
微软在2025年3月的补丁更新中修复了56个安全漏洞,包括7个零日漏洞(其中6个已被野外利用),涉及远程代码执行、权限提升等高风险问题,并影响多个产品组件如Windows、Office及Azure服务等。 2025-3-11 17:33:45 Author: www.tenable.com(查看原文) 阅读量:145 收藏
March 11, 2025
5 Min Read

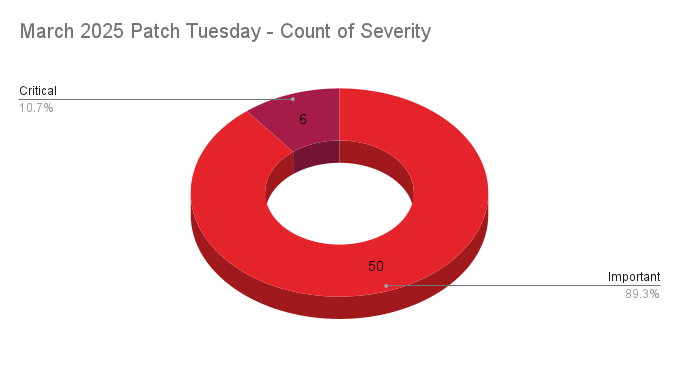
- 6Critical
- 50Important
- 0Moderate
- 0Low
Microsoft addresses 56 CVEs, including seven zero-day flaws, with six of those being exploited in the wild.
Microsoft patched 56 CVEs in its March 2025 Patch Tuesday release, with six rated critical, and 50 rated as important.
This month’s update includes patches for:
- .NET
- ASP.NET Core & Visual Studio
- Azure Agent Installer
- Azure Arc
- Azure CLI
- Azure PromptFlow
- Kernel Streaming WOW Thunk Service Driver
- Microsoft Local Security Authority Server (lsasrv)
- Microsoft Management Console
- Microsoft Office
- Microsoft Office Access
- Microsoft Office Excel
- Microsoft Office Word
- Microsoft Streaming Service
- Microsoft Windows
- Remote Desktop Client
- Role: DNS Server
- Visual Studio
- Visual Studio Code
- Windows Common Log File System Driver
- Windows Cross Device Service
- Windows Fast FAT Driver
- Windows File Explorer
- Windows Hyper-V
- Windows Kernel Memory
- Windows Kernel-Mode Drivers
- Windows MapUrlToZone
- Windows Mark of the Web (MOTW)
- Windows NTFS
- Windows NTLM
- Windows Remote Desktop Services
- Windows Routing and Remote Access Service (RRAS)
- Windows Subsystem for Linux
- Windows Telephony Server
- Windows USB Video Driver
- Windows Win32 Kernel Subsystem
- Windows exFAT File System
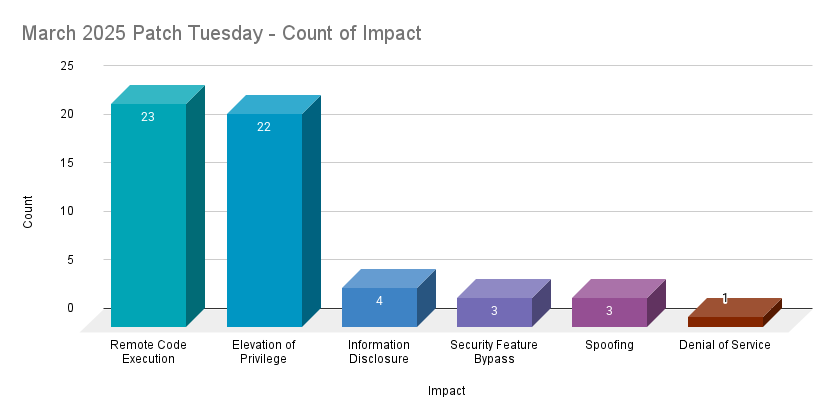
Remote code execution (RCE) vulnerabilities accounted for 41.1% of the vulnerabilities patched this month, followed by elevation of privilege (EoP) vulnerabilities at 39.3%.
CVE-2025-26633 | Microsoft Management Console Security Feature Bypass Vulnerability
CVE-2025-26633 is a security feature bypass vulnerability in the Microsoft Management Console (MMC). It was assigned a CVSSv3 score of 7.0 and is rated important. An attacker could exploit this vulnerability by convincing a potential target with either standard user or admin privileges to open a malicious file.
According to Microsoft, CVE-2025-26633 was exploited in the wild as a zero-day. This is the second zero-day in the MMC to be exploited in the wild since CVE-2024-43572, a RCE vulnerability patched in October 2024.
CVE-2025-24985 | Windows Fast FAT File System Driver Remote Code Execution Vulnerability
CVE-2025-24985 is a RCE vulnerability in the Windows Fast FAT File System Driver. It was assigned a CVSSv3 score of 7.8 and is rated as important. A local attacker could exploit this vulnerability by convincing a potential target to mount a specially crafted virtual hard disk (VHD). Successful exploitation would grant an attacker arbitrary code execution.
According to Microsoft, CVE-2025-24985 was exploited in the wild as a zero-day. This is the first vulnerability in Windows Fast FAT File System to be reported since 2022 and the first to be exploited in the wild.
CVE-2025-24044 and CVE-2025-24983 | Windows Win32 Kernel Subsystem Elevation of Privilege Vulnerabilities
CVE-2025-24044 and CVE-2025-24983 are EoP vulnerabilities in the Windows Win32 Kernel Subsystem. CVE-2025-24044 and CVE-2025-24983 were assigned CVSSv3 scores of 7.8 and 7.0 respectively, while both vulnerabilities are rated as important. A local, authenticated attacker would need to win a race condition in order to exploit CVE-2025-24983. Successful exploitation of either vulnerability would allow the attacker to gain SYSTEM privileges.
According to Microsoft, CVE-2025-24983 was exploited in the wild as a zero-day. While CVE-2025-24044 was not exploited, Microsoft assessed it as “Exploitation More Likely” according to Microsoft’s Exploitability Index. Prior to this month, Microsoft patched seven vulnerabilities in the Win32 Kernel Subsystem (one in 2022, five in 2024, one earlier in 2025), though CVE-2025-24983 is the first to be exploited in the wild.
CVE-2025-24993 | Windows NTFS Remote Code Execution Vulnerability
CVE-2025-24993 is a RCE vulnerability in Windows New Technology File System (NTFS). It was assigned a CVSSv3 score of 7.8 and is rated as important. According to Microsoft, a heap-based buffer overflow can be exploited in order to execute arbitrary code on an affected system. In order to exploit this vulnerability, an attacker must entice a local user to mount a crafted VHD. According to Microsoft, this flaw was reportedly exploited in the wild as a zero-day.
CVE-2025-24984, CVE-2025-24991, CVE-2025-24992 | Windows NTFS Information Disclosure Vulnerabilities
CVE-2025-24984, CVE-2025-24991 and CVE-2025-24992 are information disclosure vulnerabilities in Windows NTFS. Both CVE-2025-24991 and CVE-2025-24992 were assigned CVSSv3 scores of 5.5, while CVE-2025-24984 was assigned a score of 4.6. All three of these vulnerabilities were rated as important and can be exploited in physical attacks such as an attacker utilizing a malicious USB drive or by enticing a local user to mount a crafted VHD.
While two information disclosure vulnerabilities in Windows NTFS have previously been patched in 2022 (CVE-2022-26933) and 2023 (CVE-2023-36398), CVE-2025-24984 and CVE-2025-24991 are the first to have been exploited in the wild as zero-days.
CVE-2025-26630 | Microsoft Access Remote Code Execution Vulnerability
CVE-2025-26630 is a RCE vulnerability in Microsoft Access. It was assigned a CVSSv3 score of 7.8 and is rated as important. An attacker could exploit this vulnerability by using social engineering to convince a potential target to download and run a malicious file on their system. Successful exploitation would grant an attacker arbitrary code execution.
According to Microsoft, CVE-2025-26630 is considered a zero-day vulnerability as it was publicly disclosed prior to a patch being available. This is the sixth vulnerability in Microsoft Access disclosed since 2023. However, this is the fourth zero-day to be publicly disclosed and attributed to Unpatched.ai. Three were disclosed in Microsoft’s January 2025 Patch Tuesday release (CVE-2025-21186, CVE-2025-21366, CVE-2025-21395)
CVE-2025-24035 and CVE-2025-24045 | Windows Remote Desktop Services Remote Code Execution Vulnerabilities
CVE-2025-24035 and CVE-2025-24045 are RCE vulnerabilities in Windows Remote Desktop Services. Each was assigned a CVSSv3 score of 8.1 and rated as critical. To exploit these flaws, an attacker must be able to win a race condition. Despite this requirement, Microsoft assessed both flaws as “Exploitation More Likely.”
Tenable Solutions
A list of all the plugins released for Microsoft’s March 2025 Patch Tuesday update can be found here. As always, we recommend patching systems as soon as possible and regularly scanning your environment to identify those systems yet to be patched.
For more specific guidance on best practices for vulnerability assessments, please refer to our blog post on How to Perform Efficient Vulnerability Assessments with Tenable.
Get more information
- Microsoft's March 2025 Security Updates
- Tenable plugins for Microsoft March 2025 Patch Tuesday Security Updates
Join Tenable's Security Response Team on the Tenable Community.
Learn more about Tenable One, the Exposure Management Platform for the modern attack surface.
![]()
Tenable Security Response Team
The Tenable Security Response Team (SRT) tracks threat and vulnerability intelligence feeds to ensure our research teams can deliver sensor coverage to our products as quickly as possible. The SRT also works to analyze and assess technical details and writes white papers, blogs and additional communications to ensure stakeholders are fully informed of the latest risks and threats. The SRT provides breakdowns for the latest vulnerabilities on the Tenable blog.
- Exposure Management
- Vulnerability Management
Cybersecurity news you can use
Enter your email and never miss timely alerts and security guidance from the experts at Tenable.
如有侵权请联系:admin#unsafe.sh