Staying ahead of malicious threat actors in the cloud is the key to preventing costly data breaches and ensuring secure operations. But how do you know what these bad actors are looking for in order to carry out their schemes? It may help to look inside the mind of a cloud threat actor and understand the techniques they use.
They often exploit existing APIs to find vulnerabilities and employ a variety of tools. Some of these tools are specifically designed for compromising cloud environments, while others are repurposed from technologies originally intended for risk awareness and defense. These methods enable attackers to conduct reconnaissance, move laterally, escalate privileges, exfiltrate data, create backdoors, and more.
Unlocking the cloud: How APIs become vulnerabilities
Picture a cunning burglar sneaking into a pitch-black house, unaware of its layout, valuable possessions, locked doors, or even the number of floors. Just like in the world of cyber attackers, they must conduct reconnaissance to gather vital information and answer key questions.
In cloud computing, reconnaissance involves calling various APIs. That's why it becomes essential to comprehend which APIs your team uses. One way you can narrow the possibilities is by leveraging the source IP and user agent string. However, keep in mind there are specific APIs that threat actors always target – their way of feeling their way around your house, often leaning on tools to do so.
This understanding becomes critical since these adversaries have no clue about the credentials they have stolen or their exact location. Hence, they will always resort to reconnaissance to figure out where and how they can progress within an account.
 Figure 1–Example APIs used by a threat actor to perform recon on a cloud environment
Figure 1–Example APIs used by a threat actor to perform recon on a cloud environment
Cloud complexity makes attacks easier
Cloud providers are like a web of APIs that connect various services. Let's take AWS as an example. Whether you interact with AWS through the console, SDK, or CLI, you're accessing their APIs.
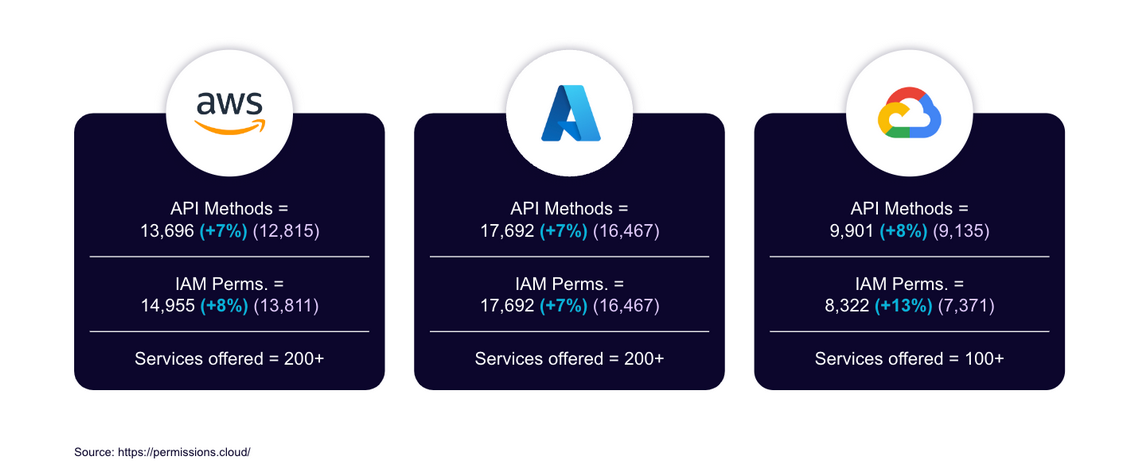
All three major cloud service providers have experienced significant growth in permissions and API methods since Feb. 2023, as seen in the graphic below.
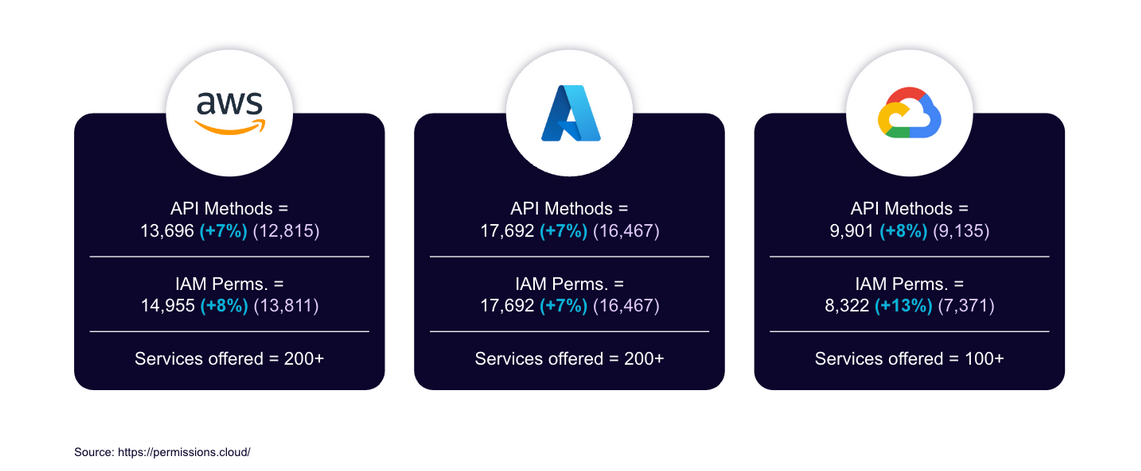 Figure 2–API growth, February through August 2023
Figure 2–API growth, February through August 2023
APIs truly shape the capabilities of cloud providers, paving the way for innovation and security challenges, but also increasing the complexity of managing a cloud environment.
Beyond APIs: Exploiting legitimate security tools
Have you ever wondered how threat actors achieve their desired outcomes? The tools outlined below are just a few examples of those widely used, some of which were actually designed to help defenders identify and fix vulnerabilities:
- Pacu:
- Tool Function: Pacu is an open-source framework for exploiting AWS cloud environments, aimed at offensive security assessments. It helps penetration testers take advantage of configuration weaknesses in an AWS account through easily extendable modules. These modules facilitate a variety of attacks, such as elevating user privileges, compromising IAM users, targeting vulnerable Lambda functions, and more.
- Attacker’s Use: Pacu allows penetration testers to exploit configuration flaws within an AWS account, using modules to expand its functionality easily. They’re about to escalate privileges, create backdoors, perform remote code execution, attack vulnerable Lambda functions, and much more.
- CloudFox:
- Tool Function: CloudFox is designed to provide insights into unknown cloud settings and is an open-source command-line utility. It aims to assist penetration testers and offensive security experts in identifying vulnerable avenues for attack within AWS & Azure environments.
- Attacker’s Use: A threat actor would use CloudFox to gain insights into unfamiliar cloud environments. The tool enables them to pinpoint vulnerable attack paths within cloud infrastructure, assisting in their efforts to exploit security weaknesses.
- Stratus Red Team:
- Tool Function: Stratus Red Team is an open-source initiative designed to mimic typical attack methods within AWS, Azure, GCP, and Kubernetes environments. It enables you to effortlessly carry out offensive maneuvers on live systems while also testing the effectiveness of your threat detection mechanisms from start to finish.
- Attacker’s Use: A threat actor could use Stratus Red Team to practice and refine attack strategies within a cloud environment, taking advantage of the tool's capabilities to emulate common techniques. This allows the attacker to test their methods against live systems without detection, helping them identify successful tactics and understand how to circumvent existing threat detection mechanisms.
- SkyArk:
- Tool Function: SkyArk identifies the entities (users, groups, and roles) that have the most sensitive and risky permissions in both AWS & Microsoft Azure environments.
- Attacker’s Use: Attackers might use SkyArk to discover overly permissive entities, potentially leading to unauthorized access, data breaches, and lateral movement by stealing/using the credentials of those entities.
- Kali Linux:
- Tool Function: Kali Linux is a platform of several hundred tools primarily utilized for various information security tasks, such as Penetration Testing, Security Research, Computer Forensics, and Reverse Engineering.
- Attacker’s Use: Threat actors can use Kali Linux to identify and exploit vulnerabilities in networks, gaining unauthorized access to systems and sensitive data. The software suite allows them to escalate privileges, maintain control over compromised systems, and even cover their tracks to evade detection.
- TruffleHog:
- Tool Function: TruffleHog is a security utility that examines code repositories to identify potential weaknesses associated with confidential keys, like private encryption keys and passwords. It operates by combing through the code to spot text strings resembling secrets and then assesses the robustness of those secrets to gauge their security risk.
- Attacker’s Use: A threat actor would use TruffleHog to scan code repositories for security flaws, particularly looking for mistakenly included sensitive information like passwords and encryption keys. The attacker could gain unauthorized access to secure assets and pilfer confidential data by identifying these vulnerabilities.
- Scout Suite:
- Tool Function: Scout Suite is an open-source tool designed for auditing security across AWS, Azure, GCP, Alibaba Cloud, Oracle Cloud, and Kubernetes. It uses the APIs provided by cloud services to collect configuration information, making it easier to manually inspect and identify vulnerabilities. Instead of sifting through numerous web console pages, Scout Suite automatically offers a streamlined overview of potential attack vectors.
- Attacker’s Use: A threat actor could exploit Scout Suite's capabilities to assess the security posture of targeted cloud environments. By using the APIs that the tool accesses, the attacker could efficiently collect configuration data to manually inspect and pinpoint vulnerabilities. Scout Suite's streamlined presentation of the attack surface would save the threat actor time, allowing them to quickly identify weak spots for exploitation. Since all gathered data can be analyzed offline, the threat actor could conduct their reconnaissance without continuous engagement with the target environment, reducing their chances of detection.
- PowerZure:
- Tool Function: PowerZure is a PowerShell-based project designed to evaluate and exploit assets on Azure. It was developed to serve as a framework capable of conducting reconnaissance and attacks on Azure, AzureAD, and related resources.
- Attacker’s Use: A threat actor could use PowerZure to perform targeted reconnaissance and exploitation activities on Azure. The tool's capabilities in assessing and exploiting Azure, AzureAD, and related resources would enable the attacker to efficiently identify vulnerabilities and execute attacks, potentially gaining unauthorized access or control over these cloud-based assets.
- StormSpotter:
- Tool Function: Stormspotter generates an "attack graph" for resources linked to an Azure subscription, providing red teams and penetration testers a visual map of the attack surface and opportunities for lateral movement within a tenant. This tool also empowers defense teams to rapidly focus and prioritize their incident response efforts.
- Attacker’s Use: A threat actor could use Stormspotter to generate an "attack graph" of resources in a targeted Azure subscription, giving them a visual representation of the attack surface and potential pivot points within a tenant. This information can streamline their attack planning, enabling them to identify vulnerabilities more quickly and execute attacks more efficiently.
These tools hold immense value for threat actors as they provide crucial information for decision-making. They can move laterally, escalate privileges, exfiltrate data, and more. The outputs generated by these tools are of utmost importance. Understanding the mindset of a threat actor means diving into their actions and the tools they leverage.
From observing to outsmarting threat actors
If you’re a SecOps engineer constantly looking to secure environments, I implore you to take a closer look at these amazing tools. I encourage you to use them in a test environment. By doing so, you will witness firsthand the incredible output they provide. It's a chance to truly understand what that output means and ask yourself important questions.
For instance, you might find yourself wondering after using Pacu, ‘Why is this module giving me this particular output? What would a threat actor gain from it? How does it contribute to their tactics?’ Don't worry if you don't have all the answers immediately. This is an opportunity for research and collaboration. Reach out to experienced security professionals, tap into their knowledge, and, most importantly, adopt their mindset.
Understanding the how and why of threat actors will empower you to better defend, configure, and mitigate potential attacks within your own environment. Let's strengthen our security posture and stay one step ahead of any adversary.
The Uptycs shield: Your cloud's best defense
While understanding threat actors' tactics is important, being equipped with the right tools to counteract their actions is critical. That's where Uptycs comes into play. From detecting abnormal API calls to flagging suspicious user activities and configurations, the Uptycs platform is designed to detect and remediate threats in real time.
Request a demo to learn more about how Uptycs can help you improve your cloud security and become more proactive in your defense strategy.
 Figure 1–Example APIs used by a threat actor to perform recon on a cloud environment
Figure 1–Example APIs used by a threat actor to perform recon on a cloud environment Figure 2–API growth, February through August 2023
Figure 2–API growth, February through August 2023