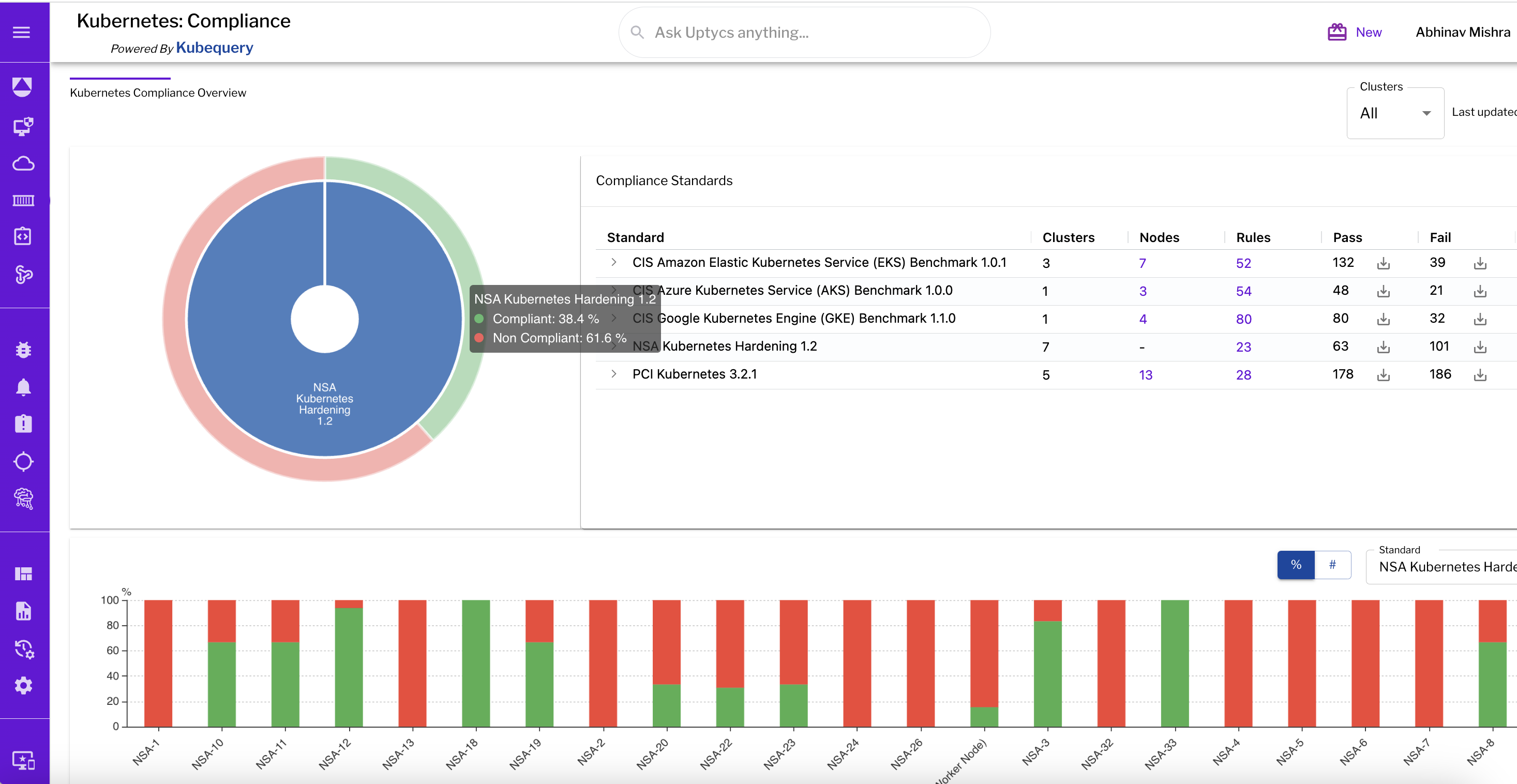
Organizations across the globe are embracing Kubernetes and harnessing its power to deliver cloud-native applications on top cloud providers like Amazon Web Services (AWS), Azure, and Google Cloud Platform. However, Kubernetes' default security limitations mean safeguarding your cluster and data should be a top priority. Securing Kubernetes can be a challenge, particularly since clusters are a common source of misconfigurations in the cloud, can be shared between multiple teams, and the learning curve for Kubernetes is steep. But there is help available. Last August, the National Security Agency (NSA) and the Cybersecurity and Infrastructure Security Agency (CISA) released an updated version of the Kubernetes Hardening Guide. The guide helps organizations solve those key misconfigurations and provides guidance to enterprises on solving key misconfigurations such as: While the insights the guide provides are a fantastic first step, there are some key challenges we saw in the market when it came to using the recommendations: While these three challenges can seem daunting, the Uptycs platform streamlines visibility into key compliance risks and provides real-time evidence and remediation steps that are continuous, actionable, and insightful. Let’s see an example of this in action! When you land on the compliance dashboard, you get a single pane of glass view into the different standards being run across your cluster fleet. Any cluster you enroll, whether EKS, GKE, AKS, or even ones you manage yourself, can undergo the same compliance scanning process. Compliance scanning is done every 6 hours and is configurable. This gives the user a good understanding that their assets are being continuously monitored for compliance issues and an overall sense of the state of their system at any present moment. In the example below, we see that roughly 40% of our assets are compliant when it comes to NSA Hardening, and 60% are non-compliant. We can see that 63 rules passed while 101 failed, and below, we get a breakdown across the different NSA Hardening categories of our pass/fail rate. Figure 1 - Compliance overview Next, let’s look at what actual rules are failing so we can appropriately triage. Next, we can click the list of rules and get an overview across different categories of what is passed, what is failing, and how many assets for the given rule are passing/failing. The good thing is that just like the NSA Hardening Guide, Uptycs also logically organizes it into the relevant sections so you can focus on a specific security task that is most relevant to you instead of traversing through tables of 100s of rules. Clicking a specific rule, for example, NSA-23 - Defining Resource Quota Policies, gives us the clusters that are passing and failing this rule. In this case, most of my clusters do not have resource quota policies defined for their namespaces. This can be problematic, especially in shared cluster environments where one user assigned to a namespace can over-inflate their namespace and limit other applications and pods from getting deployed. This can be especially problematic if you have important software add-ons for security, observability, cost metrics, and more that constantly need to be running on the cluster. Suppose you assign this to a DevOps or platform engineer to take a closer look at. Let’s see how we can use the evidence-based view to get more details. Many times, as a security ops engineer, you may get pushback asking why this check is so important. By clicking the purple magnifying glass, you get an evidence-based view that gives the real source of why this issue is so important, the evidence behind it, and the remediation steps. For example, for the no resource policies defined issue, you can see exact remediation steps of how one can define a ResourceQuota with CPU and memory limits for a given namespace. Another example below shows the importance of implementing a default network policy to prevent lateral movement inside the cluster. This is especially important because, by default, every pod can talk to one another inside a cluster, increasing your lateral surface attack in case one pod with vulnerabilities is compromised. Uptycs provides a 3 step process of visualizing, triaging, and generating evidence to remediate that allows CISOs and security admins to be continuously compliant. This process applies to NSA Hardening and any standard such as CIS Kubernetes Benchmarks out of the box. If you’re looking to harden your infrastructure using the NSA Hardening rules, try the Uptycs platform and see how it enables you to take the great guidance the NSA has provided and make it operational and actionable for your organization. You might also like: Uptycs for Kubernetes and container security
Step 1: Assessing the State of the System
Step 2: Triaging Through the Rules
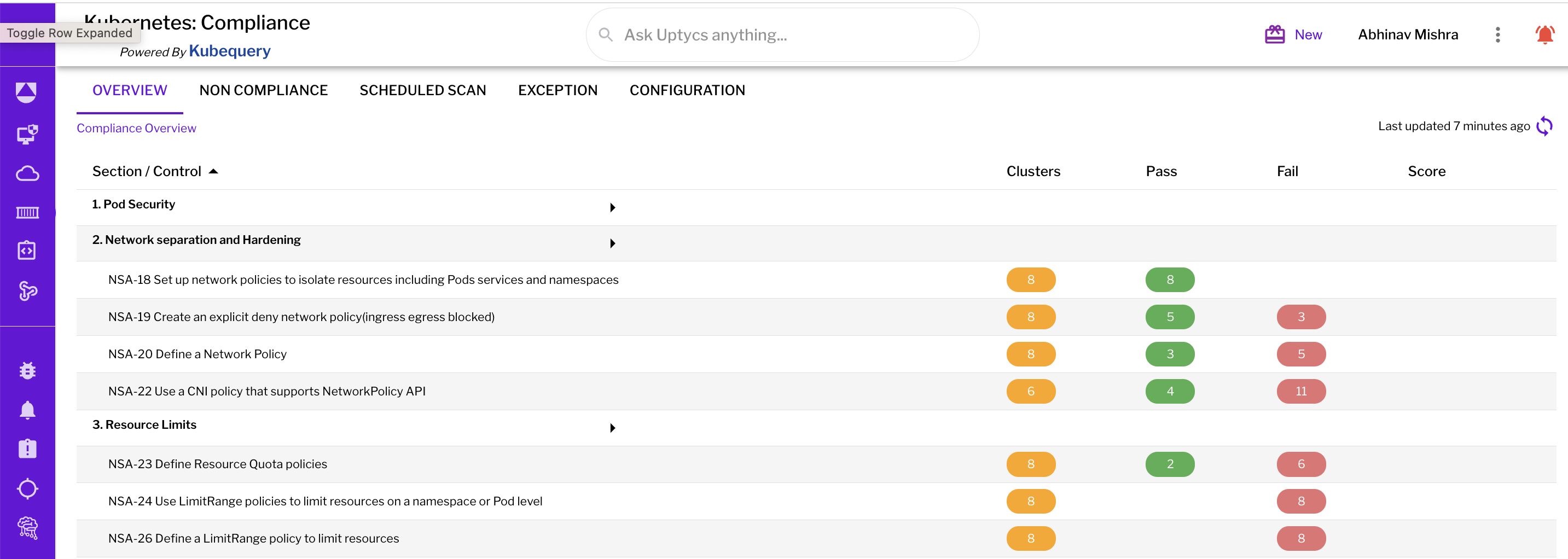 Figure 2 - Rules listing
Figure 2 - Rules listing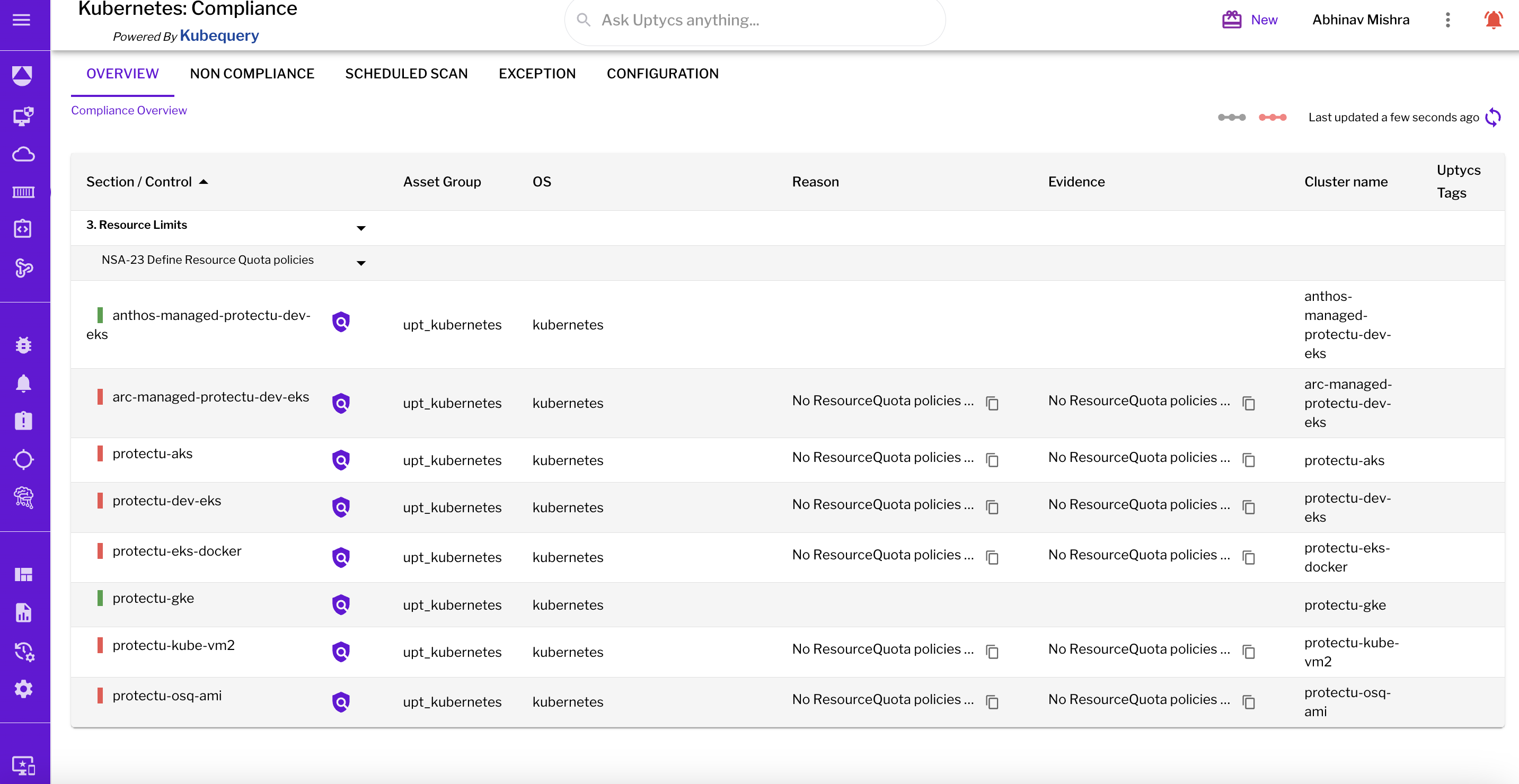 Figure 3 - Cluster listing
Figure 3 - Cluster listingStep 3: Generating the Evidence and Remediation To Take Action
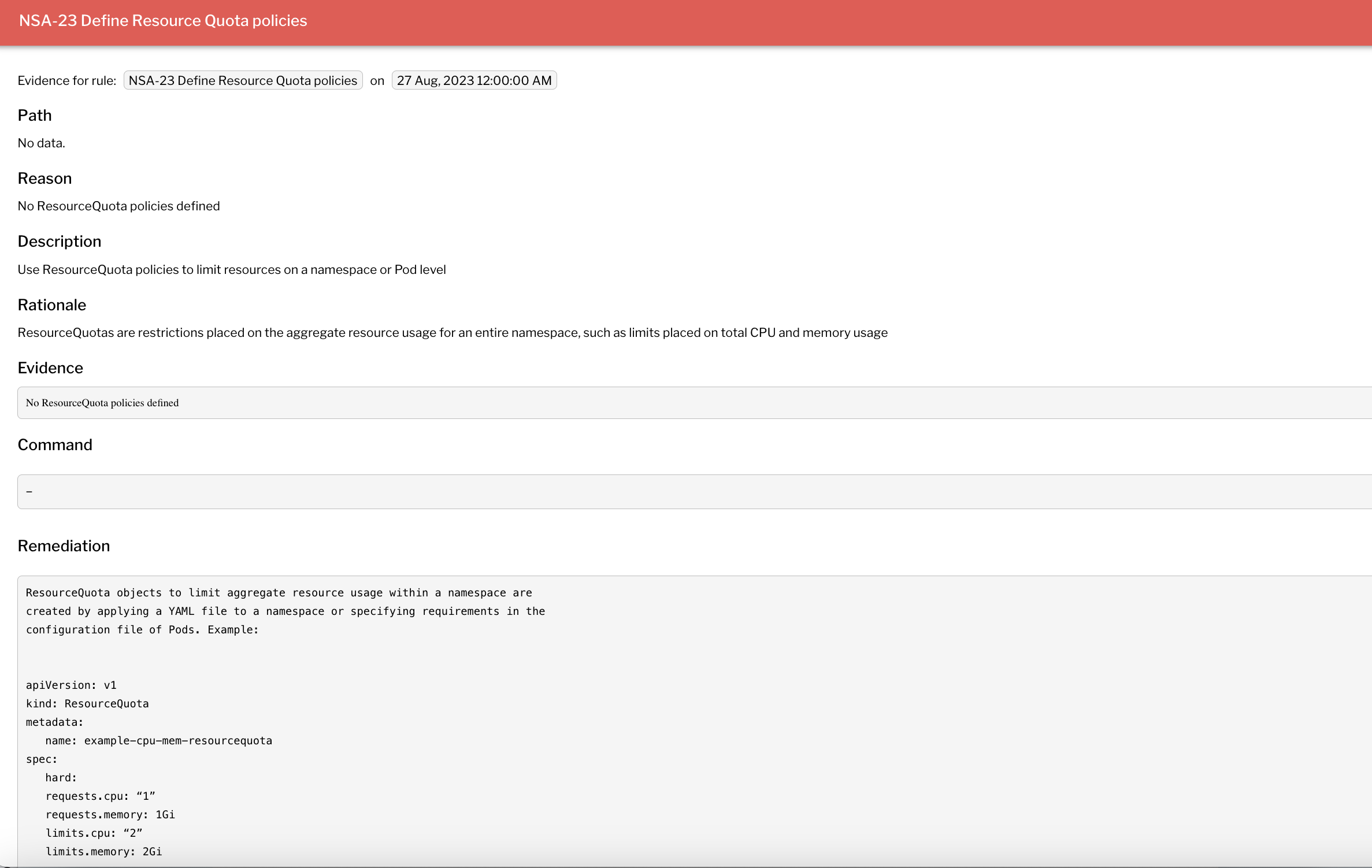 Image 4 - Resource quota evidence
Image 4 - Resource quota evidence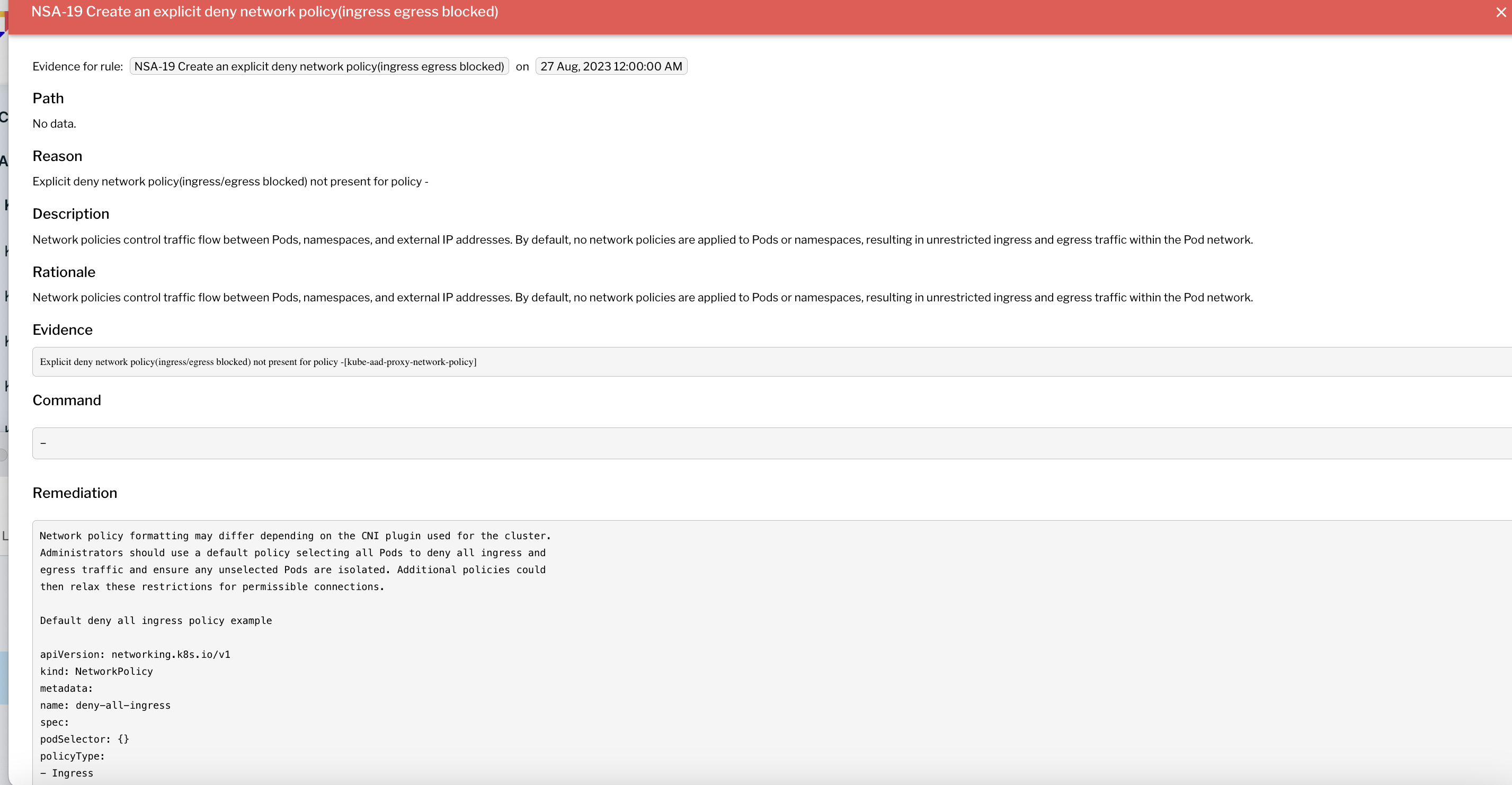 Figure 5 - Network policy evidence
Figure 5 - Network policy evidenceConclusion

Kubernetes Security: Uptycs Solution for NSA Hardening & Compliance
Organizations across the globe are embracing Kubernetes and harnessi 2023-9-11 20:0:0 Author: www.uptycs.com(查看原文) 阅读量:30 收藏
Organizations across the globe are embracing Kubernetes and harnessi 2023-9-11 20:0:0 Author: www.uptycs.com(查看原文) 阅读量:30 收藏
文章来源: https://www.uptycs.com/blog/kubernetes-security-actionable-insights-nsa-compliance-reporting
如有侵权请联系:admin#unsafe.sh
如有侵权请联系:admin#unsafe.sh