
文章讨论了Ghost勒索软件团伙利用已知漏洞攻击组织的问题,并提供了缓解建议。同时,探讨了如何吸引和留住网络安全人才的方法,并介绍了CIS关于恶意软件的最新报告、AI安全黑客马拉松、更新后的CIS基准以及国际执法行动打击勒索软件团伙的情况。 2025-2-21 14:0:0 Author: www.tenable.com(查看原文) 阅读量:31 收藏
Check out mitigation recommendations to protect your organization against the Ghost ransomware gang. Plus, get tips on how to attract and retain top cybersecurity professionals. And get the latest on the most prevalent malware; CIS Benchmarks; an AI security hackathon; and much more!
Dive into six things that are top of mind for the week ending Feb. 21.
1 - CISA: Ghost ransomware gang exploits known vulnerabilities
For years, ransomware group Ghost has been making hay out of well-known vulnerabilities for which patches have long been available – and it continues to aggressively pick low-hanging fruit by targeting outdated software.
That’s the warning that the U.S. Cybersecurity and Infrastructure Security Agency (CISA) and the Federal Bureau of Investigation (FBI) made this week in their joint advisory “#StopRansomware: Ghost (Cring) Ransomware.”
Since 2021, China-based Ghost, also known as Cring, Crypt3r and Phantom, has been using publicly available code to attack internet-facing servers whose software and firmware contain years-old vulnerabilities – including one disclosed and patched in 2009.

“This indiscriminate targeting of networks containing vulnerabilities has led to the compromise of organizations across more than 70 countries, including organizations in China,” the advisory reads. Ghost’s main motivation is financial.
CVEs that Ghost has specifically targeted include:
Security teams will find indicators of compromise (IoCs); tactics, techniques and procedures (TTPs); and mitigation recommendations in the advisory.
Some high-level recommendations to mitigate Ghost ransomware attacks include:
- Patch known vulnerabilities in operating systems, firmware and software on a timely basis using risk prioritization.
- Segment networks to restrict lateral movement.
- Protect all privileged accounts and email services accounts using phishing-resistant multi-factor authentication (MFA).
- Back up systems regularly, and store those backups separately.
For more information about ransomware prevention and mitigation:
- “Tenable Cyber Exposure Study: Defending Against Ransomware” (Tenable)
- “Protecting yourself from ransomware: a comprehensive guide to prevention and mitigation” (Cybernews)
- “Mitigating malware and ransomware attacks” (U.K. National Cyber Security Centre)
- “Ransomware: How to prevent and recover” (Canadian Centre for Cyber Security)
- “Best practices for protection from ransomware in cloud storage” (TechTarget)
2 - How CISOs can attract and retain cyber pros in competitive job market
A majority of cybersecurity professionals are unimpressed with their employers and mulling a job change, but CISOs can improve employee retention – as well as recruitment – by boosting career development opportunities.
That’s a key takeaway from the “2025 Cybersecurity Staff Compensation Benchmark Report,” based on a survey of about 525 cybersecurity professionals and published this week by IANS Research and Artico Search.
“This year’s data reinforces a critical truth – cybersecurity professionals often feel stuck in demanding roles without opportunities for meaningful career growth," Nick Kakolowski, Senior Research Director at IANS Research, said in a statement.
Specifically, the report found that more than 60% of respondents are considering changing jobs, and only one-third of respondents said they’d recommend their employer. Moreover, under 40% said they’re satisfied with their advancement opportunities.
So how can CISOs reduce turnover among top-performing cybersecurity professionals? Here are some recommendations:
- Create clear career advancement plans
- Clearly communicate growth opportunities
- Roll out leadership development programs
Meanwhile, understaffing remains a challenge, so in order to attract the best candidates, CISOs must be ready to pay them a premium – often as much as 40% above the average comparable candidate.
This is especially true for versatile cybersecurity professionals who have experience in a variety of areas, such as application security, security operations, and governance, risk and compliance. That’s because performing multiple cyber functions has become the norm on security teams.
Specifically, 61% of respondents said they devote at least 30% of their time to more than one function.
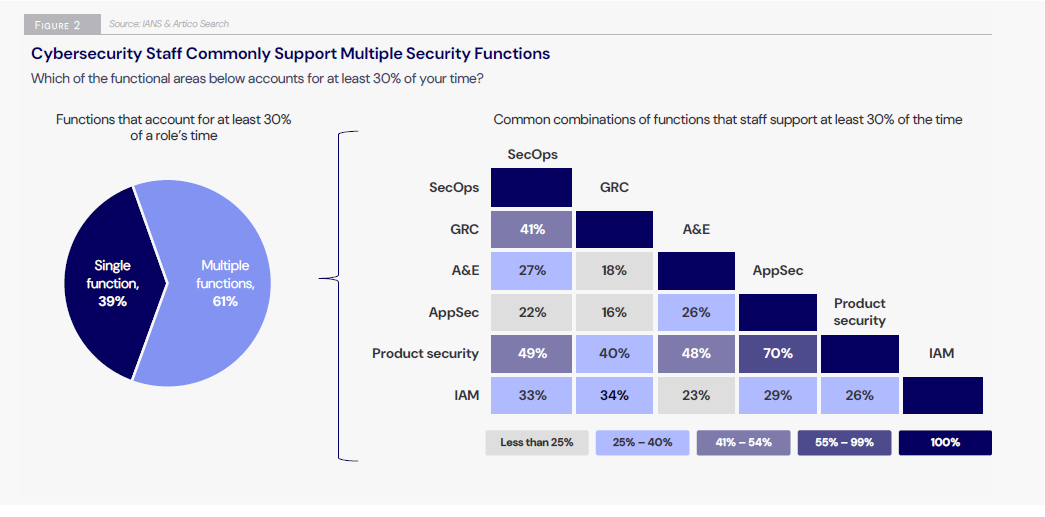
(Source: “2025 Cybersecurity Staff Compensation Benchmark Report” from IANS Research and Artico Search, February 2025)
Other interesting tidbits from the report include:
- Top-earning cyber professionals include security architects and security engineers, with average annual cash compensation of $206,000 and $191,000, respectively.
- Cybersecurity professionals who specialize in cloud security, application security and threat intelligence command higher compensation.
To get more details, check out:
- The blog “Solve Staff Hiring and Retention Issues: The Cybersecurity Staff Comp Report is Live”
- The report’s announcement “IANS Research and Artico Search Unveil the 2025 Cybersecurity Staff Compensation Benchmark Report”
- The report “2025 Cybersecurity Staff Compensation Benchmark Report”
3 - CIS: Most malware infections tied to fake update attacks
SocGholish, a variant used in fake software-update attacks, once again topped the Center for Internet Security’s malware-infections report for 2024's fourth quarter.
It’s the sixth straight time in which SocGholish ranks first on the CIS top 10 list of malware incidents, which is published quarterly.
The prevalence of SocGholish reflects the popularity of fake software-update attacks remain among hackers.
Fake software-update attacks trick users into installing a legitimate-looking update for, say, their preferred browser. Instead, the downloaded software infects their computers with malware.
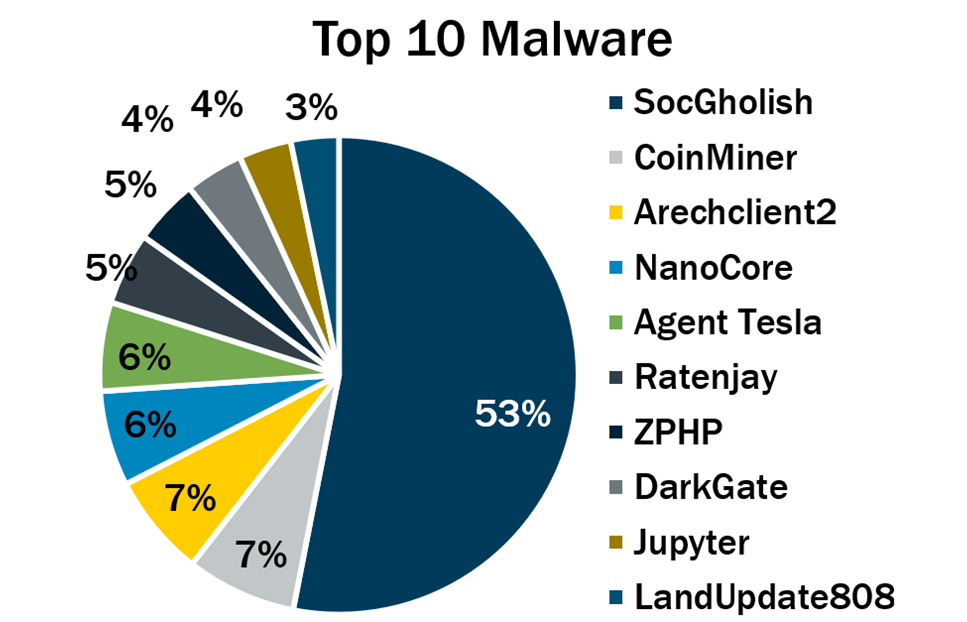
(Source: Center for Internet Security, January 2025)
Here’s the full list, in descending order:
- SocGholish, a downloader distributed through malicious websites that tricks users into downloading it by offering fake software updates
- CoinMiner, a cryptocurrency miner that spreads using Windows Management Instrumentation (WMI)
- Arechclient2, also known as SectopRAT, is a .NET remote access trojan (RAT) whose capabilities include multiple stealth functions
- NanoCore, a RAT that spreads via malspam as a malicious Excel spreadsheet
- Agent Tesla, a RAT that captures credentials, keystrokes and screenshots
- Ratenjay, a RAT that executes commands remotely and features keylogging capabilities
- ZPHP, a JavaScript downloader that’s distributed via fake browser updates
- DarkGate, a downloader and keylogger that steals financial data and personally identifiable information (PII), and delivers other malware
- Jupyter, also known as SolarMarker, an evasive and adaptive .NET infostealer often distributed via Zip and PDF files
- LandUpdate808, a JavaScript downloader distributed through malicious or compromised websites via fake browser updates
To get more information, check out the CIS blog “Top 10 Malware Q4 2024,” where you’ll find more details, context and indicators of compromise for each malware strain.
For details on fake update attacks:
- “The Fake Browser Update Scam Gets a Makeover” (Krebs on Security)
- “Watch Out: Attackers Are Hiding Malware in 'Browser Updates'” (Dark Reading)
- “Hackers Use Fake Browser Updates for AMOS Malware Attacks Targeting Mac Users” (MSSP Alert)
- “Malware crooks find an in with fake browser updates, in case real ones weren't bad enough” (The Register)
- “Hackers have been spreading malware via fake Chrome updates” (TechRadar)
VIDEOS
Fake Chrome Update Malware (The PC Security Channel)
Beware Google Chrome fake update browser pop ups that bring malware (Windows, Computers and Technology)
4 - SANS holds AI security hackathon
To encourage cybersecurity professionals and others to attain AI security knowledge and to promote the development of open-source AI security tools, SANS Institute is holding a hackathon that runs through mid-March.
“The hackathon aims to inspire participants to develop expertise in AI security, identify and support cybersecurity talent, and drive progress in AI security research through open-source contributions,” reads a SANS Institute statement.
The hackathon is aimed at cybersecurity professionals, ethical hackers, software developers and students. Entrants can participate as individuals or as part of a team.
"Through this hackathon, SANS hopes to not only contribute vital open-source tools but also encourage individuals to pursue and refine the AI security skills the industry desperately needs,” Rob Lee, Chief of Research at SANS Institute, said in the statement.
Those interested can register at the “SANS AI Cybersecurity Hackathon” website.
For more information about AI security, check out these Tenable blogs:
- “How AI Can Boost Your Cybersecurity Program”
- “6 Best Practices for Implementing AI Securely and Ethically”
- “How to Discover, Analyze and Respond to Threats Faster with Generative AI”
- “Securing the AI Attack Surface: Separating the Unknown from the Well Understood”
- “Harden Your Cloud Security Posture by Protecting Your Cloud Data and AI Resources”
5 - New, updated CIS Benchmarks released for Apache, AWS, Oracle products
The Center for Internet Security has published new and updated CIS Benchmarks for multiple products, including Apache Cassandra, AWS Compute Services and Oracle MySQL Enterprise Edition.

Here’s the full list of updated and new CIS Benchmarks for January.
Updated
- CIS Apache Cassandra 4.0 Benchmark v1.2.0
- CIS Apache Cassandra 4.1 Benchmark v1.1.0
- CIS AWS Compute Services Benchmark v1.1.0
- CIS Oracle MySQL Community Server 8.0 Benchmark v1.1.0
- CIS Oracle MySQL Enterprise Edition 8.0 Benchmark v1.4.0
New
- CIS Apache Cassandra 5.0 Benchmark v1.0.0
- CIS Oracle MySQL Community Server 8.4 Benchmark v1.0.0
- CIS Oracle MySQL Enterprise Edition 8.4 Benchmark v1.0.0
- CIS PostgreSQL 17 Benchmark v1.0.0
Organizations use the CIS Benchmarks’ secure-configuration guidelines to harden products and increase their resiliency against cyberattacks. Today, CIS offers 100-plus Benchmarks for 25-plus vendor product families. Categories of products include cloud platforms; desktop and server software; mobile devices; operating systems; and more.
To get more details, read the CIS blog “CIS Benchmarks February 2025 Update.” For more information about the CIS Benchmarks list, check out its home page, as well as:
- “How to use CIS benchmarks to improve public cloud security” (TechTarget)
- “How to Unlock the Security Benefits of the CIS Benchmarks” (Tenable)
- “Getting to Know the CIS Benchmarks” (CIS)
- “CIS Benchmarks Communities: Where configurations meet consensus” (HelpNet Security)
- “CIS Benchmarks: DevOps Guide to Hardening the Cloud” (DevOps)
VIDEO
CIS Benchmarks (CIS)
6 - Int’l operation disrupts Phobos and 8Base ransomware ops
A multinational law enforcement effort has impacted individuals and infrastructure tied to 8Base and Phobos, two ransomware groups that caused major damage last year.
The international crackdown led to the arrest of four people – all Russian nationals – and to the takedown of 27 servers used by Phobos and 8Base, according to Europol, which helped coordinate the operation involving law enforcement agencies from 14 countries.

Two of the individuals arrested were part of an affiliate ransomware gang that used Phobos to victimize 1,000-plus organizations, collecting more than $16 million in ransom payments, according to the U.S. Department of Justice.

Juan Perez
Juan has been writing about IT since the mid-1990s, first as a reporter and editor, and now as a content marketer. He spent the bulk of his journalism career at International Data Group’s IDG News Service, a tech news wire service where he held various positions over the years, including Senior Editor and News Editor. His content marketing journey began at Qualys, with stops at Moogsoft and JFrog. As a content marketer, he's helped plan, write and edit the whole gamut of content assets, including blog posts, case studies, e-books, product briefs and white papers, while supporting a wide variety of teams, including product marketing, demand generation, corporate communications, and events.
如有侵权请联系:admin#unsafe.sh