (CTI) combined with detection rules enhances detection capabilities. Indeed, our resilience to the evolving infection chains of attackers is hopefully maintained by our detection rules strategy. This strategy uses a mixture of CTI and in-depth coverage of the possible attacker steps, from basic TTPs to a combination of several TTPs.
Sekoia TDR team is committed to ongoing monitoring of similar attacks and will bolster proactive defense strategies by evaluating the efficiency of existing detection methods.
Command and Control servers
malawi-light-pill-bolt[.]trycloudflare[.]com
players-time-corresponding-th[.]trycloudflare[.]com
spaces-corner-notices-battery[.]trycloudflare[.]com
xi-if-grows-valued[.]trycloudflare[.]com
phvnmarch8787[.]duckdns[.]orgFiles hashes
0d8d46ec44e737e6ef6cd7df8edf95d83807e84be825ef76089307b399a6bcbb (mslibrary attachment)
c935cc41342794c23d640333a1ddd511f9c51e5b790261dc848ec5f7ac28650a (ben.bat)
47453b0ad93f60254ffb30a0964e0b8b6f1979e199d707b971c6ab6277fe0185 (jmb.hta)
5d932bfda0ffd31715700de2fd43fc89c0f1d89eeabac92081ebe2062da84152 (pws1.vbs)
0d7cee0c13374181a23e8f605b32f2969c9c490b83c7891318f26bd17777fd7c (PWS.vbs)
e0e0f9a1082b641acff2cb225454342ca54109d01001b0e20b4fac0c9d5501a4 (RE_0059038327392.pdf.lnk)
c458a21ae510f81fd76affb147ce84008c66b9dab246f6a2322e0f3b137e0539 (RE_070362683042.pdf.lnk)
33feae2e66e25f1b2d5905e0ce7b837bdeb6e8e9782ab39ff06b2243a7c4b5e7 (RE_1047389392.pdf.lnk)
a0a446acd5540772ab9a3ae2f78f94f9a203cae06249d9e70710d7f797ff9da9 (startupppp.bat)
0ff5dd1787acc886a586282858112c6f73b48c31093080d2d8a6e66f018ce8c7 (ENCRYPTION01.jpg)Sigma rules
如有侵权请联系:admin#unsafe.sh