工具 | 看我如何开发挖掘src工具
申明:本次测试只作为学习用处,请勿未授权进行渗透测试,切勿用于其它用途!公众号现在只对常读和星标的公众号才展示大图推送,建议大家把 明暗安全 设为星标,否则可能就看不到啦!1.漏洞背景前些日子开发了一 2024-1-5 15:24:57 Author: F12sec(查看原文) 阅读量:30 收藏
申明:本次测试只作为学习用处,请勿未授权进行渗透测试,切勿用于其它用途!公众号现在只对常读和星标的公众号才展示大图推送,建议大家把 明暗安全 设为星标,否则可能就看不到啦!1.漏洞背景前些日子开发了一 2024-1-5 15:24:57 Author: F12sec(查看原文) 阅读量:30 收藏
申明:本次测试只作为学习用处,请勿未授权进行渗透测试,切勿用于其它用途!
公众号现在只对常读和星标的公众号才展示大图推送,
建议大家把 明暗安全
设为星标,否则可能就看不到啦!
1.漏洞背景
前些日子开发了一个web版的google语法生成工具,反响很不错,月访问量达到了1k+但是感觉在线版的不太方便,索性做一个小工具。
首先下载scenebuilder
https://gluonhq.com/
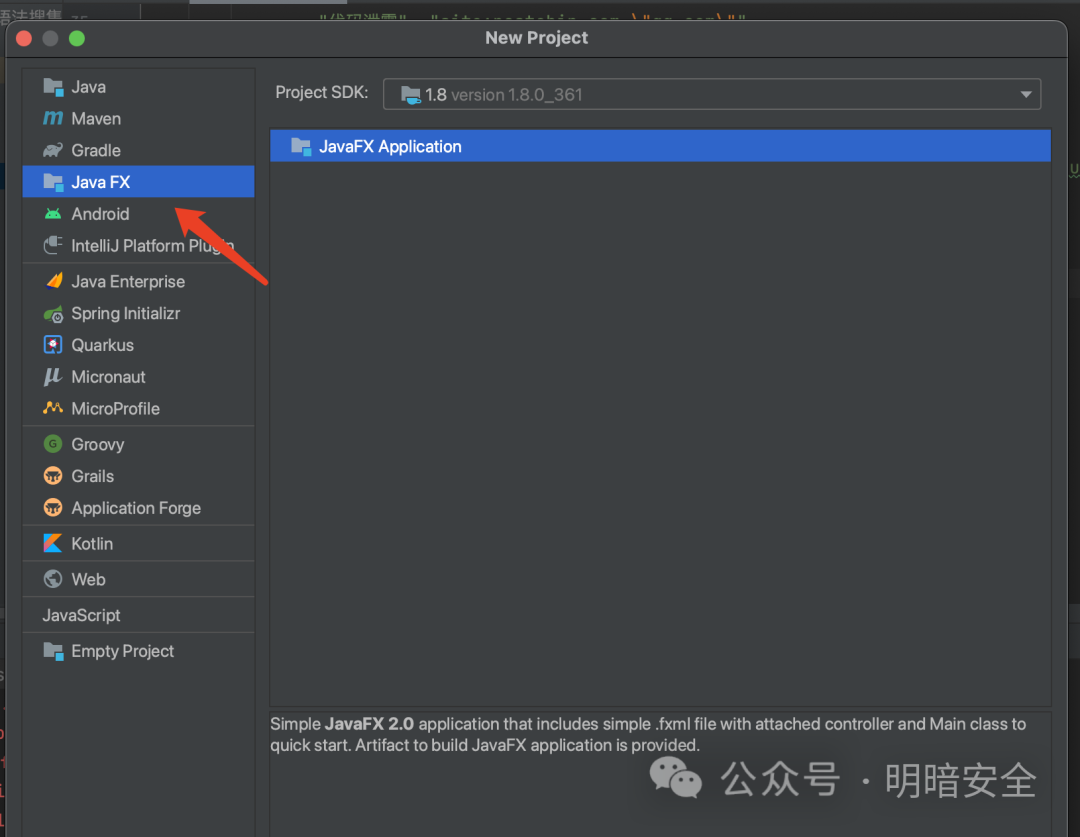
2. idea里导入path
setting-->搜索javafx
3. 新建javafx项目
如果配置正确,就能在idea里打开可视化工具。
4. 绘制自己想要的格式,并给文本框添加属性。 为什么要给文本添加 因为在文本里输入数据,需要获取文本里的数据进行处理。
5. 为按钮添加事件。
为什么要添加事件,为了方便执行点击按钮的操作。如果看不懂,百度翻译即可
6. 生成java代码。
代码很简单,是自己配置的东西,两个text属性,一个点击事件。剩下代码在点击事件里写就行。
关键代码如下:
获取text的数据(小框)修改格式输出到文本里
void google(MouseEvent event) {String website = text.getText().trim();StringBuilder stringBuilder = new StringBuilder();String[] queries = new String[]{"敏感信息搜索", "site:qq.com ( \"默认密码\" OR \"学号\" OR \"工号\")","后台接口和敏感信息探测", "site:qq.com (inurl:login OR inurl:admin OR inurl:index OR inurl:登录) OR (inurl:config | inurl:env | inurl:setting | inurl:backup | inurl:admin | inurl:php)","查找暴露的特殊文件", "site:qq.com filetype:txt OR filetype:xls OR filetype:xlsx OR filetype:doc OR filetype:docx OR filetype:pdf","已公开的 XSS 和重定向漏洞", "site:openbugbounty.org inurl:reports intext:\"qq.com\"","常见的敏感文件扩展", "site:qq.com ext:log | ext:txt | ext:conf | ext:cnf | ext:ini | ext:env | ext:sh | ext:bak | ext:backup | ext:swp | ext:old | ext:~ | ext:git | ext:svn | ext:htpasswd | ext:htaccess","XSS 漏洞倾向参数", "inurl:q= | inurl:s= | inurl:search= | inurl:query= | inurl:keyword= | inurl:lang= inurl:& site:qq.com","重定向漏洞倾向参数", "inurl:url= | inurl:return= | inurl:next= | inurl:redirect= | inurl:redir= | inurl:ret= | inurl:r2= | inurl:page= inurl:& inurl:http site:qq.com","SQL 注入倾向参数", "inurl:id= | inurl:pid= | inurl:category= | inurl:cat= | inurl:action= | inurl:sid= | inurl:dir= inurl:& site:qq.com","SSRF 漏洞倾向参数", "inurl:http | inurl:url= | inurl:path= | inurl:dest= | inurl:html= | inurl:data= | inurl:domain= | inurl:page= inurl:& site:qq.com","本地文件包含(LFI)倾向参数", "inurl:include | inurl:dir | inurl:detail= | inurl:file= | inurl:folder= | inurl:inc= | inurl:locate= | inurl:doc= | inurl:conf= inurl:& site:qq.com","远程命令执行(RCE)倾向参数", "inurl:cmd | inurl:exec= | inurl:query= | inurl:code= | inurl:do= | inurl:run= | inurl:read= | inurl:ping= inurl:& site:qq.com","敏感参数", "inurl:email= | inurl:phone= | inurl:password= | inurl:secret= inurl:& site:qq.com","API 文档", "inurl:apidocs | inurl:api-docs | inurl:swagger | inurl:api-explorer site:qq.com","代码泄露", "site:pastebin.com \"qq.com\"","云存储", "site:s3.amazonaws.com \"qq.com\"","JFrog Artifactory", "site:jfrog.io \"qq.com\"","Firebase", "site:firebaseio.com \"qq.com\"","文件上传端点", "site:qq.com \"choose file\"","漏洞赏金和漏洞披露程序", "\"submit vulnerability report\" | \"powered by bugcrowd\" | \"powered by hackerone\" site:*/security.txt \"bounty\"","暴露的 Apache 服务器状态", "site:*/server-status apache","WordPress", "inurl:/wp-admin/admin-ajax.php"};for (int i = 0; i < queries.length; i += 2) {stringBuilder.append(queries[i]).append(":\n").append(queries[i + 1]).append("\n\n");}text1.setText(stringBuilder.toString());}
7. 打包为jar
8. 输出到了指定目录,运行如下:
成品关注公众号回复:google工具 获取
往期精彩推荐
工具 | burp被动扫描xss神器
工具 | 无回显变可回显rce
❤️爱心三连击
1.本文已收录在明暗官方网站:http://www.php1nf0.top/
文章来源: http://mp.weixin.qq.com/s?__biz=Mzg5NjU3NzE3OQ==&mid=2247488797&idx=1&sn=96aeed4e36053eb4a590caf138497438&chksm=c19d02f406cf74ba46178ef40db495c331f3a0f86de14d16edc8f9d0d427672eaffc2843bf06&scene=0&xtrack=1#rd
如有侵权请联系:admin#unsafe.sh
如有侵权请联系:admin#unsafe.sh