
The FCC wants stronger cyber regulations for telecoms after cyber espionage breaches. Meanwhile, fin 2024-12-13 14:0:0 Author: www.tenable.com(查看原文) 阅读量:18 收藏
The FCC wants stronger cyber regulations for telecoms after cyber espionage breaches. Meanwhile, find out why cyber pros say work has become more difficult. Plus, check out tips to prevent AI-boosted financial fraud. And get the latest on vulnerability management, EU cyber challenges and CIS predictions for 2025.
Dive into six things that are top of mind for the week ending Dec. 13.
1 - FCC seeks tighter cyber regulations for telecoms
U.S. telecommunications companies may have to comply with tougher cybersecurity regulations after at least eight of them got breached by Salt Typhoon, a cyber espionage group affiliated with the Chinese government.
“The attack underscores the urgent need for robust cybersecurity frameworks to protect against escalating threats targeting the telecommunications sector,” reads a fact sheet published by the U.S. Federal Communications Commission (FCC) this week.
Here are two key ways in which the FCC wants to tighten telecoms’ regulatory screws:
- Have telecoms annually create, update and adopt cybersecurity risk-management plans and certify the plans are compliant with FCC requirements. The FCC is seeking to implement this new cybersecurity compliance framework via a Notice of Proposed Rulemaking.
- Clarify that telecoms are legally bound to secure their networks — not just their equipment — against unlawful access and interception. This would be achieved via a declaratory ruling about Section 105 of the Communications Assistance for Law Enforcement Act (CALEA).

If FCC commissioners vote in favor of these two measures, the declaratory ruling would go into effect right away, while the cybersecurity compliance framework would be opened for public comment.
To get more details, read the FCC document, titled “Fact Sheet: Implications of Salt Typhoon Attack and FCC Response.”
For more information about the Salt Typhoon cyber espionage attacks against telecoms:
- “New CISA Hardening Guidance Provides Valuable Insights for Network Security Engineers” (Tenable)
- “China's 'Salt Typhoon' Hackers Breached US Networks Using Existing Flaws” (PCMag)
- “Salt Typhoon's surge extends far beyond US telcos” (The Register)
- “Telcos struggle to boot Chinese hackers from networks” (Axios)
- “How to protect comms infrastructure from China-backed Salt Typhoon hackers” (Tenable)
2 - Life is tough for cybersecurity pros
More cybersecurity complexity and workloads. An increase in cyberthreats. Thornier regulatory compliance. Understaffed cyber teams.
Those are the top factors making work more difficult for cybersecurity professionals, according to a report from Enterprise Strategy Group (ESG) and the Information Systems Security Association (ISSA).
“The Life and Times of Cybersecurity Professionals,” for which 369 IT and cybersecurity professionals were polled, found that 65% of respondents said cybersecurity work is harder today than it was two years ago.
Factors Making Cybersecurity Work More Difficult Than Two Years Ago
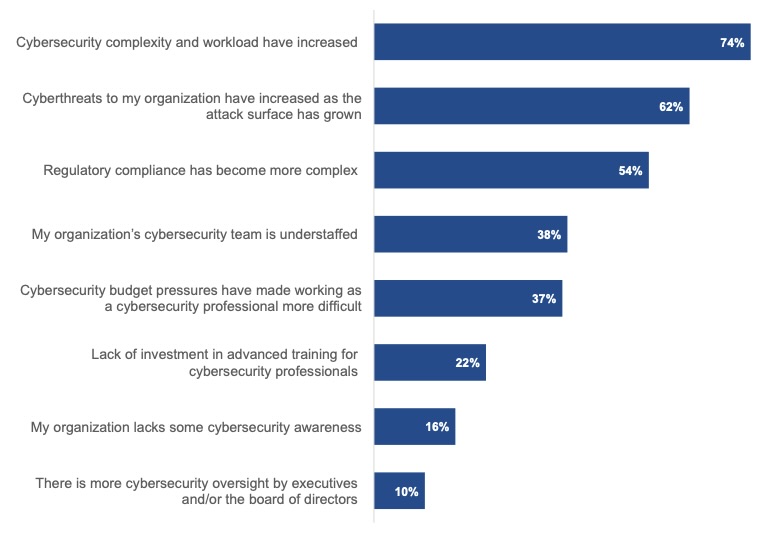
(Source: ““The Life and Times of Cybersecurity Professionals” by ESG and ISSA, December 2024)
Moreover, 57% of respondents said their job is stressful at least half the time, citing as the main reasons an overwhelming workload; disinterested business managers; IT initiatives launched without security oversight; and constant emergencies and disruptions.
So what can help strengthen cybersecurity professionals’ job satisfaction? These are the top five happiness boosters:
- Commitment from the leadership team to a strong cybersecurity posture
- Competitive compensation
- Career-advancement opportunities
- Strong leadership from the CISO and other cyber leaders
- Working with talented cybersecurity peers
“Organizations with a strong cybersecurity culture that empower the CISO and collaborate with and support the cybersecurity staff can not only improve security efficacy and efficiency but also create a harmonious and healthy work environment for cybersecurity teams,” Jon Oltsik, ESG analyst emeritus and report author, said in a statement.
For more information about stress and burnout among cybersecurity pros:
- “Can strategic AI deployment reduce cybersecurity burnout?” (Security Info Watch)
- “Persistent Burnout Is Still a Crisis in Cybersecurity” (Dark Reading)
- “Burnout: A chronic epidemic in the IT industry” (CIO)
- “The Hidden Culture Crisis and Human Burden Undermining Cybersecurity Resilience” (ISACA)
- “The Psychology of Cybersecurity Burnout” (InformationWeek)
3 - CIS experts forecast 2025 cyber trends
The Center for Internet Security (CIS) has published a bunch of 2025 predictions from its cybersecurity experts. Here’s a small sampling.
- Zero trust adoption in the enterprise will gain momentum as cybersecurity teams scramble to secure resources and data from a wider number and variety of devices and locations, driving the need to continuously verify access and authorization.
- The IT/OT convergence will deepen, as more operational technology / industrial control systems (ICS) get connected to IT networks for purposes like remote management. Consequently, organizations will emphasize vulnerability management, threat detection and security frameworks for converged environments.

- Many enterprises have accumulated a glut of cybersecurity products and are struggling to use them effectively. In 2025, many of these organizations will consolidate their tool stack, discarding redundant and unused products, which will lead to a more impactful use of the products that are kept.
- Adoption of multicloud strategies will expand, as enterprises pursue this approach to comply with new data-sovereignty laws that create geographic-location requirements for cloud data storage.
- Regulation of AI systems will increase, and as a result AI compliance frameworks will be introduced, pushing companies to improve AI security in areas such as data privacy; AI model integrity; and use of AI-generated content.
- The concept of security-by-design will be embraced by IT teams, who will accordingly incorporate security, compliance and governance early in the design phase of their IT projects.
For more information about some of these topics, check out these Tenable resources:
- "Making Zero Trust Architecture Achievable" (blog)
- "What is vulnerability management?" (guide)
- "If You Only Have 3 Minutes: Key Elements of Effective Exposure Response" (blog)
- "AI Security Posture Management" (solutions page)
- "Walking the Walk: How Tenable Embraces Its 'Secure by Design' Pledge to CISA" (blog)
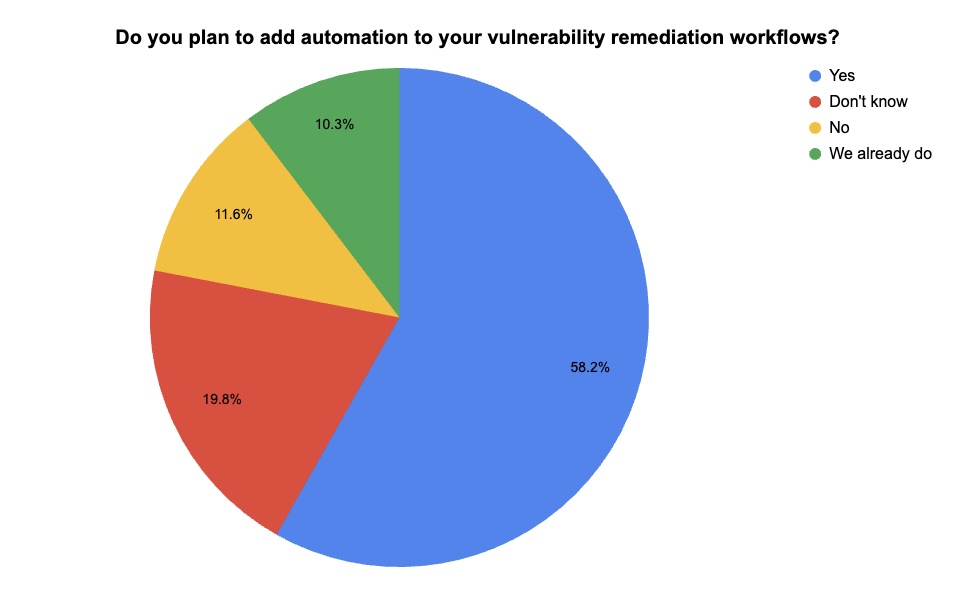
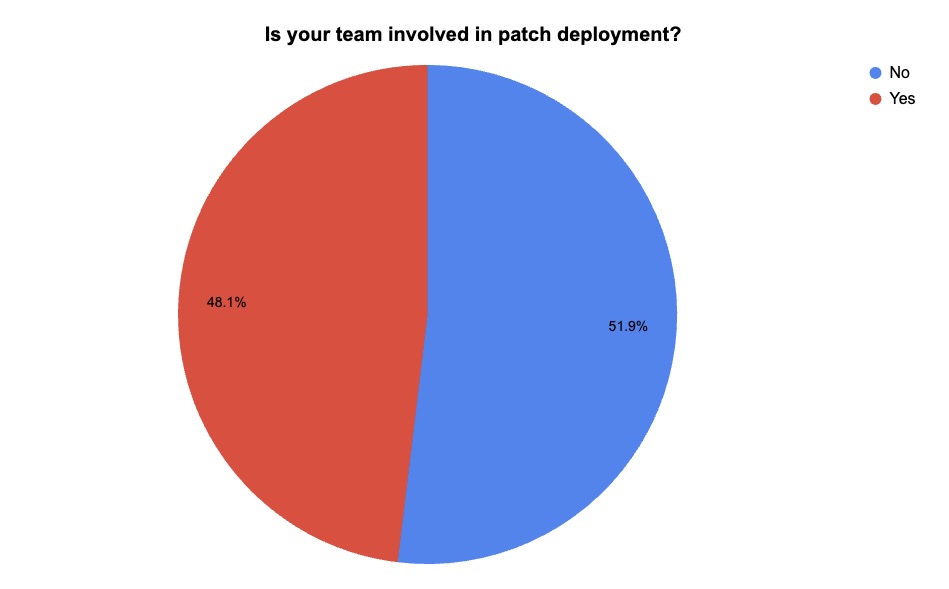
4 - Tenable poll looks at patch management, vulnerability fixes
During two recent webinars about vulnerability management, we polled attendees about their involvement with patch management and about their plans for automating vulnerability remediation. Check out how they responded.
(232 webinar attendees polled by Tenable, December 2024)
(235 webinar attendees polled by Tenable, December 2024)
Watch the on-demand webinars to learn about the latest in Tenable Vulnerability Management and in Tenable Security Center.
5 - FBI spotlights financial fraudsters’ use of GenAI
Cybercrooks are leveraging generative AI tools to sharpen financial fraud schemes against individuals and businesses, but there are ways to prevent becoming a victim.
That’s the message from the FBI in its new public service announcement titled “Criminals Use Generative Artificial Intelligence to Facilitate Financial Fraud.”
With generative AI tools, cybercriminals create believable text, images, videos and audio that seem legit, making it hard to detect financial fraud efforts, including romance scams, impersonation schemes and investment rackets.
For example, these tools allow a cybercriminal to clone voices of real people and create fake audio that sounds like them to use in phone calls. Similarly, generative AI lets scammers doctor real videos of, say, a CEO, and turn them into a clip of the CEO instructing an employee into transferring money to a fraudulent account.

To protect yourself in your personal life and at work from fraud attempts that use generative AI, FBI tips include:
- Look for subtle imperfections in images and videos.
- Pay attention to the caller’s tone of voice and word choice in phone calls.
- Verify the identity of callers by hanging up and dialing directly the organization they said they’re calling you from, like a bank.
- Don’t share sensitive information with people you’ve only met online or over the phone, nor send them money, gift cards, cryptocurrency or other assets.
For more information about the confluence of AI and financial cybercrime, including trends and prevention tips:
- “The near-term impact of AI on the cyber threat” (UK National Cyber Security Centre)
- “How a new wave of deepfake-driven cyber crime targets businesses” (Security Intelligence)
- “Managing Artificial Intelligence-Specific Cybersecurity Risks in the Financial Services Sector” (U.S. Treasury Department)
- “Identity theft is being fueled by AI & cyber-attacks” (Reuters)
- “The Dark Alliance: Addressing the Rise of AI Financial Frauds and Cyber Scams” (Michigan Journal of Economics)
6 - EU cyber agency calls for stronger supply chain security
Software supply chain security is a key challenge for European Union member nations, requiring concerted risk assessments and the development of common policies.
So said the European Union Agency for Cybersecurity, better known as ENISA, in its “2024 Report on the State of Cybersecurity in the Union,” whose goal is to assess the cyber landscape in the EU and offer policy recommendations to strengthen cybersecurity in all 27 EU countries. Securing the software supply chain is one of the priority areas identified in the report.
Currently, hackers are continuously trying to insert malware into legitimate software updates that are then distributed to customers via trusted delivery channels. By 2030, attacks against software supply chains are expected to become the top emerging cybersecurity threat.

Right now, 74% of EU countries have legislation that defines supply chain security measures, a percentage expected to increase with new EU regulatory requirements. Meanwhile, 77% of digital service providers (DSP) and operators of essential services (OES) have a policy in place to manage third-party risk.
To shore up supply chain security, ENISA proposes “stepping up EU wide coordinated risk assessments and the development of an EU horizontal policy framework,” the report reads.
The report also tackles three other critical challenges: the cybersecurity skills gap; the management of cybersecurity crises; and the need for a coordinated approach to cybersecurity policy adoption.

Juan Perez
Juan has been writing about IT since the mid-1990s, first as a reporter and editor, and now as a content marketer. He spent the bulk of his journalism career at International Data Group’s IDG News Service, a tech news wire service where he held various positions over the years, including Senior Editor and News Editor. His content marketing journey began at Qualys, with stops at Moogsoft and JFrog. As a content marketer, he's helped plan, write and edit the whole gamut of content assets, including blog posts, case studies, e-books, product briefs and white papers, while supporting a wide variety of teams, including product marketing, demand generation, corporate communications, and events.
如有侵权请联系:admin#unsafe.sh