Google Play Protect is a built-in Android solution that enhances devices’ security. Its main job is to detect and block malware on Android devices. Several malware families were known for bypassing Play Protect checks in recent years. This brings us to an important question: “Is Google Play Protect a Reliable Defense Mechanism?”. This blog post shows how Play Protect deals with various Android malware in different scenarios. I deal with Play Protect as a black box.
Google Play Protect is a part of Google’s built-in solutions that provide security features to Android devices. Such features include “Find my phone”, a password manager, and safer browsing on Chrome. In the center of these features, Play Protect is presented as a malware detection and prevention service. According to Google, Play Protect scans 125 billion apps every day. Each app is also checked by on-device machine learning, similarity comparisons, and other techniques to confirm if it is suspicious. Despite being a significant service, Play Protect cannot be found as a separate component on Android devices, as it is accessible through the Google Play app.
Play Protect scans all apps installed on the device, whether installed from the Play Store or any other source. It checks if any of these apps are malware, such as trojans, spyware, phishing, and fraud apps. Additionally, it conducts real-time security checks on any app the user tries to install on the device. When a harmful app is detected, Play Protect can take security measures from warning the user to automatically uninstalling the app. Moreover, if Play Protect suspects an unknown app, the user can send the malicious app to Google for further Cloud-based tests. Play Protect scans all installed apps daily, but users can run additional scans anytime.
According to Google, Play Protect flags apps with several malicious behaviors as malware, for example:
- Backdoors: Apps executing remote and harmful operations on the device.
- Spyware: transmitting personal data from the device, such as contacts, recording audio/video, and collecting logs without user consent.
- Potentially Harmful Apps (PHA): Apps with malicious behaviors, even if they use deprecated APIs that do not work with the installed Android version.
- If the app abuses sensitive permissions, such as accessibility, notification listener, and reading SMS
- The app violates Unwanted Software Policy for e.g., by collecting user personal data, committing ad fraud, or impersonating other apps.
My main target is installing different malware on my test device and seeing if Play Protect can detect them as malicious or potentially harmful. If Play Protect detects malware, I try to disguise the app to bypass it. If the malware bypasses Play Protect validation and gets installed successfully, I verify if further scans can detect its malicious attacks. I ran my tests on the following test device:
- Pixel 4a with Android 13 installed.
- The device is not rooted
- Latest security updates are installed
- Play Protect is updated
I also made sure that Play Protect is set to scan apps on my device. So, let’s start with our first malware.
Anubis is a famous Android malware that has been around for years. As a banking trojan, it focuses on collecting data from the victim’s devices for financial gains, such as accessing their bank accounts. It applies several techniques, such as phishing login pages, keyloggers, SMS interception, anti-detection, and anti-removal techniques. Therefore, it is an excellent example of a trojan malicious app that commits phishing and fraud attacks.
In my first test, I will try to install Anubis malware on my test device. The malware is disguised as a currency converter app. The malware was clearly detected on Virustotal as malware, with a score of 40/63. I called this app “anubis_original.apk” for simplicity. So, what happens when I try to install it on my device?
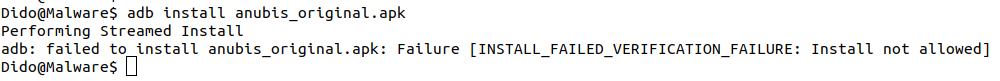
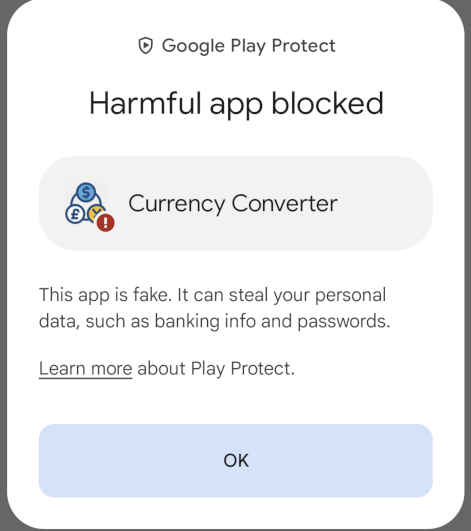
Wonderful ! Play Protect detected it as a malware and blocked the installation. Thanks Play Protect!
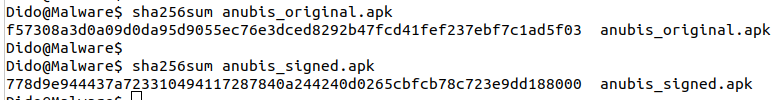
Let’s disguise the app. Usually, the app’s signing certificate/key identifies the developer or its source in general. Therefore, it is a common way to detect malware. I will generate a new keystore and sign the app with it.
# Duplicate the app cp anubis_original.apk anubis_signed.apk # Generate a keystore keytool -genkey -v -keystore PlayProtectBypass.keystore -keyalg RSA -keysize 2048 -validity 10000 -alias PlayProtect # Sign the app with my keystore Dido@Malware$ apksigner sign --ks PlayProtectBypass.keystore anubis_signed.apk
Virustotal still detects the app as malicious, with a score of 27/63. Is this disguise enough to trick Play Protect? Let’s see.
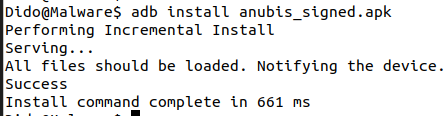
The app is successfully installed on the device! Unfortunately, that was too easy. When the app is started, it asks for permissions, such as running in the background and accessing files. I ran the Play Protect scan, hoping that it would detect the malware, but it did not. The malware icon is highlighted in red in the following screenshot of Play Protect’s scan result.
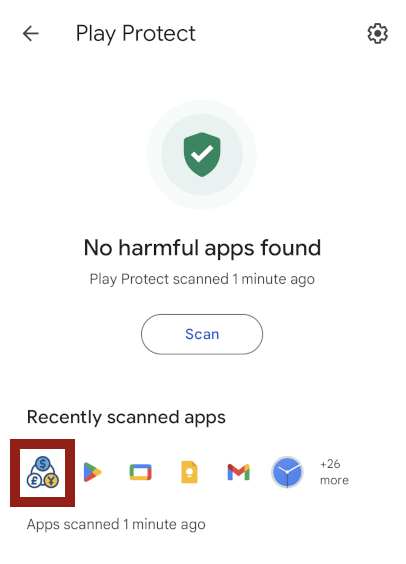
Downloaded Apps
Usually, malicious apps are installed from third-party stores. Victims are somehow tricked into downloading the app from a website and installing it from the device’s storage. To simulate this scenario, I hosted the app on a local Python web server, downloaded it, and tried to install it. For a clean test, I uninstalled anubis_signed.apk and repeated the signature steps for another copy, anubis_signed2.apk.
When I tried to download the app using Chrome, it warned me that the download was not safe, but that is because it’s over clear-text HTTP. Additionally, Chrome warned me that the file I was downloading might be harmful, but it also showed the same warning with benign apps. After I allowed apps from other applications (in this case, Chrome) to be installed, the app was successfully installed. I scanned my device using Play Protect, and I did not find any harmful apps.
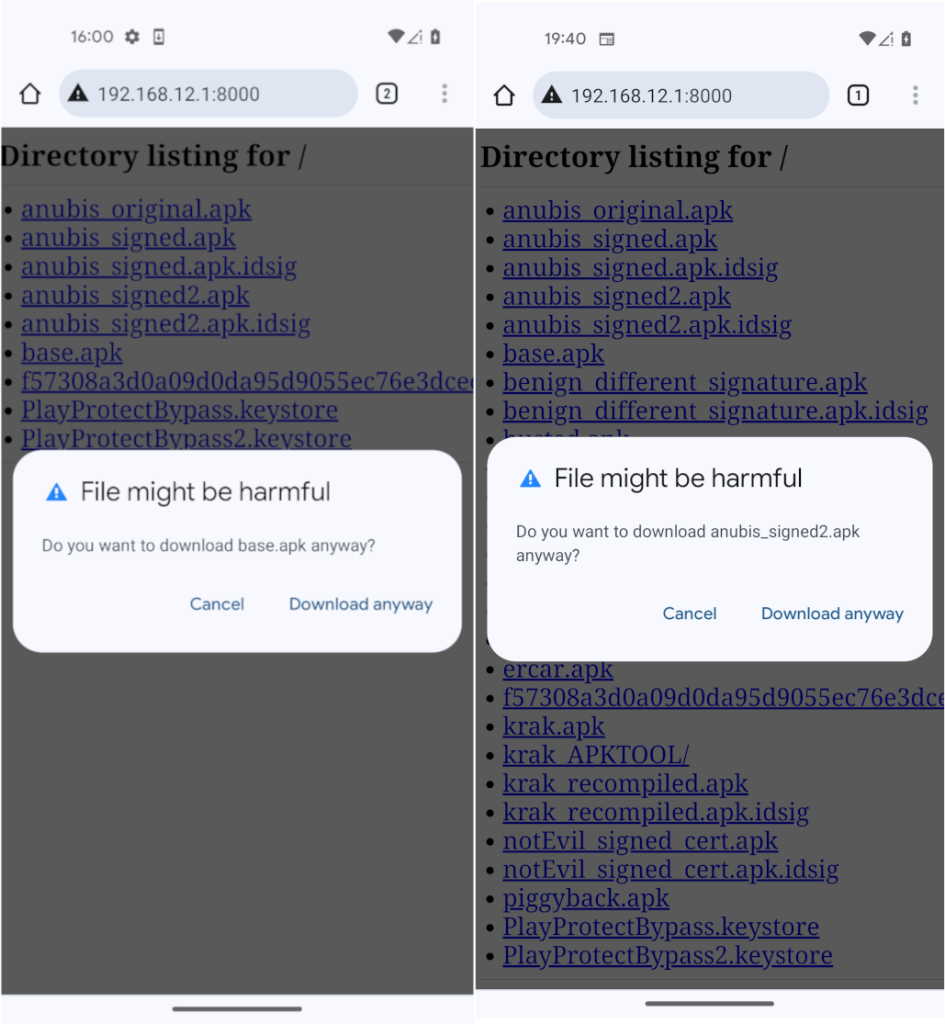
This test suggests that Play Protect tests only some attributes of the app, such as the signing certificate, but not the app’s nature or capabilities. Moreover, signing the app with another certificate changes its hash. Therefore, it is also possible that Play Protect validates the app’s hash, not its signing certificate. Further tests will elaborate on this.
So, it seems that Play Protect was not very successful in blocking the installation of malicious apps. But to give it a reason for doubt, it might detect them later when they start to act maliciously! Since I do not have access to the C&C server for this Anubis malware, I am not 100% sure what this malware does on my device.
In a previous blog post, I analyzed Spymax RAT. It would have been convenient to use it in this context, but Spymax depends on a deprecated API, so its apps do not work properly on recent Android versions and keep crashing. So, I will use his younger brother, CraxsRAT.
CraxsRAT is a very popular RAT. It has capabilities similar to Spymax, including keylogging, camera and mic monitoring, clipboard monitoring, capturing contacts, SMS, etc. In addition, it offers new features such as monitoring the device’s screen and even reading text from it. CraxsRAT can be bought on the public internet for prices reaching $1000. Moreover, its cracked versions are also available. So, it is pretty common. Both Spymax and CraxsRAT were known for bypassing Play Protect.
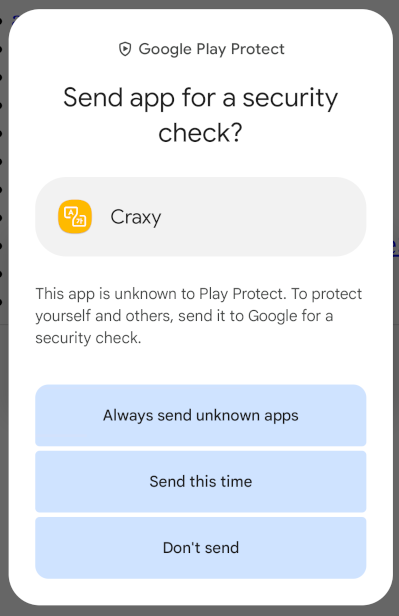
Its dropper app can be built from its C&C server, which provides a random package name and icons. Moreover, it offers extra anti-detection techniques, such as binding the dropper to benign apps and emulator detection. For a simple start, I built a dropper without these extra anti-detection techniques and called it “craxy”.On Virustotal this dropper is detected by 14/55 scanners. I tried to install craxy using ADB and by downloading it as before.
Play Protect detected the app as “unknown”; therefore, it recommended that I send it to Google for security checks, to which I agreed. This did not block the installation on the device. Both installation trials were successful even since the malware’s original keystore signs the app.
After the app was installed, I enabled some dangerous permissions for the app, including:
- Letting the app run in the background
- Accessibility
- Enabling drawing over the app
- Install unknown apps
- Access to contacts, files (sdcard), and calls
These permissions/capabilities allowed me to perform the following attacks:
- Keylogging
- Capturing clipboard
- Uploading/downloading files from/to the device
- Launch an app on the device
- Other attacks, such as camera and mic monitoring, did not work on this test device.
After each attack, I ran a Play Protect scan, which never flagged the app as malicious. A couple of hours after I finished my tests, I found that Play Protect has detected the app as malicious. Since the app was idle for a long time, I suspect that sending the app to Google for cloud-based scanning has detected the app as malicious. After that, Play Protect blocked further trials to reinstall the app on this device or other devices.
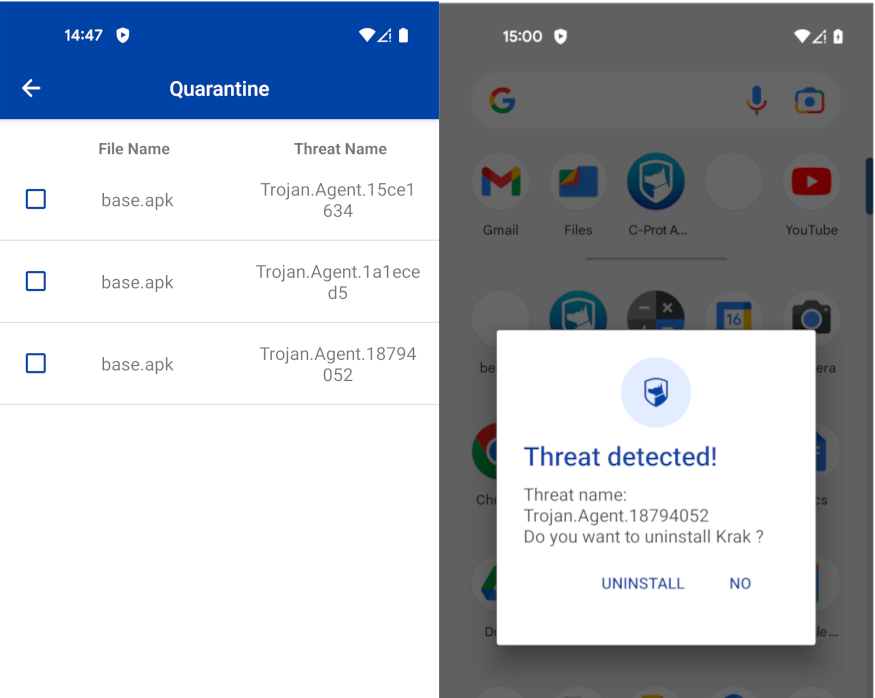
Sending an app to Google should increase the chances of detecting malicious behaviors. Unfortunately, there is no clear way to send an app to be checked by Google at installation time. So, I have built two droppers: “Krak” and “Busted.” Both were detected as unknown apps by Play Protect during installation, but I sent only “Busted” to be checked. I granted both the same permissions and capabilities mentioned earlier. The Play Protect scan did not detect any malicious nature in either app.
After almost three hours, I ran another Play Protect scan. This time, “Busted” was detected as harmful and uninstalled from the device. On the other hand, “Krak,” whose logo is highlighted in red in the following screenshot, was not detected.
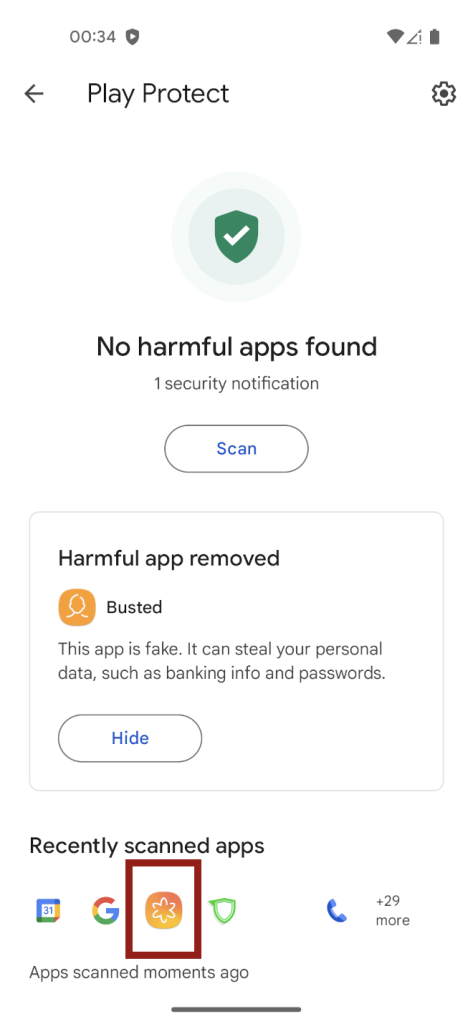
This simple test shows the following points:
1. Sending unknown apps to Google increases the chances of malware detection
2. Once an app is detected harmful, it will not be installed on any other device (with enabled and updated Play Protect)
3. Detecting a malicious app does not teach Play Protect to detect slightly different apps with the same malicious behavior and capabilities.
Is it about signing certificate ?
In section 2 it was not clear if Play Protect validates the signing certificate of the app. Both “Busted” and “Krak” are signed by the same keystore/certificate, as shown below:
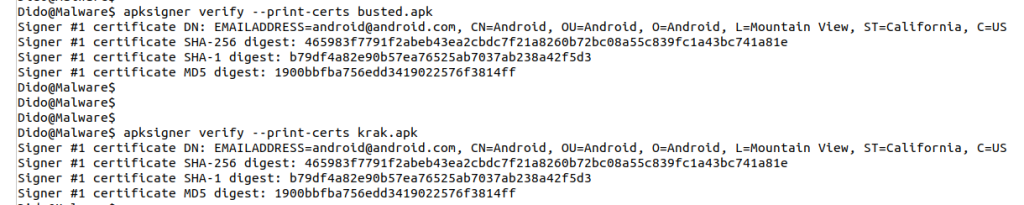
I uninstalled “Krak” and reinstalled it successfully. This shows that Play Protect does not judge an app based on its signing certificate. Additionally, as shown in Chapter 2, “anubis.apk” and “anubis_signed.apk” are the same app except for their signature and hash. Combining the results of the two tests, it seems that the on-device scans of Play Protect judge whether the app is malicious depending on its hash. If that’s the case, then any minor change in the app, such as signing it with another certificate or changing a single character in any of its files, would enable it to bypass on-device Play Protect scans.
I installed three antivirus apps on the test device to compare Play Protect to other alternatives. This blog post will not analyze how these antivirus apps work; I will compare their performances to Play Protect’s. With each antivirus app, I will perform the following tests:
- Install previously mentioned anubis_signed.apk
- Install a Spymax APK, signed with a custom keystore
- Install previously mentioned Krak.apk
- Scan the device; when the three apps are already installed on the device
Phone Guard
The first is called “Phone Guard: Antivirus and Malware Cleaner”, developed by “Minim Dev”. It was released just one month ago. It was downloaded more than 1000 times. I was able to install these three apps on its watch. Additionally, scanning the device did not detect any of the three apps.
C-Prot Antivirus Security
The second antivirus has been in use since 2016. Since then, it has been downloaded more than 100K times. Its latest version, 1.01.8897, is about four months old. This antivirus asks for special permissions such “access to all files”, “allow display on other apps” and “usage access/PACKAGE_USAGE_STATS”.
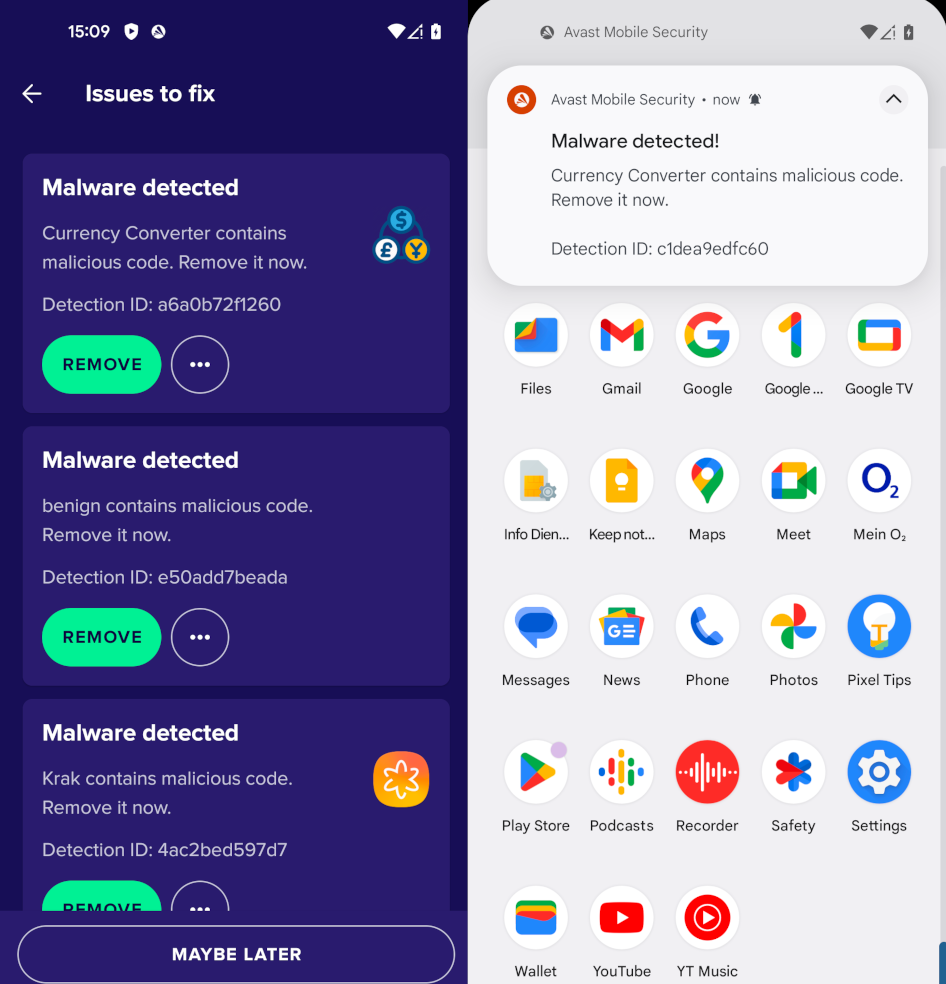
The antivirus immediately detected the three apps as malicious, whether when installing or scanning them if they were already installed.
Avast Antivirus and Security
Avast is considered one of the best antivirus apps for Android. First released in 2011, it has been downloaded over 100 million times! It offers paid packages, but I will go for the free version. It asks only for notifications and access to all files.
Avast immediately detected apps during and after installation.
I informed Google about this issue on March 31st, 2024. I used the example of resigning the Anubis app to show how easy it is to bypass Play Protect scans. On April 3rd, they responded, “The issue might not be severe enough to track it as an abuse risk.”
Conclusion
In conclusion, my tests show that Play Protect is yet to be reliable as the only defense mechanism against Android malware. Installing malware on my test device bypassing Play Protect tests was relatively easy. Moreover, it could not detect noisy malicious attacks such as keylogging or periodic phishing notifications. Apps requesting many dangerous permissions, such as accessibility and installing other apps, do not trigger anything in Play Protect.
Furthermore, the tests show that sending malicious apps to Google for further cloud-based tests successfully detected them as malware. Another good point is that the detected malware cannot be installed on other devices. However, cloud-based tests take a relatively long time, which can be enough for malware to cause harm to the user. Besides, Play Protect does not allow users to send an app to Google for cloud-based checks only once during installation.
Moreover, flagging an app as malicious does not help Play Protect detect similar apps as malware. Signing the app with another certificate is enough to bypass Play Protect on-device scans. At the same time, similar but not identical apps signed with the same certificate are treated differently. I would say that Play Protect compares the hashes of the installed apps to a list of already detected malware. However, I cannot confirm that only through black box research.
Finally, Play Protect’s performance still needs improvement compared to average antivirus apps. An average antivirus app detected malware more accurately and faster than Play Protect’s combined on-device and cloud-based scans. Only some services that Google provides have to be on the highest level. This blog post discusses weak security measures in Google’s MDM solution, “Endpoint Management.”
Recommendation
It is a great idea to have a built-in security component such as Play Protect, powered by Google itself, and scans billions of apps daily. It may step up to its promises in the future. As for the time being, the following measures are recommended to secure your Android device:
- Despite the disappointing results, enabling Play Protect on your device is still recommended.
- Choose always to send unknown apps to Google when asked.
- Never install apps from untrusted sources, such as websites or SMS campaigns.
- Install a well-known third-party antivirus on your Android device.
- Upgrade to the latest Android version available on your phone.
- Do not root your phone because it increases the impact of infected malware
You have had bad experience with android malware before? It would be nice to share your experience in the comments 🙂
Cheers!
Ahmad
P.S.: If you are interested in IT security and would like to get insight into various security topics, then you potentially want to check out #TROOPERS24 in the beautiful city of Heidelberg, Germany and attend my “Hacking Mobile Apps” training!
