研究人员披露了Erlang/OTP SSH服务器中的一个最高严重级别的远程代码执行漏洞(CVE-2025-32433),CVSSv3评分为10.0。该漏洞允许未认证攻击者执行任意代码并完全控制设备。研究人员已发布概念验证代码,官方已发布补丁修复该漏洞。 2025-4-18 15:22:15 Author: www.tenable.com(查看原文) 阅读量:37 收藏
April 18, 2025
3 Min Read

Proof-of-concept code has been released after researchers disclosed a maximum severity remote code execution vulnerability in Erlang/OTP SSH. Successful exploitation could allow for complete takeover of affected devices.
Background
On April 16, Fabian Bäumer, Marcus Brinkmann, Marcel Maehren, and Jörg Schwenk of the Ruhr University Bochum in Germany disclosed a critical vulnerability in Erlang/OTP SSH to the OpenWall vulnerability mailing list. Additionally an official advisory was posted to the GitHub project for Erlang/OTP crediting the researchers for their disclosure.
| CVE | Description | CVSSv3 | VPR |
|---|---|---|---|
| CVE-2025-32433 | Erlang/OTP SSH Remote Code Execution Vulnerability | 10.0 | 10 |
*Please note: Tenable’s Vulnerability Priority Rating (VPR) scores are calculated nightly. This blog post was published on April 18 and reflects VPR at that time.
Analysis
CVE-2025-32433 is a remote code execution (RCE) vulnerability affecting the Erlang/OTP SSH server. The vulnerability exists due to a flaw in the SSH protocol message handling which could allow an unauthenticated attacker to execute arbitrary code. According to the advisory, all users running Erlang/OTP SSH servers are impacted and to assume impact if your application utilizes the Erlang/OTP SSH library. This vulnerability received the maximum CVSSv3 score of 10.0 and when the SSH daemon is running as root, allows an attacker to completely compromise an affected device.
At the time this blog was published, no known exploitation has been observed, however with the ease of exploitation and critical severity, we anticipate attacks will occur soon.
Proof of concept
On April 17, researchers at Platform Security released a public proof-of-concept (PoC) exploit for CVE-2025-32433. The writeup notes that the PoC was generated with the help of ChatGPT and Cursor, and that it was fairly simple to do so using those AI tools.
The PoC initiates an SSH protocol negotiation as a normal client would. But, before authenticating the user, the client sends an unexpected message with an arbitrary command. The vulnerable server will process these messages and execute the commands. A patched server will disconnect immediately upon seeing these messages prior to authentication.
An additional PoC has been released, and the Horizon3 Attack Team posted on X (formerly Twitter) that they had developed a PoC but have chosen not to release it as of writing.
Just finished reproducing CVE-2025-32433 and putting together a quick PoC exploit — surprisingly easy. Wouldn’t be shocked if public PoCs start dropping soon. If you’re tracking this, now’s the time to take action. #Erlang #SSH pic.twitter.com/hBqJMfFHMN
— Horizon3 Attack Team (@Horizon3Attack) April 17, 2025
Solution
Erlang/OTP has released patches to address this vulnerability.
| Affected Versions | Fixed Versions |
|---|---|
| OTP-27.3.2 and below | OTP-27.3.3 |
| OTP-26.2.5.10 and below | OTP-26.2.5.11 |
| OTP-25.3.2.19 and below | OTP-25.3.2.20 |
If immediate patching cannot be performed, restricting access via a firewall or disabling the SSH server are mitigation steps provided by Erlang/OTP. However, we strongly recommend upgrading as soon as possible to fully remediate this vulnerability.
Identifying affected systems
A list of Tenable plugins for this vulnerability can be found on the individual CVE page for CVE-2025-32433 as they’re released. This link will display all available plugins for this vulnerability, including upcoming plugins in our Plugins Pipeline.
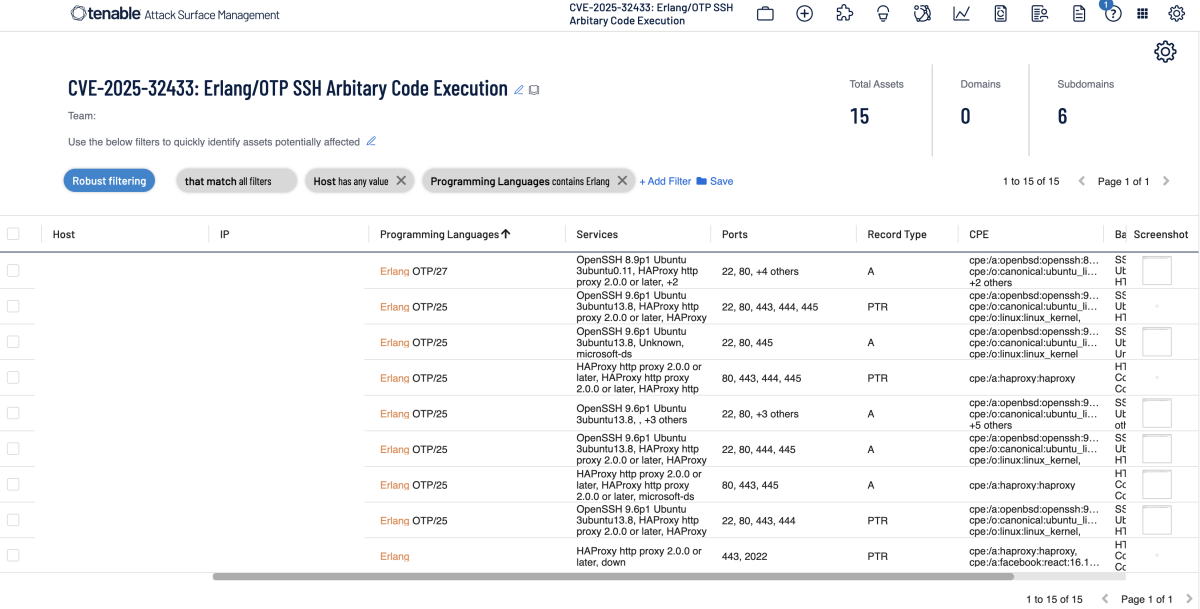
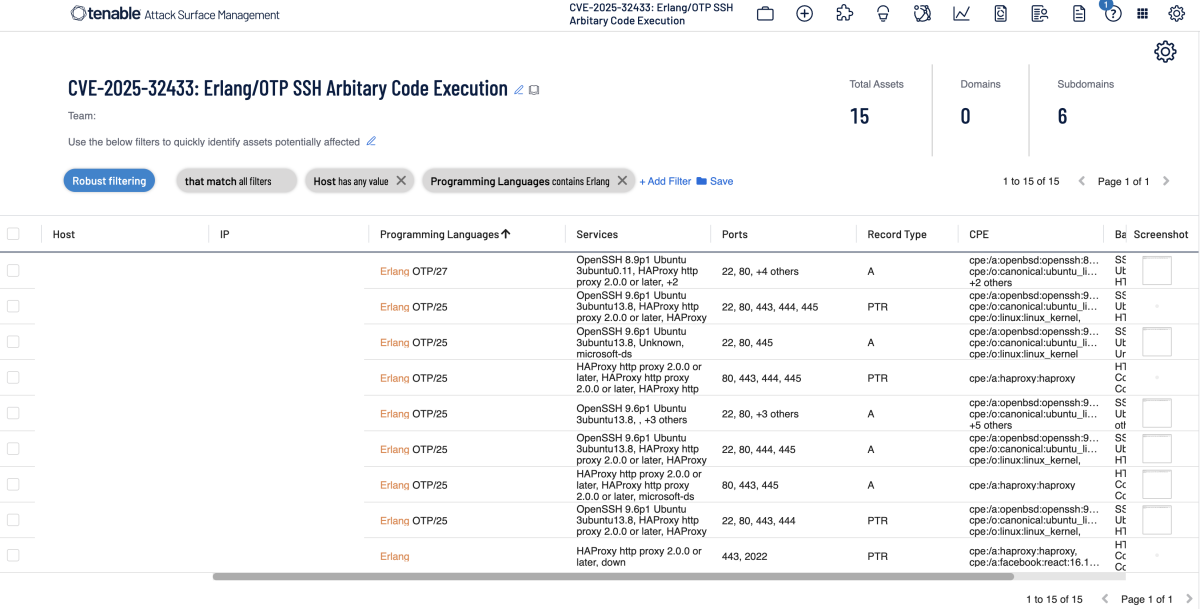
Additionally, customers can utilize Tenable Attack Surface Management to identify hosts running Erlang/OTP SSH Server.
Get more information
Join Tenable's Security Response Team on the Tenable Community.
Learn more about Tenable One, the Exposure Management Platform for the modern attack surface.

Scott Caveza
Staff Research Engineer, Security Response
Scott joined Tenable in 2012 as a Research Engineer on the Nessus Plugins team. Over the years, he has written hundreds of plugins for Nessus, and reviewed code for even more from his time being a team lead and manager of the Plugins team. Previously leading the Security Response team and the Zero Day Research team, Scott is currently a member of the Security Response team, helping the research organization respond to the latest threats. He has over a decade of experience in the industry with previous work in the Security Operations Center (SOC) for a major domain registrar and web hosting provider. Scott is a current CISSP and actively maintains his GIAC GWAPT Web Application Penetration Tester certification.
Interests outside of work: Scott enjoys spending time with his family, camping, fishing and being outdoors. He also enjoys finding ways to break web applications and home renovation projects.

Ben Smith
Ben Smith Staff Research Engineer, Vulnerability Detection, Tenable
Ben joined Tenable in 2015 to pull apart packets for Nessus Network Monitor. Since then he’s donned many hats, working on products, plugins and content. Most recently, Ben has found a home providing vulnerability research and coverage via Nessus plugins. Prior to Tenable, Ben spent years as a customer, working on all aspects of vulnerability management and defending networks.
- Exposure Management
- Vulnerability Management
Cybersecurity news you can use
Enter your email and never miss timely alerts and security guidance from the experts at Tenable.
如有侵权请联系:admin#unsafe.sh