Active Directory是IT基础设施的核心,负责身份验证和资源管理。常见的攻击如Kerberoasting和AS-REP Roasting利用配置错误或弱密码进行破坏。采用分层模型(Tier Model)严格隔离资源层级,减少横向移动风险。禁用不受限委派、使用Protected Users组保护敏感账户,并强化LDAP及SMB通信安全。实时监控与渗透测试是保障AD安全的关键措施。 2025-4-8 08:59:22 Author: www.vaadata.com(查看原文) 阅读量:3 收藏

Introduction
Active Directory (AD) is at the heart IT infrastructures. It manages identities, access and network resources. However, it is often poorly secured, making it a prime target for attackers.
An Active Directory compromise can have disastrous consequences. An attacker who gains control can access the entire network, steal data and deploy malicious softwares. In this article, we take a look at best practices for securing your Active Directory. In particular, we’ll look at common vulnerabilities and attacks, as well as configuration flaws that can compromise the security of your AD.
Comprehensive Guide to Active Directory Security Best Practices
- Understanding Active Directory and its Key Role in IT Infrastructures
- What are the Best Practices for Securing Active Directory?
- Carry out a pentest to assess and strengthen the security of your Active Directory
- Conclusion
Understanding Active Directory and its Key Role in IT Infrastructures
What is Active Directory?
Active Directory (AD) is a directory service developed by Microsoft. It is the backbone of identity and access management in Windows environments.
Its main objective is to centralise the authentication and administration of resources (users, machines, applications, permissions) within a network.
AD is based on a hierarchical structure organised into domains, forests, organisational units (OUs) and objects:
- A domain is a logical entity grouping AD objects under the same management and authentication policy.
- A forest is a set of domains that share a common schema but may have distinct policies.
- Organisational units are used to organise and structure domain objects according to the organisation of the company (e.g. HR, IT, Accounting departments).
- Each resource (user, computer, group, printer, etc.) is an AD object with specific attributes.
The Domain Controller (DC) is a server that hosts AD and manages user authentication. Its role is to check credentials (username and password) and apply security policies via Group Policy Objects (GPOs).
GPOs can be used to define specific configurations on network machines, such as password rules, connection parameters or access restrictions.
Finally, in terms of authentication, Active Directory relies on two main protocols: Kerberos and NTLM (NT LAN Manager).
Active Directory is a critical component of an organisation’s network. It controls access to critical resources: sensitive files, applications, servers and workstations. If compromised, it can jeopardise the entire information system.
An attacker who manages to gain access with a standard user account may try to obtain higher rights. To do this, he can exploit vulnerabilities or misconfigurations: Kerberoasting, misconfigured kerberos delegations, lateral movements, domain controller takeovers, etc.
To reduce these risks, it is essential to secure Active Directory proactively. This involves reducing the attack surface, strict segmentation of access and systems, hardening of systems and advanced intrusion detection.
Let’s take a closer look.
What are the Best Practices for Securing Active Directory?
Partitioning Active Directory components: Focus on the Tier Model
Active Directory security is based on a defence-in-depth approach, and one of the fundamental principles for limiting risks is the partitioning of components.
In an environment where cyber-attacks are becoming increasingly sophisticated, uncontrolled access to the AD can have disastrous consequences for the organisation.
The Tier Model, recommended by ANSSI, enables a strict segmentation to be applied between privilege levels and critical resources.
The aim is simple: to prevent a compromise at user workstations (the most exposed) from leading to privileges being escalated to domain controllers.
Why segment Active Directory?
Segmentation based on the Tier Model offers a number of strategic advantages in terms of cyber security:
- Reduced risk of privilege escalation: An attacker who compromises a user workstation should never be able to escalate his privileges to servers or domain controllers.
- Isolation of critical resources: Essential systems (domain controllers, servers) are protected from threats from less secure equipment.
- Limitation of lateral attacks: Good segmentation slows down the propagation of an attack within the network, making it more difficult to exploit transversal vulnerabilities.
- Better management of access and permissions: Compartmentalising roles and access prevents administrators or users from having unnecessary rights.
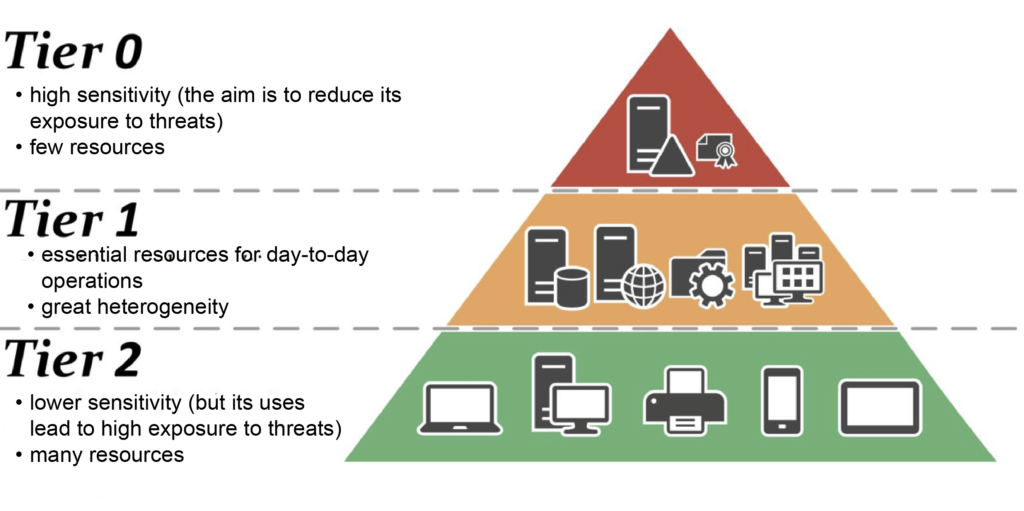
Understanding the three-tier model
The Tier Model is based on a hierarchy of privileges and resources administered within the organisation. It is structured in three tiers:
- Tier 0 represents the trusted core of the system. It includes the organisation’s most sensitive systems and accounts: domain controllers (DCs), AD administrator accounts, identity management servers (PKI, ADFS, etc.) as well as accounts and systems with administrative rights on AD. In fact, a compromise at this level gives the attacker total control over Active Directory and, by extension, over the entire information system.
- Tier 1 encompasses the resources essential to the operation of the business. It includes business and application servers, critical databases, industrial systems and specialised equipment, as well as application server administrator accounts. A compromise at this level could affect critical business data and disrupt internal and external IT services.
- Finally, Tier 2 focuses on user workstations and peripherals (printers, scanners and other connected devices). It should also be noted that user workstations are the main entry point for attacks (phishing, malware, malicious code execution). So an attacker seeking to elevate his privileges will almost always start by compromising a standard user account.
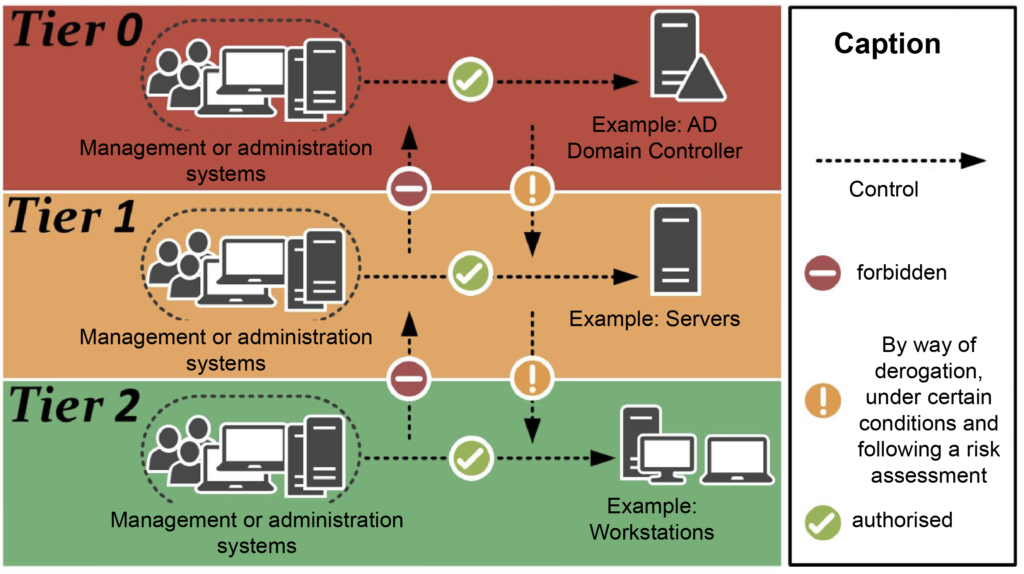
Ensuring hermeticity between tiers
The effectiveness of the Tier Model is based on strict isolation between each tier. A fundamental principle is that a Tier must never administer a higher-level Tier. Here are the essential rules to ensure effective segmentation:
- Firstly, Tier 0 administrators only use dedicated secure workstations (PAWs) and never connect to lower-level resources.
- Secondly, Tier 1 servers must never be accessible for administration from a Tier 2 user workstation.
- In addition, administration accounts and groups must be strictly limited and reviewed regularly.
- Finally, the use of RDP sessions, PowerShell Remote and other administration tools must be controlled and monitored.
The rigorous application of the Tier Model drastically reduces the possibility of an Active Directory environment being compromised. Indeed, an organisation that effectively partitions its resources and applies strict administrative controls significantly reduces the risks associated with lateral movements and elevation of privileges.
However, this model is not the only solution, but must be combined with other security best practices.
Reducing Active Directory attack surface
Active Directory is a prime target for attackers seeking to escalate their privileges or move laterally in a network.
Several techniques are used to exploit well-known vulnerabilities in AD services (AD CS, AD DS, AD FS). It is therefore crucial to apply strict controls to reduce the attack surface and minimise the risks.
Protecting Active Directory against Kerberoasting
Kerberoasting is an attack that allows an attacker with a valid account to extract Kerberos service tickets and attempt to crack them offline to recover passwords in clear text.
This works because the service tickets are encrypted with the password hash of the associated service account. If this account uses a weak password, the attacker can break it with tools such as Hashcat and gain access.

To reduce the risk of this vulnerability, the following security controls should be implemented:
- Use gMSAs (Group Managed Service Accounts) for these objects. They will have automatic password management with rotation to prevent passwords being broken.
- Limit the privileges of accounts with an SPN (Service Principal Name) and prevent them from being members of high privilege groups (e.g. Domain Admins) in order to reduce the impact of a compromise.
Countering AS-REP Roasting
AS-REP Roasting is an attack that targets user accounts configured with the ‘Do not require Kerberos pre-authentication’ option.
An attacker with no privileges can request an authentication ticket (AS-REP) for these accounts and retrieve a response encrypted with the user’s password hash. If this account uses a weak password, the attacker can break it with Hashcat and gain access to the account.
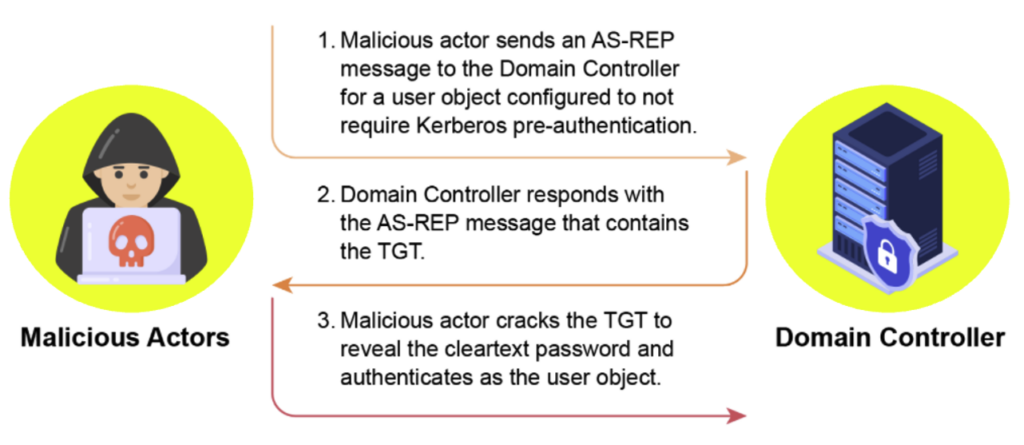
To reduce the risk of this vulnerability, the following security controls should be implemented:
- Enable Kerberos pre-authentication on all accounts. If an account needs to bypass it, limit its privileges and prevent it from being a member of high-privilege groups (e.g. Domain Admins).
- Use strong passwords: minimum 30 characters, making sure they are unique and managed correctly.
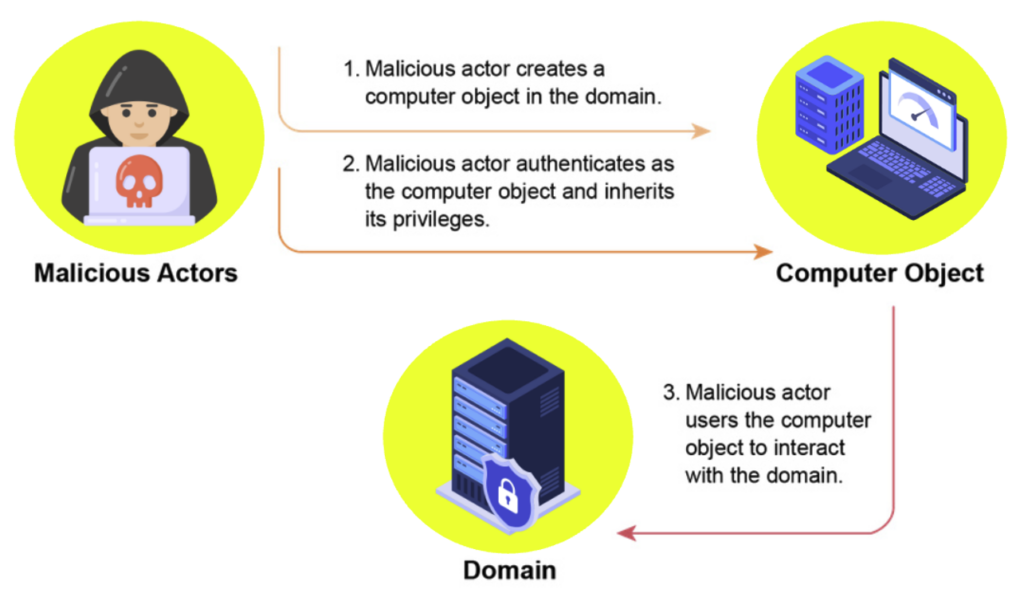
Prevent machines from being added to the AD domain
The presence of the MachineAccountQuota attribute comes from a default configuration in Active Directory. This attribute allows any authenticated user to create up to 10 machine accounts in the domain.
An attacker with no privileges can exploit this by registering a new computer, thereby obtaining a machine account with its own credentials. This machine can then be used to carry out various attacks within the domain (including delegation attacks).
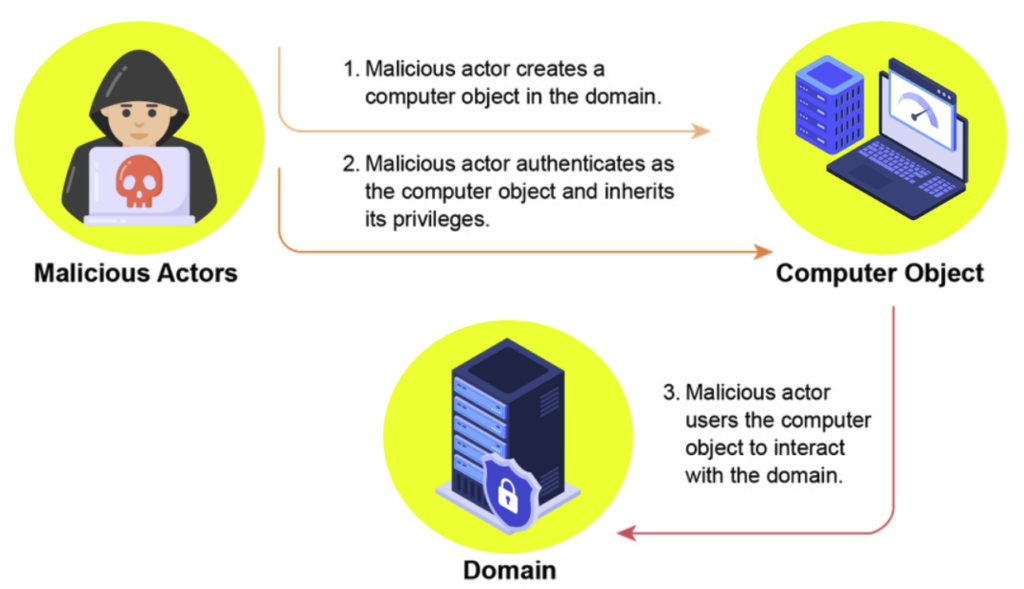
To reduce the risk of this vulnerability, simply prevent unprivileged users from adding machines to the domain by setting the MachineAccountQuota attribute to 0.
Deactivate Unconstrained Delegation
Unconstrained Delegation is a risky configuration that allows a machine to usurp the identity of users connecting to it in order to access other services.
Unlike Constrained Delegation, which limits these rights to specific services, Unconstrained Delegation allows access to any service.
When a user authenticates to a machine with this configuration, their Kerberos ticket (TGT) is stored in the memory of the LSASS process. An attacker who compromises this computer can extract these tickets and use them to impersonate the user and elevate their privileges. If a domain administrator has logged in, the attacker can retrieve his ticket and take full control of the environment.
There are also techniques for forcing a user to authenticate, which makes this attack even more dangerous.
To reduce the risk of this vulnerability, the following security controls should be implemented:
- Disable Unconstrained Delegation on machine objects or use Resource-Based Constrained Delegation instead if necessary.
- Configure privileged accounts as ‘sensitive and non-delegable’.
- Add privileged accounts to the ‘Protected Users’ security group to prevent them from being delegated.
- Disable the ‘Print Spooler’ service on domain controllers to prevent it being exploited in forced authentication attacks.
Hardening Active Directory security
Applying security fixes to an Active Directory environment is an essential first step, but it is not enough to guarantee effective protection. Many of Microsoft’s default configurations are not optimised for security, leaving vulnerabilities that can be exploited by attackers.
It is therefore necessary to reinforce the security posture by implementing additional measures such as restricting administrative access, monitoring connections and hardening communication protocols.
Strengthening LDAP: Channel Binding & Signing
LDAP Channel Binding & Signing is a security feature that uses cryptographic mechanisms to strengthen the authentication and confidentiality of Lightweight Directory Access Protocol (LDAP) communications.
By enabling LDAP Signing, LDAP connections are secured against Man in the Middle (MitM) attacks, preventing an attacker from intercepting or modifying the data exchanged between a client and a domain controller.
In addition, enabling LDAP Channel Binding reduces the risk of identity theft by requiring a stricter binding between the TLS connection and the underlying LDAP session.
Securing SMB communications with SMB Signing
SMB (Server Message Block) Signing is a security mechanism that ensures the integrity and authenticity of SMB communications by digitally signing each message exchanged between a client and a server.
By enabling this feature, each SMB request is associated with a cryptographic signing, preventing SMB Relay attacks where an attacker could intercept and replay authenticated communications.
Protecting sensitive accounts with the Protected Users group
The Protected Users security group is a feature introduced with Windows Server 2012 R2. It automatically applies enhanced security restrictions to accounts added to it. These restrictions include prohibiting the use of weak authentication methods (such as NTLM, Kerberos with DES/RC4, or unconstrained delegation); thus preventing several types of attack, including Pass the Hash and Pass the Ticket.
Including privileged accounts (such as domain administrators) in this group considerably reduces the attack surface by imposing more secure authentication and limiting the validity period of Kerberos tickets.
Securing local administrator accounts with LAPS (Local Administrator Password Solution)
Local Administrator Password Solution (LAPS) is a Microsoft solution for automatically managing passwords for local administrator accounts on workstations and servers. LAPS generates and stores unique, complex and regularly renewed passwords for each machine.
Monitoring and logging Active Directory events
Effective Active Directory monitoring enables suspicious behaviour to be identified quickly and action taken before an attacker compromises the environment.
Implementing detailed logging and real-time monitoring of critical events is essential to maintaining robust security.
Log activation and centralisation using a SIEM
The Windows audit log must be activated to record events linked to connections, changes to Active Directory objects and the creation of accounts.
However, storing these logs locally is insufficient: centralisation with a SIEM (Security Information and Event Management) is necessary to detect and correlate incidents in real time.
Once the logs have been collected, rules need to be defined to identify suspicious activities and trigger automatic alerts.
Suspicious activity detection and incident response
Certain events should be monitored closely, as they often indicate an attempted compromise:
- A series of authentication failures on privileged accounts may indicate a brute force attack.
- Unusual access to sensitive resources (critical servers, databases) may indicate an attempt to exfiltrate data.
- The creation of a new account with elevated privileges outside normal processes is a potential sign of privilege escalation.
- Any unauthorised modification of GPOs should be analysed immediately, as attackers manipulate them to establish persistence or disable security controls.
Integrating automatic alerts on these actions allows security teams to intervene quickly before an attack spreads.
GPO and critical Active Directory modification monitoring
Group Policy Objects (GPOs) play a key role in the configuration and management of workstations and servers within a domain. Attackers often try to modify them to disable protections, create backdoors or propagate malicious payloads.
It is therefore essential to :
- Monitor all changes made to critical GPOs, particularly those applied to domain controllers.
- Regularly compare current configurations with defined security standards.
- Set up regular snapshots of group policies to detect any suspicious changes.
Carry out a pentest to assess and strengthen the security of your Active Directory
An Active Directory penetration test is an essential exercise for assessing vulnerabilities in the environment and testing the robustness of security controls.
By adopting a proactive approach, vulnerabilities can be corrected before they are exploited, thereby limiting the risk of compromise and ensuring greater resilience in the face of cyber attacks.
Conclusion
Securing Active Directory is an ongoing task. Initial configuration is not enough: constant monitoring and regular testing are needed to anticipate threats.
A well-protected AD is based on several pillars: reduction of privileges, hardening of configurations, active monitoring and security audits. By applying these best practices, businesses can limit risks and strengthen their resilience in the face of cyber attacks.
Authors: Alexis PARET – Pentester & Amin TRAORÉ – CMO @Vaadata
如有侵权请联系:admin#unsafe.sh