Gartner 2025年软件供应链安全指南强调企业需实现SDLC全生命周期可见性、保护软件交付完整性并持续提升安全态势。Binarly平台通过二进制分析、AI漏洞检测、加密资产管理和持续监控等技术,帮助组织实现上述目标,确保软件供应链安全可靠。 2025-4-19 08:25:38 Author: www.binarly.io(查看原文) 阅读量:13 收藏
In April 2025, Gartner released its Market Guide for Software Supply Chain Security (SSCS), highlighting three core objectives for enterprise CISOs (Chief Information Security Officers) and cybersecurity leaders to prioritize:
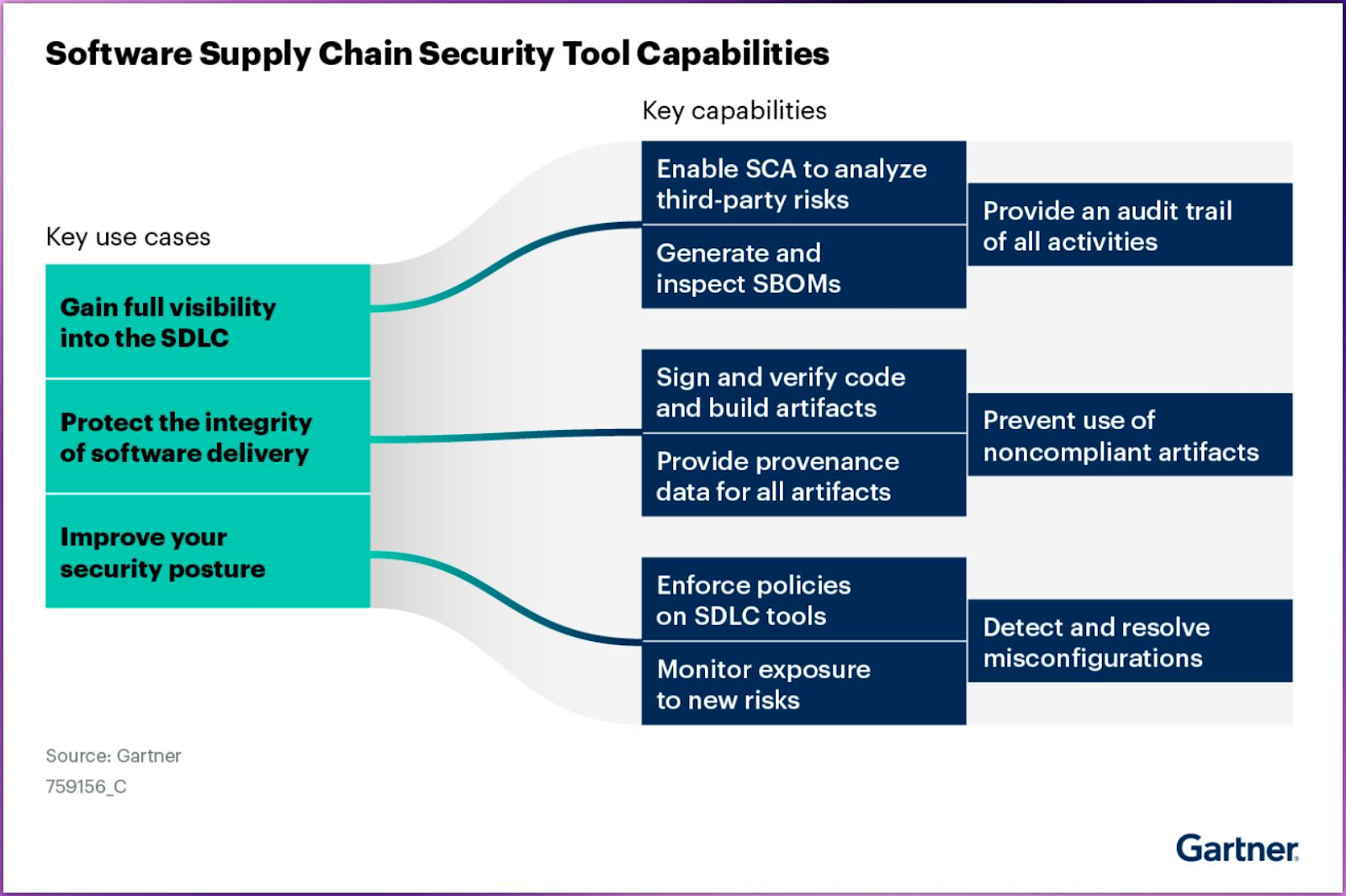
- Gain full visibility into the Software Development Lifecycle (SDLC) and secure-by-design principles.
- Protect the integrity of software delivery, and
- Improve the organization’s foundational security posture.
These use cases (visualized in Gartner’s SSCS framework) underscore the need for robust tools and processes to secure every link in the software supply chain, including layers below the operating system.

Binarly’s firmware and software supply chain security platform aligns closely with these objectives. Below, we map the Binarly Transparency Platform’s key capabilities -- binary analysis, AI-driven detection of vulnerabilities and implants, cryptographic asset management, and continuous monitoring -- to each of Gartner’s SSCS categories in a direct, solutions-focused way.
Gain Full Visibility into the SDLC
Gartner stresses that organizations must achieve full visibility into the software development lifecycle (SDLC) – including all code, components, and dependencies, even from third parties, to manage supply chain risk.
This entails capabilities like third-party software composition analysis (SCA), generating software bills of materials (SBOMs), and tracking component provenance data.
Binarly addresses this need for transparency by performing deep binary analysis on firmware and software artifacts, going beyond source code to illuminate everything that’s being built and shipped. By examining compiled binaries directly, Binarly uncovers hidden components and vulnerabilities that traditional source-focused tools might miss.

Some of the ways Binarly provides comprehensive SDLC (secure-by-design) visibility include:
- Third-Party SCA and Dependency Discovery: Binarly’s platform automatically identifies all components within a binary, including open-source libraries, proprietary modules, and even statically linked or dynamically loaded dependencies. This means security teams see the true composition of software, not just the declared dependencies. By revealing transitive dependencies and embedded third-party code, Binarly enables an accurate assessment of risks from any external or legacy component. In practice, this functions as a powerful third-party SCA, flagging known vulnerable components anywhere in your firmware or software (even if the original file names or versions aren’t obvious). As Gartner’s guidance suggests, this level of visibility into third-party code is foundational for supply chain security.
- Automated SBOM Generation (with Provenance Data): Knowing what’s inside your software is critical. Binarly automates the creation of detailed SBOMs for every software build or firmware image. These SBOMs enumerate both visible and hidden components in the code, including supplier names, component versions, and even origins, which provides essential provenance information. By generating SBOMs directly from binaries, Binarly holds your suppliers (and internal teams) accountable – you can verify that what a vendor delivered matches what’s documented. Provenance data in this context means you have a chain of evidence for each component: who developed it, which version is included, and how it got into your product. This transparency is exactly what Gartner calls for to “gain full visibility” across the SDLC. Furthermore, Binarly can validate SBOMs by cross-checking declared components versus actual binary content, ensuring no hidden or risky code slips through the cracks.
- Vulnerability and Malware Detection for Opaque Code: Visibility isn’t just about inventorying components – it’s also about understanding their security posture. Binarly uses advanced binary analysis techniques (including AI) to detect known vulnerabilities and hidden threats in third-party or proprietary code. For example, Binarly’s platform can scan firmware binaries to find instances of known vulnerable functions and even detect malicious implants or backdoors lurking in the code. This AI-driven detection goes beyond a simple CVE lookup; Binarly analyzes the context and behavior of binary code to catch security issues that may not be apparent from component names alone. The result is a richer visibility into the quality and safety of all software in your SDLC. With Binarly, a CISO gains a unified view of software components and their risks across the entire SDLC – from source to build to final binary – fulfilling Gartner’s first pillar of software supply chain security.
Protect the Integrity of Software Delivery
The second major Gartner use case is ensuring that the software your organization delivers (or deploys) hasn’t been tampered with and meets your security requirements.
To protect the integrity of software delivery, enterprises need capabilities such as enforcement of security policies during the build and release process, verification of artifact integrity (e.g. via signatures or hash checks), and provenance tracking for every change.
The Binarly Transparency Platform contributes to delivery integrity by integrating into development pipelines and proactively vetting artifacts before they ship. It acts as a guardian in the CI/CD process to catch issues or unauthorized changes early, thus preserving the integrity of the software supply chain.

Key Binarly capabilities that support software delivery integrity include:
- CI/CD Integration and Policy Enforcement: Binarly can be embedded in your continuous integration/continuous delivery pipeline to perform security checks on each build. By automatically scanning binaries for vulnerabilities, weak components, or policy violations, Binarly enables you to enforce corporate security policies before software is released.
For instance, you can set a policy that no critical vulnerabilities or banned licenses are present in a release and Binarly will flag any build that violates these criteria. The platform leverages up-to-date threat intelligence during these scans to ensure new threats are caught early and also checks for compliance with open-source license policies and other governance rules.
In Gartner’s framework, this aligns with protecting the pipeline and ensuring the software delivery process is secure and auditable.
- Artifact Integrity Verification and Tamper Detection: Maintaining integrity means guaranteeing that the code you deliver is exactly what was intended – no hidden surprises. Binarly’s cryptographic asset management features help here by identifying cryptographic elements and verifying their usage.
The platform can discover embedded cryptographic keys or certificates in firmware/software and flag any that are leaked or unintended. It also analyzes cryptographic algorithms used, to ensure no weak or unauthorized crypto is present, effectively creating a Cryptography Bill of Materials (CBOM) – a list of all cryptographic assets in the software – which is vital for integrity and compliance.
Additionally, the platform detects signs of tampering or injection by recognizing code patterns that don’t belong (malicious modifications, backdoors) even if they were never seen before, acting as a backstop against supply chain attacks that insert malware into the build
- Secure Release Management and Provenance Tracking: Every component that goes into a release can be traced and approved with Binarly in the loop. By producing SBOMs and CBOMs for each build, Binarly provides a provenance record of what’s in your software and where it came from. This means if there is a question about a particular library or firmware module, you have data on its origin and can verify if it’s the expected version from the trusted source.
Binarly provides reports that effectively timestamp and document the security state of each artifact at release, which helps in verifying integrity later (for example, if a device in the field is running a firmware, you can compare it against the approved SBOM/CBOM for that version to ensure no unauthorized changes).
Through such capabilities, Binarly enforces a strong chain-of-custody for software artifacts. This directly supports Gartner’s call to “protect the integrity of software delivery” by making sure that what gets delivered is exactly what was intended, and that it adheres to the organization’s security standards at every step.
Improve Your Security Posture
Finally, Gartner highlights the need to continuously improve your security posture with respect to the software supply chain. This is a continuous effort that includes monitoring for new risks, learning from past incidents, and adapting your defenses to reduce exposure over time.
Key capabilities here include real-time risk monitoring, proactive vulnerability management, and post-deployment validation of software integrity. Binarly’s platform is designed for continuous security improvement: it not only finds issues in the moment, but also provides the tooling and threat intelligence to help teams respond to emerging threats and tighten their security posture with each release. By covering the entire supply chain – from pre-development component vetting to post-deployment firmware auditing – Binarly ensures security isn’t a one-time checkbox but a continual process of risk reduction.

Here’s how Binarly supports ongoing enterprise security posture improvement:
- Continuous Vulnerability Monitoring and Threat Intelligence: Binarly operates on the principle that software security is never “done” at release. The platform continuously ingests threat intelligence about newly discovered vulnerabilities, malware, and attack techniques, and it updates its scanning engines accordingly.
This means that even after your software is deployed, Binarly can quickly identify if a new CVE affects one of your components or if a new firmware threat signature matches something in your devices. By integrating this continuous monitoring into the SDLC (for example, as a scheduled scan or part of each new code integration), Binarly helps ensure each release is checked for regressions or new vulnerabilities that might have surfaced.
- Post-Deployment Validation and Asset Management: Improving posture also means verifying that security controls remain effective in live environments. Binarly’s approach to post-deployment validation is to extend the same deep binary inspection to firmware and software running in the field. For example, manufacturers or enterprises can use Binarly to analyze firmware updates before deploying them to ensure they are free of vulnerabilities or malicious code.
Likewise, after deployment, one can periodically extract and inspect firmware from devices (or use telemetry, where available) to ensure it hasn’t been altered and still matches the approved secure baseline. Binarly’s cryptographic asset management (via CBOM) contributes here by monitoring cryptographic components over time – if a certificate in a device firmware is approaching expiration or a cryptographic algorithm is newly deemed vulnerable, the platform will highlight it so you can take action.
This kind of ongoing audit of software in its operational environment helps catch security drift (e.g., unintended changes or emerging weaknesses) and thus improves overall resilience. It closes the feedback loop: you don’t just trust that a product was secure at release, you continuously verify and maintain its integrity throughout its lifecycle.
- Analytics and Remediation Guidance for Risk Reduction: A critical aspect of posture improvement is learning from findings and strengthening processes. Binarly provides rich analytics on the vulnerabilities and issues it discovers. Each vulnerability is categorized by severity and even mapped to common weakness categories (CWEs) to illuminate the root causes.
The platform’s AI research assistant can explain how a given vulnerability works and what its impact could be in your particular context. Armed with this insight, development teams and security teams can prioritize fixes for the most critical weaknesses and understand where in the SDLC they need better controls. Binarly even helps verify that mitigation measures (like compiler security flags or runtime protections) are consistently applied, so you can catch any lapses and fix them in the next cycle.
Over time, this leads to fewer vulnerabilities making it into production and a stronger security posture. Essentially, Binarly’s continuous monitoring and actionable intelligence enable a cycle of continuous improvement (detect issues, fix root causes, enforce improvements in policy) which is exactly the outcome Gartner envisions by focusing on security posture.
Conclusion
CISOs and enterprise product security teams are increasingly tasked with safeguarding an entire software supply chain that spans everything from third-party code libraries to device firmware.
Gartner’s 2025 SSCS framework provides a clear set of goals (visibility, integrity, and ongoing risk reduction) for building a resilient software supply chain security program. Binarly’s platform delivers on these goals by applying deep binary analysis and AI-driven intelligence across every stage of the software lifecycle. It generates granular visibility into all software components (even those hidden in binaries), enforces integrity through continuous pipeline checks and anomaly detection, and enables continuous posture improvement with ongoing monitoring and rich insights.
In practice, Binarly helps CISOs not only check the box on SCA or SBOM generation, but also truly operationalize those capabilities, ensuring that no matter where a risk might creep in, it is identified, addressed, and fed back into a cycle of improvement. This comprehensive, coordinated approach allows organizations to stay ahead of supply chain threats and deliver software and firmware that customers and stakeholders can verifiably trust.
如有侵权请联系:admin#unsafe.sh